Mobile terminal identity authentication method and system based on wpki and time stamp
An identity authentication, mobile terminal technology, applied in user identity/authority verification, transmission systems, electrical components, etc., can solve the security threat of RSA algorithm, and achieve the effect of effective identity verification, defense against attacks, and data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0052] In the embodiment of the present invention, the user terminal obtains the time stamp from the time stamp mechanism system, and uses WPKI to establish a secure data channel with the application server. The application server receives the time stamp sent by the user terminal through the secure data channel, and the application server verifies the time stamp through the time stamp mechanism system; in the verification of the time stamp After passing, the secure data channel is used for data transmission between the application server and the user terminal.
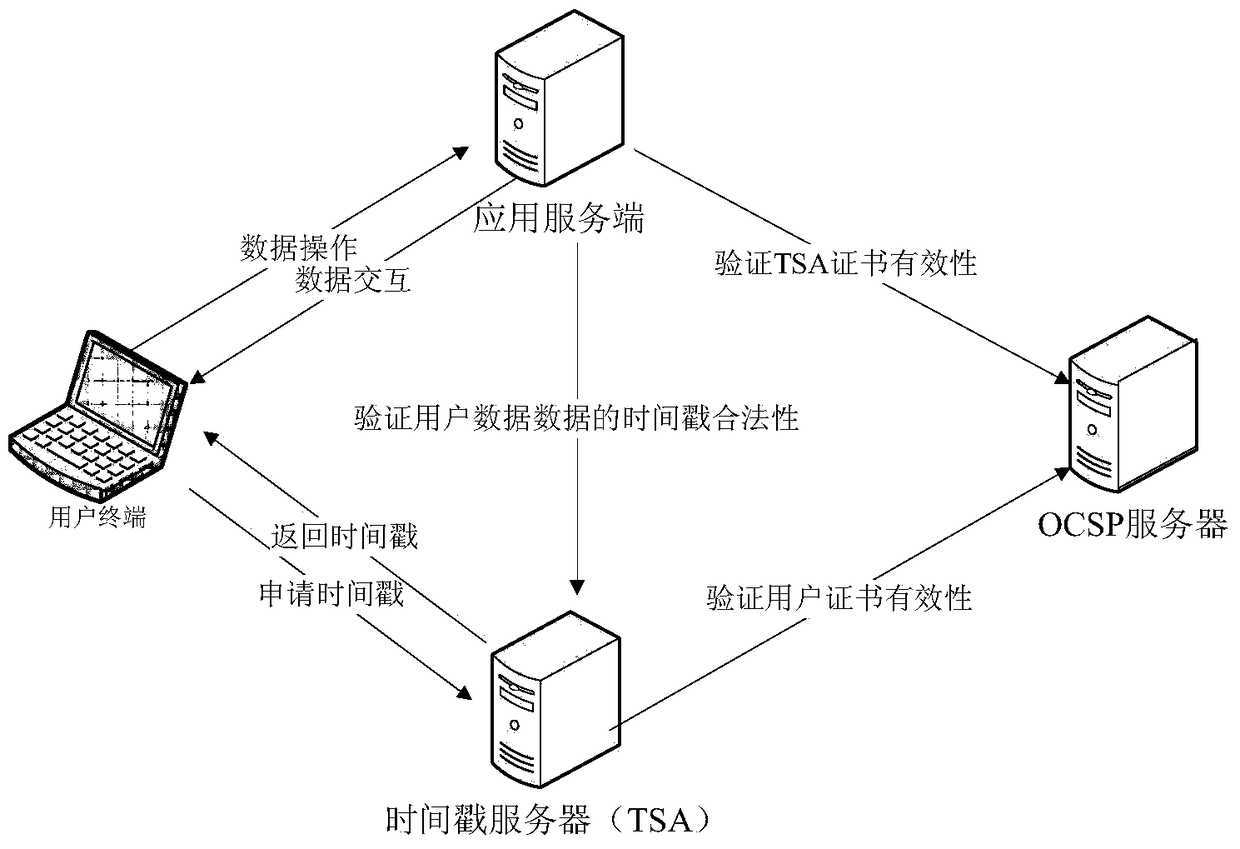
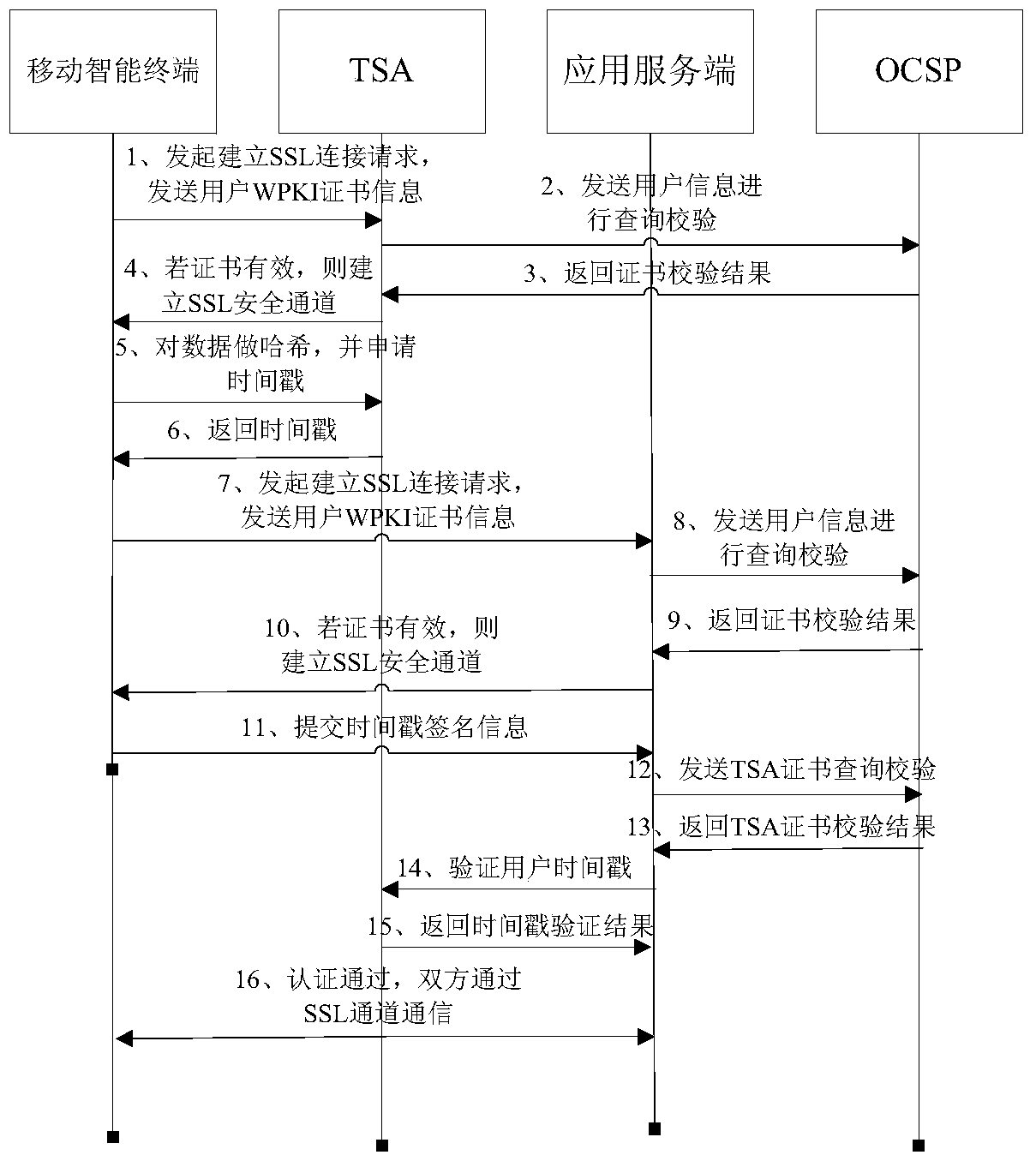
[0053] This embodiment provides a schematic diagram of the implementation principle of a mobile terminal identity authentication method based on WPKI and timestamp. figure 1 As shown, the specific processing flow is as follows figure 2 As shown, including the following processing steps:
[0054] Step S210. The time stamp is authorized by the National Time Service Center and issued by the authoritative and trusted TSA (Time...
