Password cracking method, device and system
A password and location-specific technology, applied in the field of information security, can solve the problems of high real-time requirements for password cracking, password cracking, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
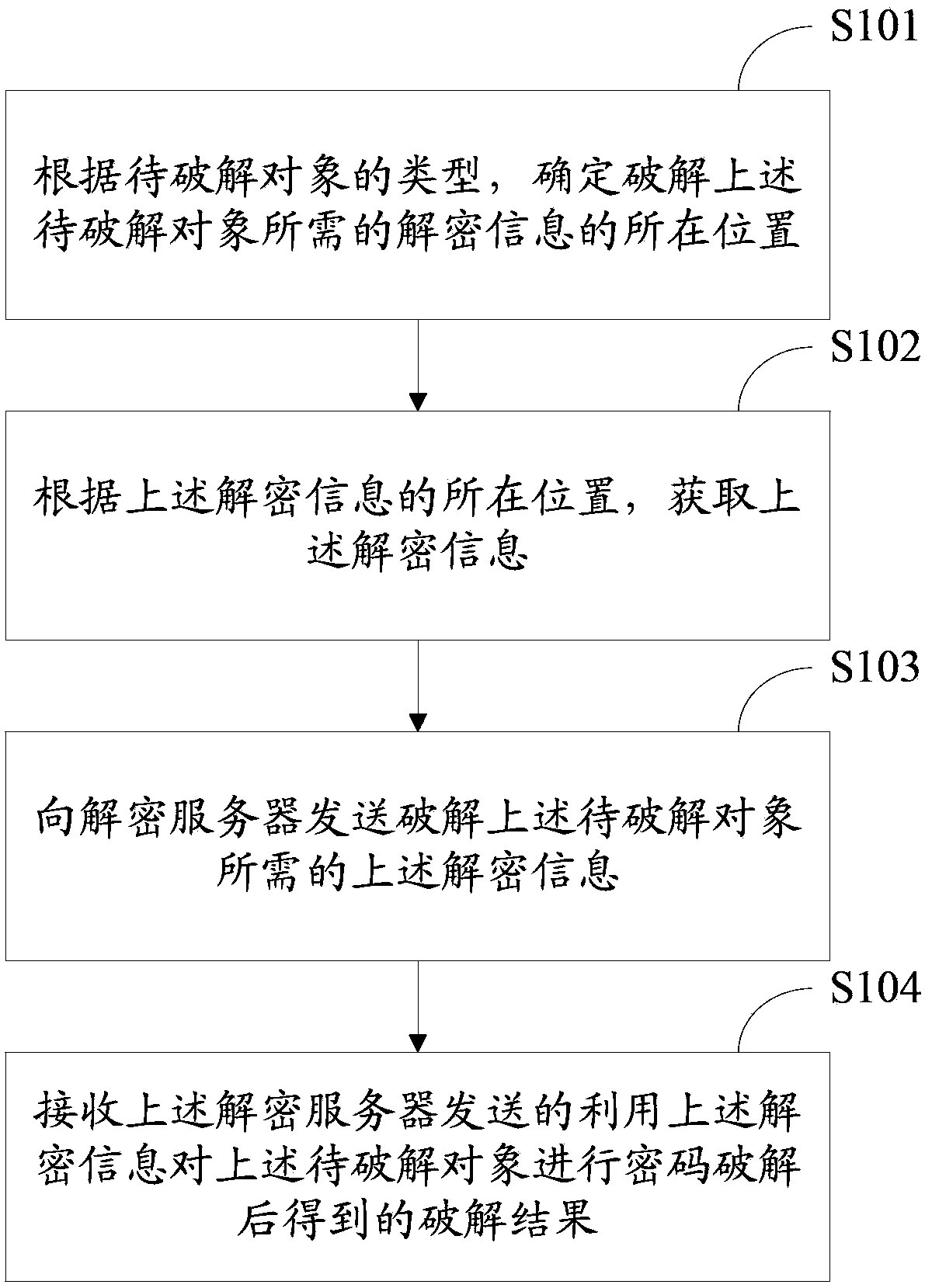
[0056] A password cracking method provided by Embodiment 1 of the present invention is applied to the client side, such as image 3 As shown, it specifically includes the following steps:
[0057] S301. According to the type of the object to be cracked, determine a location of decryption information required to crack the object to be cracked, where the location of the decryption information corresponds to the type.
[0058] In this step, the decryption information can be key information, for example, key hash value, key verification data of instant messaging software or email, encrypted data packet or key handshake data of wireless network, etc.; decryption information can also include encrypted Key information and decryption auxiliary information, such as key information and user name information related to the key information, and other decryption auxiliary information.
