Blind detection system for digital image tampering
A digital image and blind detection technology, applied in the field of image information security, can solve the problems of prolonged matching time of feature points, detection results relying on the location of copied areas and tampered areas, affecting detection efficiency, etc., so as to improve detection accuracy and avoid high Computational problem, the effect of resisting human interference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
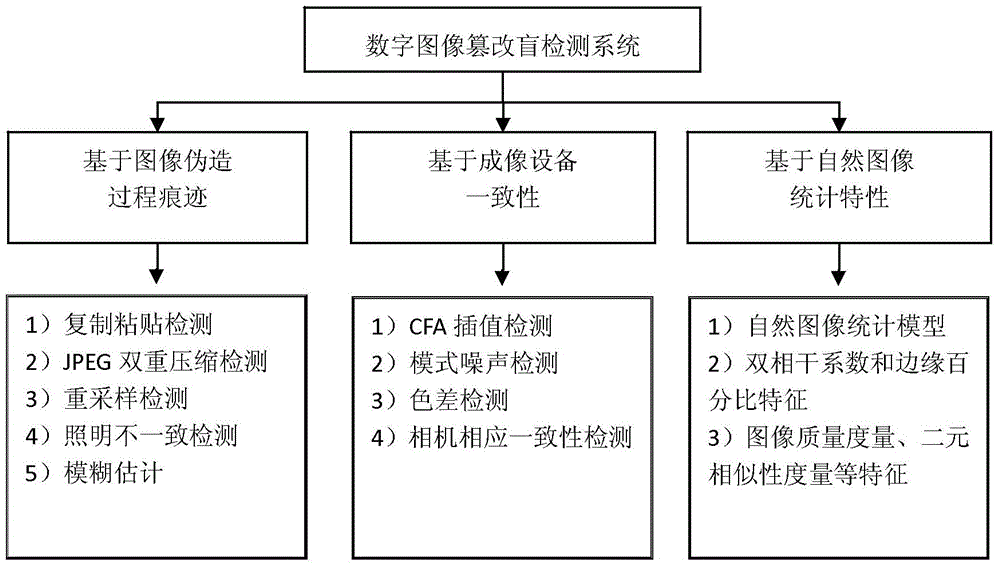
[0056] Combined with the accompanying drawings, the present invention has three main modules, which are respectively based on image forgery process trace module, imaging device consistency module, and natural image statistical characteristic module. The specific way is as figure 1 shown.
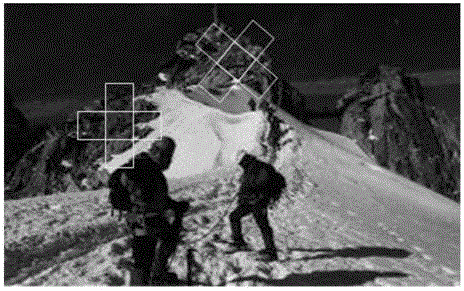
[0057] The image tampering blind detection process is as follows: figure 2 As shown, there are 8 steps involved. Among them, steps 1 to 3 perform normalized expansion on the round window; steps 4 to 6 calculate the phase correlation of adaptive band shrinkage; step 7 estimates the offset angle; step 8 estimates the border of the tampering region.
[0058] Step 1: Polar coordinate system - Cartesian coordinate system conversion
[0059] Let (x, y) be any point in the rectangular coordinate system, ρ is the polar diameter in the polar coordinate system, and θ is the polar angle, then the formula for converting polar coordinates to rectangular coordinates is as follows:
[0060] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com