Image encryption and decryption method for utilizing gray system theory to confirm ICA output
A gray system theory and encryption and decryption technology, applied in the field of image encryption and decryption, can solve problems such as the uncertain sequence of decrypted output images, imperfect structure of underdetermined matrices, and uncertain decrypted output sequence, and achieve unconditional security and confidentiality. The problem of uncertain image order and the effect of fast algorithm speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
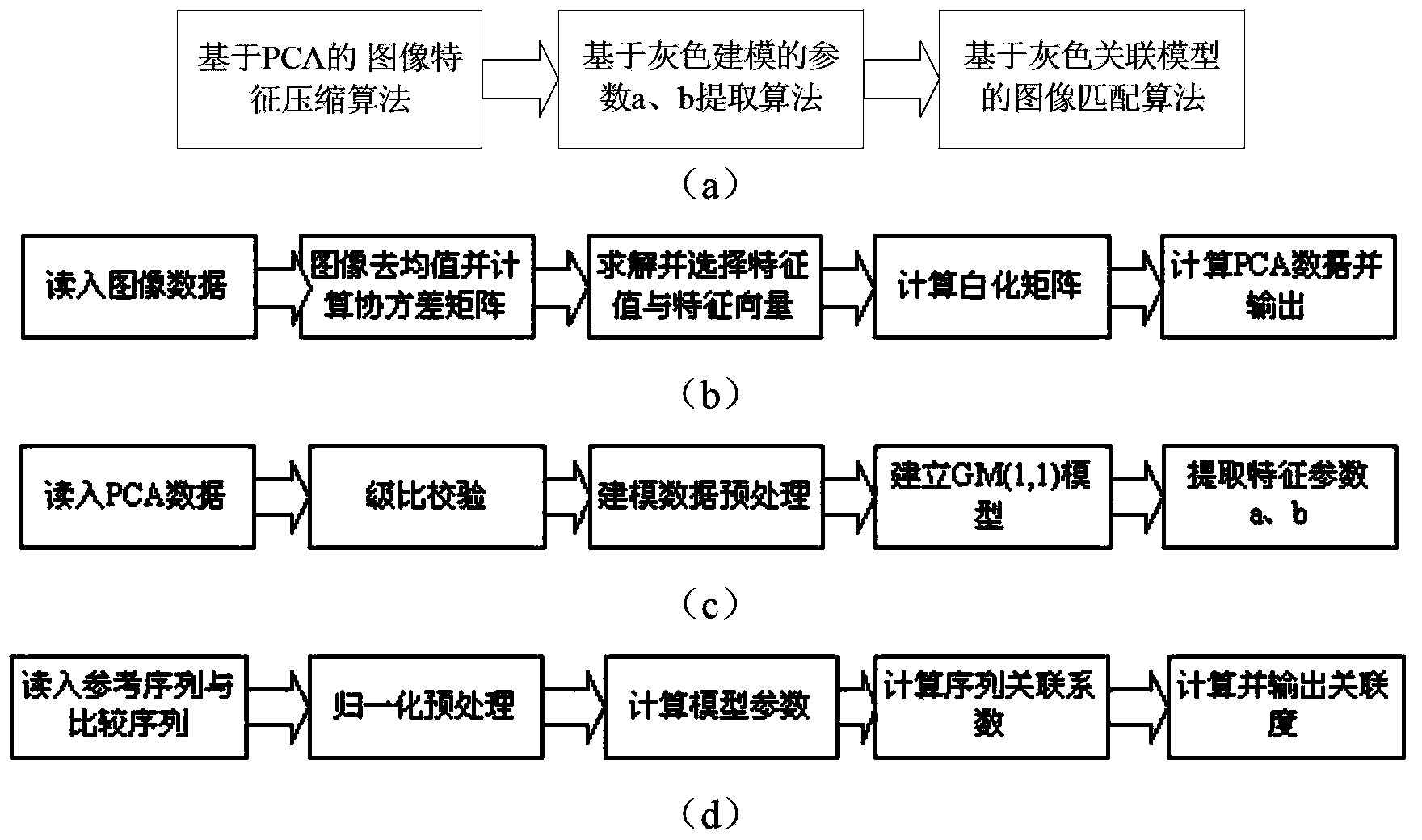
[0029] The specific implementation of the ICA-based image encryption and decryption method proposed by the present invention is as follows:
[0030] 1. Encryption algorithm:
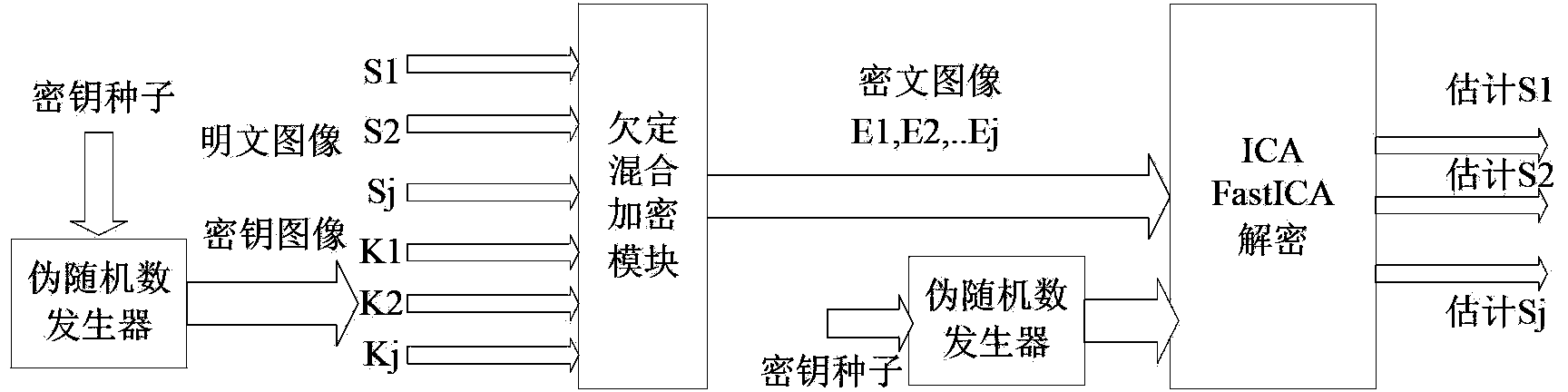
