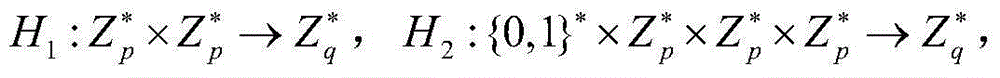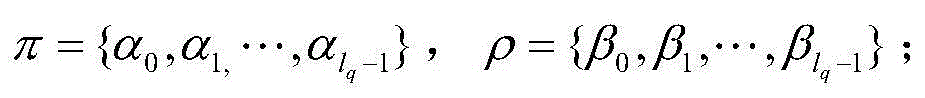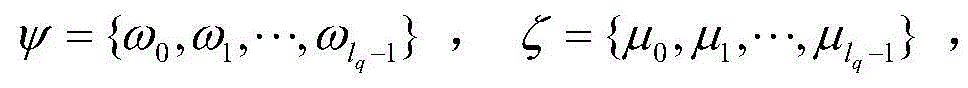Anonymous untraceable RFID mutual authentication method
A technology of mutual authentication and multiplication group, applied in the field of RFID mutual authentication technology, can solve problems such as unspecified implementation methods, inconformity with the low-cost requirements of RFID tags, and high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The symbols used in the examples are as follows:
[0024]
[0025]
[0026] The mutual authentication process of the present invention is roughly as follows:
[0027] System initialization: The issuer generates the public-private key pair of the reader, the public-private key pair of the tag and two secure hash functions. The background database connected with the reader stores the public key lists of all legal tags.
[0028] RFID Mutual Authentication Step: The reader sends a message to the tag. The tag uses its own private key and its own identity information to calculate the response value through simple multiplication and addition operations, and then sends the response value to the reader for authentication. The reader uses the tag public key to verify the response value. If the verification is passed, it means that the tag is legal; otherwise, it means that the tag is illegal. After the tag is verified to be legal, the reader uses its own private key to c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com