Man-machine identification method and system
A human-machine identification and user technology, applied in the computer field, can solve the problem of character recognition but cannot prevent computer programs, sound CAPTCHA attacks, machine learning algorithm attacks, etc., to prevent single point failures and internal attacks, improve security, and guarantee safe effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
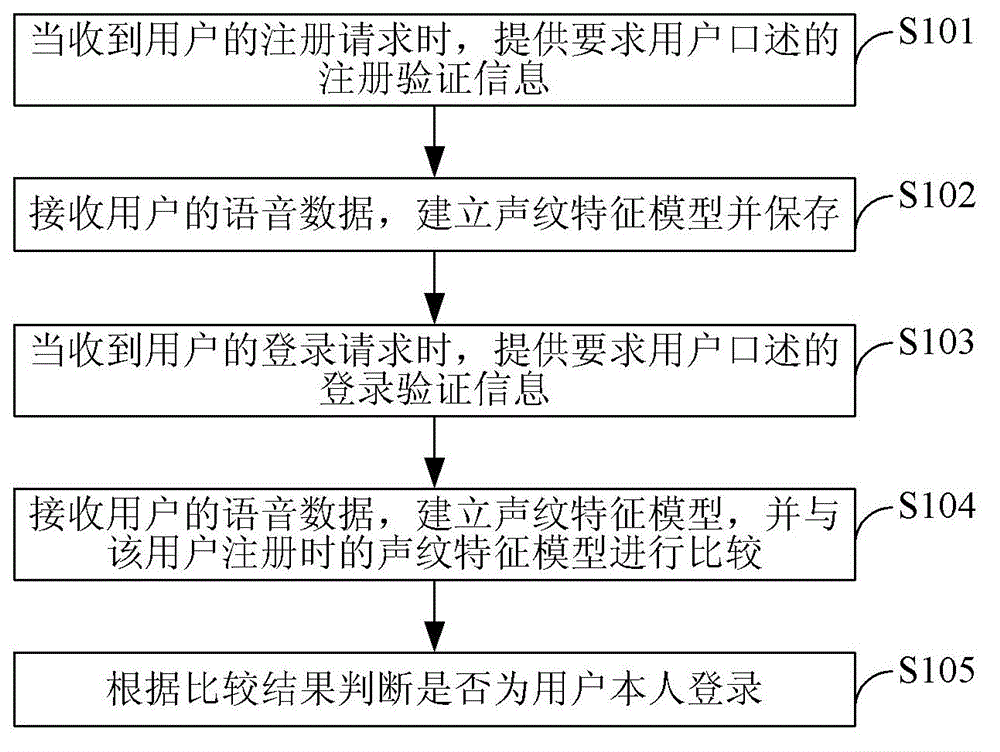
[0073] Embodiment one, a method of human-machine identification, such as figure 1 Shown, including:
[0074] S101. When receiving a registration request from a user, provide registration verification information that the user is required to dictate;
[0075] S102: Receive the user's voice data, establish a voiceprint feature model and save it;
[0076] S103. When receiving the user's login request, provide the login verification information that the user is required to dictate;
[0077] S104: Receive the user's voice data, establish a voiceprint feature model, and compare it with the voiceprint feature model when the user registers;
[0078] S105: Determine whether it is the user who logs in according to the comparison result.
[0079] This embodiment combines voiceprint recognition and human-machine recognition technology, which can improve the reliability and accuracy of recognition. Voiceprint recognition is a type of biometric technology. It is a technology that automatically recogn...
other Embodiment approach
[0122] In other embodiments, text-related (that is, the login verification information and the registration verification information are completely the same) or text-independent (that is, the login verification information and the registration verification information are completely different) may also be used for voiceprint recognition.
[0123] In an implementation manner of this embodiment, after receiving the user's registration request, it may further include:
[0124] Save the password entered by the user;
[0125] Before step S105, it may further include:
[0126] Receive the password entered by the user and compare it with the password entered when the user registered.
[0127] Step S105 may specifically include:
[0128] If the voiceprint feature model matches the voiceprint feature model and the password, it is determined that the user is logged in; otherwise, it is determined that the user is not logged in.
[0129] In this embodiment, the manual input of the password can ensur...
Embodiment 2
[0148] Embodiment two, a human-machine identification system, such as Figure 7 Shown, including:
[0149] Voiceprint feature model establishment module 21;
[0150] The voiceprint identity registration module 22 is used to provide registration verification information that requires the user to dictate when a user's registration request is received; to receive the user's voice data, instruct the voiceprint feature model establishment module 21 to establish a voiceprint feature model, and save The established voiceprint feature model;
[0151] The voiceprint identity verification module 23 is used to provide the user's dictated login verification information when receiving the user's login request; receive the user's voice data, instruct the voiceprint feature model establishment module 21 to establish a voiceprint feature model, and Compare the established voiceprint feature model with the voiceprint feature model when the user registered;
[0152] The human-machine recognition evalu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com