Dependable security cloud computing composition method
A trusted computing and trusted cloud technology, applied in electrical components, user identity/authority verification, transmission systems, etc., can solve problems such as being unable to adapt to cloud computing without borders
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
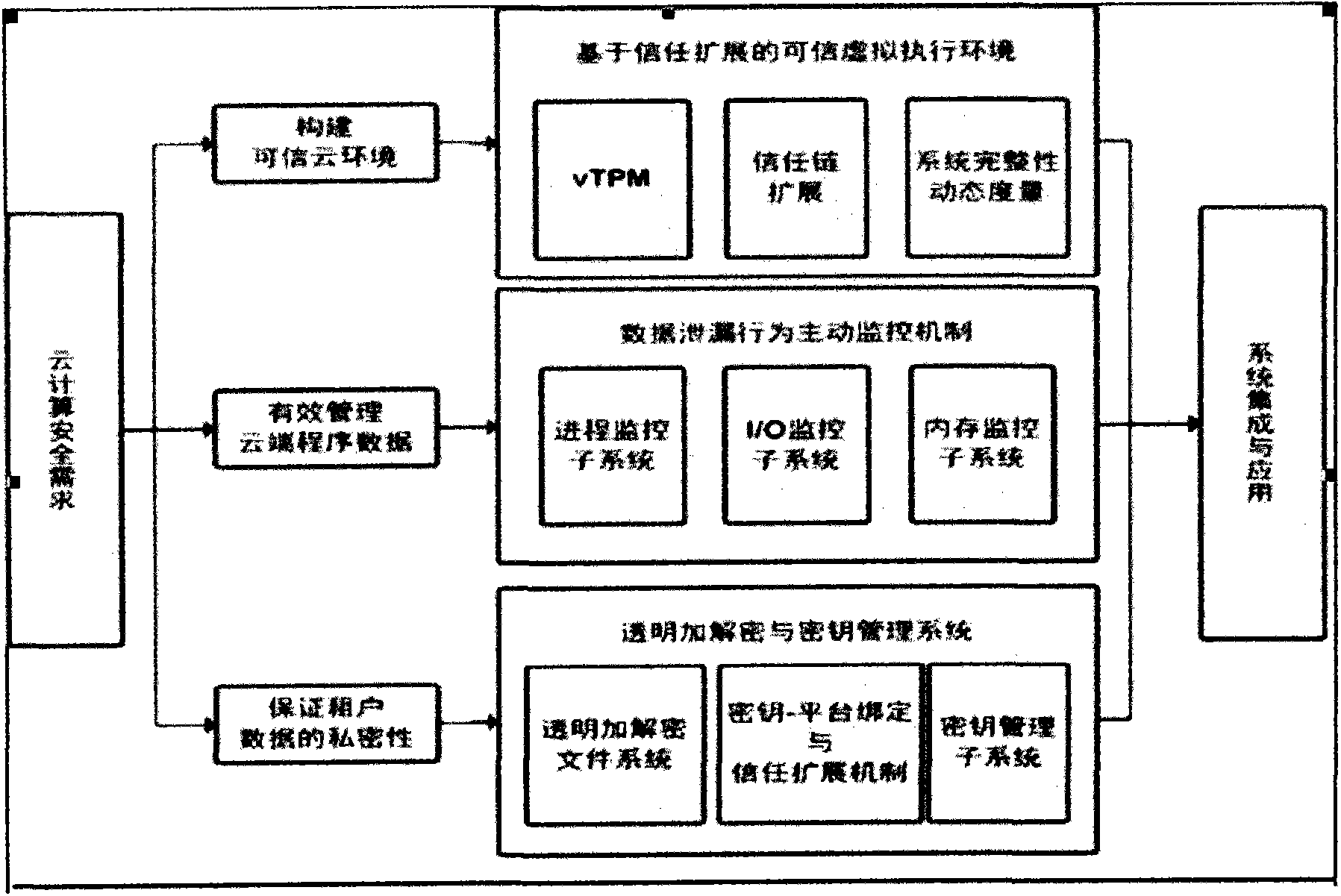
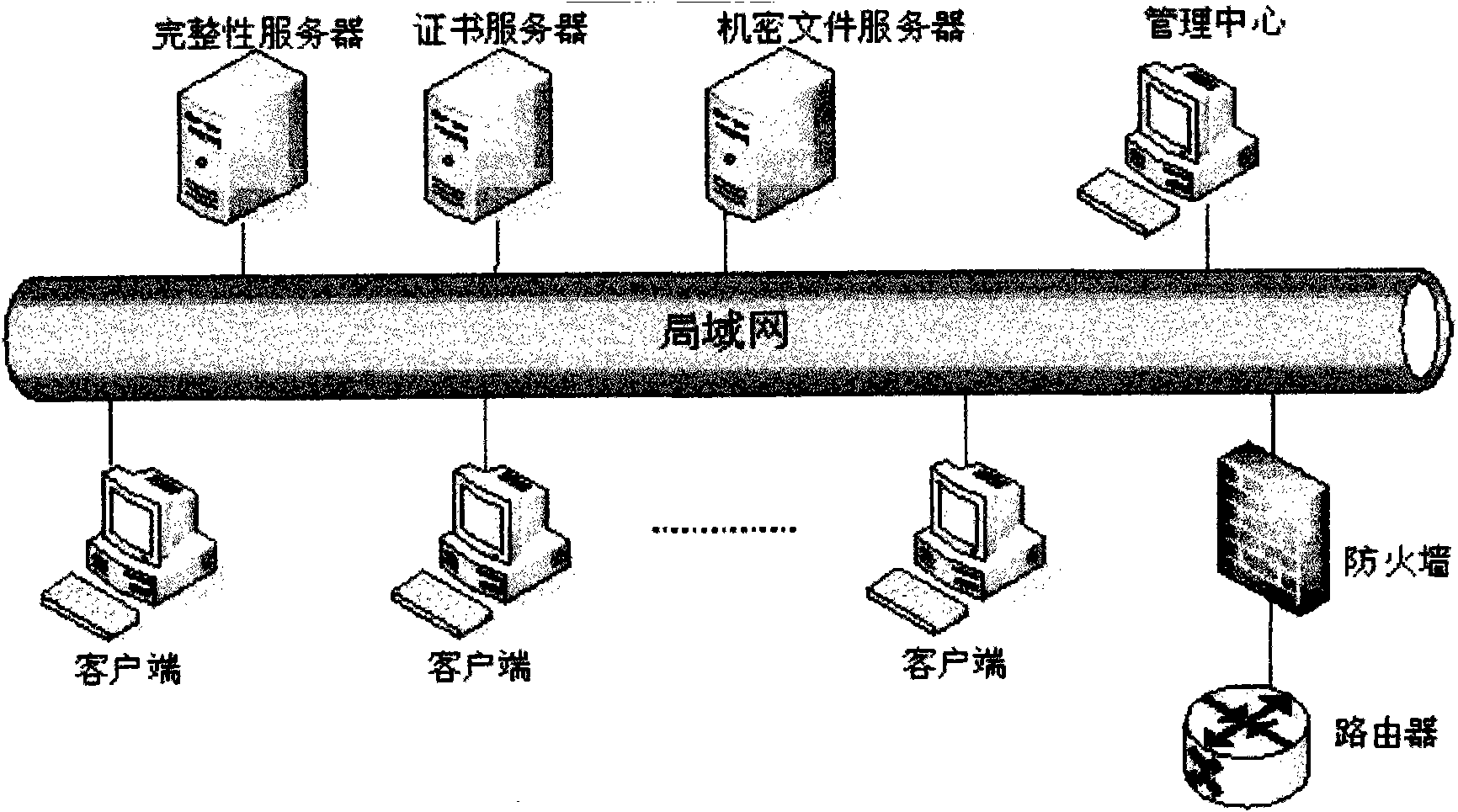
[0007] 1. System components.
[0008] 1. Development of isolation machine based on virtual machine: the VMM layer runs directly on the hardware layer, and each guest operating system runs on the VMM layer. Multiple guest virtual machines with their own operating systems and applications.
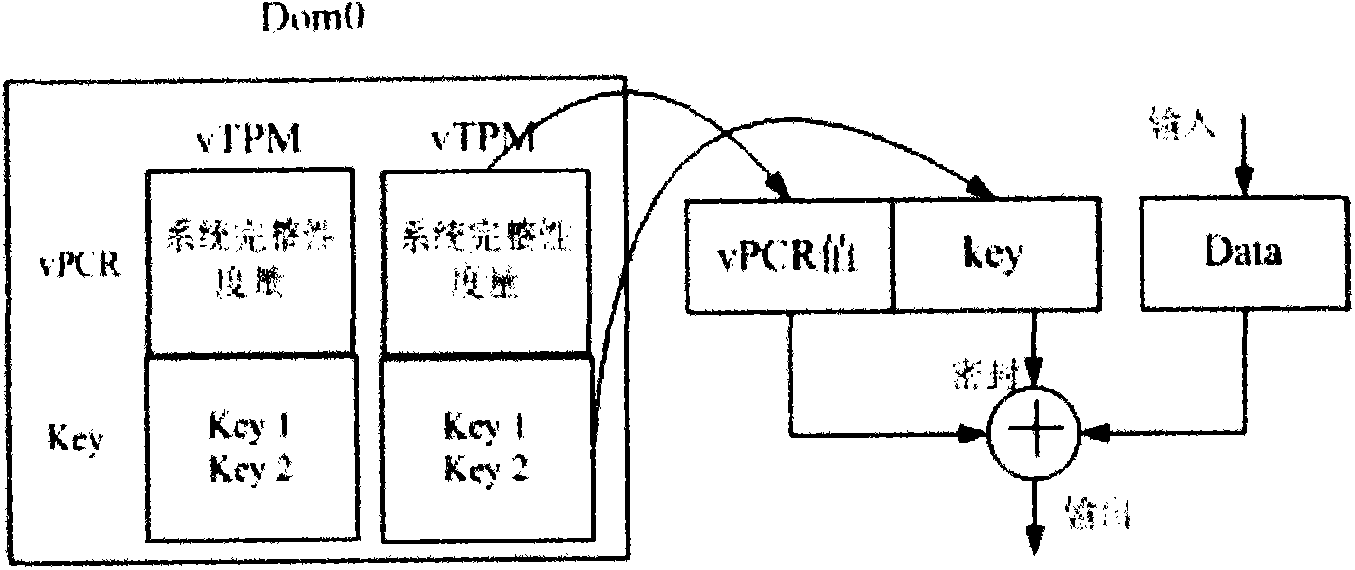
[0009] 2. Remote platform authentication and identity management based on TPCM or TPM: replace the unique endorsement key EK of TPCM with the identity certificate key AIK to sign the platform configuration register PCR, and provide the service provider with the identity certificate of the platform. One TPCM or TPM can have multiple AIKs. The process of issuing a virtual platform identity key AIK certificate for the TPM:
[0010] ①The physical TPCM first generates an AIK, which is a 2048-bit RSA key pair.
[0011] ②The physical platform requests the AIK certificate from a certificate server, and the request includes the AIK public key, the certificate of the cryptographic module key EK and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com