Positioning method and system for memory leak
A technology of memory leakage and positioning method, which is applied in the direction of instruments, electrical digital data processing, calculation, etc., and can solve the problems that users cannot know about errors, memory cannot be reused, memory leaks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
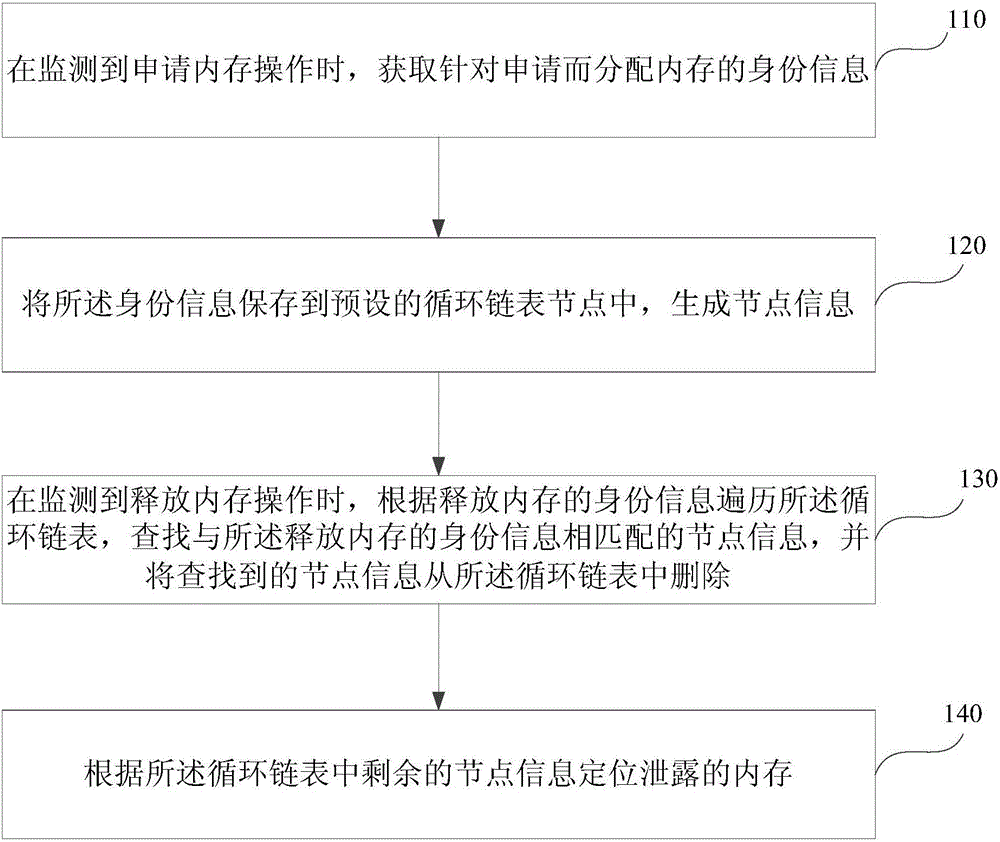
[0045] figure 1 It is a flow chart of a method for locating a memory leak provided by Embodiment 1 of the present invention. This method is applicable to the situation of quickly searching and locating the memory leaked in the program during the program debugging stage, and can be executed by a memory leak locating system. . The system can be realized by means of hardware and / or software. The method specifically includes the following steps:
[0046] Step 110 , when the memory application operation is detected, obtain the identity information of memory allocated for the application.
[0047] Usually, there are many existing standard library functions that can be called directly according to the programming language used. Therefore, the library function that realizes a specific function can be directly called in the software program. When there is no required library function, it can also be called. Customize some functional functions, and call the corresponding functional f...
Embodiment 2
[0060] figure 2 It is a schematic flowchart of a method for locating memory leaks provided by Embodiment 2 of the present invention. On the basis of Embodiment 1, this embodiment further optimizes the method. For details, see figure 2 As shown, the method specifically includes the following:
[0061] Step 210, when it is detected that a memory application function is called to apply for memory, determine that there is an operation to apply for memory.
[0062] Step 220, obtain the identity information of the memory allocated for the application by overloading the memory application function.
[0063] Among them, an overloaded function is a special case of a function, that is, it is allowed to declare several functions with the same name and similar functions in the same declaration domain, but the formal parameters of these functions with the same name must be different, and the formal parameters can specifically refer to individual parameters Number, type, or order, etc.,...
Embodiment 3
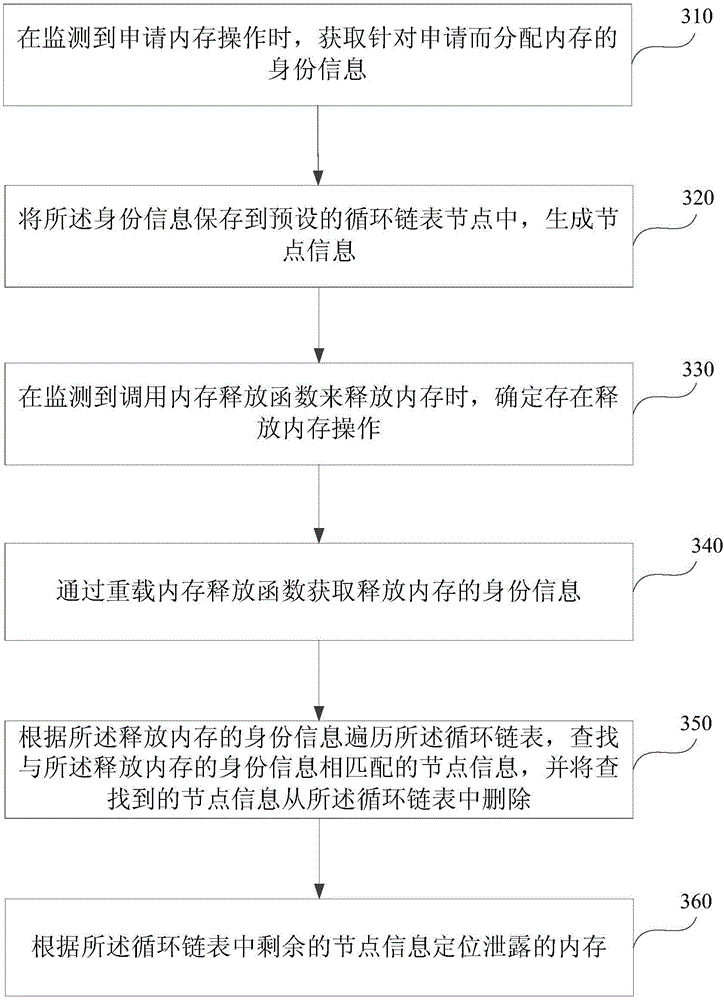
[0072] image 3 It is a schematic flowchart of a method for locating memory leaks provided by Embodiment 3 of the present invention. On the basis of the above-mentioned embodiments, this embodiment has been further optimized. For details, see image 3 As shown, the method is as follows:
[0073] Step 310 , when the memory application operation is detected, obtain the identity information of memory allocated for the application.
[0074] Step 320: Save the identity information in a preset circular linked list node, and generate node information.
[0075] Step 330 , when it is detected that a memory release function is called to release memory, determine that there is a memory release operation.
[0076] Step 340, obtain the identity information of the released memory by overloading the memory release function.
[0077] Step 350: Traverse the circular linked list according to the identity information of the freed memory, search for node information matching the released memor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com