A method and device for protecting against advanced persistent threats
A technology of business characteristics and behavior, applied in transmission systems, electrical components, etc., can solve problems such as increasing operating costs and reducing effectiveness of enterprises, and achieving the effect of curbing APT attacks, easy operation, and reducing operating costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
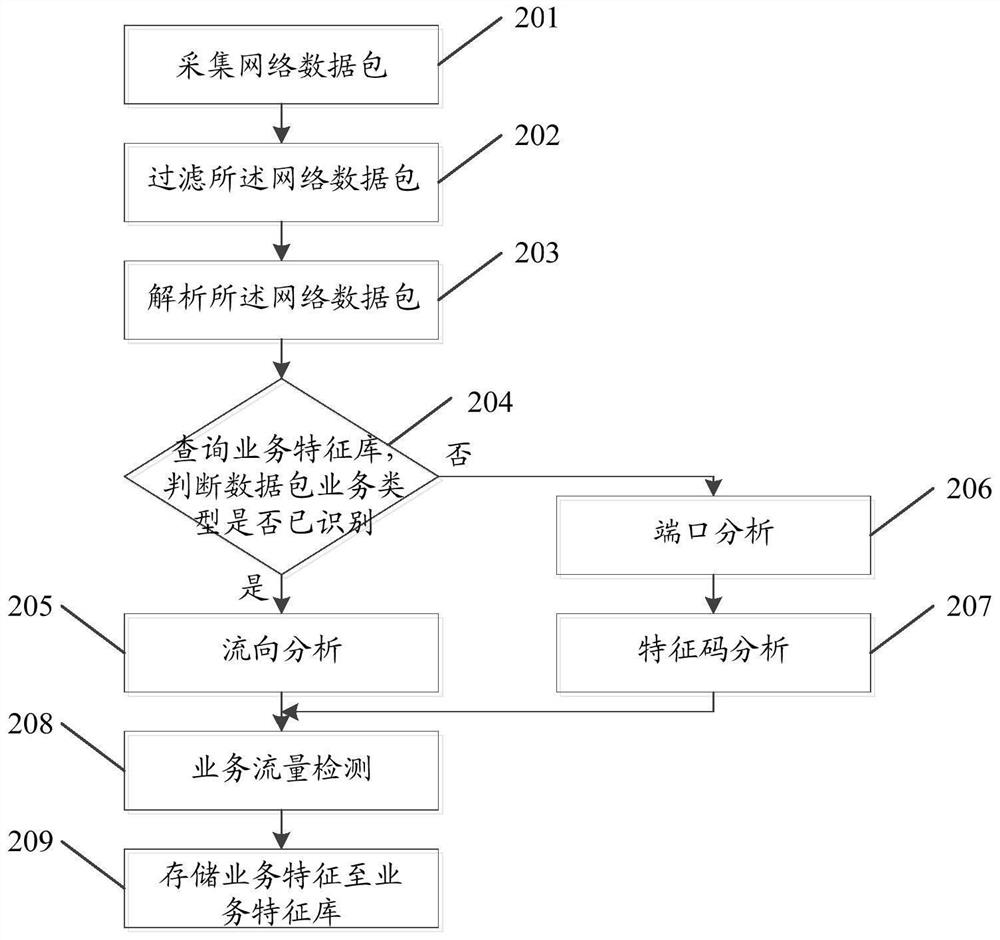
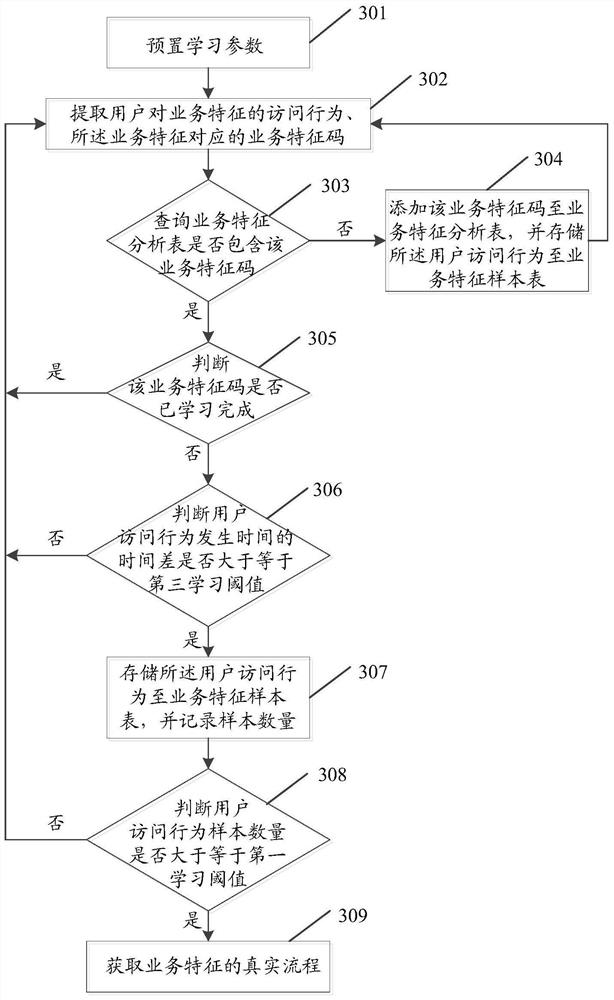
Image
Examples
Embodiment Construction
[0065] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
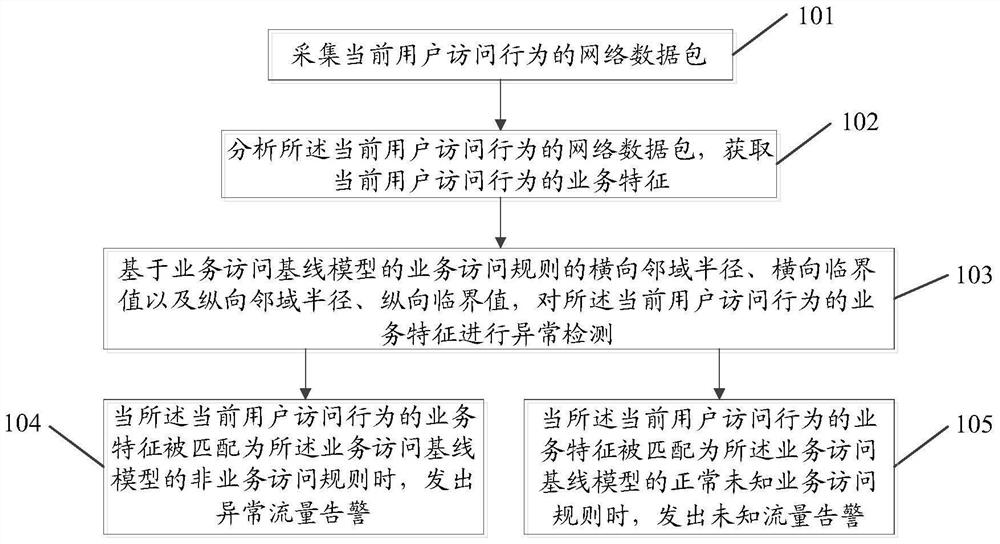
[0066] figure 1 It is a schematic diagram of the implementation flow of the advanced persistent threat attack protection method in the embodiment of the present invention, as shown in figure 1 As shown, the method includes:
[0067] Step 101: collecting network data packets of current user access behavior;
[0068] Step 102: analyzing the network data packets of the current user's access behavior to obtain the service characteristics of the current user's access behavior;
[0069] Step 103: Based on the horizontal neighborhood radius, horizontal critical value, vertical neighborhood radius, and vertical critical value of the business access rule of the business access baseline model, perform anomaly detection on the service characteristics of the current user's access behavior;
[0070] Step 104: When the business feature of the cu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com