Coding Convention Controlled Authentication and Coding Convention Controlled Encryption
A technology of coding conventions and control codes, applied in the fields of information technology and electronics, can solve problems such as non-disclosure, hacking, and backdoors for designers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
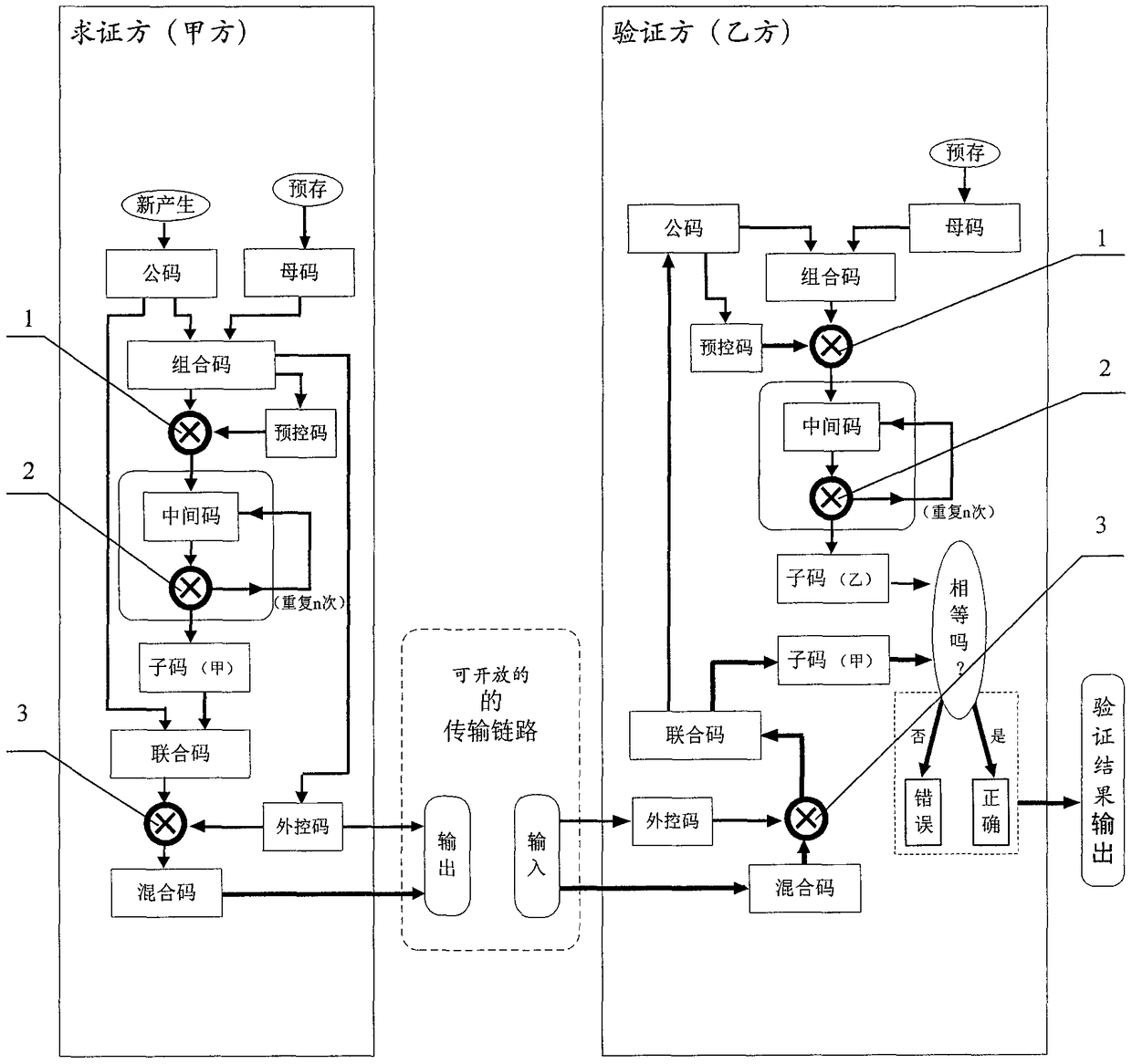
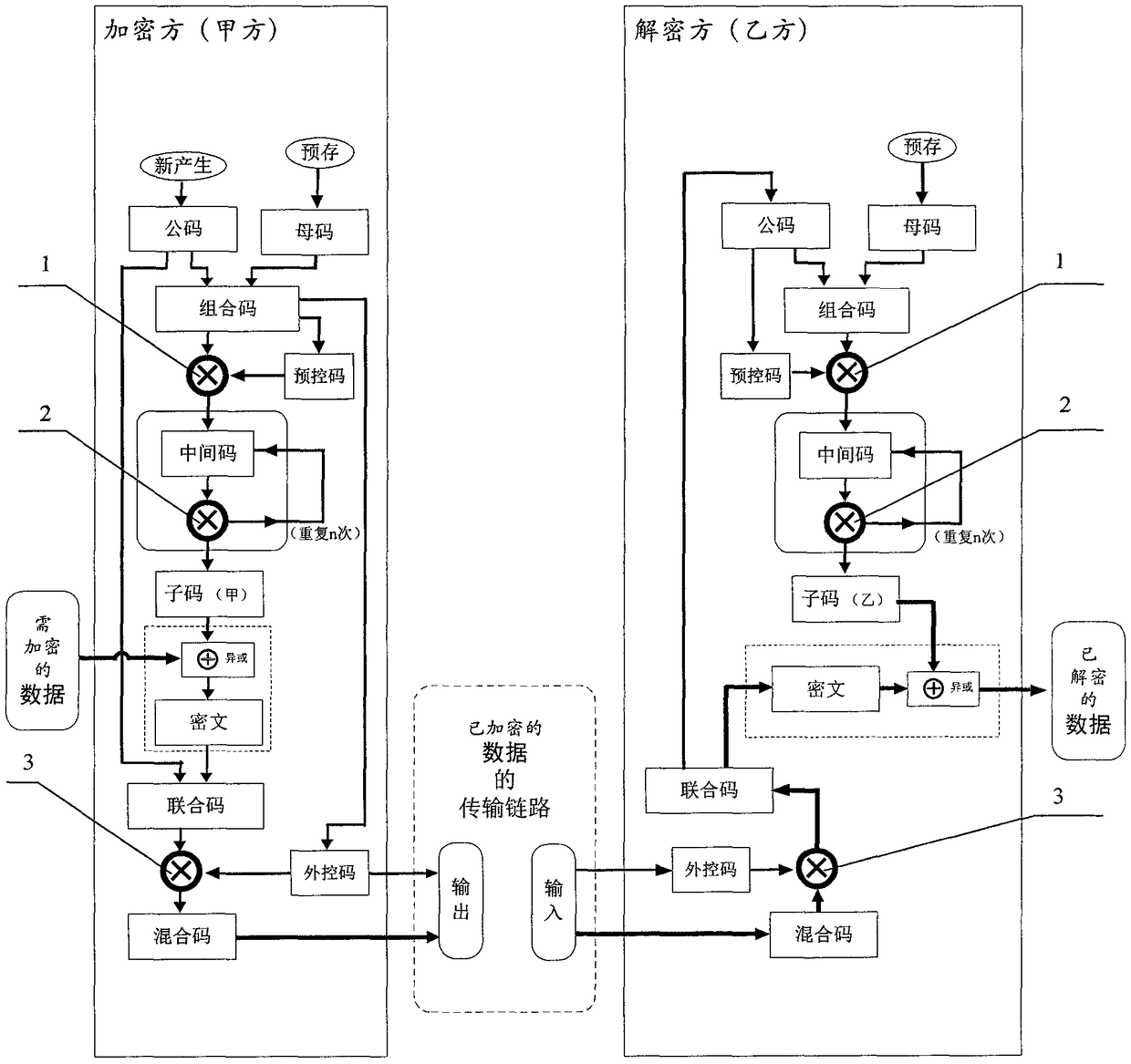
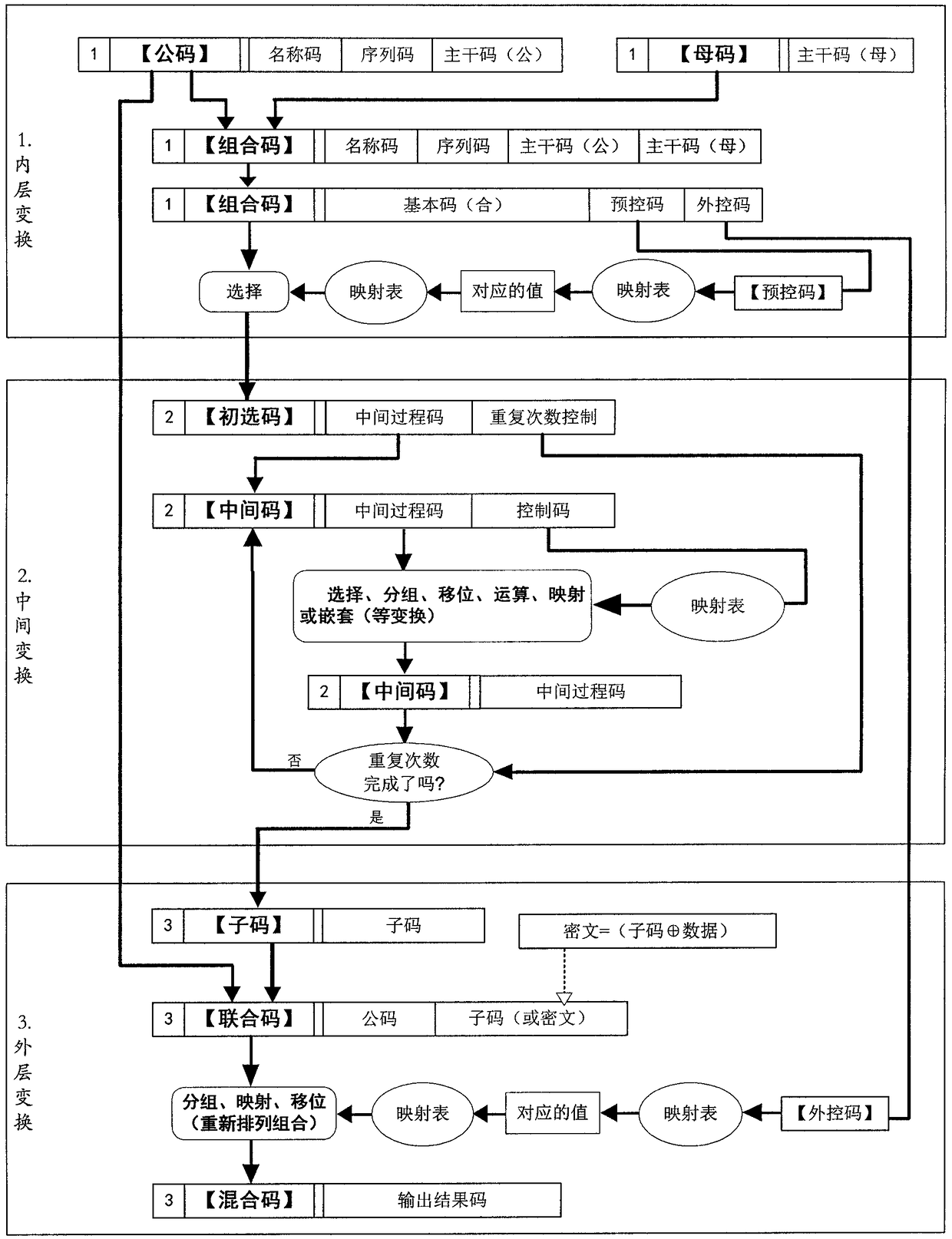
[0178] Example 1, if the program is: N(A(B(m)C(D(m))), the left side of the brackets is the control code, and the inside of the brackets is the basic code, (the basic code can be divided into the next layer Control code and basic code) if, N=number of repetitions, A=grouping