Safe E-bank implementation method
An implementation method and safety net technology, which is applied in the field of secure transfer system and e-commerce payment, can solve the problems of stealing and misappropriating private keys and digital certificates in USBKEY, and achieve the effect of increasing security, making small changes and achieving great results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
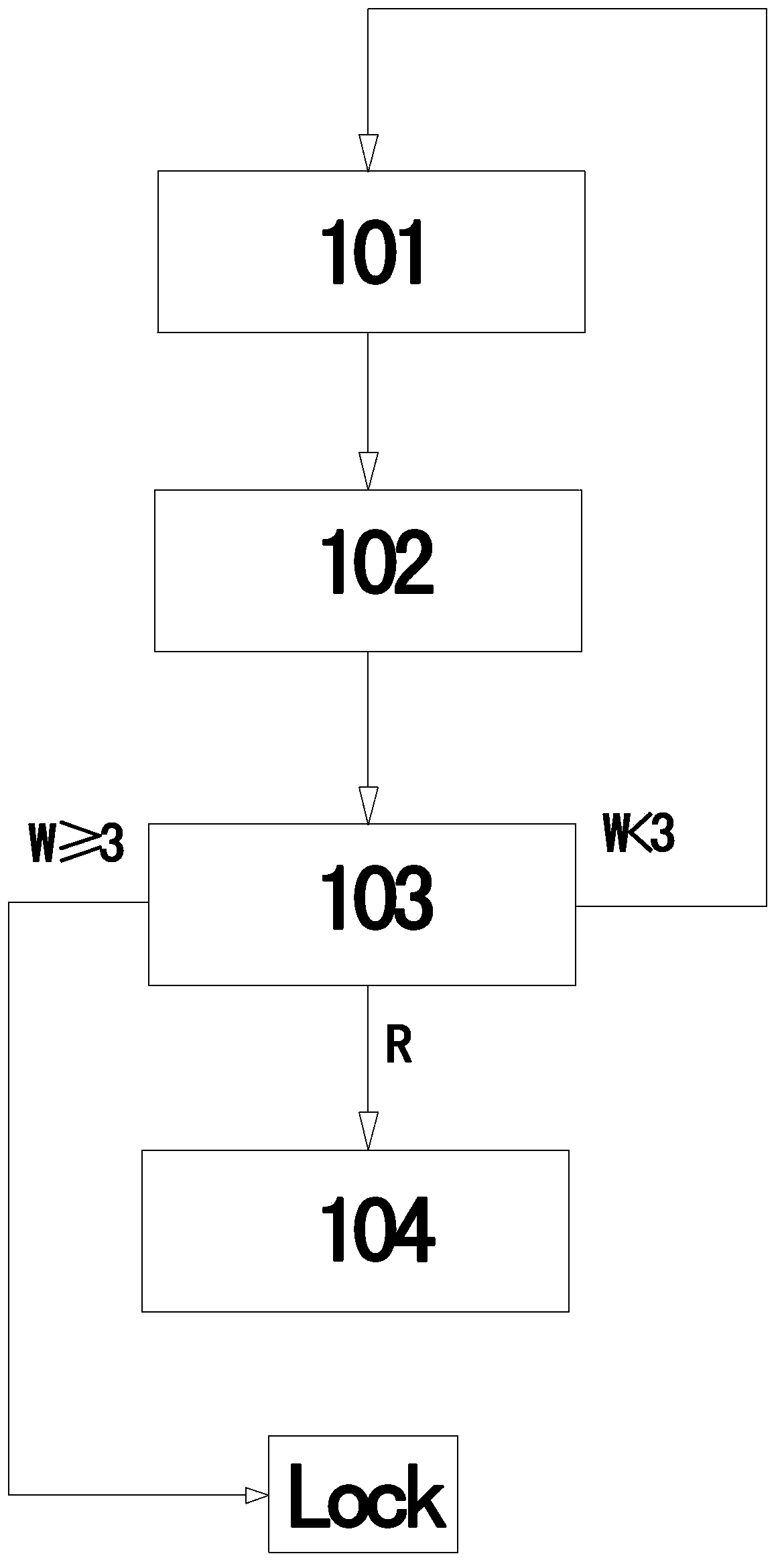
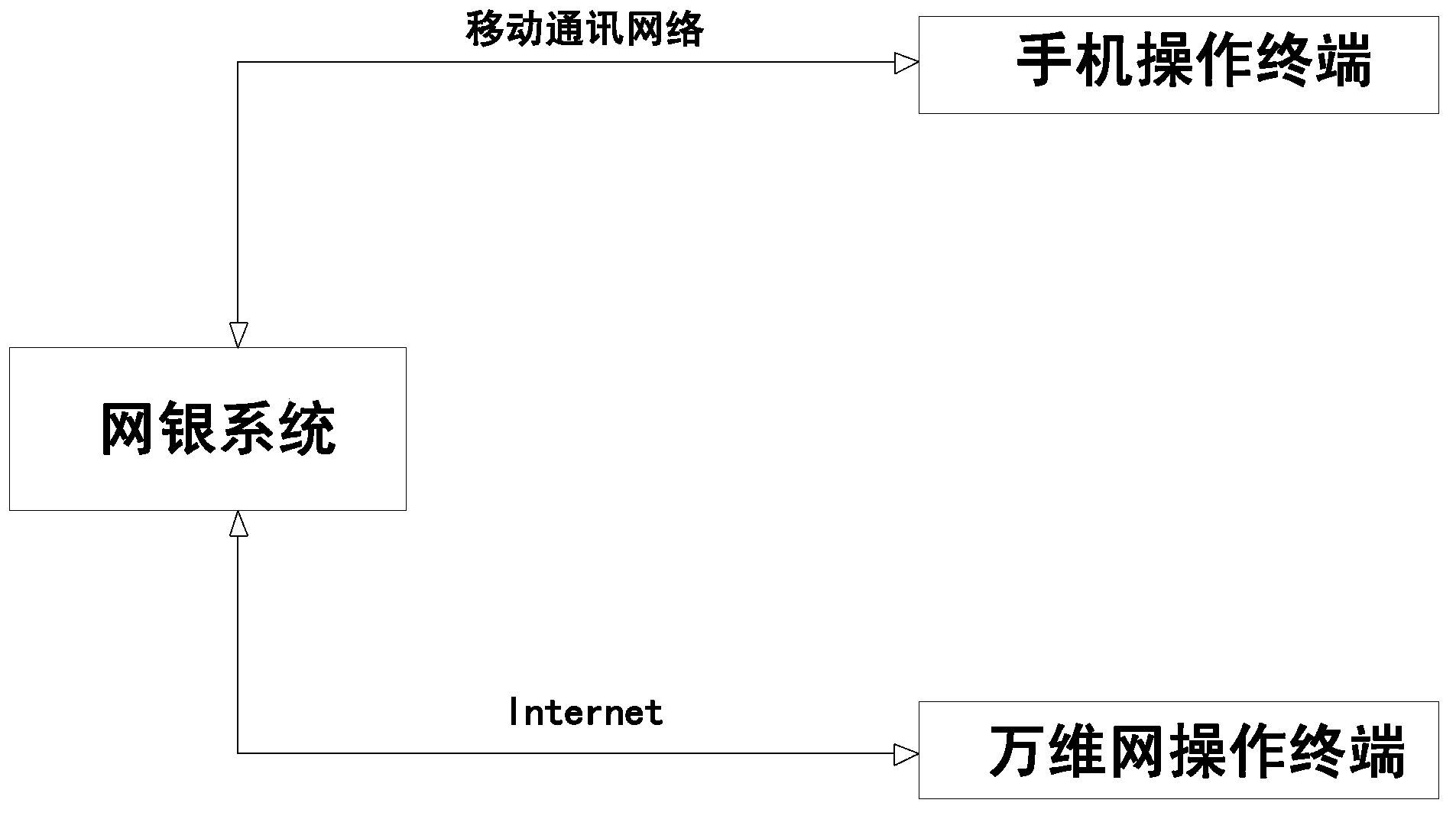
[0019] Such as figure 1 , 2 As shown, an implementation method of secure online banking combined with a mobile terminal, the specific implementation steps are as follows:
[0020] 101: The user enters the personal account number and network login password (or dynamic password) through the Internet;
[0021] 102: After receiving the user's input of the network login password, the online banking system automatically sends a randomly generated dynamic mobile phone login password to the user's registered mobile phone number;
[0022] 103: The user logs in to the online banking client through the mobile phone, enters the received dynamic mobile phone login password, and the system verifies that the mobile phone login password and the mobile phone number that sent the mobile phone login password are correct, then successfully logs in to the online banking transaction interface and enters step 104; If the login password or the mobile phone number sending the mobile login password i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com