A Complex Attack Recognition Method for Wireless Intrusion Detection System
A wireless intrusion detection and attack identification technology, applied in transmission systems, wireless communications, digital transmission systems, etc., can solve the problems of different attack methods, increased intrusion detection or defense difficulty, and different attack targets.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0130] The present invention will be further described below in conjunction with the examples. The description of the following examples is provided only to aid the understanding of the present invention. It should be pointed out that for those skilled in the art, without departing from the principles of the present invention, some improvements and modifications can be made to the present invention, and these improvements and modifications also fall within the protection scope of the claims of the present invention.
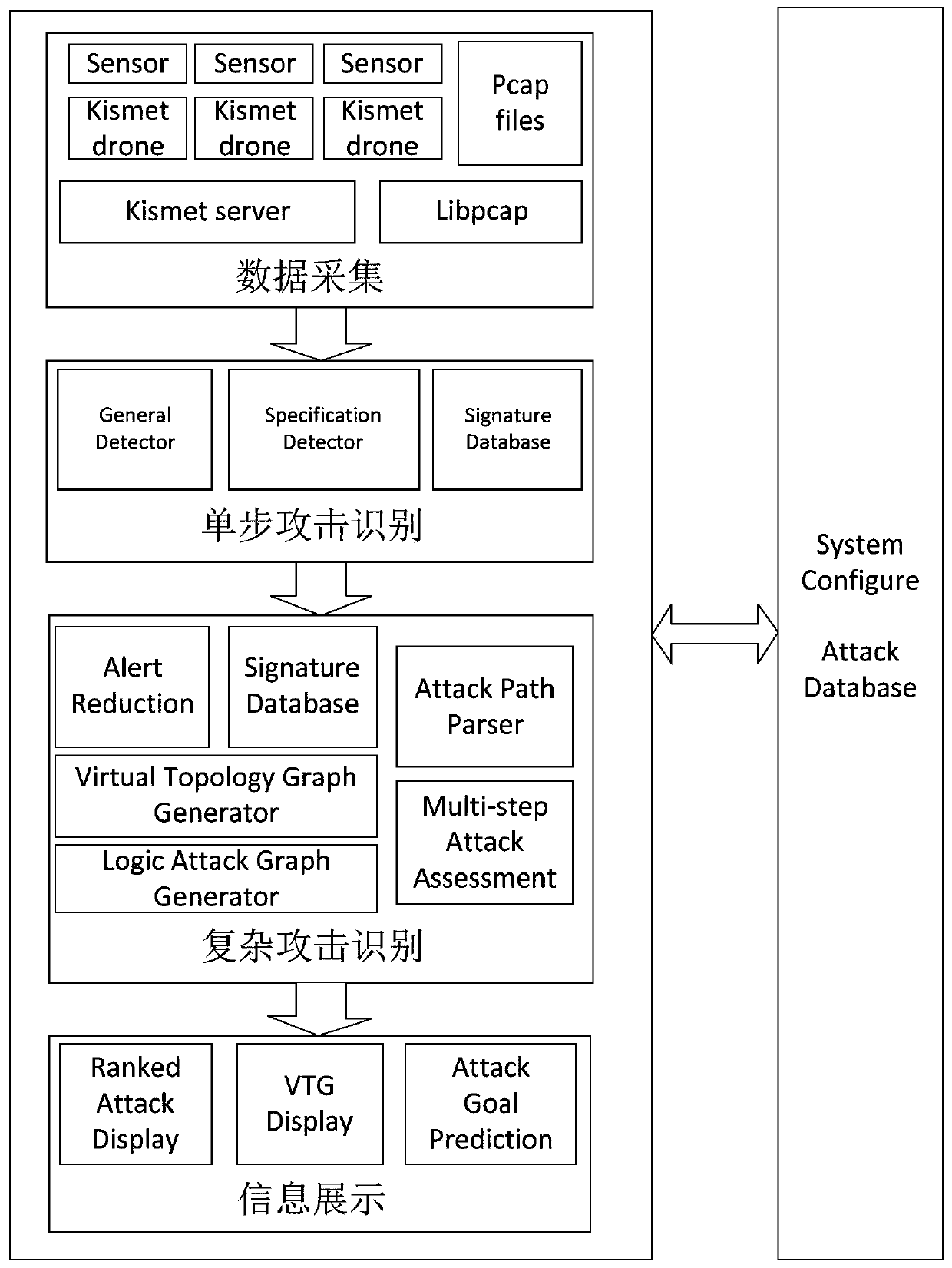
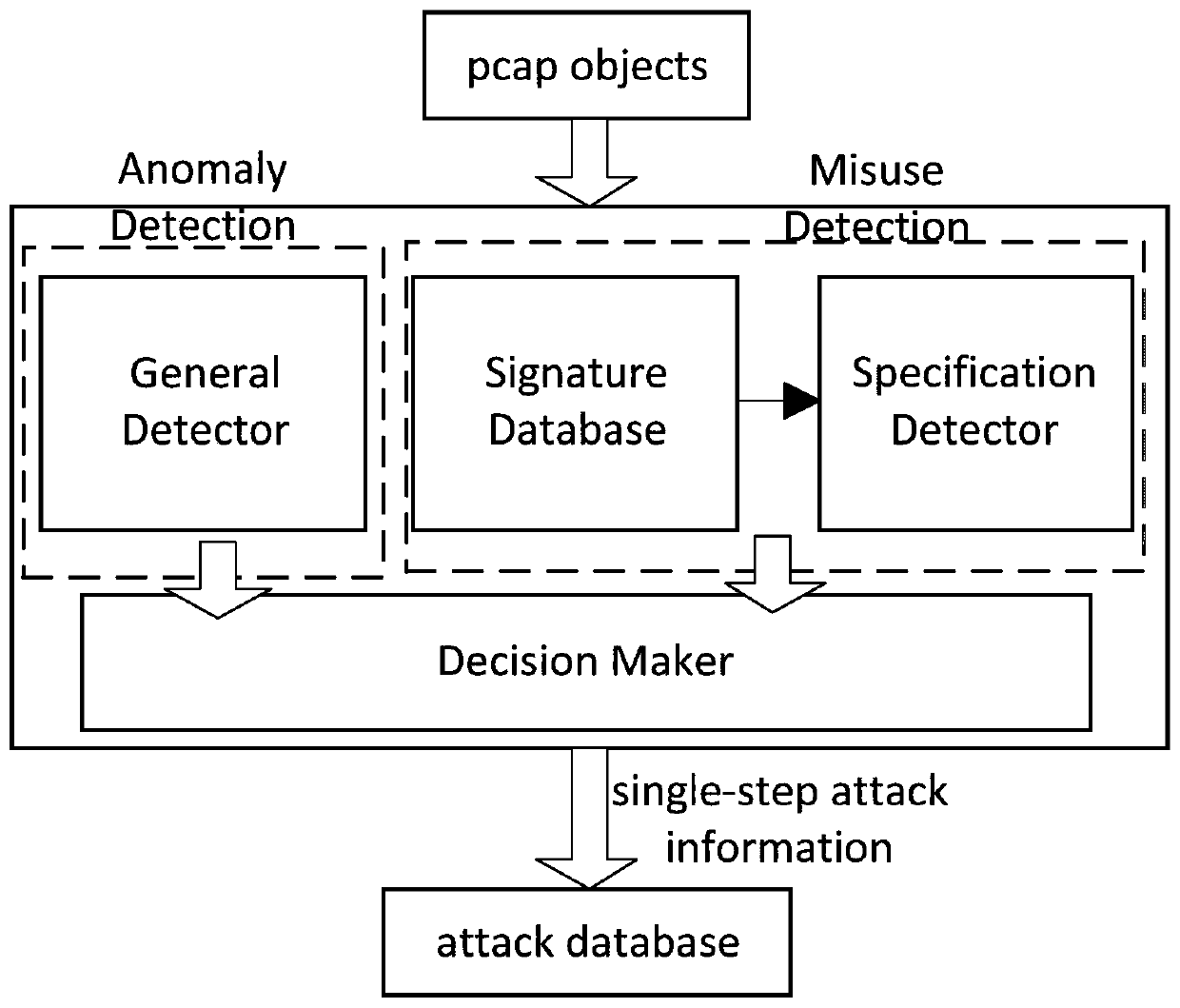
[0131] like Figure 1 to Figure 19 As shown, the complex attack identification method in the wireless network of the present invention includes four steps: data collection, single-step attack identification, complex attack identification and information display interface.
