Cross-device high-security non-password login method
A technology with high security and login method, applied in electrical components, transmission systems, etc., can solve the problem of poor security of users remembering passwords, and achieve the effect of no password memory burden, no need to enter passwords, and convenient binding.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
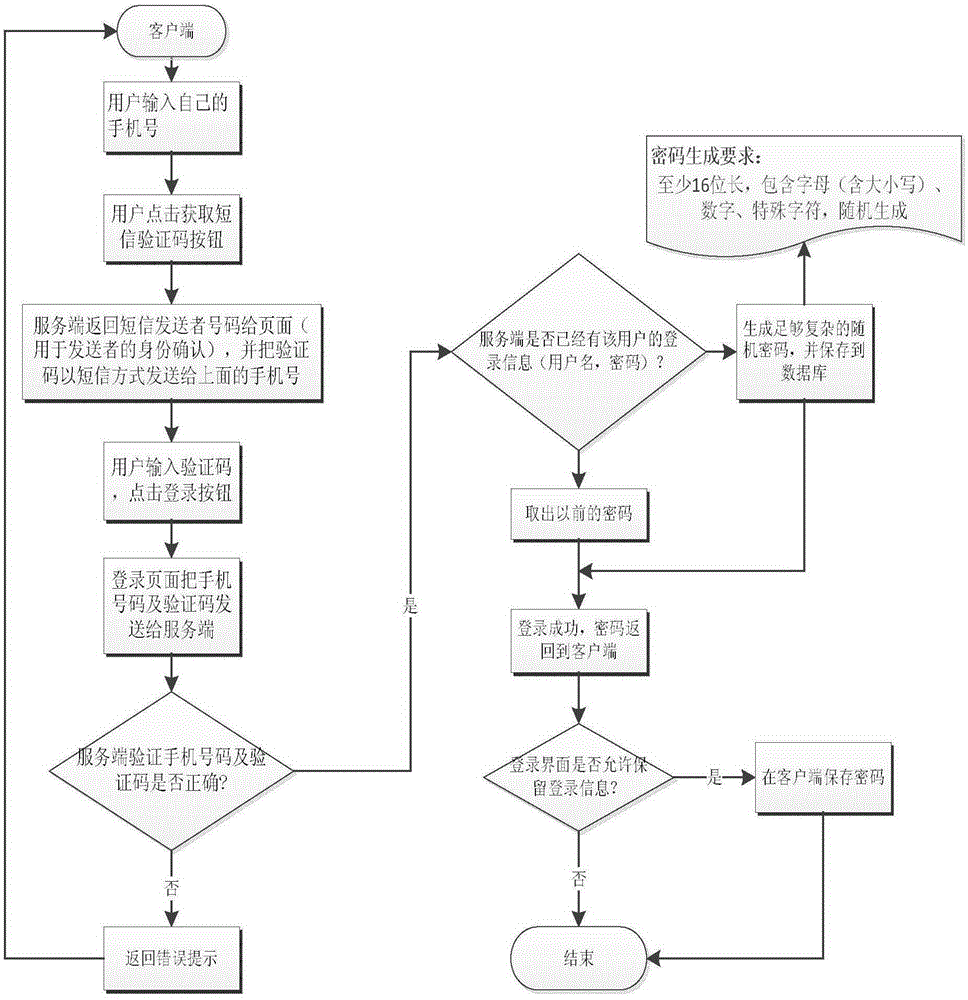
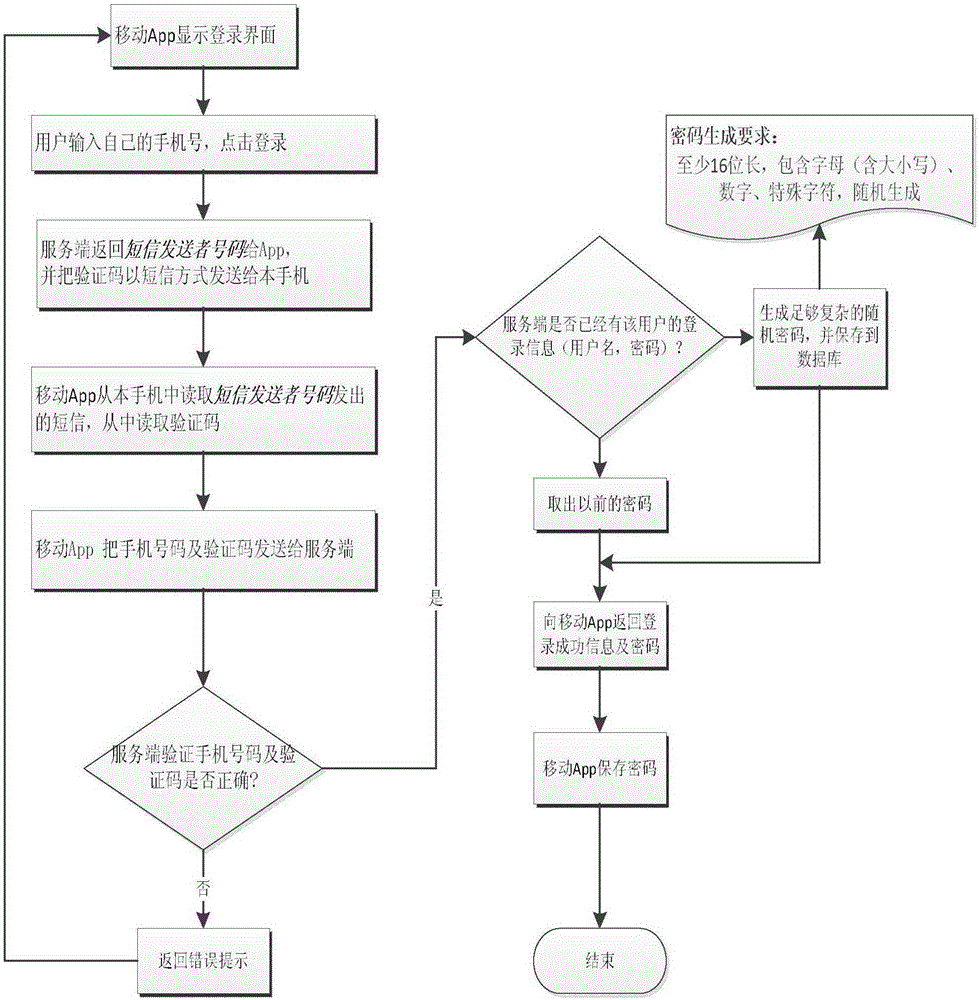
[0025] The technical principle of the cross-device high-security password-free login method of the present invention is to use the mobile phone number as the user's identity, to confirm the user's identity for the first time through the SMS verification code, and to use the random password generated by the server to realize the repeated login of the user That is, when the user uses the enterprise application system, the entire login process does not require the user to enter a password, nor does the user need to remember any password. Since the password is randomly generated by the server, the security of the enterprise application system is also guaranteed. The enterprise application system It consists of a client and a server, the client includes a desktop client and a mobile client; the server includes at least one database. The cross-device high se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com