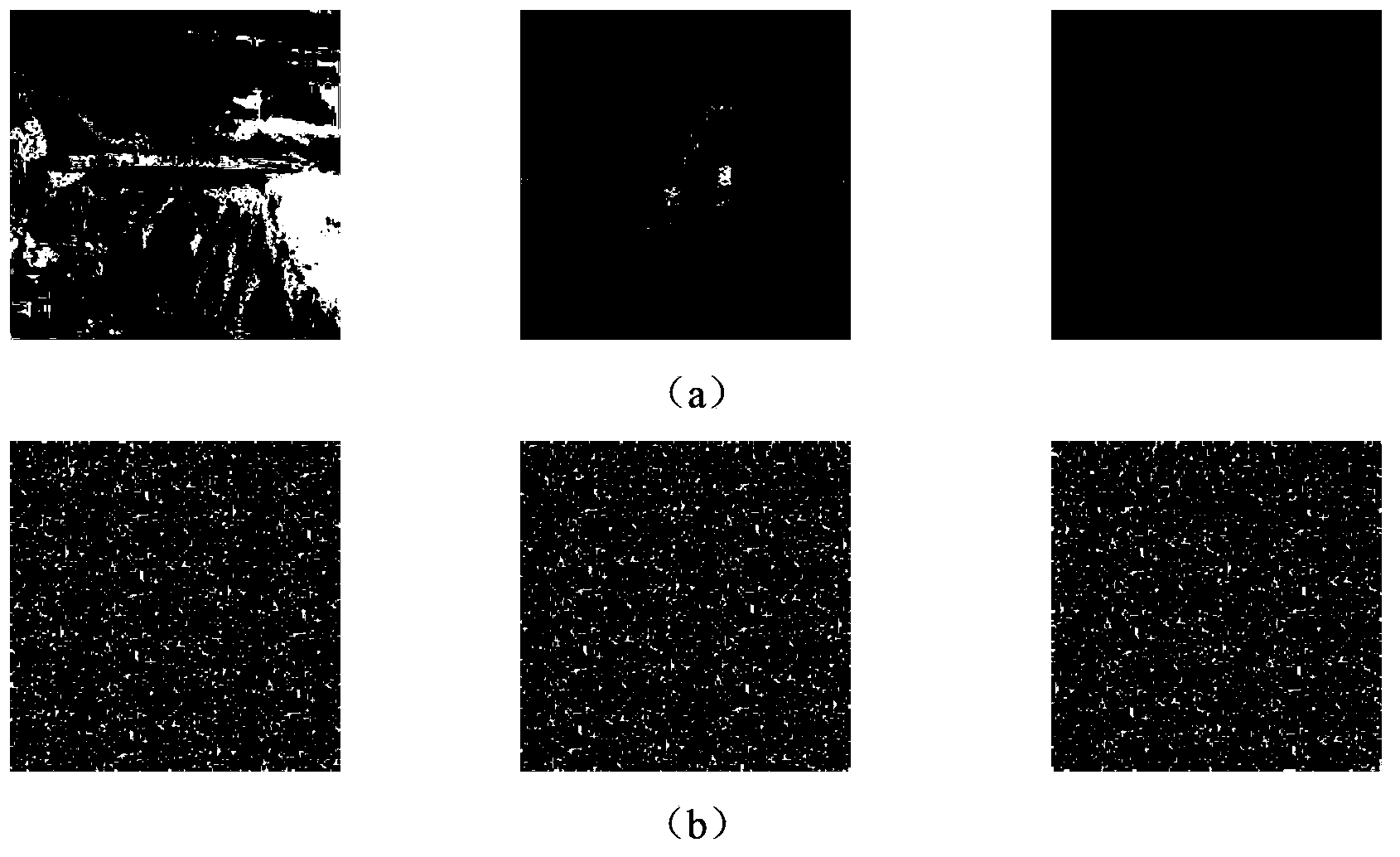
[0031] The encryption end of the present invention adopts the symmetric encryption algorithm based on ICA to encrypt the plaintext image, assuming that the existing plaintext image J,
[0032](1) Row vector straightening is performed on J plaintext images respectively to obtain J one-dimensional row straightening vectors S 1 ,S 2 ,...,S J ;
[0033] (2) First randomly select an integer as one of the random data for generating the key seed, then randomly select one from the data in the computer CPU clock register as the second random data, and use the linear congruential algorithm to generate and step (1) J one-dimensional vectors K of the same dimension as the one-dimensional...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com