System and method for preventing attacks by self-learning in cloud environment
A cloud environment and anti-attack technology, applied in the field of cloud security management, can solve problems such as prone to false positives or false negatives, inability to detect new types of intrusion behaviors, and software detection and early warning, so as to reduce difficulty and complexity and improve accuracy , the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
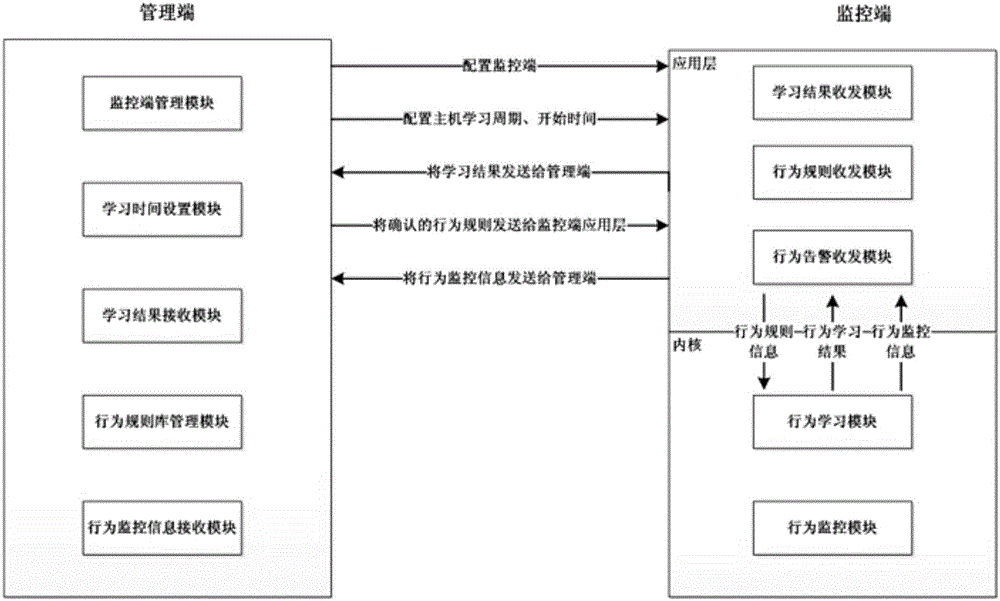
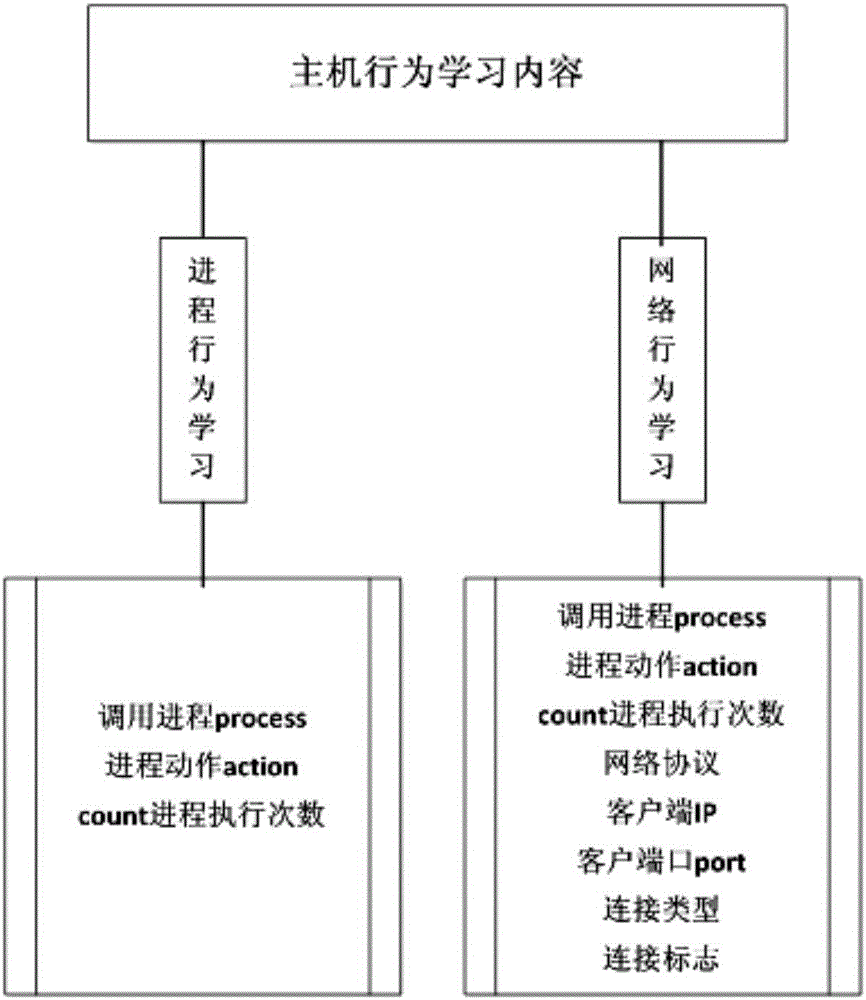
[0030] First of all, it should be explained that the present invention relates to a cloud environment attack defense method and security management technology, and is an application of computer technology in the field of information security technology. During the implementation of the present invention, the application of multiple software function modules will be involved. The applicant believes that, after carefully reading the application documents and accurately understanding the realization principle and purpose of the present invention, combined with existing known technologies, those skilled in the art can fully implement the present invention by using their software programming skills. The aforementioned software functional modules include but are not limited to: monitoring terminal management module, learning time setting module, learning result receiving module, behavior rule library management module, behavior monitoring information receiving module, learning module...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com