RFID ownership transfer method
A transfer method and RFID tag technology, applied in the field of radio frequency identification, can solve problems such as difficulty in meeting RFID systems, consuming system execution time and storage space, security loopholes, etc., to improve security and operation efficiency, good application prospects, and key short length effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
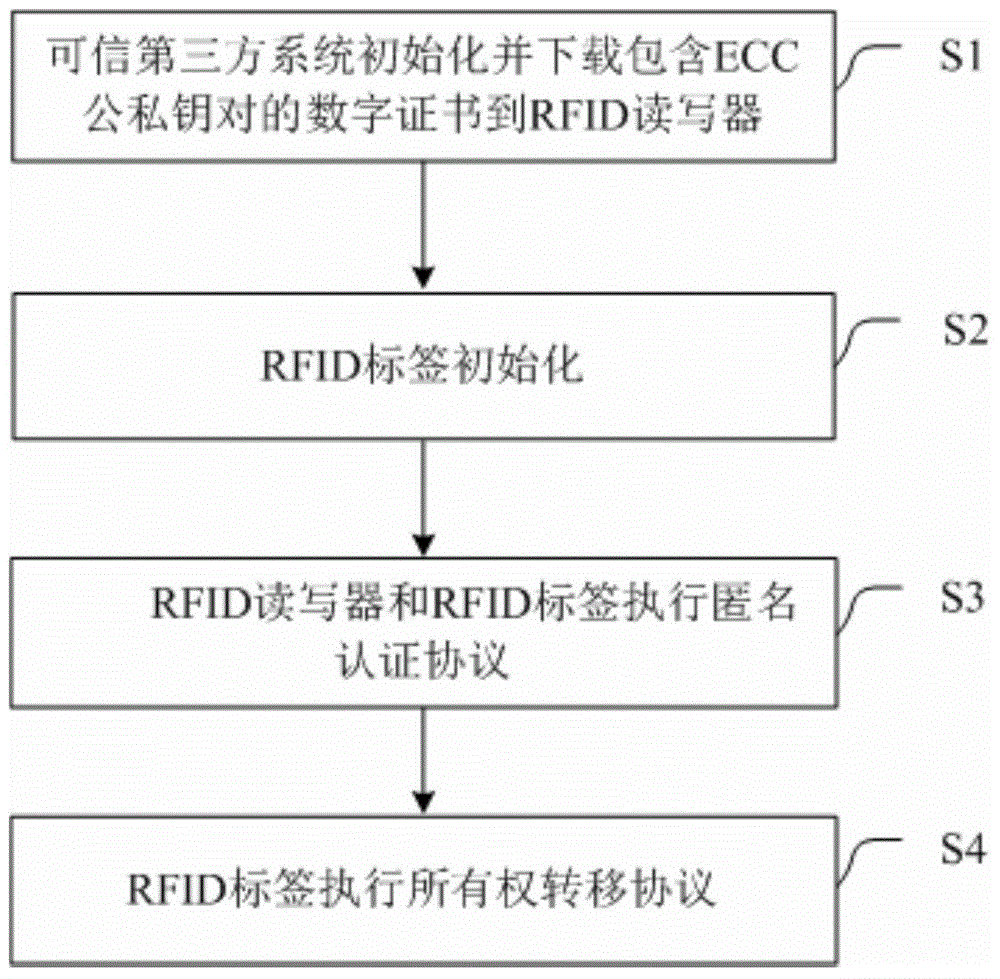
[0038] In order to further explain the technical means and effects of the present invention to achieve the intended purpose of the invention, the specific implementation, structure, features and effects of the present invention will be described in detail below in conjunction with the accompanying drawings and preferred embodiments.
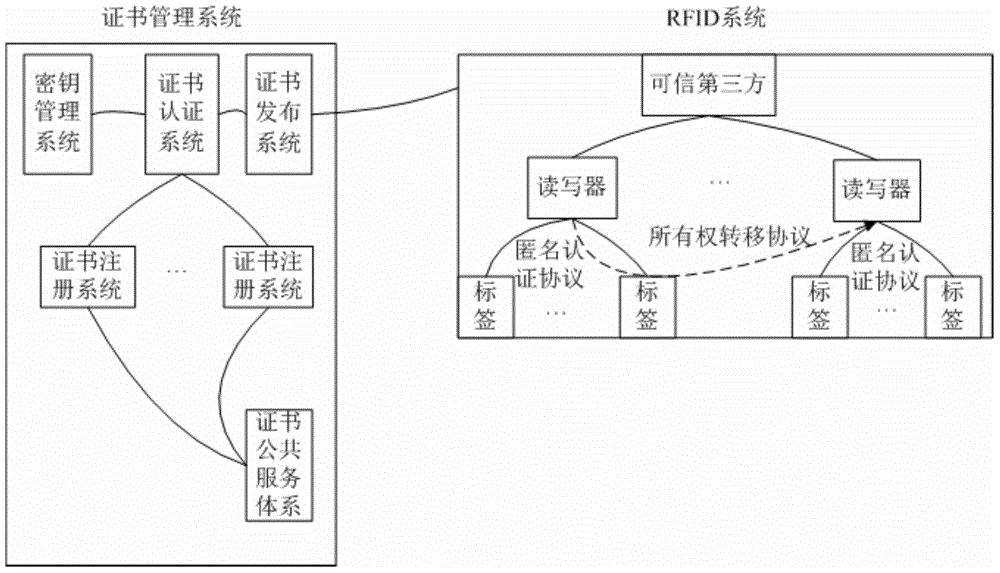
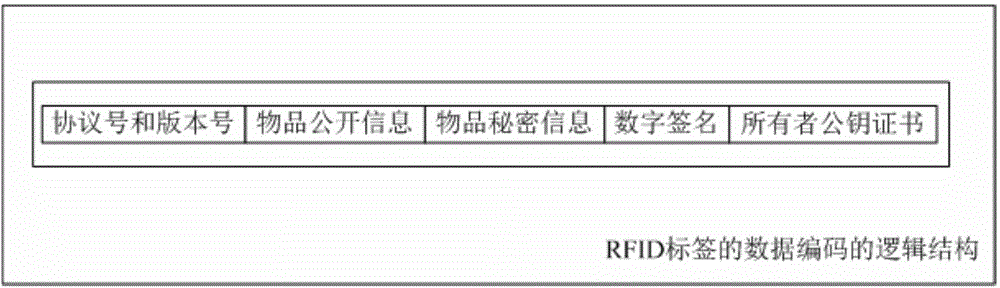
[0039] The following embodiments of the present invention provide a secure and lightweight RFID ownership transfer method based on elliptic curve cryptography (ECC). The implementation process involves the following five roles, specifically: (1) Trusted Third Party (TrustedThirdParty, referred to for short) Ttp): Responsible for accessing the certificate management system, providing privacy protection for the system, and providing a fair and arbitration mechanism for RFID tag transfer; (2) Maker (Maker): refers to the manufacturer of RFID readers and RFID tags; (3) Owner (Owner): refers to the person who owns the ownership of the RFID reader; (4) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com