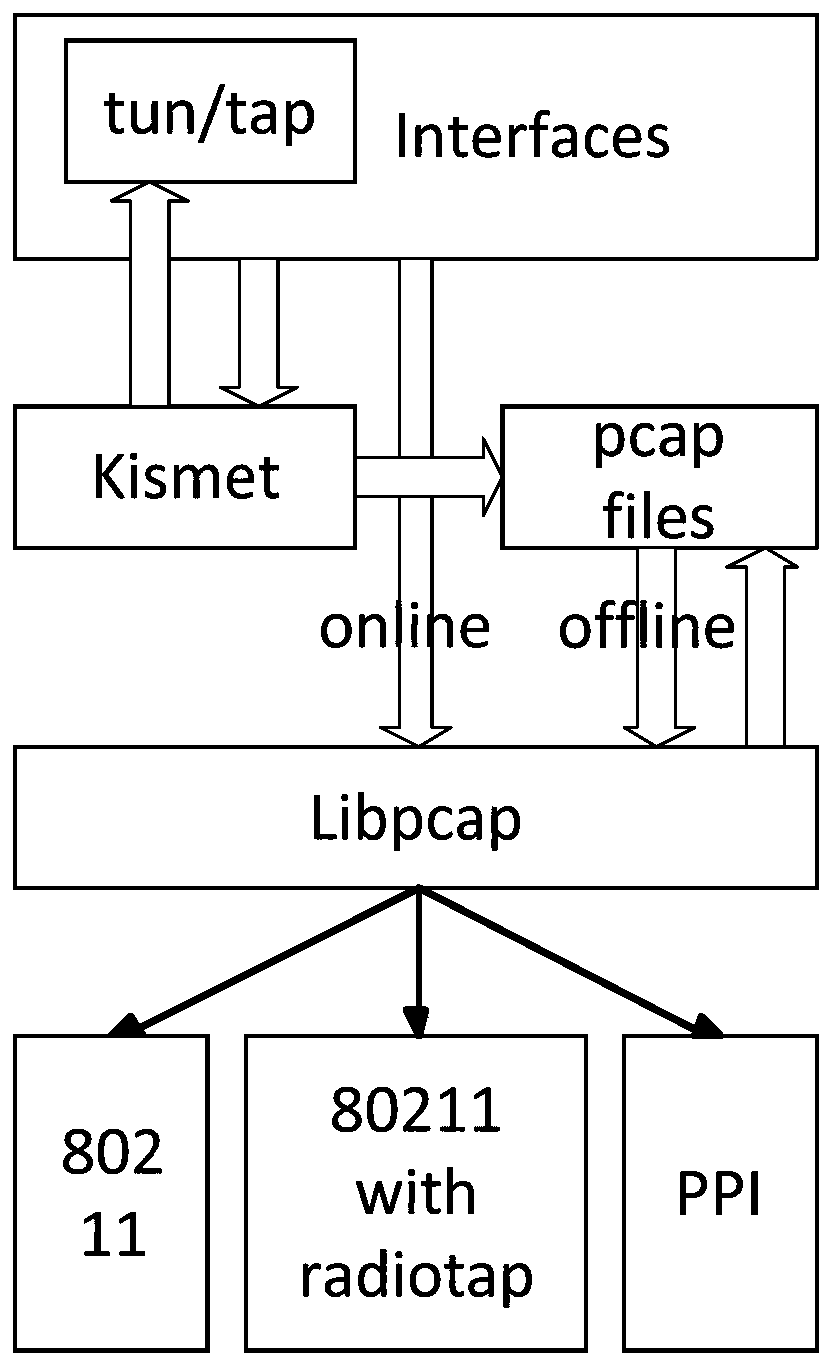
[0132] (1) Data collection: The source of data collection and the selection of metrics are very important for intrusion detection systems. Selecting appropriate metrics can effectively contr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com