Patents
Literature
38results about How to "Adapt to business needs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
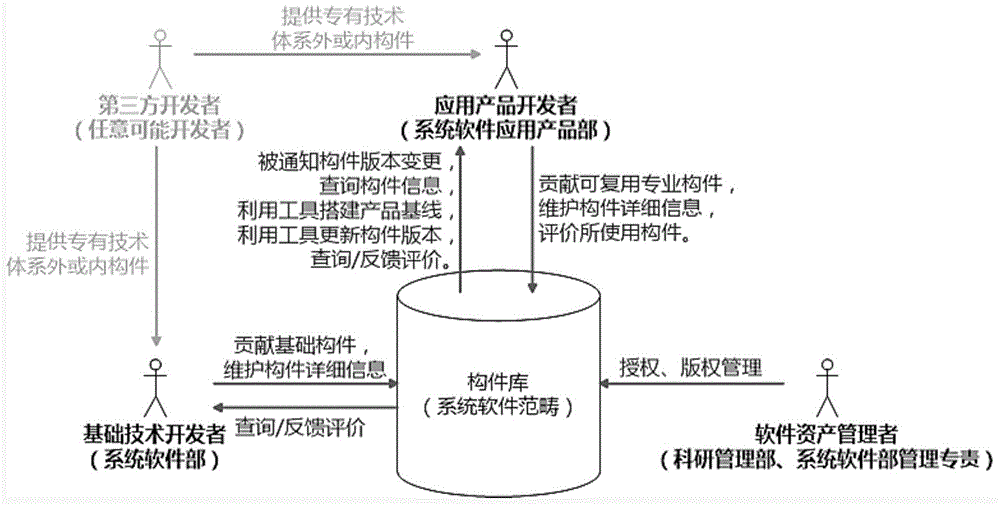
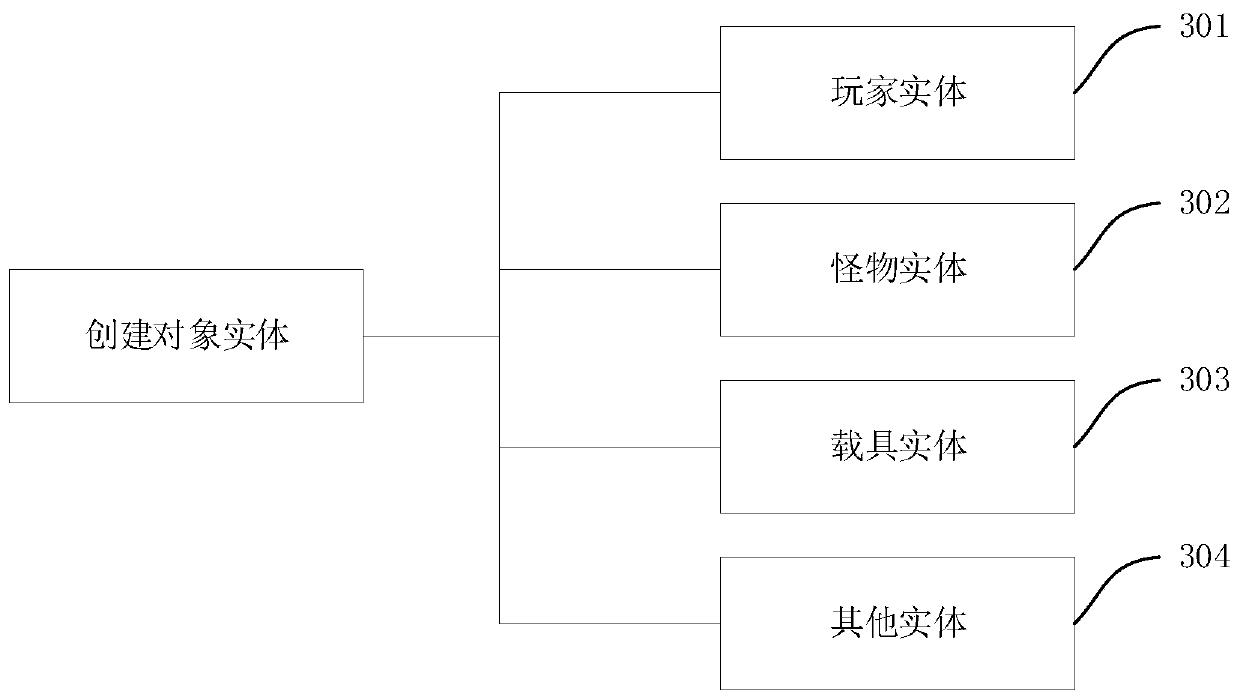
Platform-related model of large-granularity components and method of automatic code generation thereof
