Method and device for preventing UDP Flood attack
A message and terminal technology, applied in the direction of digital transmission system, electrical components, transmission system, etc., can solve the problem of ineffective protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
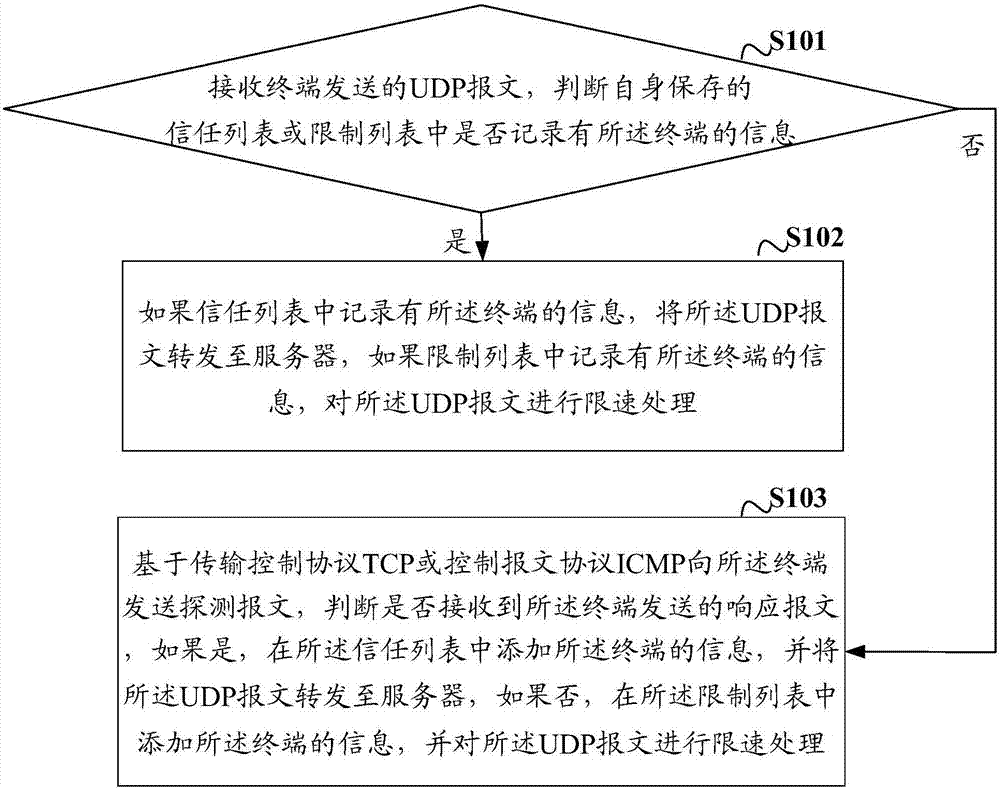
[0035] figure 1 A schematic diagram of the protection process of a UDP Flood attack provided by the embodiment of the present invention, the process includes the following steps:
[0036] S101: Receive a UDP packet sent by a terminal, and judge whether information about the terminal is recorded in a trust list or a restriction list saved by itself.
[0037] The protection method against UDP Flood attack provided by the embodiment of the present invention is applied to the cleaning device, and the cleaning device stores a trust list and a restriction list, and the trust list and the restriction list record terminal information, and the terminal information can be terminal IP address. The cleaning device may be a product that resists UDP Flood attacks, for example: NSFOCUS Anti-DDoS System (NSFOCUS ADS) of NSFOCUS Technology, and may also be a device such as a gateway with protection functions. In addition, the embodiments of the present invention The terminal in can be a devi...
