Cloud resource pool data security detection method and system
A technology of data security and detection method, applied in the field of information security, to achieve the effect of flexible system framework and good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] In order to make the purpose, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the examples and accompanying drawings. As a limitation of the present invention.
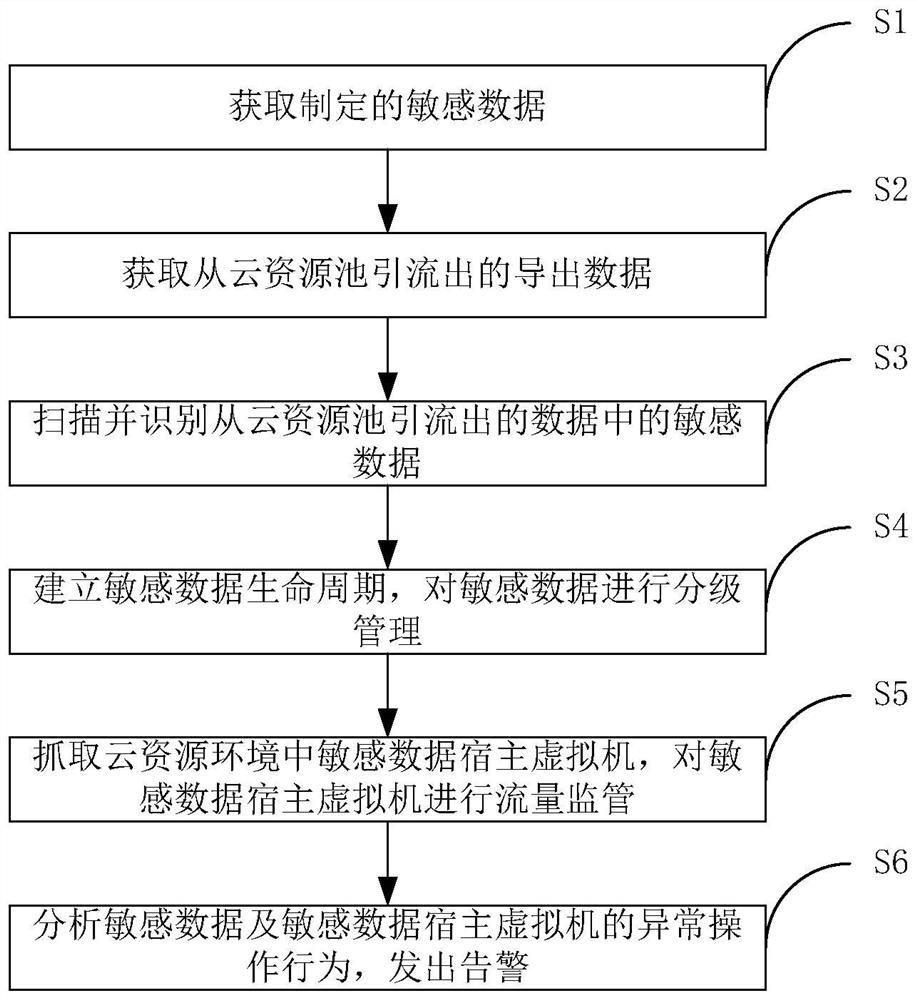
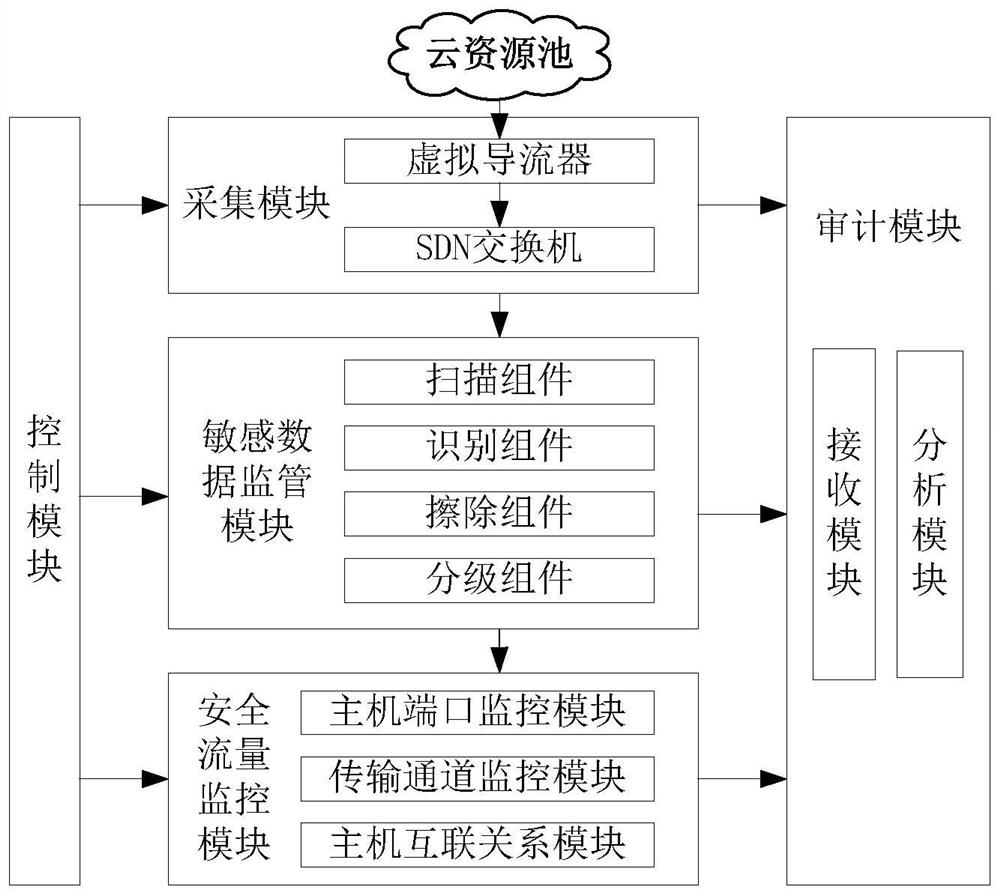
[0057] In the cloud resource pool, virtual hosts are dynamically generated using shared resources. There is a possibility that data is not erased before sharing, data is not encrypted for transmission, and sensitive data may be leaked through data monitoring and recovery technologies. Realize the full life cycle security management and control of the creation, production, use, and destruction of various sensitive data in the cloud computing environment, such as the retrieval and transmission of business data in the domain and cross-domain virtual machines, and the creation, production, use, and destruction of various sensitive data during the migration process. Monitor what kind of sensitive data is involved...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com