Safe and credible networking system for deep sea observation
A trusted group and trusted technology, applied in transmission systems, wireless communications, network topology, etc., can solve problems such as being vulnerable to illegal access, difficult to prevent underwater robots from approaching survey and access, and Trojan horse implantation. Achieve the effect of major technological innovation and practical value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The technical solution of the present invention will be described in further detail below in conjunction with specific embodiments and accompanying drawings.
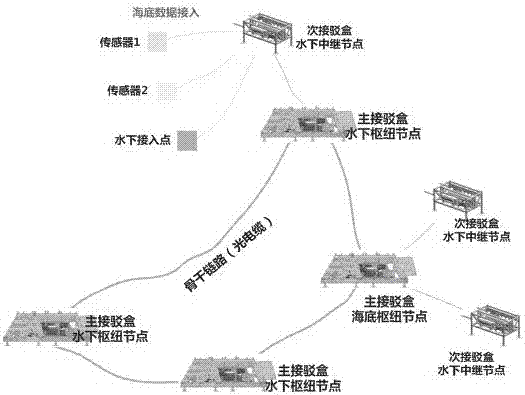
[0025] Such as figure 2 The schematic diagram of the seabed observation network structure shown mainly includes the interconnected main junction box hub node and the secondary junction box relay node, and the secondary junction box relay node is connected with various sensors and underwater access points.
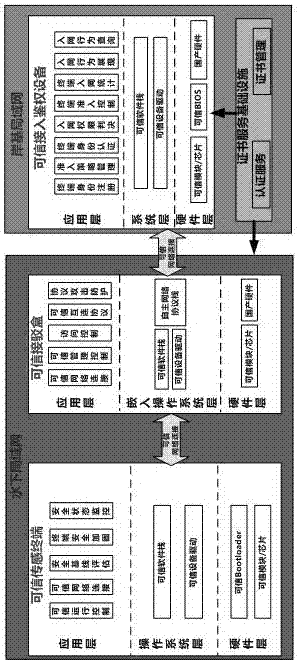
[0026] The biggest security risk facing this open and shared submarine observation network architecture is that it is difficult to prevent the enemy's underwater robots from approaching for survey and access. Compared with shore-based networks, they are more vulnerable to illegal access, virus intrusion, Trojan horse implantation, data tampering and other security attacks.
[0027] Such as figure 1 As shown, a deep-sea observation safety and trusted networking system proposed by the present invention includ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com