Security authorization method which solves problem that certificate private key is reused by multiple users
A multi-user and certificate technology, which is applied in user identity/authority verification and key distribution, can solve the problems of electronic signature repudiation, high cost, slow key generation and certificate issuance, and achieve the effect of completeness and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
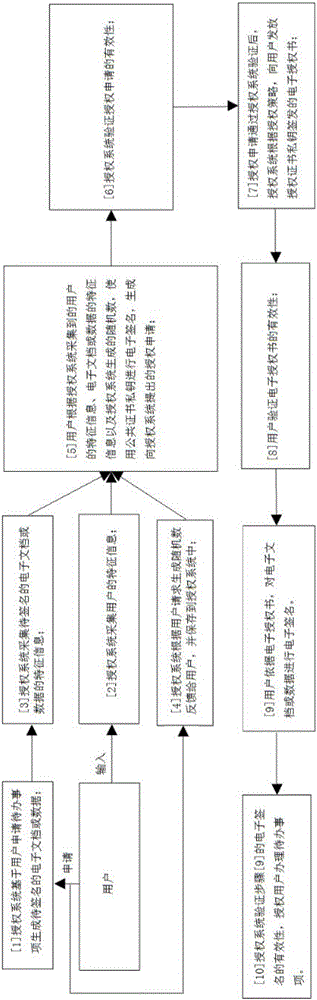
[0071] figure 1 It is a flow chart of a method for solving the problem of multi-user reuse of certificate private keys through security authorization technology when users sign electronically. In order to further illustrate the technical scheme of the present invention, below in conjunction with figure 1 Detailed description. Specific steps are as follows:
[0072] Step 1. The authorization system generates the electronic document or data to be signed based on the user's application to-do item, and obtains the characteristic information of the electronic document or data, including the name DC of the data Name , data type DC Type , the calculated hash value DC Hash ;
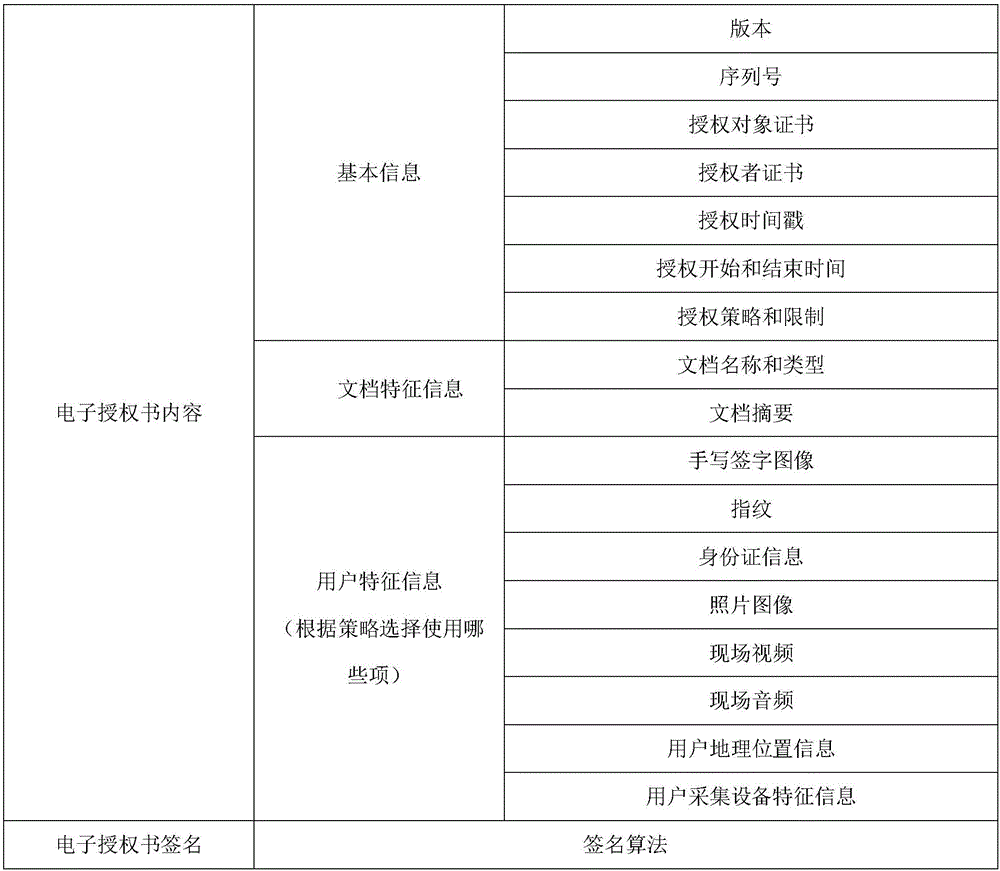
[0073] Step 2: The authorization system collects the user's feature information, including the user's handwritten signature image UC Sign , Fingerprint UC FP , ID card information UC IDC , photo image UC Pic , live video UC Vid and audio UC Aud Wait;
[0074] Step 3. The authorization system generate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com