Collaborative theory-based DDoS (Distributed Denial of Service Attack) defense system and method
A technology of attack defense system and synergy theory, which is applied in the field of DDoS attack defense system based on synergy theory, can solve problems such as easy DDoS attacks, achieve strong security and robustness, improve robustness, and reduce false alarm rates.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
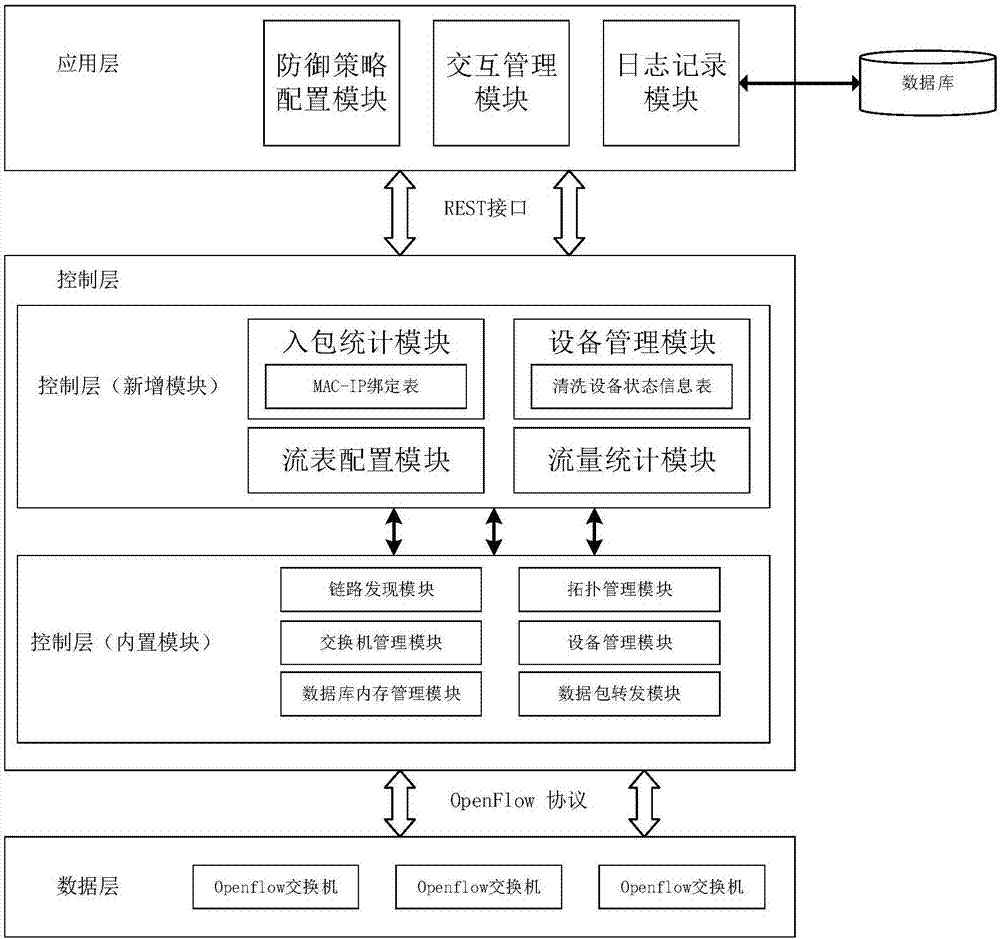
[0047] The present invention provides a DDoS attack defense system based on the synergy theory. The system architecture is mainly composed of two parts: an SDN controller and a cleaning device group.
[0048] Such as figure 1 As shown, the SDN controller includes modules located at the control layer and modules located at the application layer using the REST API interface provided by the controller. The modules at the control layer mainly include: incoming packet statistics module, traffic statistics module, flow table configuration module and device management module. The modules at the application layer mainly include: defense strategy configuration module, interaction management module and log recording module.
[0049] At the control layer of the SDN controller, the incoming packet statistics module is used to perform statistical analysis on the Packet-In packets sent to the controller, and based on the analysis results, it is determined that the switch under the false IP...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com