Security policy matching method based on onsite layer device, and onsite layer device
A security policy and field layer technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of complex security policy matching process, complex maintenance of table items to be matched, and slow matching speed, achieving a wide range and coverage Large range and good accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
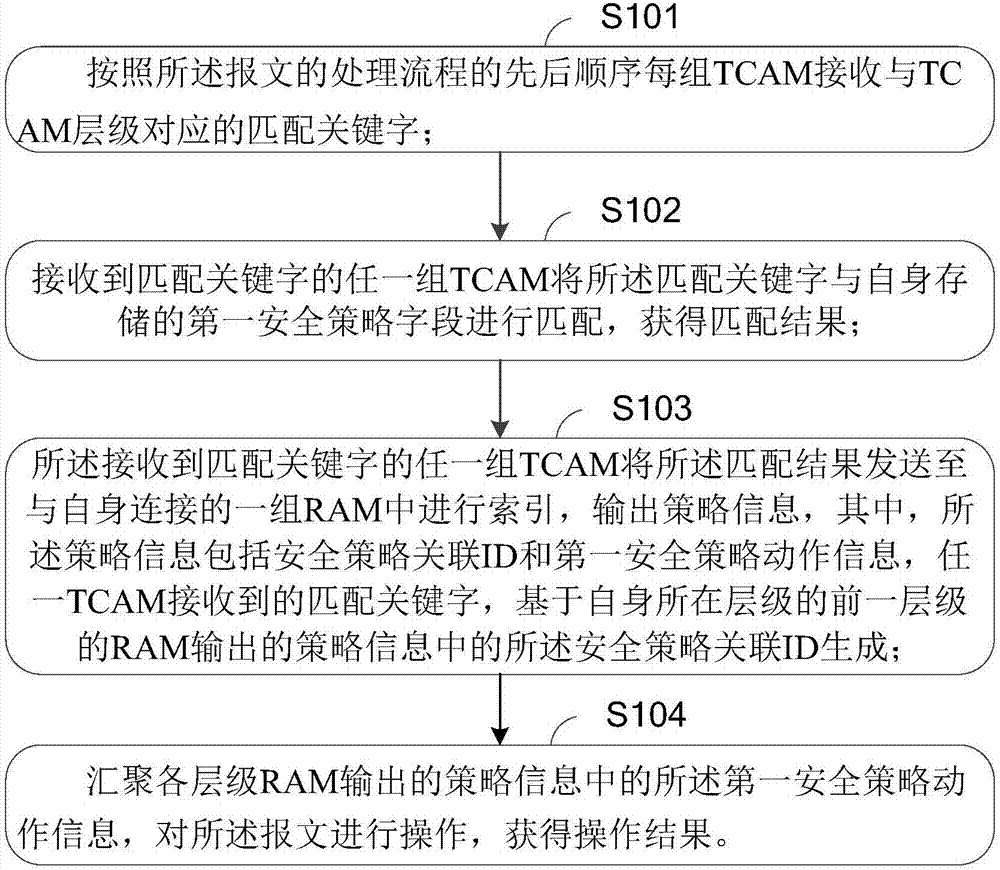
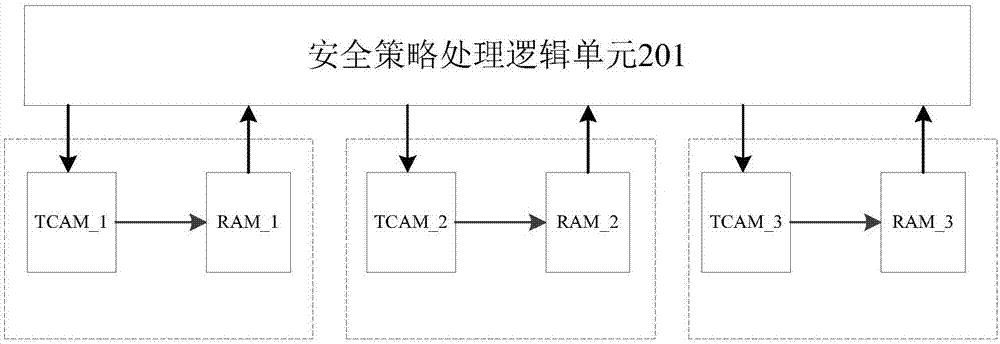
[0042] In order to better understand the above-mentioned technical solution, the above-mentioned technical solution will be described in detail below in conjunction with the accompanying drawings and specific implementation methods.
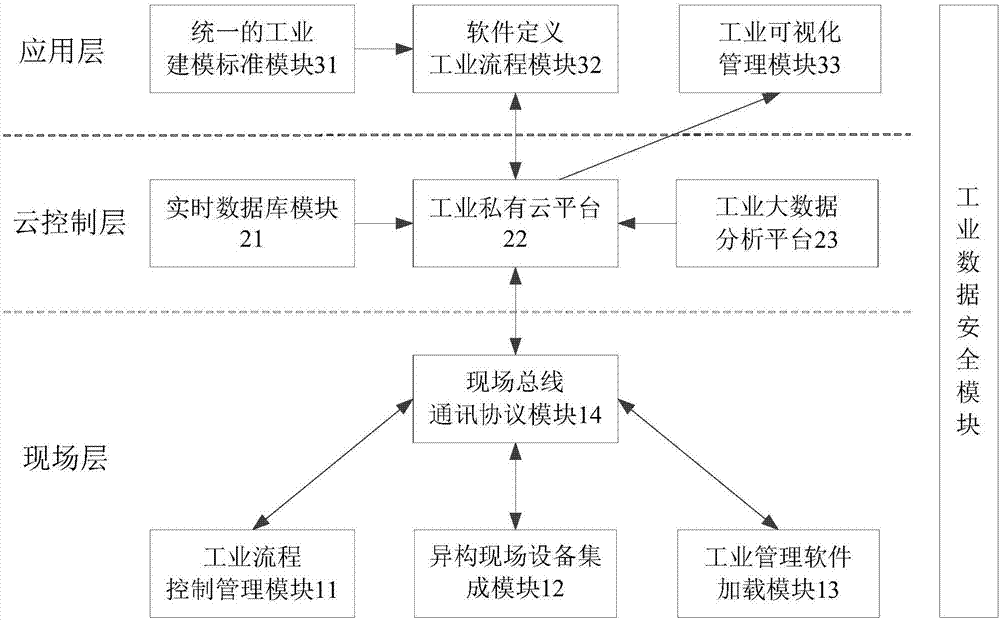
[0043] In practical applications, the industrial Internet operating system is the basic system for realizing networked industrial control, cloud industrial control, visualized factory and industrial big data analysis, etc. The unified system is a reliable guarantee for the controllability of industrial sites. like Figure 1A In the functional architecture diagram of the industrial Internet operating system shown, the industrial Internet operating system includes at least: application layer, cloud control layer and field layer, wherein the application layer includes at least: unified industrial modeling standard module 31, software-defined industrial process Module 32 and industrial visualization management module 33; cloud control layer at least in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com