Server network behavior description method
A server and network technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of many differences, poor new attack or intrusion detection effect, high false positive rate, etc., to achieve intuitive and reliable results, The effect of reducing the false negative rate and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
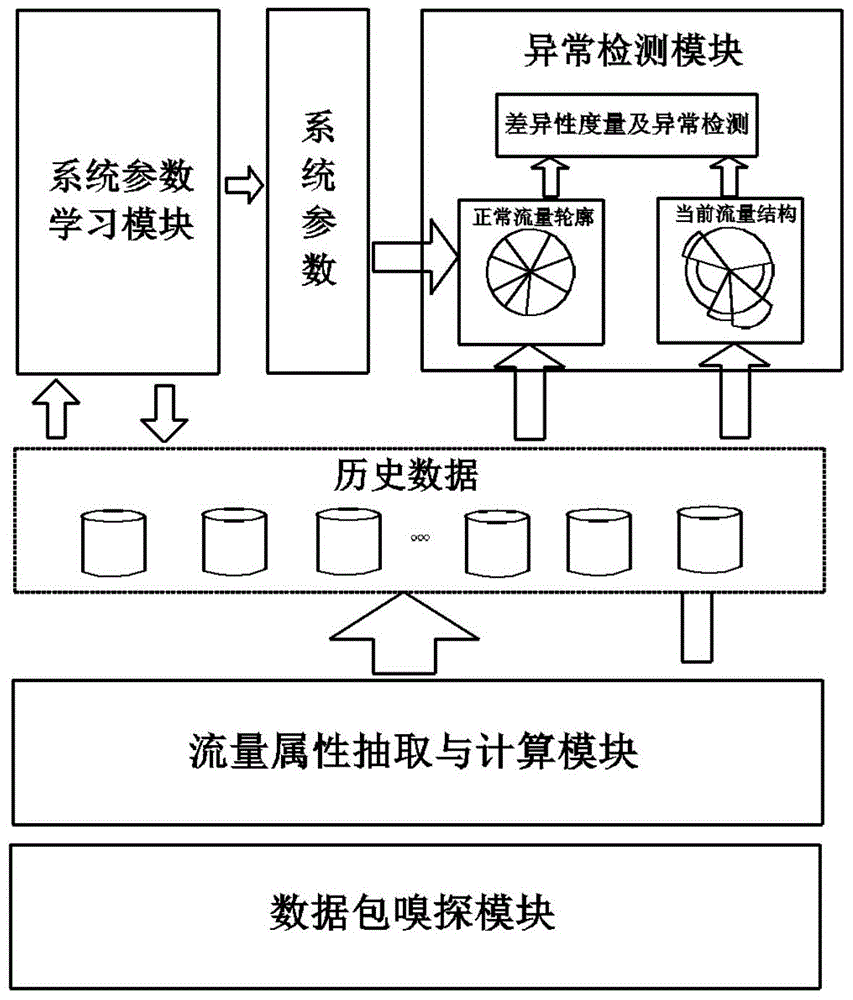
[0050] A server network behavior description method, comprising the following steps:
[0051] (1) Obtain the flow information of entering and exiting the server through the data packet sniffing module;
[0052] (2) Extract the flow information according to the flow attributes through the flow attribute extraction and calculation module, and make statistics on the flow corresponding to each flow attribute according to the time window to form historical data;
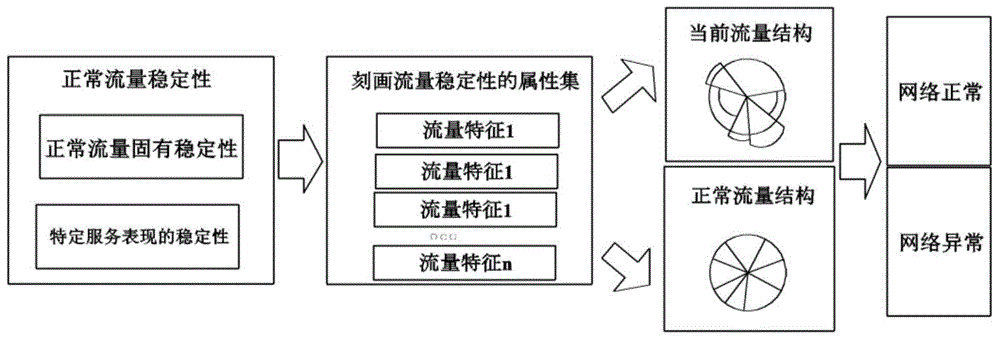
[0053] (3) Calculate the acquired historical data through the system parameter learning module that interacts with the historical data in real time, and obtain the system parameters based on the stability of the traffic structure;
[0054] (4) Construct a dynamic normal flow profile according to system parameters and historical data;
[0055] (5) Construct the current traffic structure a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com