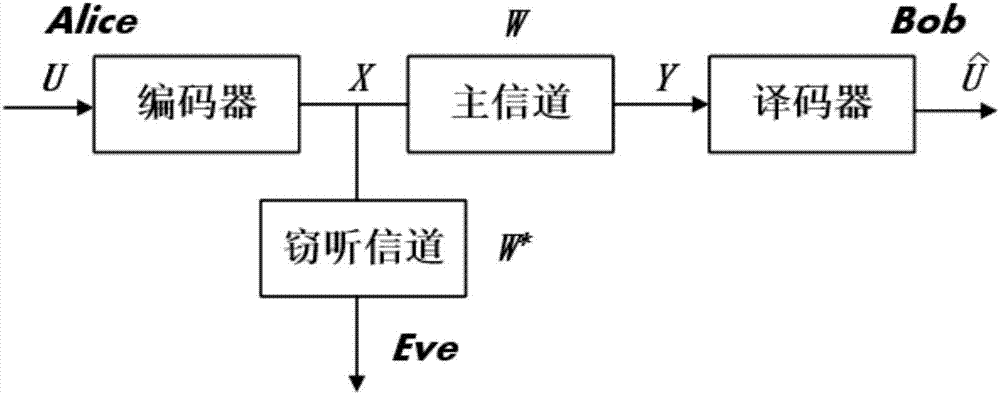
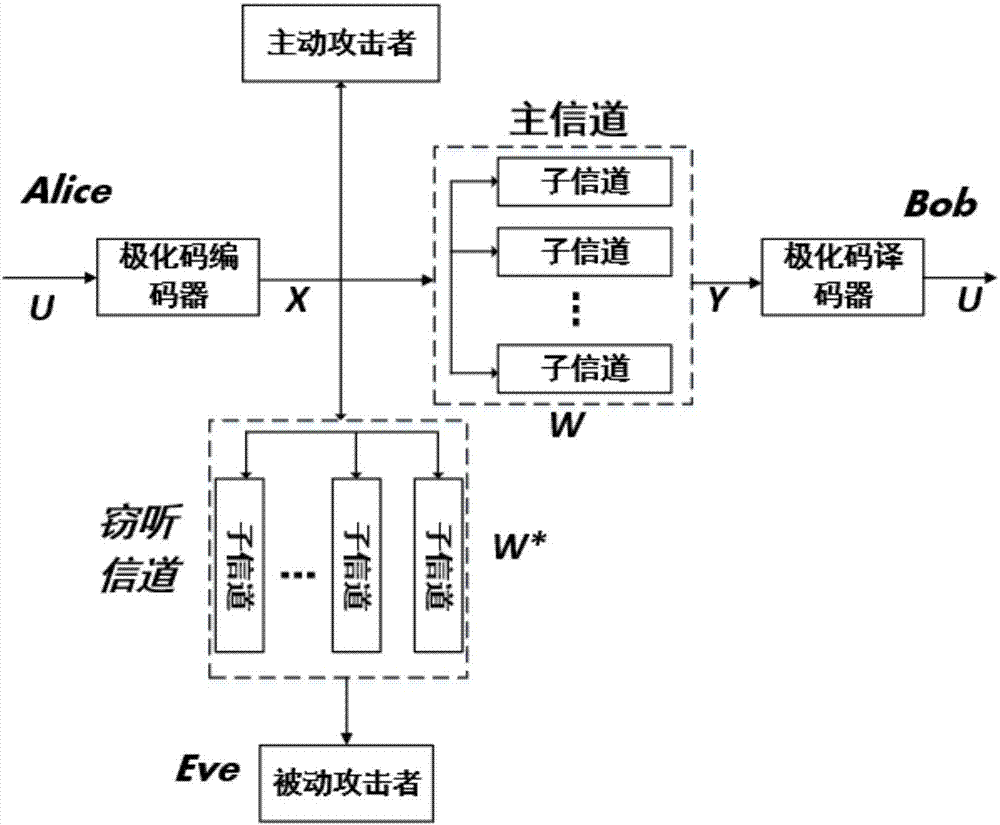
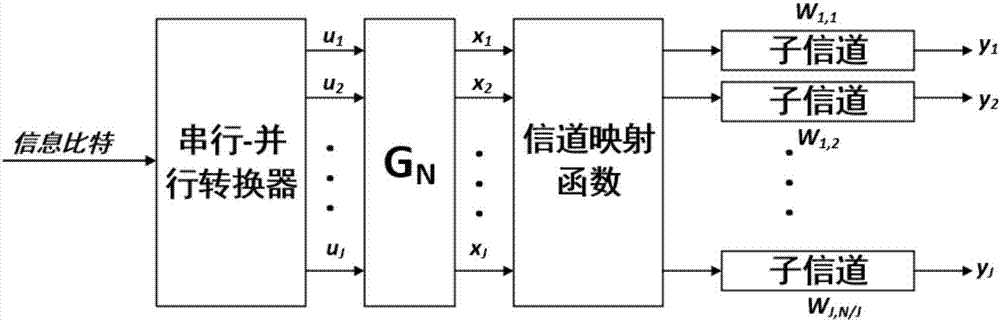
Security transmission method based on polarization code under parallel channel
A technology for secure transmission and polar codes, applied in the field of physical layer security, it can solve the problems that assumptions may not be established, the eavesdropping channel and the main channel do not satisfy the degradation relationship, etc., and achieve a wide range of application scenarios.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The implementation of the method of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0026] Let the code length be 1024, the information sequence length be 512, and the code rate be The channel is a parallel Additive White Gaussian Noise (AWGN, Additive White Gaussian Noise) channel, and the parallel channel contains 32 sub-channels. The decoding method uses a list-based serial cancellation (SCL, Successive Cancellation List) decoding algorithm, and the search path L =32. A polar code-based secure transmission method under parallel channels, comprising the following steps:
[0027] Step 1, channel quality selection. The 32 parallel sub-channels are used M=1024 / 32=32 times to construct 1024 polarized sub-channels, and the channel quality of the 1024 polarized sub-channels is calculated and sorted.
[0028] Step 2: Construct the sequence u to be encoded. Select 512 positions with the best channel quality from th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com