[0059] In this step, the object to be cracked may be an operating system login password to be cracked, ...
Embodiment 2
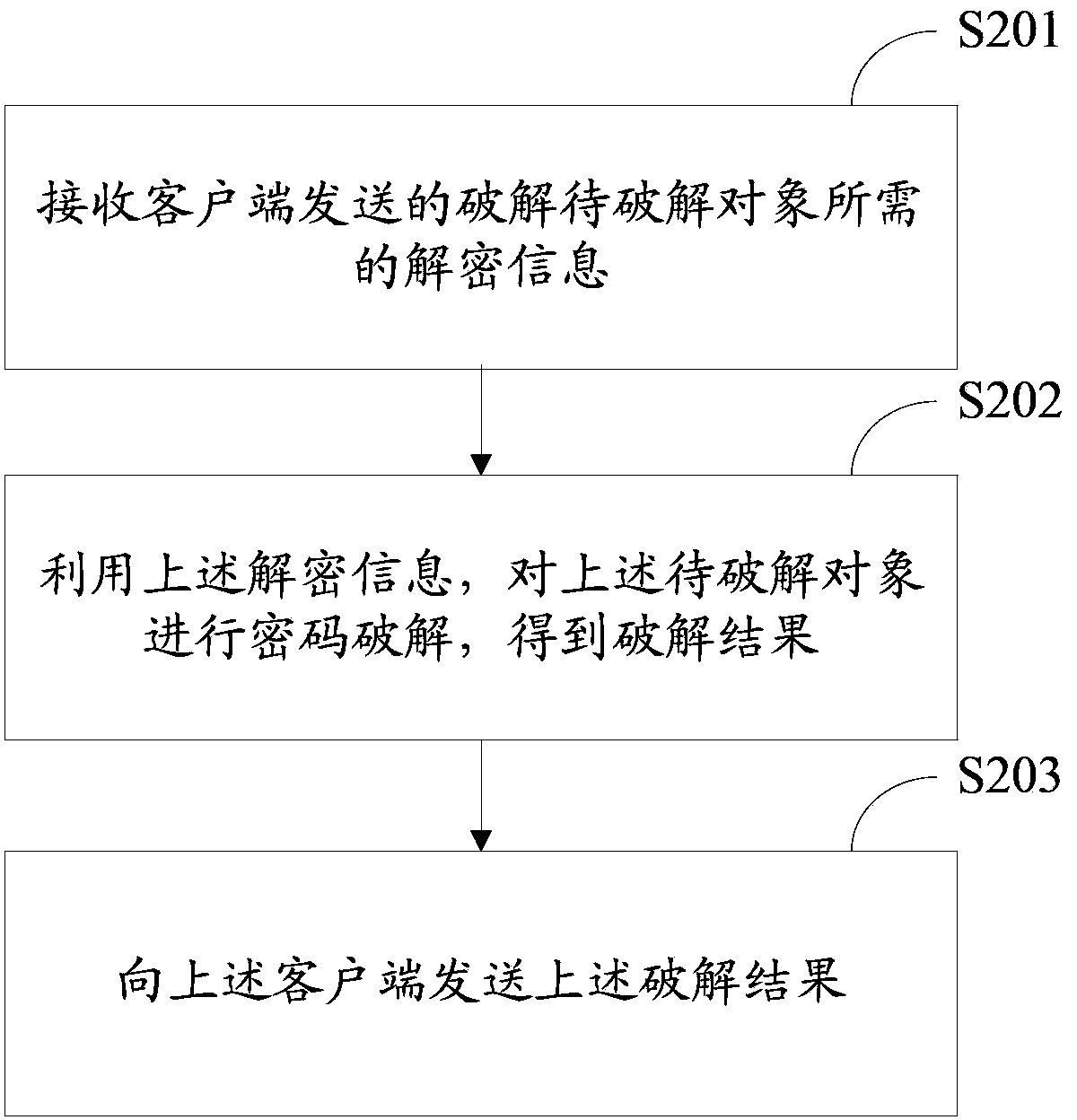
[0076] with the above image 3 Corresponding to the shown method, a password cracking method provided in Embodiment 2 of the present invention is applied to the decryption server side, such as Figure 4 As shown, it specifically includes the following steps:
[0077] S401. Receive the decryption information required for cracking the object to be cracked sent by the client.
[0078] In this step, the decrypted information may be received through a safe and reliable data link according to actual needs.
[0079] S402. Using the above decryption information, perform password cracking on the object to be cracked, and obtain a cracking result.
[0080] Further, in this step, the decryption server may be a decryption server specially designed for the type of object to be cracked, or a decryption server capable of cracking multiple types of objects to be cracked, if the decryption server is capable of cracking for A decryption server that cracks various types of objects to be crack...
