Method and system for two-factor mutual authentication
A two-way authentication and two-factor technology, applied in the field of network communication, can solve the problems of incorrect downloading of the client, difficulty in plug-in deployment, and incorrect execution, etc., and achieves the effects of wide application range, improved security performance, and simple design
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
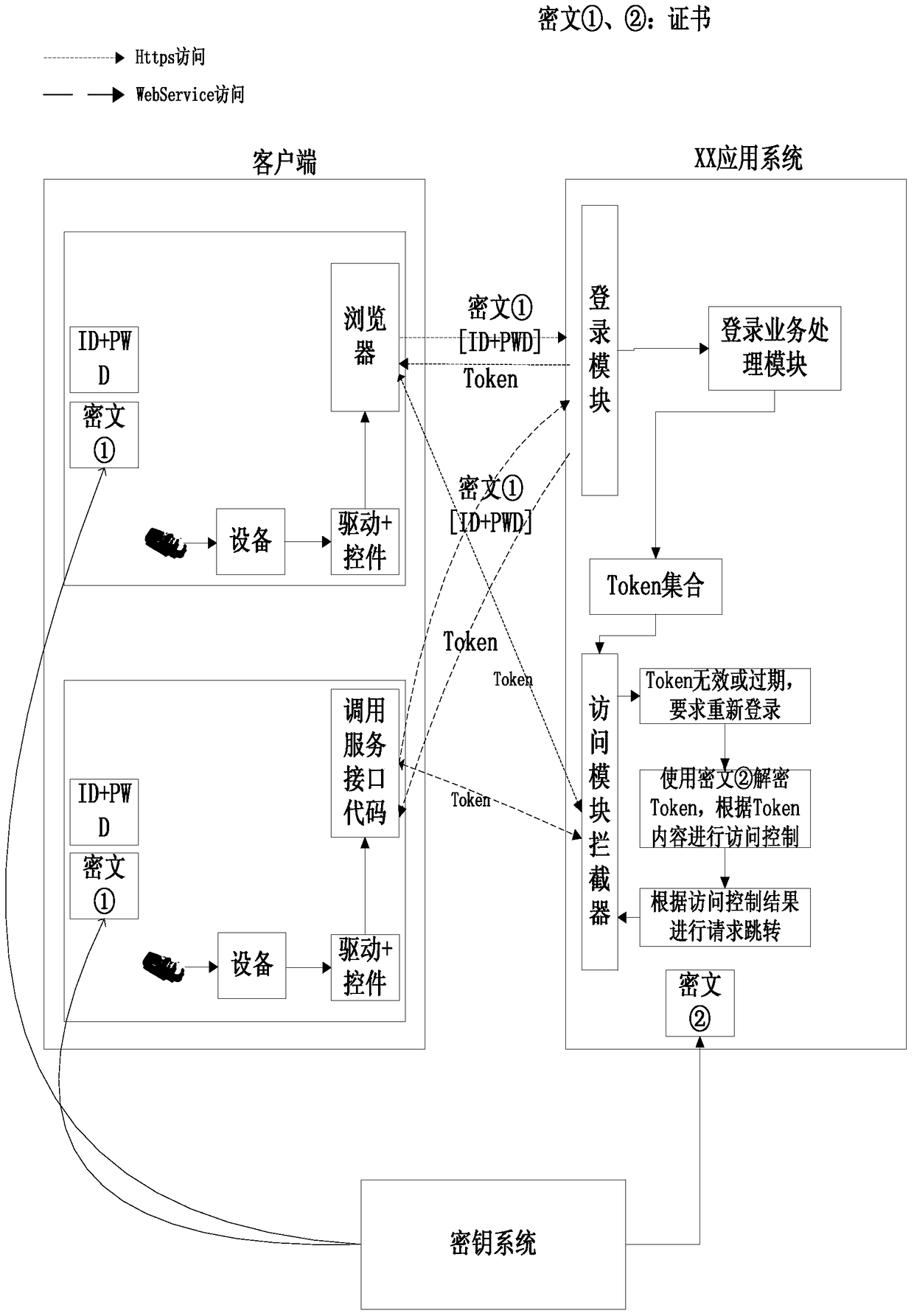
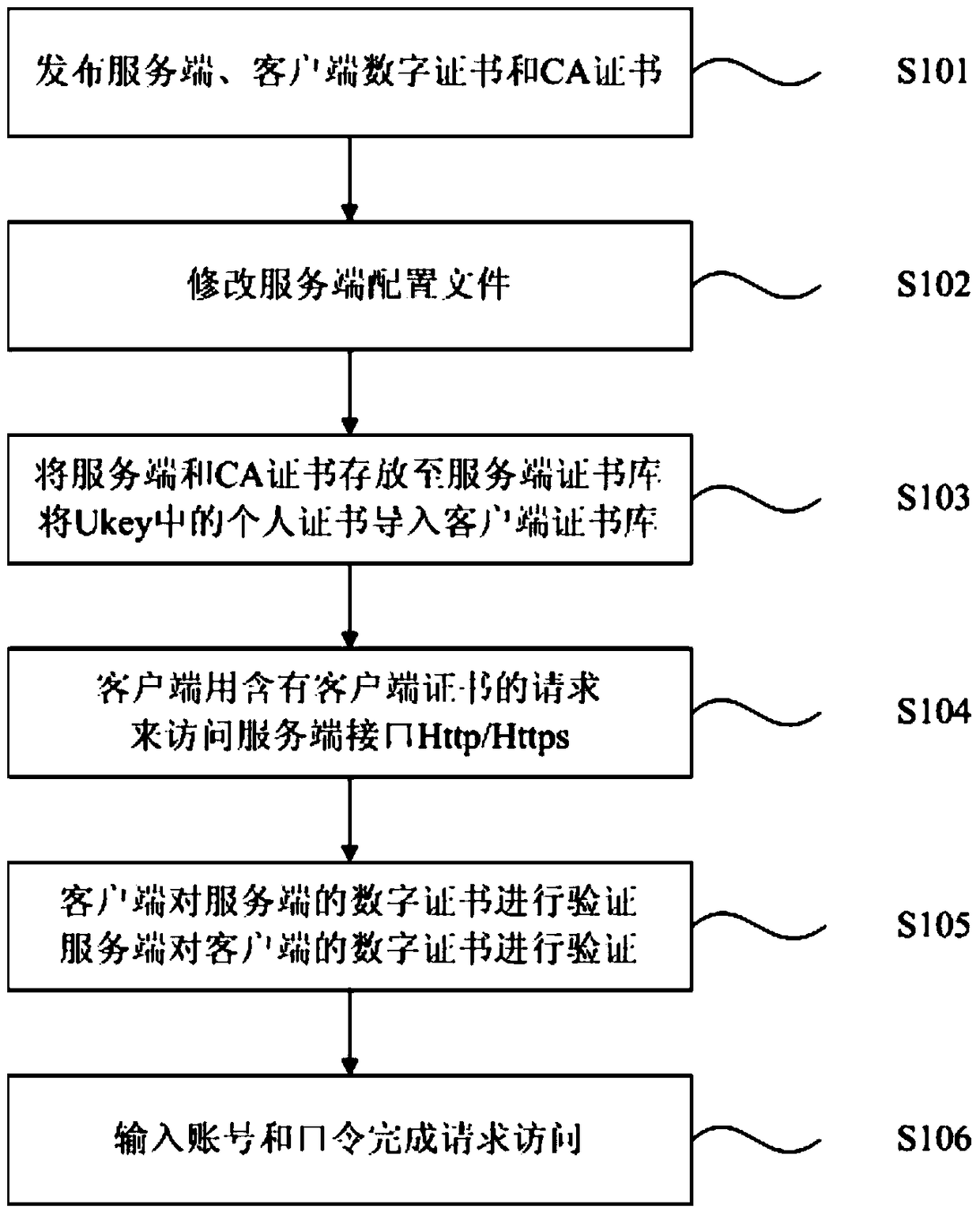
[0070] Generate a certificate library through conventional certificate generation tool software, such as KeyTool and OpenSSL1.0.1g. The personal certificate of the client in the certificate store can be stored in the personal Ukey to achieve the purpose of protecting the personal certificate and identifying the identity of the user. Because Tomcat is an open source and free server, the following server uses Tomcat7 as an example to explain the two-way authentication process of accessing the Http / Https interface of the server through the two factors of account password and digital certificate stored in Ukey;
[0071] Such as figure 1 As shown, the system and its components involved in this embodiment are as follows:
[0072] (1) The key system is used to issue the client personal certificate, the server certificate, the CA certificate used for signing when making the digital certificate, etc., which is realized by using a conventional certificate generation tool;
[0073] (2)...
