Industrial Internet Intrusion Detection Method Based on Traffic Feature Map and Perceptual Hash
A technology of industrial Internet and traffic characteristics, applied in the field of industrial Internet intrusion detection, can solve the problems of algorithm time complexity not meeting real-time requirements, poor adaptability, low intrusion detection performance, etc., achieve good intrusion detection performance and meet robustness performance, improve the effect of the hash digest matching method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
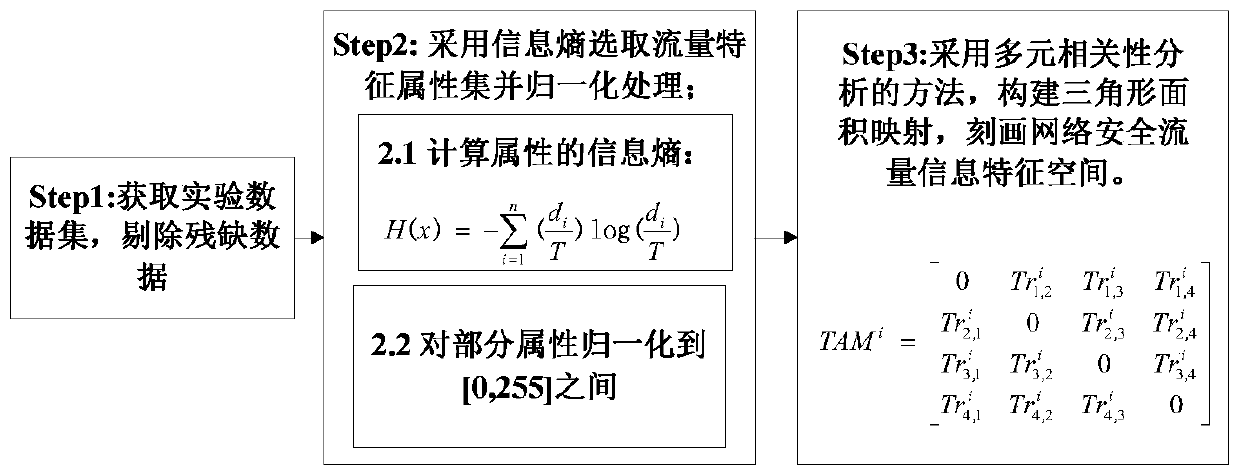
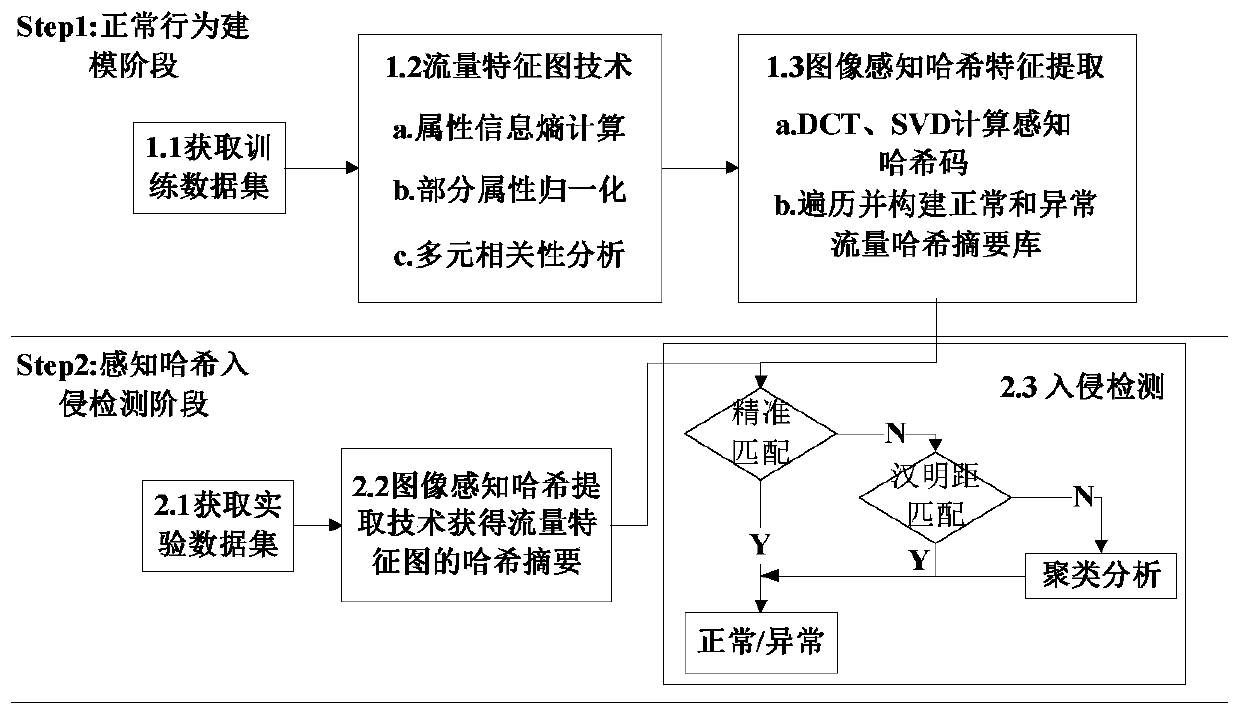
[0033] The invention is an industrial Internet intrusion detection method based on traffic characteristic graph and perceptual hash, and its steps include two stages of normal behavior modeling and perceptual hash intrusion detection.
[0034] (1) Normal behavior modeling stage;
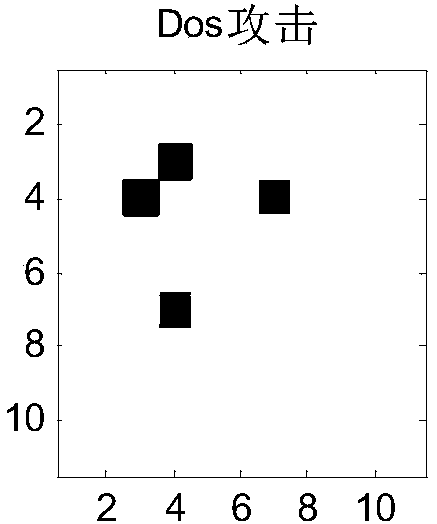
[0035] Using traffic feature map technology based on multiple correlation analysis, the traditional text traffic information of the industrial Internet is transformed into a traffic feature map, and the traditional research on the relationship within attributes is extended to the research on the relationship between attributes, and traffic features are mined from different angles. Specific steps are as follows:
[0036] (1a) Obtain the standard test experimental data set of the industrial Internet field network, perform preprocessing operations on the experimental data, and eliminate incomplete traffic data records;
[0037] (1b) Calculate the information entropy of each attribute of the experimenta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com