Data transmission method, system and device
A data transmission method and information transmission technology, which are applied in the field of responder client equipment and data transmission systems, and can solve problems such as heavy processing load of VPN servers.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0049] In this embodiment, the data transmission method provided by the embodiment of the present invention will be described from the perspective of the initiator client.
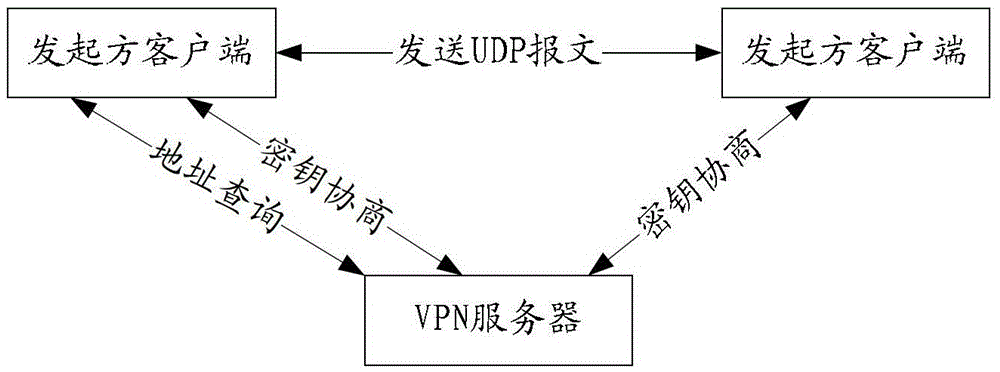
[0050] attached figure 1It is a schematic diagram of a VPN scenario applied in the embodiment of the present invention, including a client 1, a VPN server, and a client 2. It should be noted that the same client can act as the initiator in one communication process and as the initiator in another communication process. responding party. In this embodiment, the data transmission scheme is described by taking the client 1 as an initiator client and the client 2 as a responder client as an example.
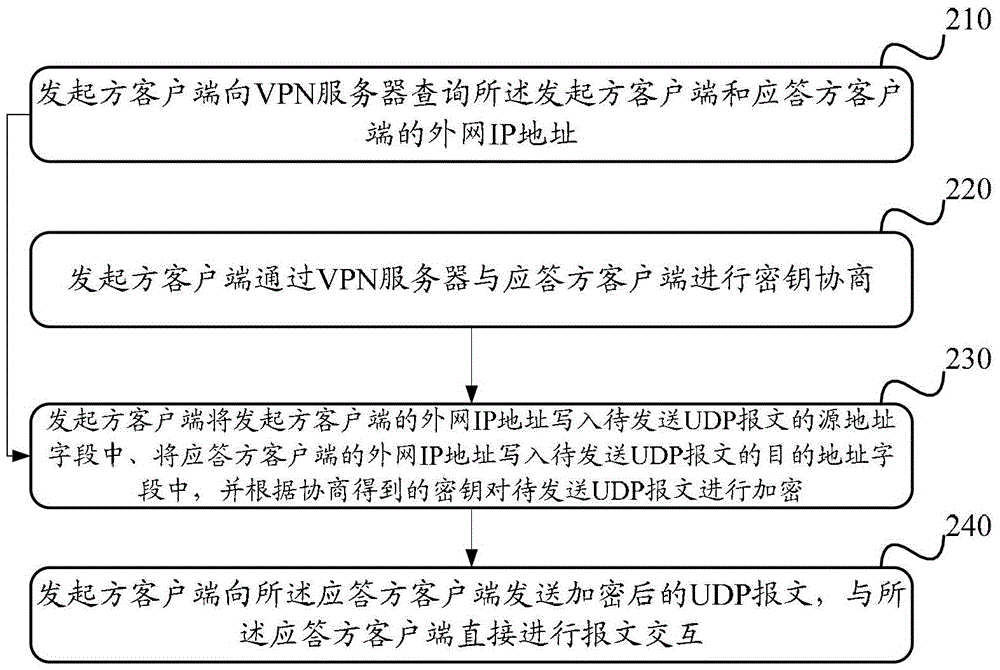
[0051] Such as figure 2 As shown, the flow of the data transmission method provided by the embodiment of the present invention is as follows:
[0052] Step 210, the initiator client queries the VPN server for the external network IP addresses of the initiator client and the responder client, and the external ...
Embodiment 2
[0071] The embodiment of the present invention describes the data transmission solution provided by the embodiment of the present invention from the perspective of the VPN server. Its application scene diagram is attached figure 1 shown.
[0072] attached Figure 4 It is a flow chart of the data transmission method provided by the embodiment of the present invention.
[0073] Step 410, the VPN server provides the initiating client and the responding client with the queried external IP addresses of the client according to the pre-stored external IP addresses of the clients.
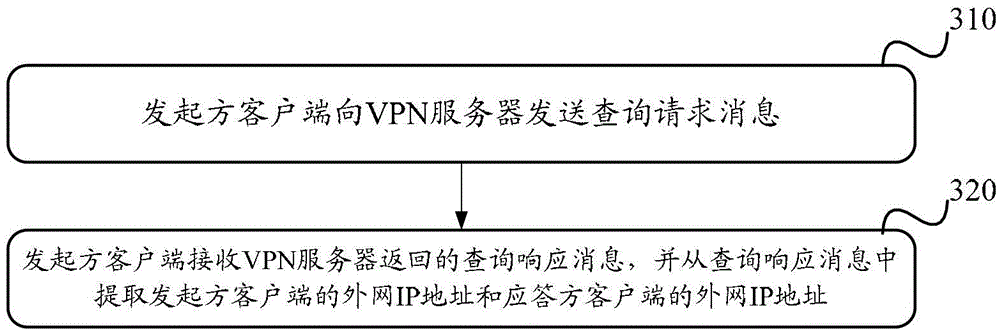
[0074] Optionally, as attached Figure 5 As shown, the VPN server provides the initiator client with the external network IP addresses of the initiator client and the responder client that are queried. The specific process includes:
[0075] Step 510, the VPN server receives the query request message sent by the initiator client, and extracts the ID of the initiator client and the ID of the responder c...
Embodiment 3
[0085] The embodiment of the present invention describes the data transmission solution provided by the embodiment of the present invention from the perspective of the responder client. Its application scene diagram is attached figure 1 shown.
[0086] attached Figure 6 It is a flow chart of the data transmission method provided by the embodiment of the present invention.
[0087] Step 610, the responder client performs key negotiation with the initiator client through the VPN server.
[0088] Optionally, during the key negotiation, what is negotiated may be a symmetric key, such as a key generated based on the DES algorithm, or an asymmetric key, which is not limited here.
[0089] Step 620, after the key negotiation is completed, the responder client extracts the external network IP addresses of the initiator client and the responder client from the received UDP message sent by the initiator client.
[0090] After receiving the UDP packet sent by the initiator client, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com