Embodiment 2
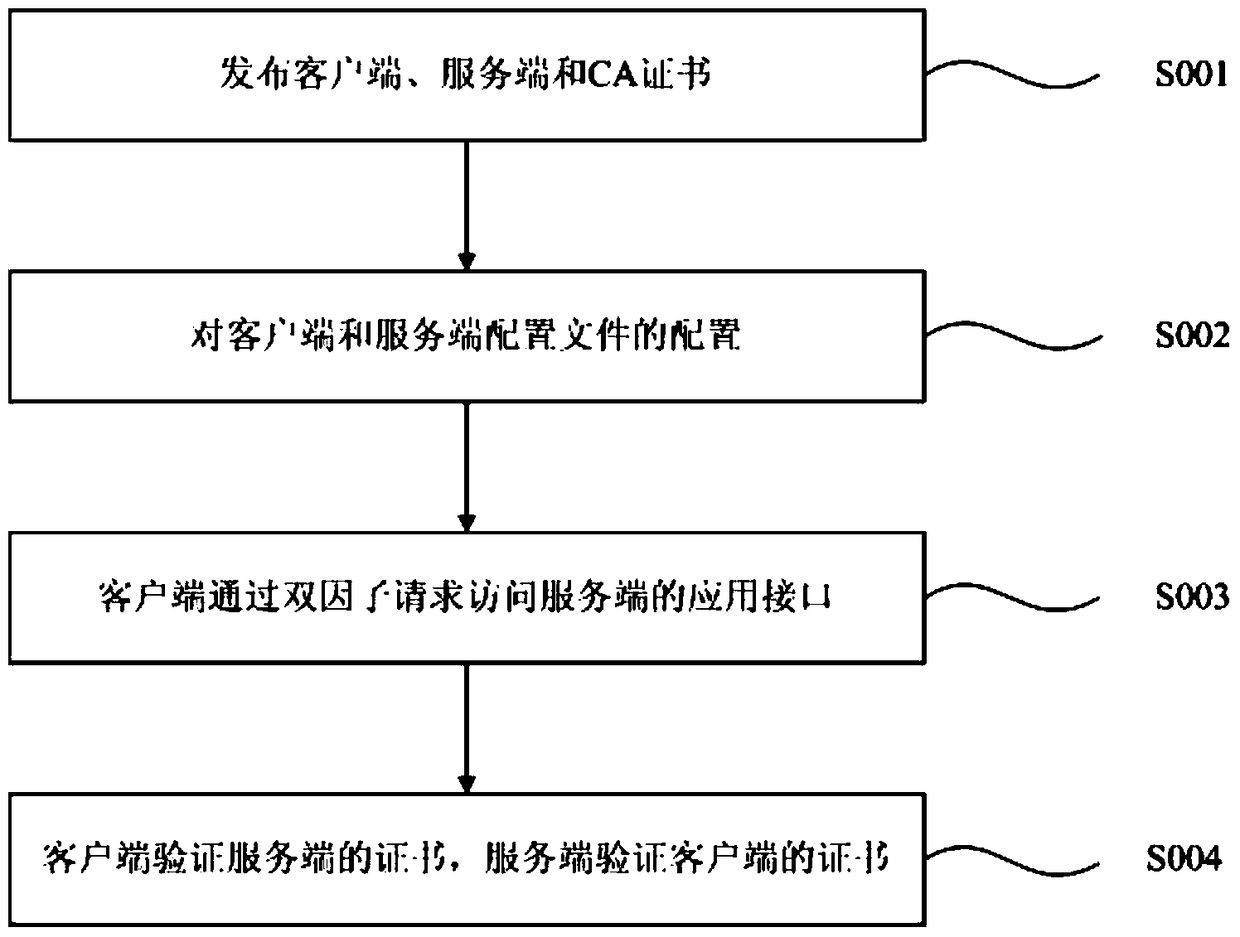
[0110] Combine below Figure 4 Explain the two-way authentication process of accessing the Web Service interface of the server through the account password and the digital certificate stored in Ukey. The specific content such as configuration of Https and certificate issuance that are the same as those in Embodiment 1 will not be described repeatedly, and only the content that is different from it will be described here. In this embodiment, the configuration of the configuration files of the Web Service server and client is mainly implemented through the Apache Rampart framework. Configure the Rampart framework to support digital certificates. Such as Figure 4 As shown, the specific authentication process in this embodiment is as follows:
[0111] Step S201: Publish the digital certificates and CA certificates of the server and client;
[0112] Step S202: Configure the Https interface on the server, specifically configure the server port, certificate store, certificate ty...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com