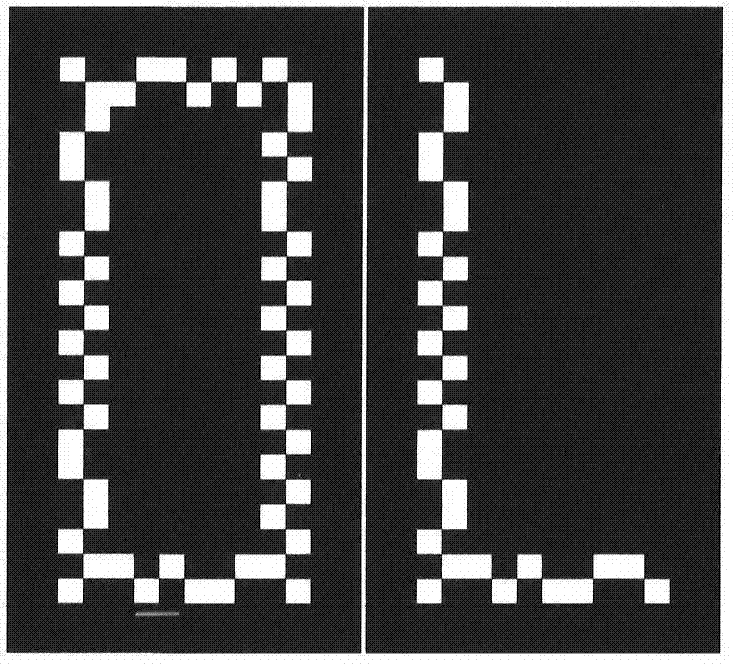Indirect vision password scheme achieved with photoelectricity method
A visual cryptography and scheme technology, applied in image data processing, user identity/authority verification, instruments, etc., can solve the problems of obvious target of decrypting ciphertext, inconvenient system integration and application, and insufficient security, achieving indirectness , Improve concealment and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
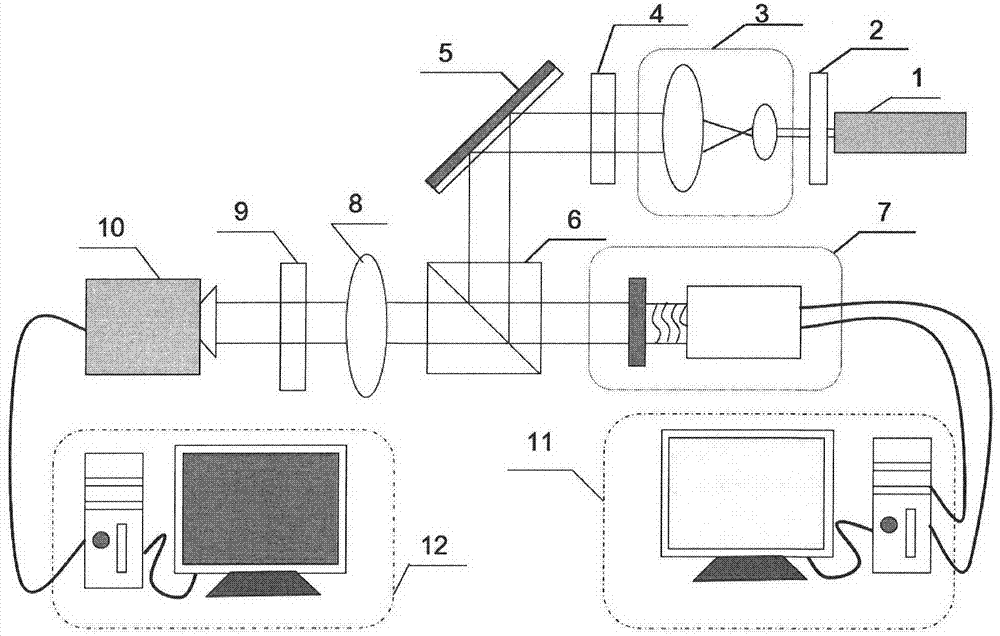
[0034]In order to better explain the implementation process of the present invention, the operation process when two sub-graphs are used will be described in detail below in conjunction with the accompanying drawings. Since the present invention is fully based on the visual cryptography scheme proposed by Moni.Naor and Adi.Shamir in 1994 (see the background introduction part of this description), the visual cryptography scheme can be composed of "(2, 2)-visual cryptography scheme" The characteristics of extending to "(k, n)-visual encryption scheme" are also fully possessed in the present invention, that is, the indirect visual encryption scheme described in the present invention can also be extended to "( k,n) - Indirect Visual Cryptography Scheme".
[0035] figure 1 It is an optical path structure diagram of implementing the decryption of pure phase information by using the photoelectric method in the indirect visual cryptographic scheme of the present invention. The optic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com