Time-triggered in-vehicle network message authentication method based on hierarchical multi-layer one-way key chain
An in-vehicle network, time-triggered technology for key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0065] Include the following steps:
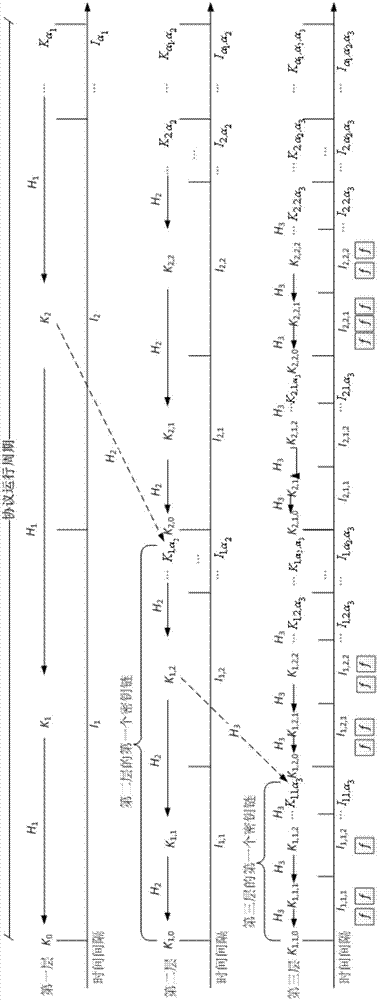
[0066] The first stage: the sending node is initialized. In this stage, the sending node builds a hierarchical multi-layer one-way key chain, and credibly distributes the initial key of the first key chain of each layer to its receiving node;
[0067] The second stage: send the node multicast verification message and key;
[0068] The third stage: the receiving node verifies the received message and key;
[0069] In the first stage of the present invention, the sending node constructs a hierarchical multi-layer one-way key chain including the following steps:
[0070] Definition 1: The structure of a hierarchical n-layer unidirectional key chain is defined as a set S={(α 1 ,β 1 ),(α 2 ,β 2 ),...,,(α n ,β n )}, where α i and beta i Respectively used to indicate the length of each one-way key chain of the i-th layer (i∈[1,...n]), excluding its initial key and key size;
[0071] Definition 2: The key generation function of a hierarc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com