Embodiment 2
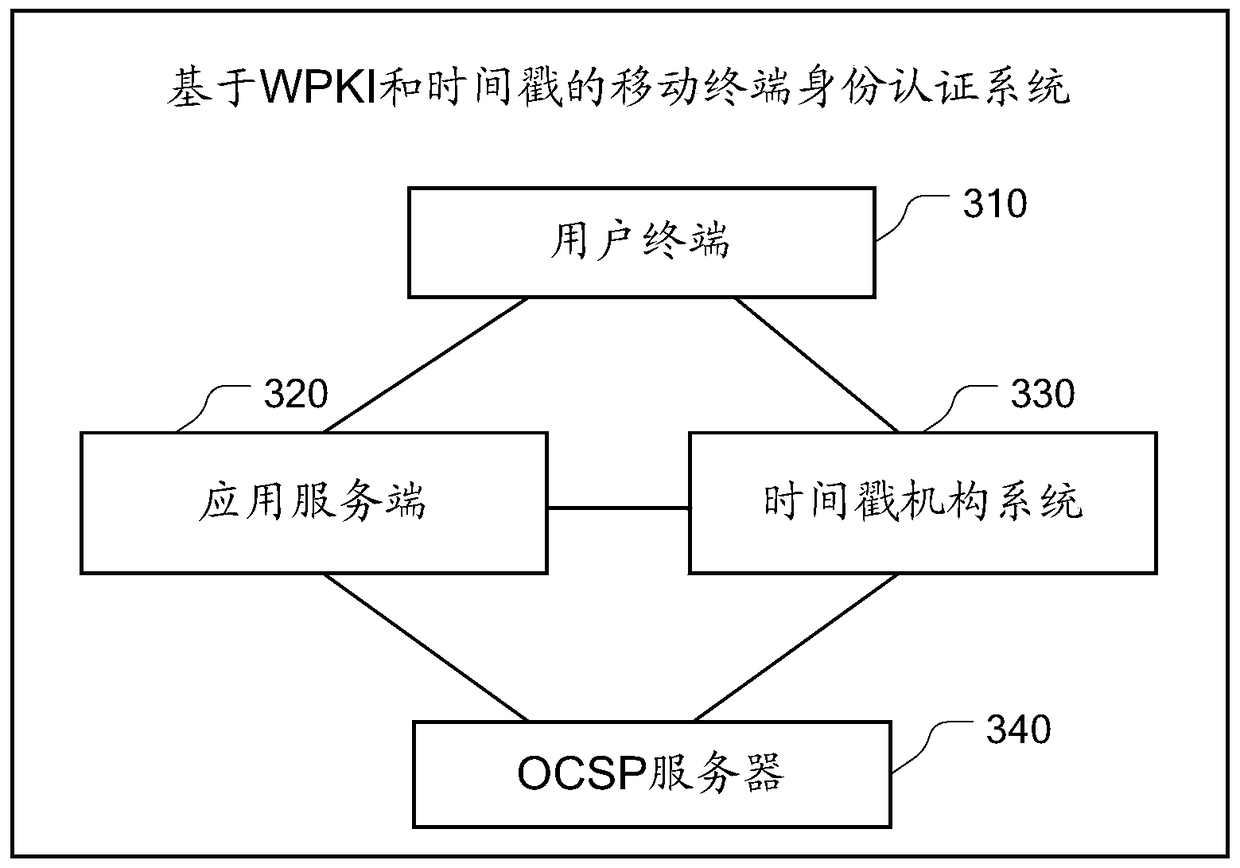
[0079] This embodiment provides a mobile terminal identity authentication system based on WPKI and timestamp. Its specific structure is as follows image 3 As shown, it includes: user terminal, application server, time stamp mechanism system and OCSP server.
[0080] The user terminal is used to obtain the time stamp from the time stamp institution system, and establish a secure data channel with the application server using the wireless public key infrastructure WPKI;
[0081] The application server is configured to receive the time stamp sent by the user terminal through the secure data channel, and the application server verifies the time stamp through the time stamp mechanism system; After the verification of the timestamp is passed, the secure data channel is used for data transmission with the user terminal;
[0082] The time stamp mechanism system is used to send a time stamp to the user terminal and verify the time stamp sent by the application server.
[0083] Specifically, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com