Embodiment 3
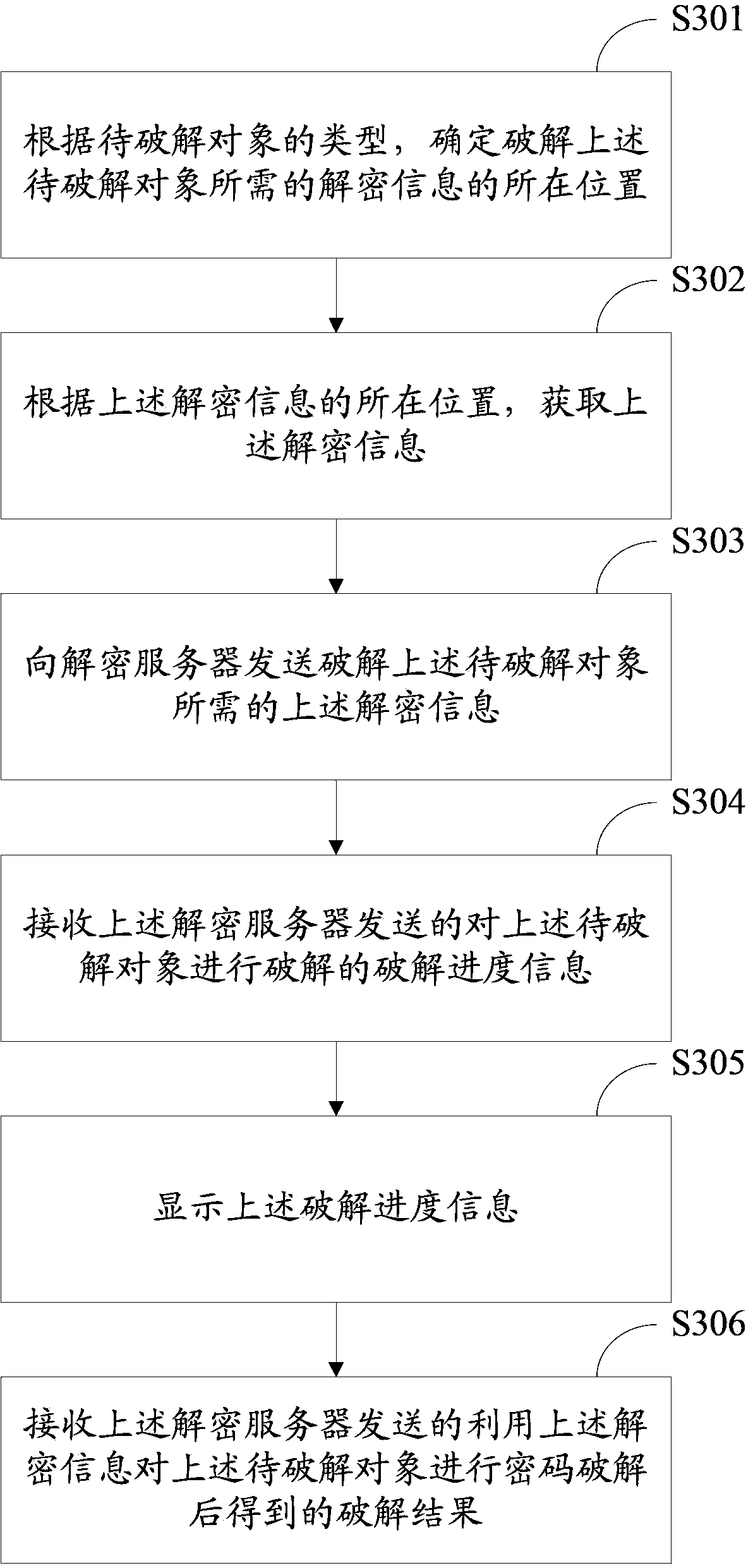
[0086] A password cracking method provided by Embodiment 3 of the present invention is applied to the client side, such as Figure 5 As shown, it specifically includes the following steps:
[0087] S501. According to the type of the object to be cracked, determine a location of decryption information required to crack the object to be cracked, where the location of the decryption information corresponds to the type.
[0088] S502. Acquire the decrypted information according to the location of the decrypted information.
[0089] S503. Send the decryption information required to decrypt the object to be decrypted to the decryption server.
[0090] S504. Receive the remaining cracking time for cracking the object to be cracked sent by the decryption server.
[0091] S505. Displaying the remaining duration of cracking.
[0092] S506. Determine whether cracking is completed; if yes, go to step S510; if not, go to step S507.
[0093] S507. Determine whether the remaining crackin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com