mode, B=shifting method, C=operation method, D=mapping method, then, as long as the corresponding data is given, the corresponding conversion rule will be formed.
[0179] Like this, give digital 341826763321, just get 3(4(1(826)7(6(3321))) by program, wherein N=repetition times 3, A=grouping mode 4, B=shift method 1, C =operation method 7, D=mapping method 6, then the transformed result is unique.
example 2
[0180] Example 2, "common code"=abcdefg, "female code"=ABCDEFG, "combined code"=ABCDEFGabcdefg.
[0181] The first transformation (the program) is shifting: mutual intersection=AaBbCcDdEeFfGg.
[0182] The second conversion (program) is operation: "basic code" "control code"=(AaBbCc)(DdEeFfGg), artificially agreed coding situation: 1=+1; 2=×2, 3=-3, 4= +4, 5=x5, 6=-6, 7=+7, 8=x8, 9=-9.
[0183] Then, given "maternal code"=ABCDEFG=1234567, "common code"=abcdefg=9876123, the formula can be obtained:
[0184] 91827364152637=(918273)(64152637)=(((918273-6)+4)+1)×5×2-6-3+7=….
[0185] will have unique results. Given different "female code" and "male code" values, there are different unique values.
[0186] (Or, if "01~09" is agreed to be +1~+9 respectively, "11~19" is agreed to be -1~-9 respectively, "21~29" is agreed to be ×1~×9 respectively, "31~39" "respectively agreed as / 1~ / 9..., the change will be more)
[0187] Such a simple program can provide millions of "mother code...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com