InactiveCN101533349AAchieve adaptationRealize multiplexingSpecific program execution arrangementsSoftware patternProgram code
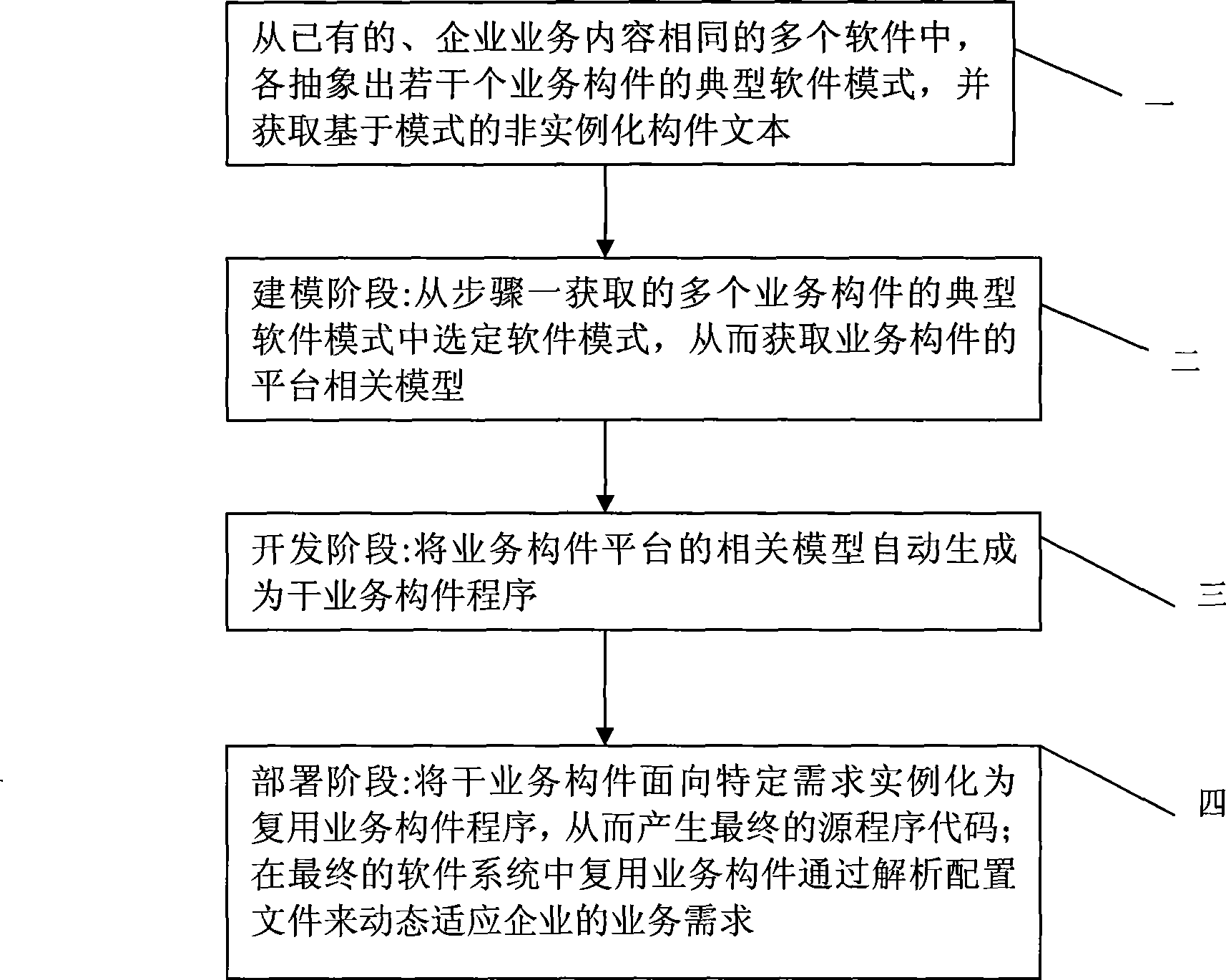
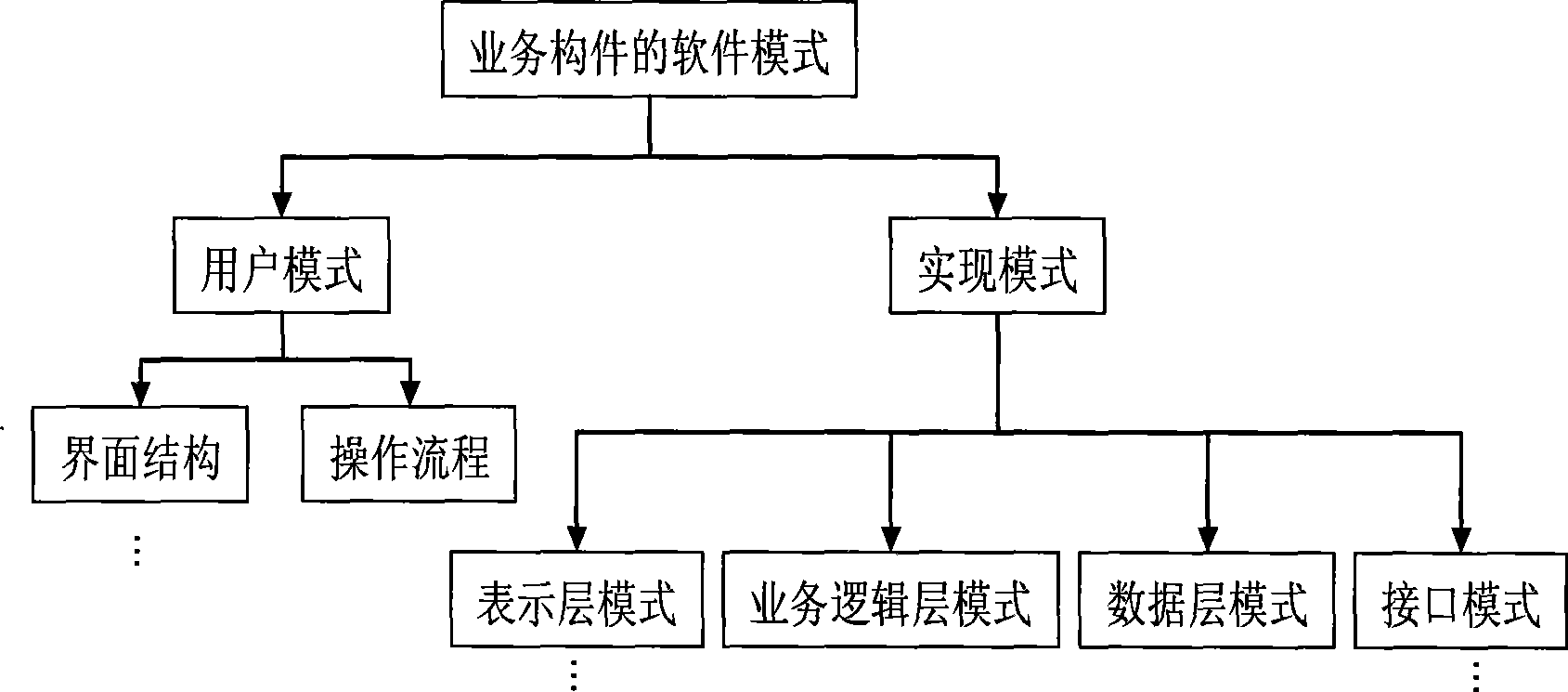
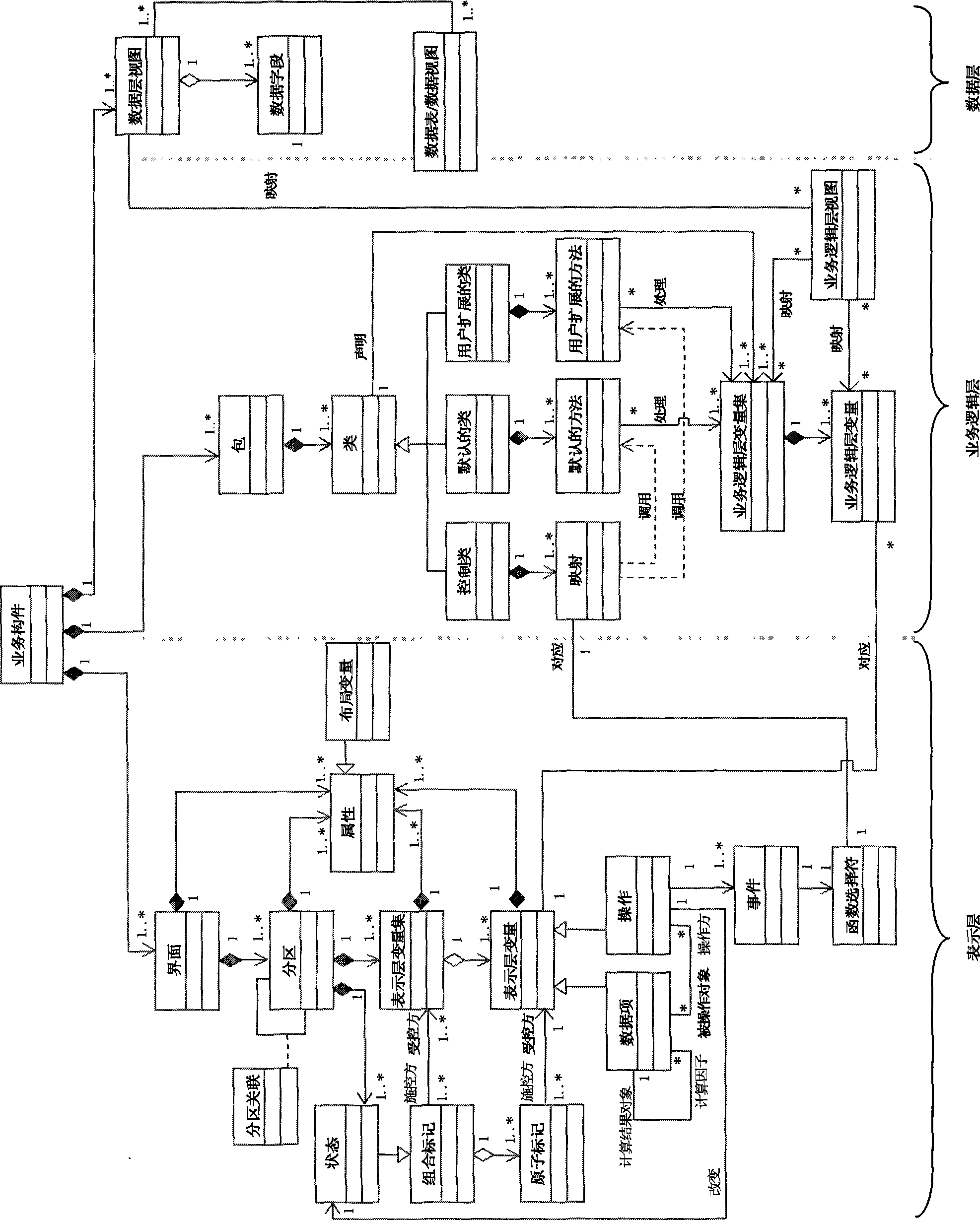
A platform-related model of large-granularity components and a method of automatic