Intrusion detection method based on Markov chains
A Markov chain and intrusion detection technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as labeling difficulties, and achieve the effects of reducing false alarm rates, high detection efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The following examples describe the present invention in more detail.
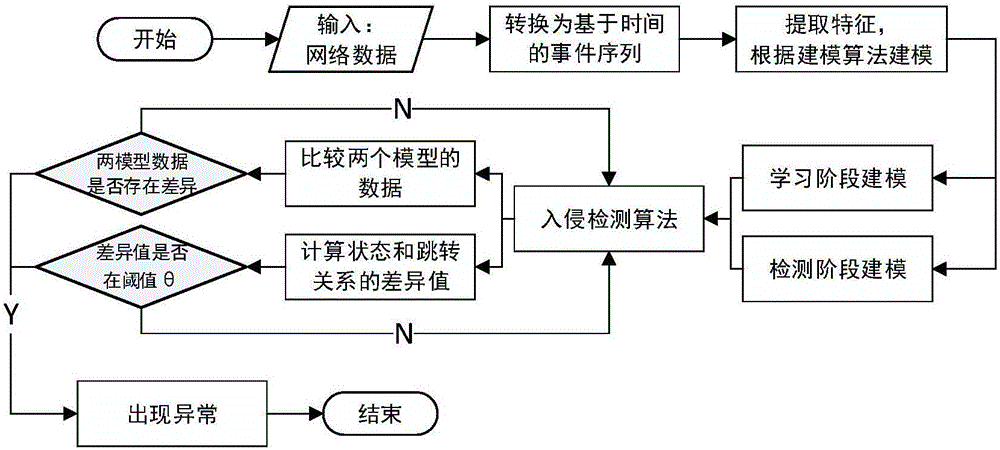
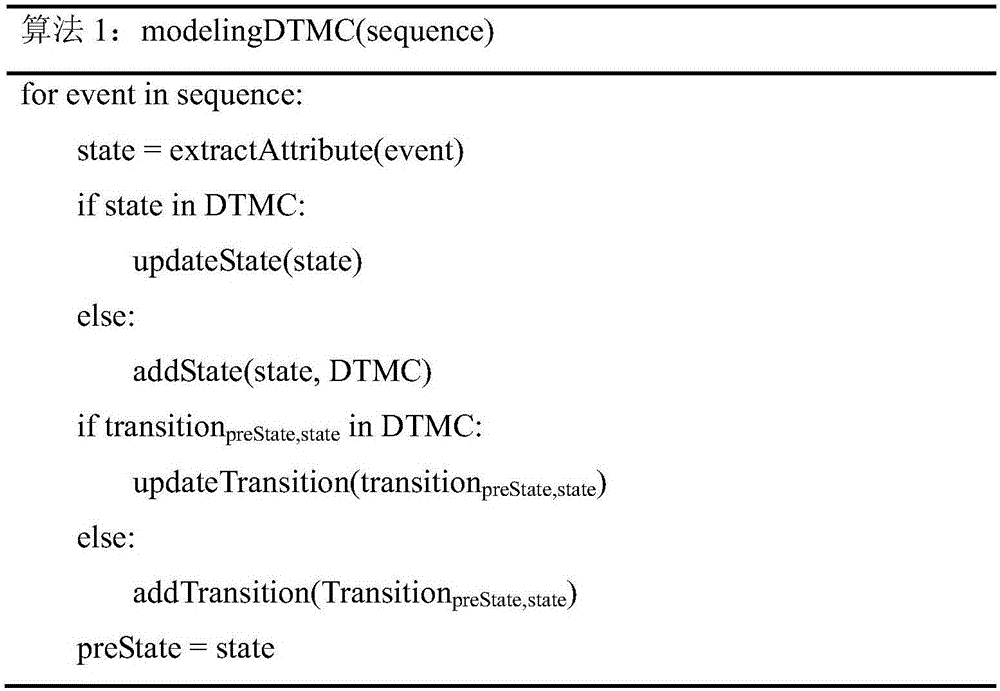
[0038] combine figure 1 , the Markov chain-based intrusion detection method of the present invention mainly includes: First, define a time-based event sequence for network data; Afterwards, the Markov chain model is established for the learning phase and the detection phase respectively; finally, the intrusion detection algorithm is applied to the two models, and two methods are used to screen abnormalities, namely, whether the data comparison of the two models and the difference value are within the threshold range Inside. Specifically, the following technical means are included:
[0039] 1. Define time-based event sequences for network data.
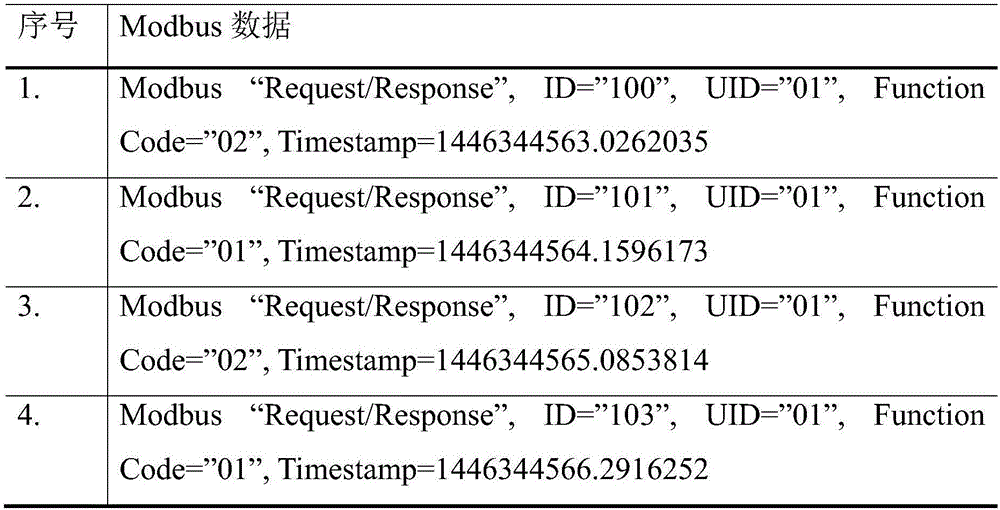
[0040]The present invention is illustrated with the Modbus protocol. The definition of time-based event sequences mainly depends on two attributes: function code and time. For the Modbus protocol, the specific formal description of the time-based event ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com