Target authentication method based on mobile device and authentication center
A mobile device and authentication center technology, applied in the field of authentication system of integrated identity discrimination technology, to achieve the effect of saving manufacturing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0070] Use this method to authenticate items such as products and invoices. A mobile device and network-based method for target authentication through authentication identification and authentication behavior, comprising:
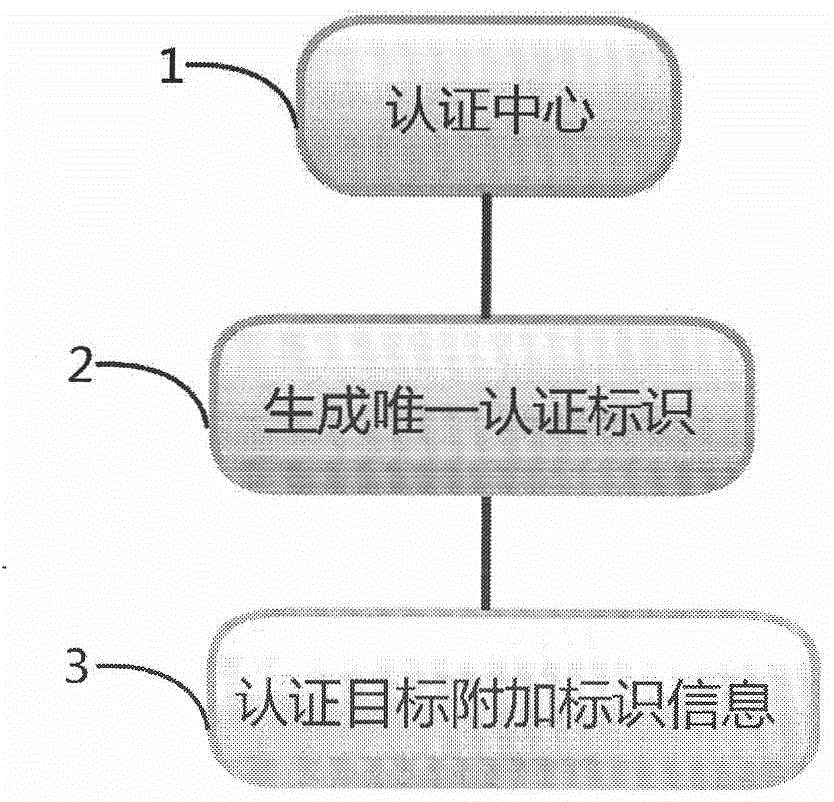
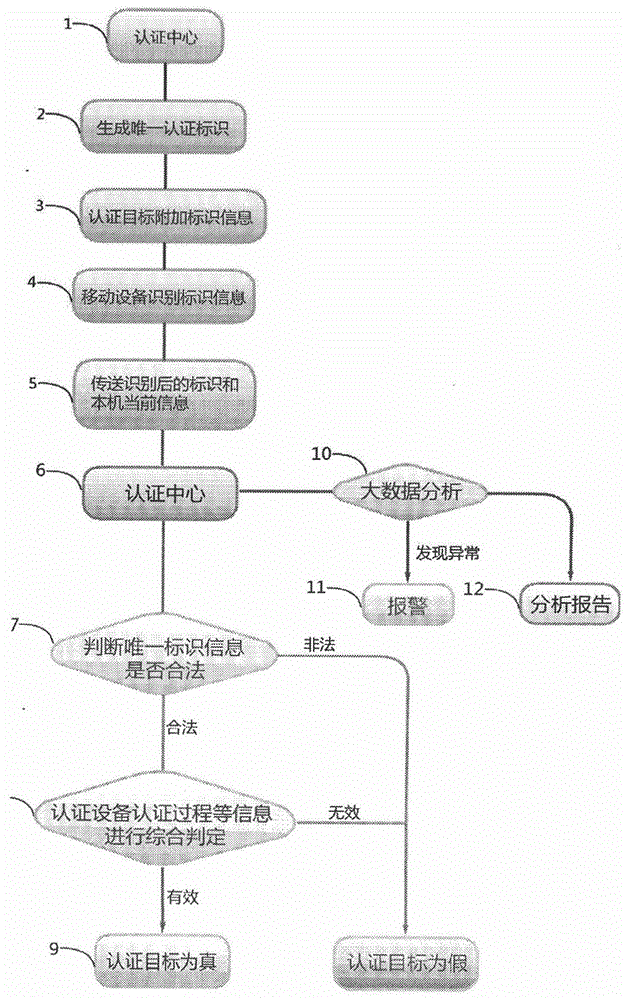
[0071] 1. Certification center
[0072] 2. The certification center generates unique identification information A;
[0073] 3. On the certification target (certified item), use the printed QR code to record the unique identification information B:
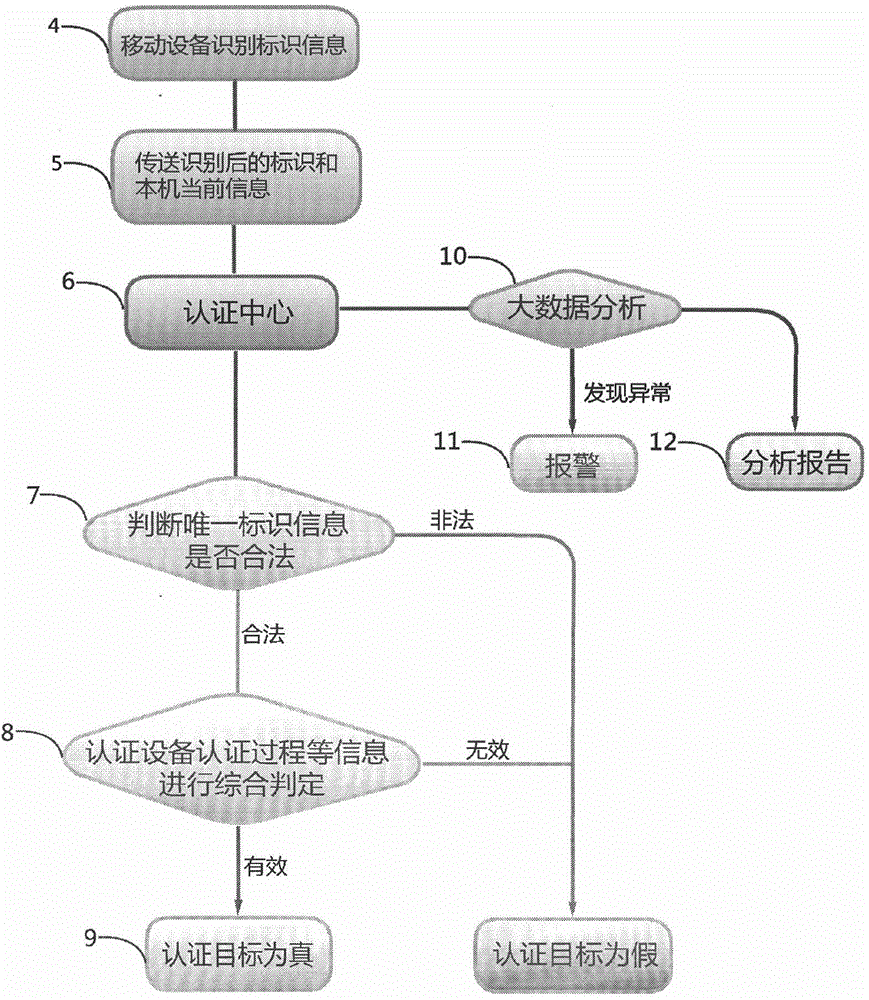
[0074] 4. The authenticator uses the camera of the mobile device (mobile phone, tablet, wearable smart device, etc.) to take pictures of the QR code printed on the authentication target (certified item) and read the unique identification information B;
[0075] 5. Send unique identification information B, authentication equipment information, and authentication process information to the authentication center;
[0076] 6. The certification center receives the information;
[0077] 7. The certification center...
Embodiment 2
[0085] This method is used to authenticate objects such as personnel. A mobile device and network-based method for target authentication through authentication identification and authentication behavior, comprising:
[0086] 1. Certification center
[0087] 2. The certification center generates unique identification information A;
[0088] 3. On the jewelry worn by the authentication target (certified person), use the NFC (near field communication technology) tag to record the unique identification information B, and the tag is implanted on the wearable jewelry. Can include but not limited to: mobile phones, bracelets, necklaces, rings, NFC cards, etc.;
[0089] 4. The authenticator uses the NFC (Near Field Communication Technology) device of the mobile device (mobile phone, tablet, wearable smart device, etc.) to read the jewelry worn by the authentication target (the authenticated person);
[0090] 5. The mobile device used for authentication transmits the read unique ide...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com