Industrial control operation system active defense method with self-learning characteristic
An operating system and active defense technology, applied in platform integrity maintenance, instruments, electrical digital data processing, etc., can solve problems such as difficulty in updating industrial control system patches, inapplicability to industrial control environments, and poor business adaptability, etc., to meet business needs, Good compatibility, the effect of resisting hacker attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
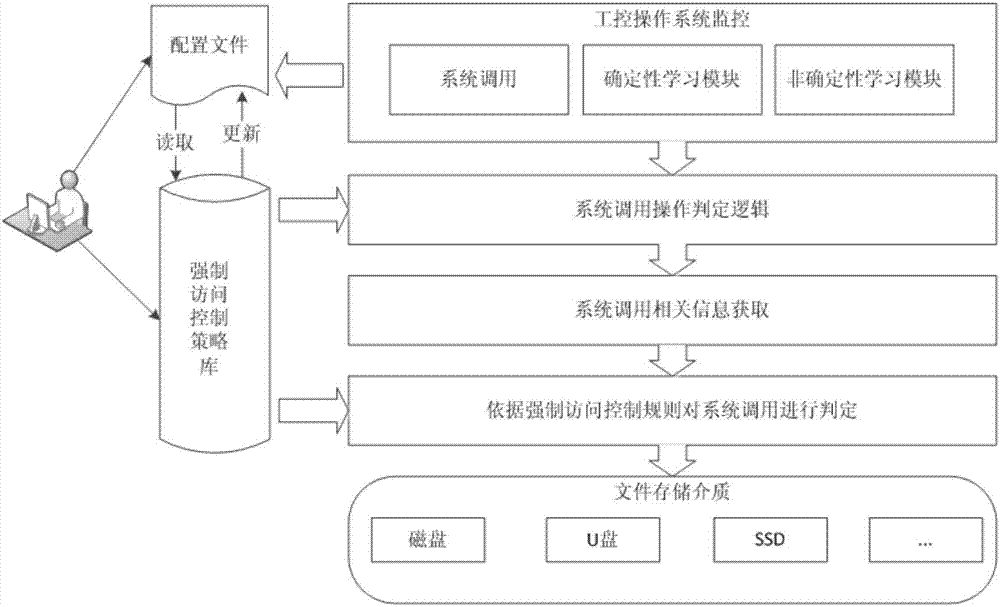
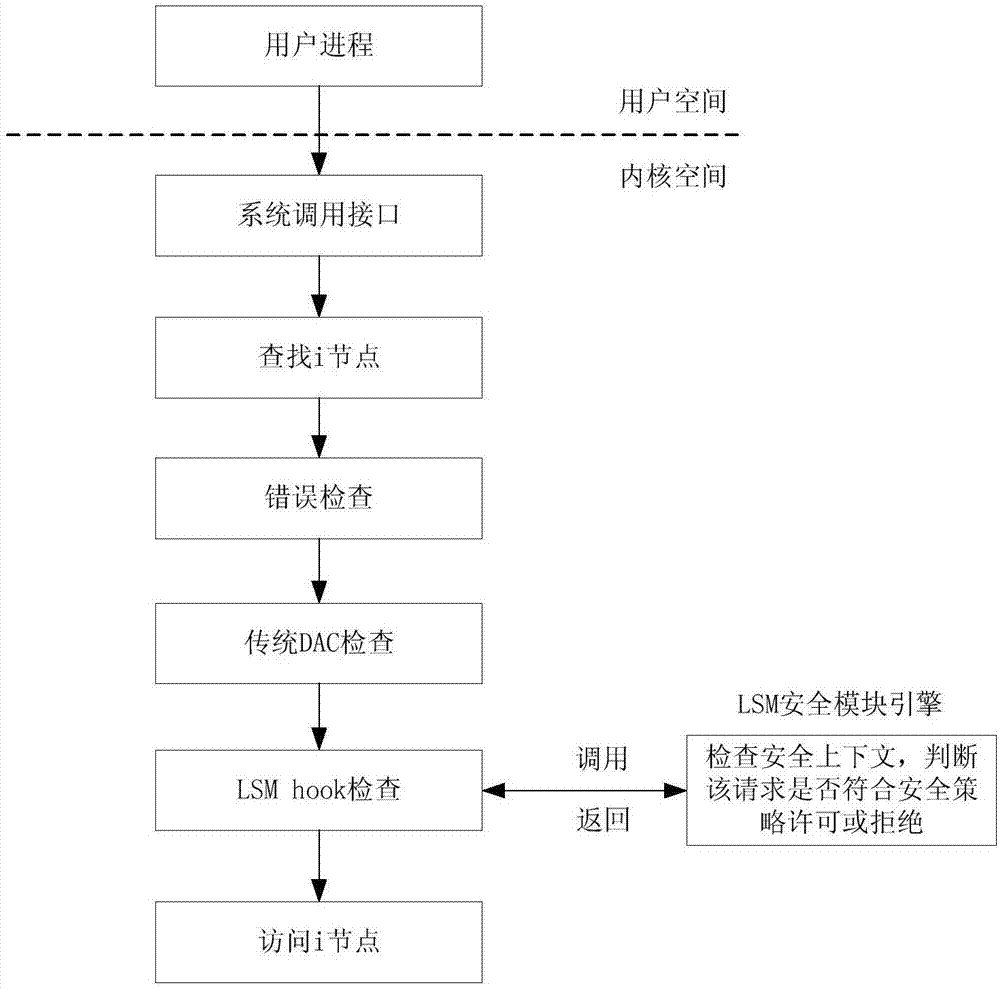
[0025] Such as figure 1 Shown, a kind of industrial control operating system active defense method with self-learning characteristic, this method is realized based on Linux LSM, comprises the following steps:
[0026] Step 1: Determine whether the program can be executed according to the trusted policy, monitor business behavior if it is executable, and complete deterministic security policy learning based on the detected subject-object access operations. The security policy library described here includes several rules, which define the access control rules of the subject to the object, and the trusted measurement value of the application.
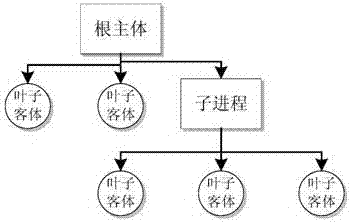
[0027] For this type of event, in addition to its own access to the corresponding object, the main program will call other executable programs for resource access in most cases. The final resource access sequence forms a tree structure. The initial subject is the root node of the tree. Leaf nodes represent the objects that are actually...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com