Power information system anti-violation outreach device
A power information and outreach technology, applied in the protection of internal/peripheral computer components, platform integrity maintenance, etc., can solve problems such as forgetting and losing lock keys, troublesome carrying keys, and failure of computer managers to open them, so as to ensure safety, The effect of safe and reliable control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
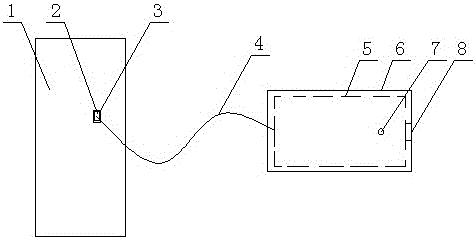
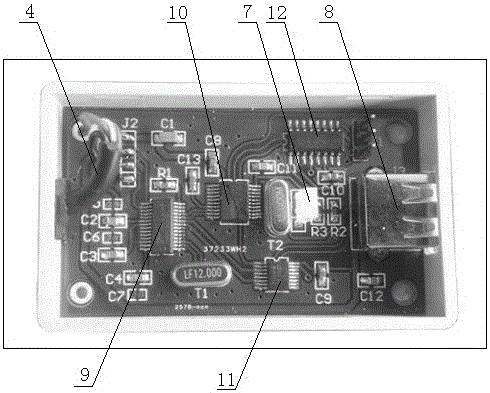
[0026] Such as Figure 1-Figure 5 As shown, a power information system anti-violation outreach device includes a hardware part and a software part. The hardware part includes a box body 6 and a control circuit board 5 arranged in the box body 6. The control circuit board 5 A USB socket 8 and a data line 4 leading out of the box body are connected, and the data line 4 is connected with the computer 1 through the data interface 2; the software part includes an anti-violation external device hardware driver installed on the computer 1 Program 13 and Management Control Program 14.
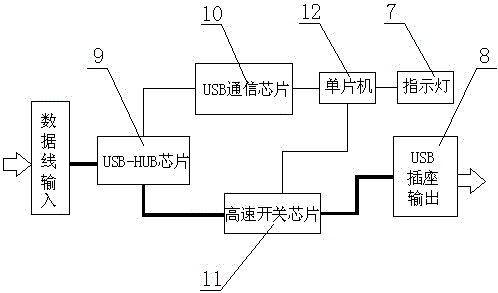
[0027] As an optimized solution of the present invention, the control circuit board 5 includes a USB-HUB chip 9 and a high-speed switch chip 11 connected in sequence, the USB-HUB chip 9 is connected to the data line 4, and the high-speed switch chip 11 is connected to the data line 4. The USB socket 8 is connected, and the USB-HUB chip 9 is also connected with a USB communication chip 10 , and the USB...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com