Network security authentication system
A verification system and security technology, applied in the field of network security verification system, can solve the problems of false negatives and false positives, intrusion detection technology can not effectively detect unknown types of attacks, can not prevent attacks and other problems, to achieve a low false positive rate , avoid chance, improve the effect of accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
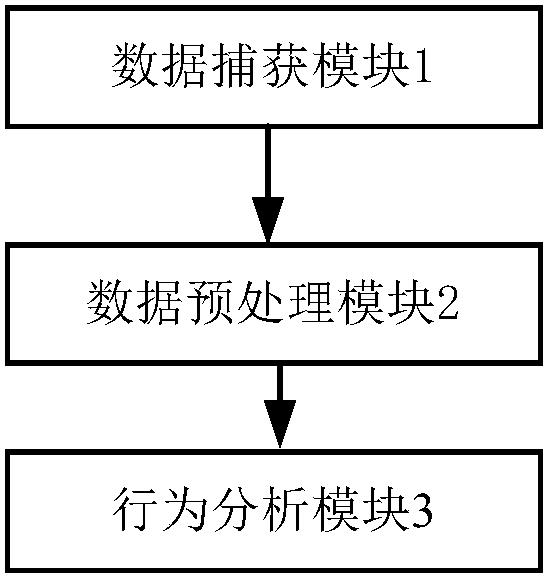
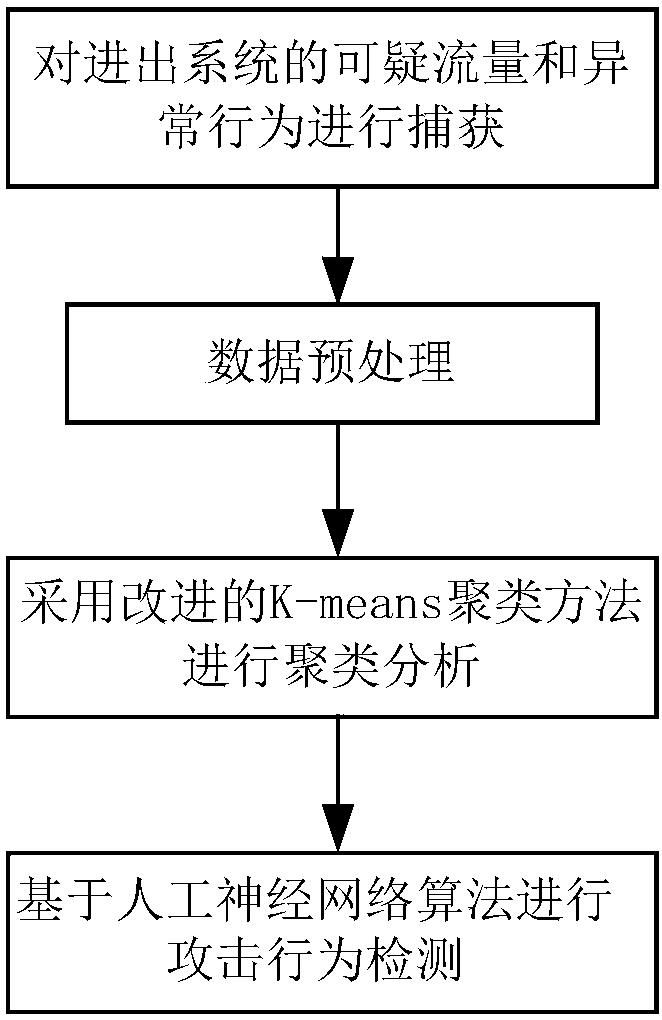
[0030] see figure 1 , figure 2 , the network security verification system of this embodiment includes a data capture module 1, a data preprocessing module 2, and a behavior analysis module 3; the data capture module 1 is used to capture suspicious traffic and abnormal behavior entering and leaving the system to form a sample Data; the data preprocessing module 2 is used to filter and preprocess the sample data, remove the noise data in the sample data, and then perform dimensionality reduction processing on the sample data; the behavior analysis module 3 is used to adopt the improved K The -means clustering method performs cluster analysis on the preprocessed sample data, and detects attack behaviors based on the artificial neural network algorithm to identify potential unknown attacks in the network.
[0031] Wherein, the data capture module 1 uses a firewall to collect suspicious traffic entering and exiting the system.
[0032] Wherein, the data capture module 1 captures...
Embodiment 2
[0046] see figure 1 , figure 2 , the network security verification system of this embodiment includes a data capture module 1, a data preprocessing module 2, and a behavior analysis module 3; the data capture module 1 is used to capture suspicious traffic and abnormal behavior entering and leaving the system to form a sample Data; the data preprocessing module 2 is used to filter and preprocess the sample data, remove the noise data in the sample data, and then perform dimensionality reduction processing on the sample data; the behavior analysis module 3 is used to adopt the improved K The -means clustering method performs cluster analysis on the preprocessed sample data, and detects attack behaviors based on the artificial neural network algorithm to identify potential unknown attacks in the network.
[0047] Wherein, the data capture module 1 uses a firewall to collect suspicious traffic entering and exiting the system.
[0048] Wherein, the data capture module 1 captures...
Embodiment 3
[0062] see figure 1 , figure 2 , the network security verification system of this embodiment includes a data capture module 1, a data preprocessing module 2, and a behavior analysis module 3; the data capture module 1 is used to capture suspicious traffic and abnormal behavior entering and leaving the system to form a sample Data; the data preprocessing module 2 is used to filter and preprocess the sample data, remove the noise data in the sample data, and then perform dimensionality reduction processing on the sample data; the behavior analysis module 3 is used to adopt the improved K The -means clustering method performs cluster analysis on the preprocessed sample data, and detects attack behaviors based on the artificial neural network algorithm to identify potential unknown attacks in the network.
[0063] Wherein, the data capture module 1 uses a firewall to collect suspicious traffic entering and exiting the system.
[0064] Wherein, the data capture module 1 captures...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com