IEC61850-based detection method and system for detecting power industrial control network intrusions
A network control and intrusion detection technology, applied in transmission systems, electrical components, etc., can solve problems such as missing real attacks, detection accuracy needs to be improved, and spoofing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0106] In the following, the implementation cases of the present invention will be described in detail with reference to the accompanying drawings;
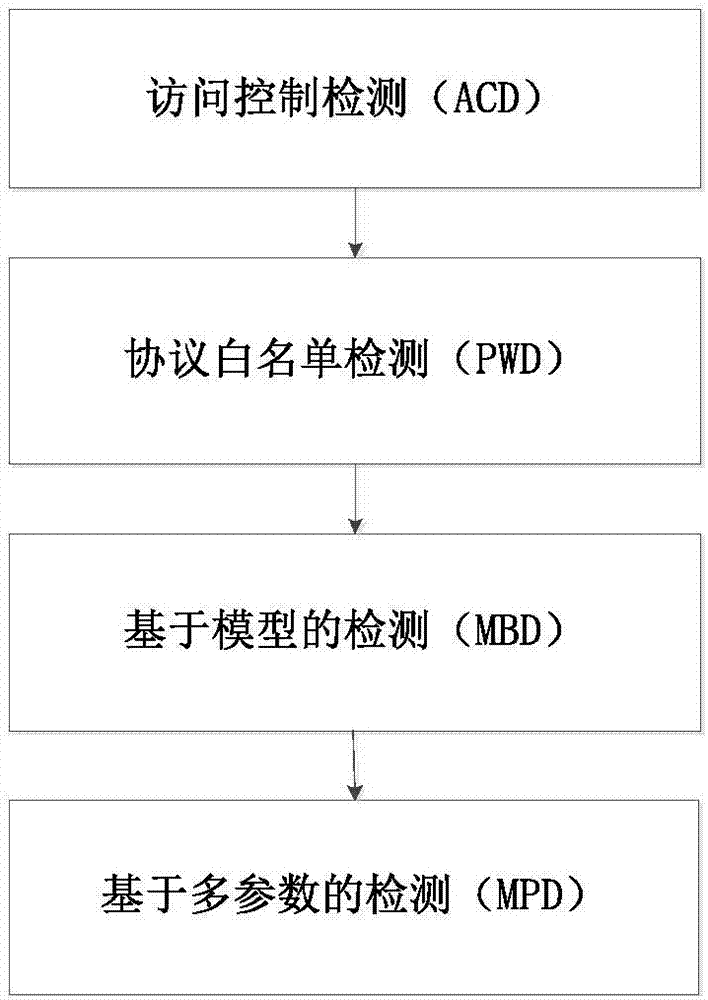
[0107] Such as figure 1 As shown, the IEC 61850-based intrusion detection method for electric power industry control network according to the present invention includes:
[0108] ACD access control detection: used to prevent malware activities and attacks that try to communicate with the control server during the initial infection stage; it includes the establishment of the MAC address in the data link layer, the IP address in the network layer and the access control of the transport layer port Whitelist, if any address or port is not in the corresponding whitelist, a preset action will be taken;
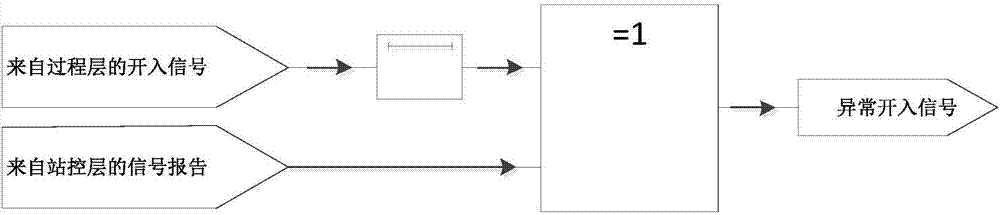
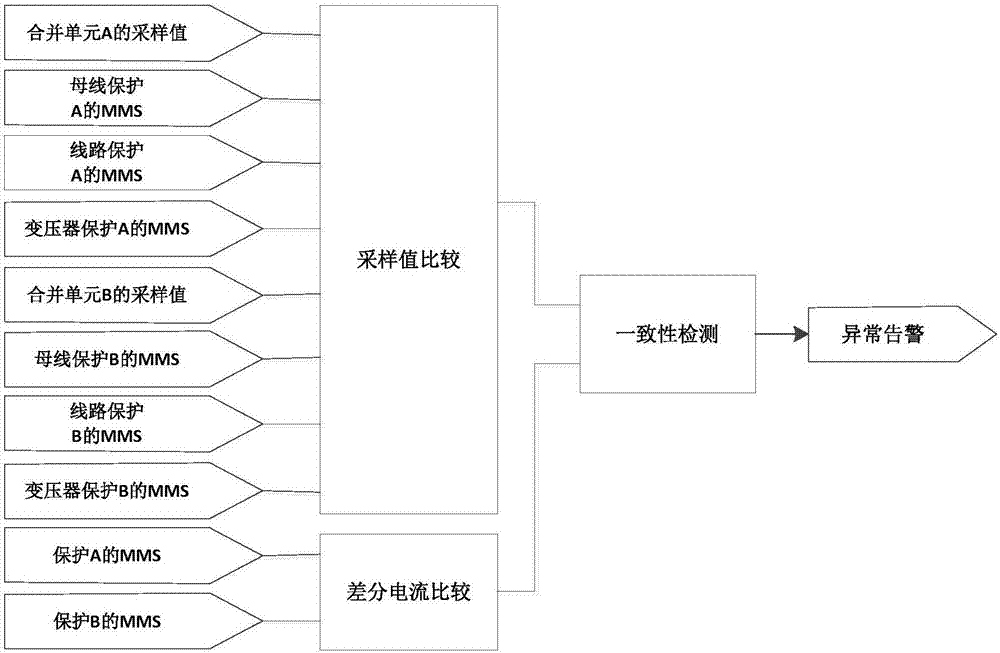
[0109] PWD protocol whitelist detection: used to detect abnormal protocol traffic in the station control layer network and process layer network of the substation and alarm; it includes the setting of various protocols supported by the stati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com