Embodiment 2
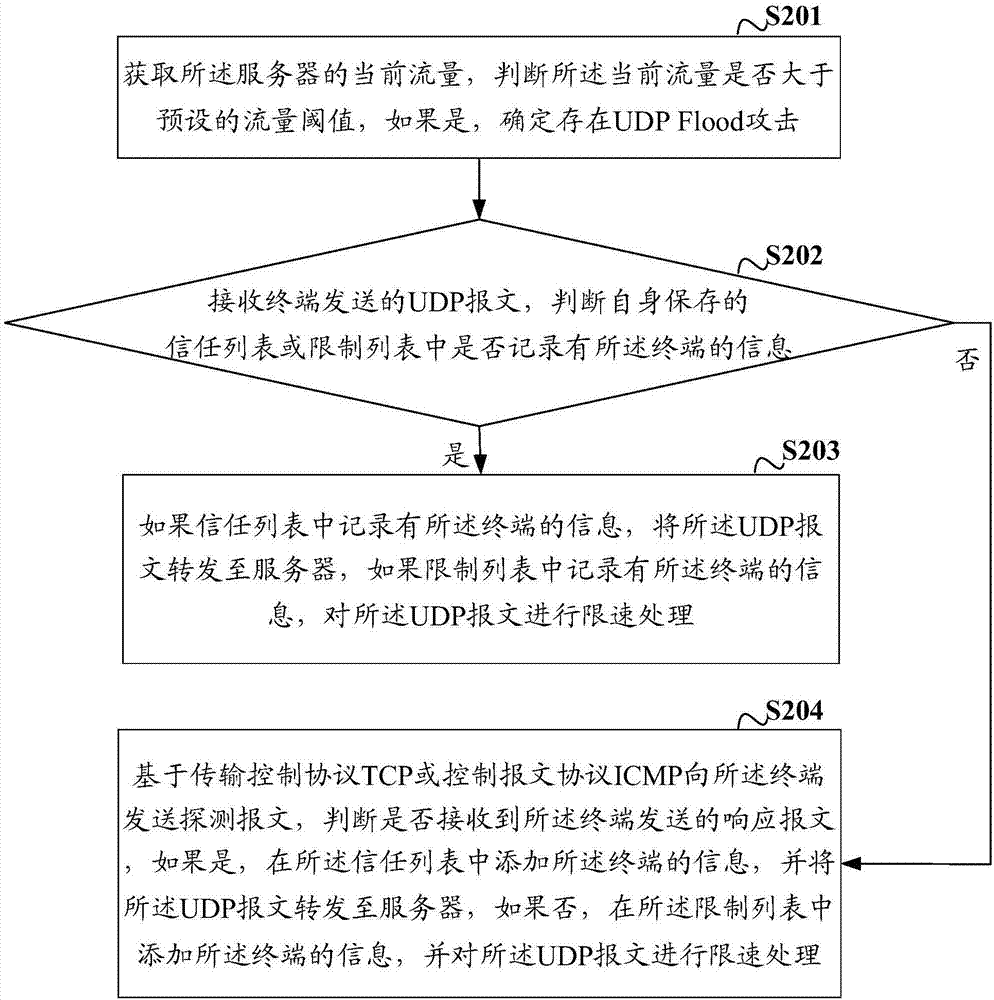
[0052] Since the protection method provided in this case is aimed at UDP Flood attacks, before the protection, it can be judged whether there is a UDP Flood attack. If it is judged that there is no UDP Flood attack, no protection is required. Protect against UDP Flood attacks. In order to save the protection resources of the cleaning equipment, on the basis of the above-mentioned embodiments, in the embodiments of the present invention, before the judging whether the information of the terminal is recorded in the trust list or restriction list saved by itself, the method further includes :
[0053] Acquiring the current traffic of the server, judging whether the current traffic is greater than a preset traffic threshold, and if so, determining that there is a UDP Flood attack, and performing subsequent steps.
[0054] After the cleaning device receives the UDP message sent by the terminal, before judging whether the information of the terminal is recorded in the trust list or...
Embodiment 3
[0064] In order to improve the accuracy of determining the authenticity of the terminal, on the basis of the above embodiments, in the embodiment of the present invention, the judging whether the response message sent by the terminal is received includes:
[0065] Judging whether the response message sent by the terminal is received within the first set time period.
[0066] According to the rules of the TCP protocol and the ICMP protocol, after the cleaning device sends a detection message to the terminal based on the TCP protocol or ICMP protocol, the terminal will send a response message to the cleaning device within a set period of time, that is to say, the cleaning device The device will receive the response message sent by the terminal within the set time period. If the response message sent by the terminal is received within the set time length, it can be considered that the terminal satisfies the TCP protocol or the ICMP protocol, and therefore, it can be determined th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com