Method and system for correlation analysis of security events
A security event and correlation analysis technology, applied in the field of network security, can solve problems such as failure to trigger, inversion, misreporting or omission of correlation analysis engine, etc., to avoid distortion problems, meet accuracy requirements, and improve accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The technical solutions of the present invention will be described in further detail below with reference to the accompanying drawings and embodiments.
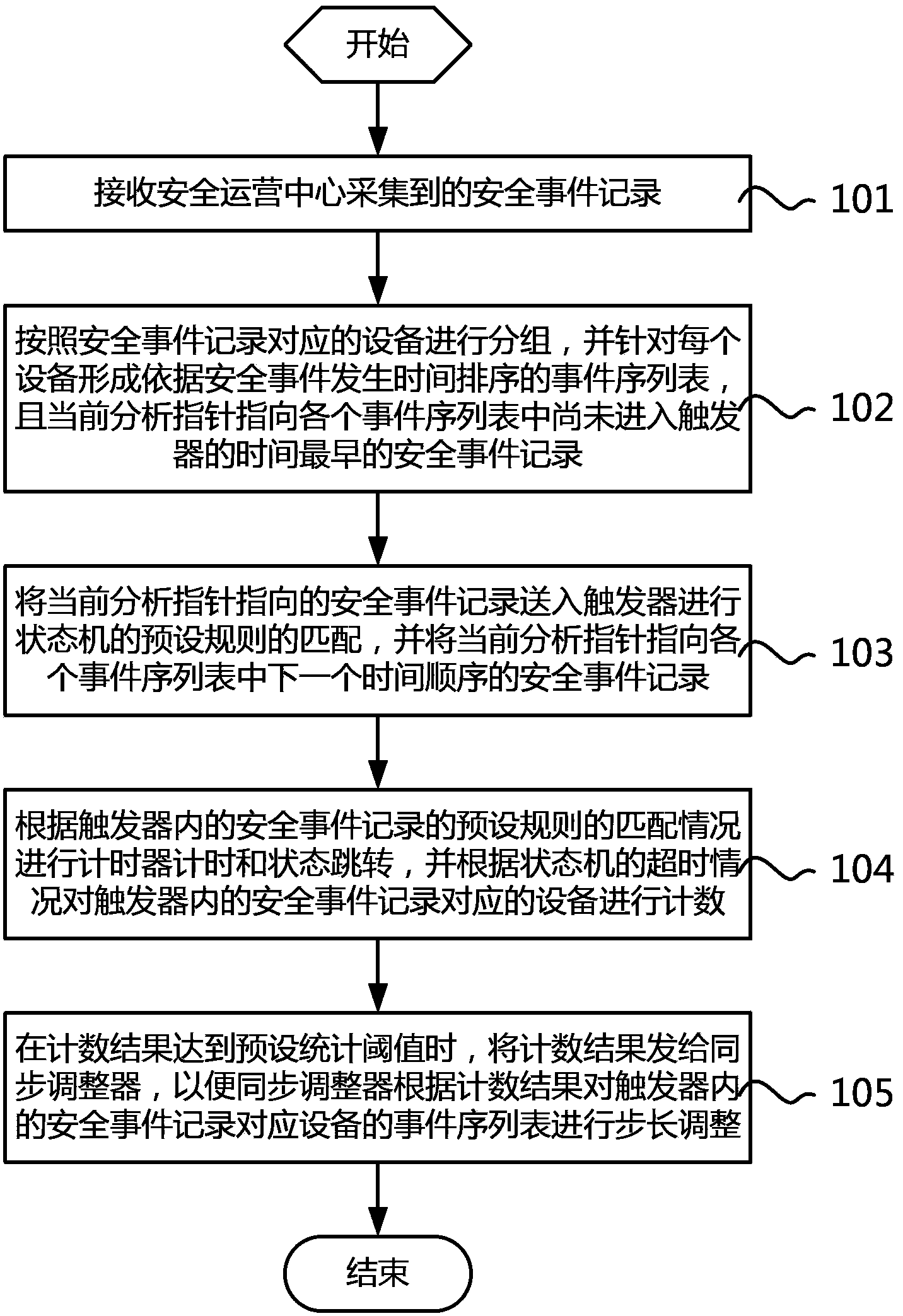
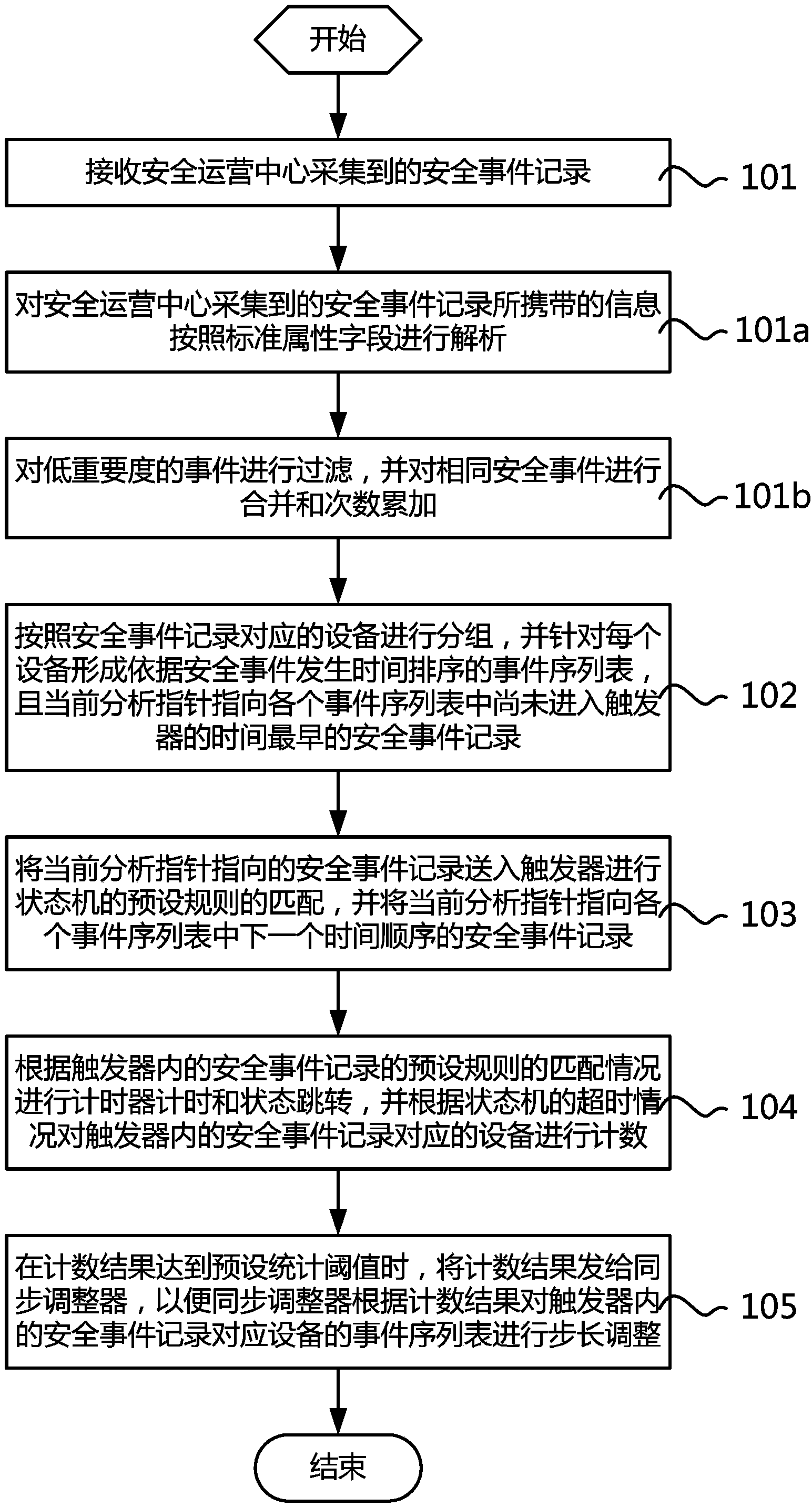
[0054] like figure 1 As shown, it is a schematic flowchart of an embodiment of the security event correlation analysis method of the present invention. In this embodiment, the security event correlation analysis process includes:
[0055] Step 101, receiving the security event records collected by the security operation center;
[0056] Step 102: Group the devices corresponding to the security event records into groups, and form an event sequence list sorted according to the occurrence time of the security event for each device, and the current analysis pointer points to the earliest time in each event sequence list that has not yet entered the trigger. security incident records;
[0057] Step 103, sending the security event record pointed to by the current analysis pointer into the trigger to match the preset rules...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com