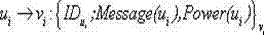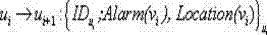Novel method for detecting Sybil attack in Internet of Things
A new method, the technology of the Internet of Things, applied in the direction of electrical components, sustainable buildings, transmission systems, etc., to achieve the effect of reducing energy consumption, reducing energy consumption, and improving safety performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
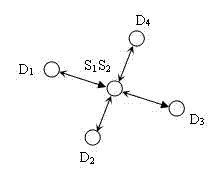
[0027] According to the signal strength of the receiving node to calculate the position of the node, it can be judged whether a Sybil attack has occurred in the Internet of Things. Assume the following network environment: a two-dimensional flat cluster head network; all nodes have the same initial energy, computing power, and communication capabilities; once the node is deployed, its position is fixed; the network is safe before the node initialization is completed . The following describes the detection method of Sybil attack.
[0028] In the Jakes channel space of the Internet of Things, the signal strength received by the receiving antenna is the transmit-receive distance d function, the received signal strength of the node is:
[0029] (1)
[0030] In the formula, is the transmitted signal strength ( ), assuming that the transmit and receive antenna gains are both 1, is the channel gain following the Rayleigh distribution, H is the impulse r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com