Information security guarantee method of internet of things sensing device cloud simulation system
A technology of perception equipment and simulation system, which is applied in the field of information security, can solve problems such as data tampering, data privacy cannot be guaranteed, and system performance is affected, so as to avoid illegal access, ensure data privacy, and access safe and reliable Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention is described below based on examples, but the present invention is not limited to these examples.
[0027] The present invention is aimed at a cloud simulation system for IoT sensing devices, which includes: IoT sensing devices for data collection, IoT gateways for access and integration, and cloud device simulation for cloud simulation center.
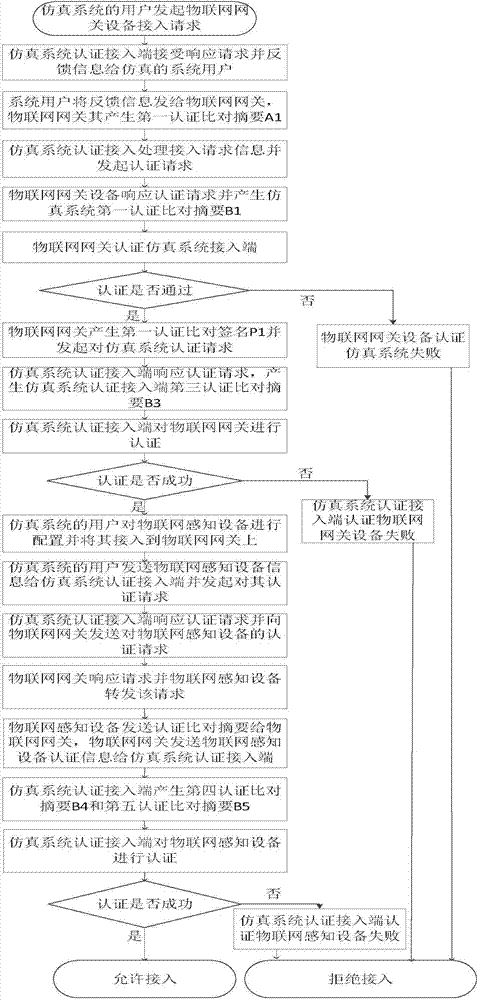
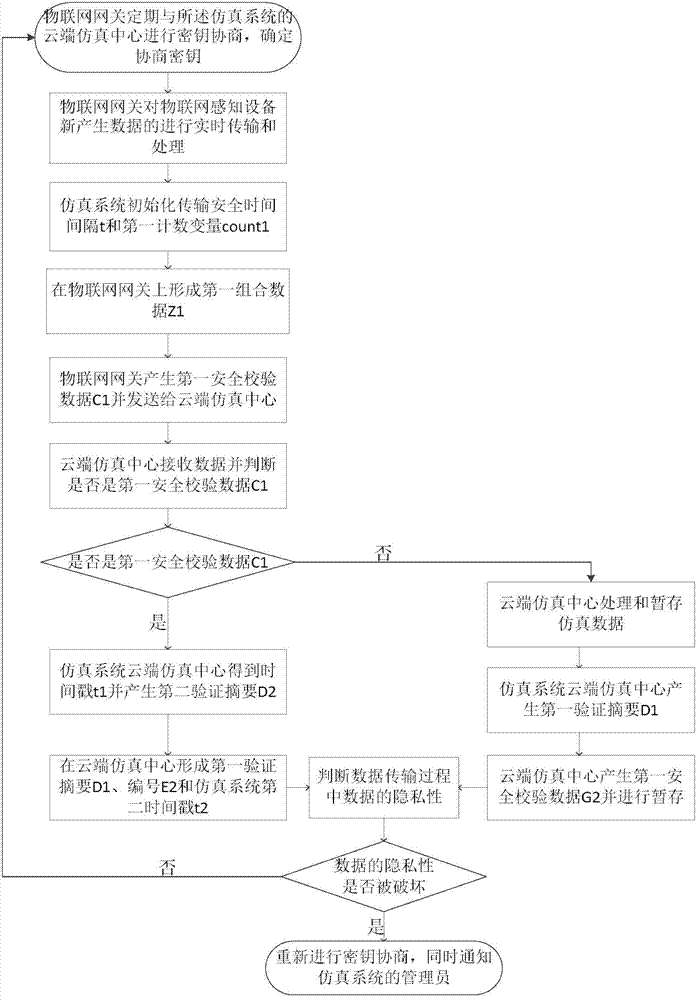
[0028] refer to figure 1 , the implementation method for ensuring the system information security of the present invention includes three parts: one is to perform authentication before the IoT sensing device accesses the cloud real-time simulation system, so as to ensure the legitimacy of the IoT sensing device accessing the simulation system; The second is to perform comprehensive processing of encryption, timing and real-time transmission, decryption, and verification of data in the process of real-time data transmission to ensure the privacy of the data transmission process; the third is when the cloud...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com