code generation thereof relate to the development method of model driven enterprise application softwares, and solve the prior problem of no modeling method of systematic specified large-granularity business component and shortcomings of lack of flexibility and variability of software generated by the prior art. The invention is realized by the following steps: abstracting typical software modes of a plurality of business components from the existing software with the same enterprise business content to acquire non-instantiating component texts based on the modes, selecting software modes from the typical software modes of the acquired business components and establishing platform-related models of the business components based on the specific software modes, automatically generating the platform-related models of the business components into main business component programs, instantiating the main business component programs into multiplexing business component programs based on the specific demands and generating the final source program codes, and dynamically adapting the business requirements of enterprises by analyzing configuration files using the business components in the final software system.
Owner:HARBIN INST OF TECH
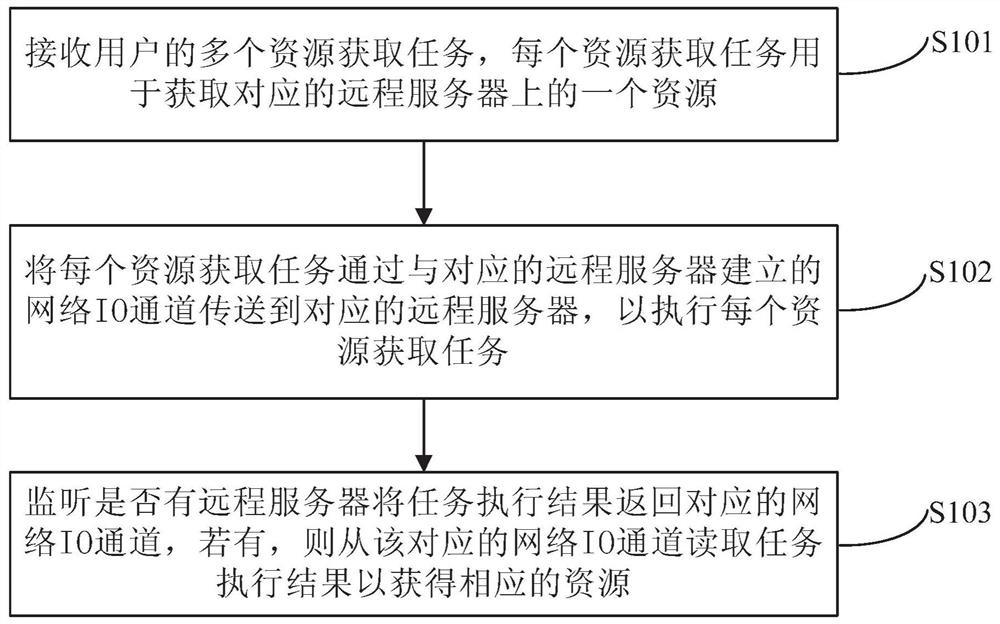
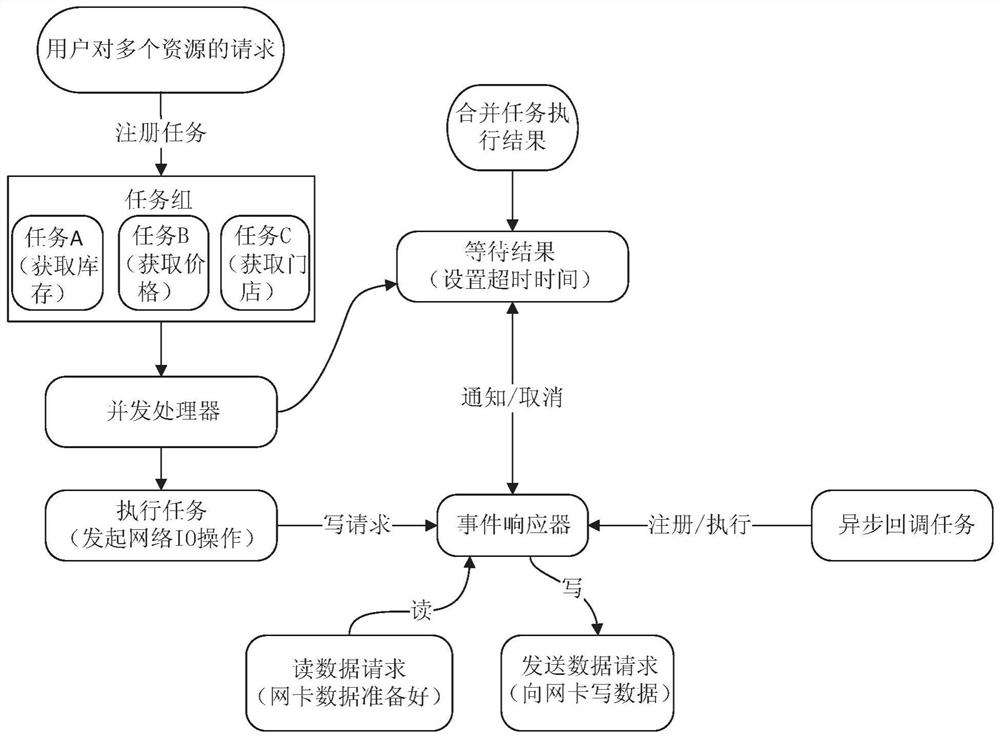
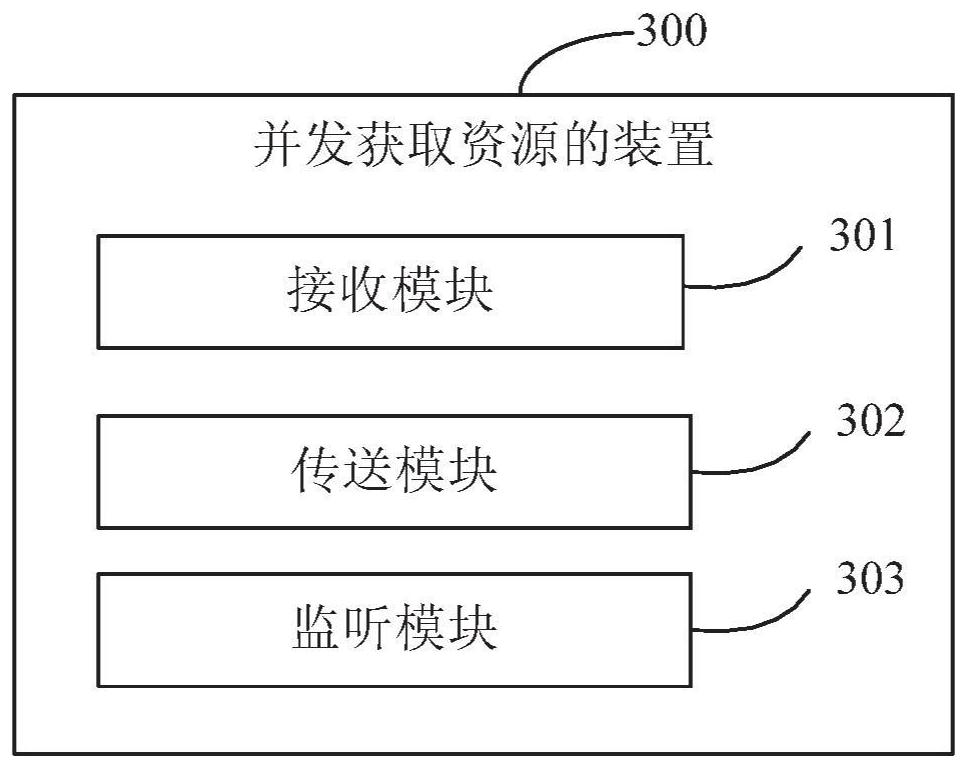
Method and device for concurrently obtaining resources
ActiveCN107729139AReduce overheadSatisfy concurrent processingResource allocationExtensibilityBusiness requirements
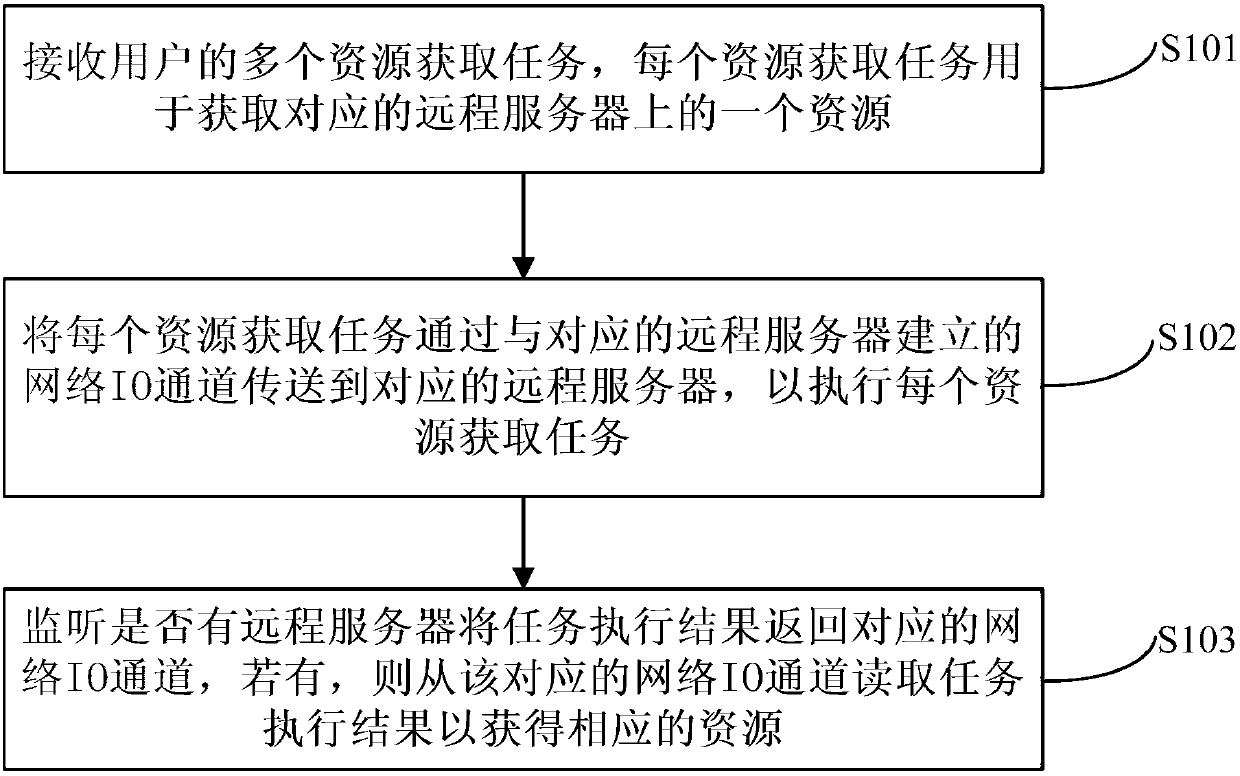
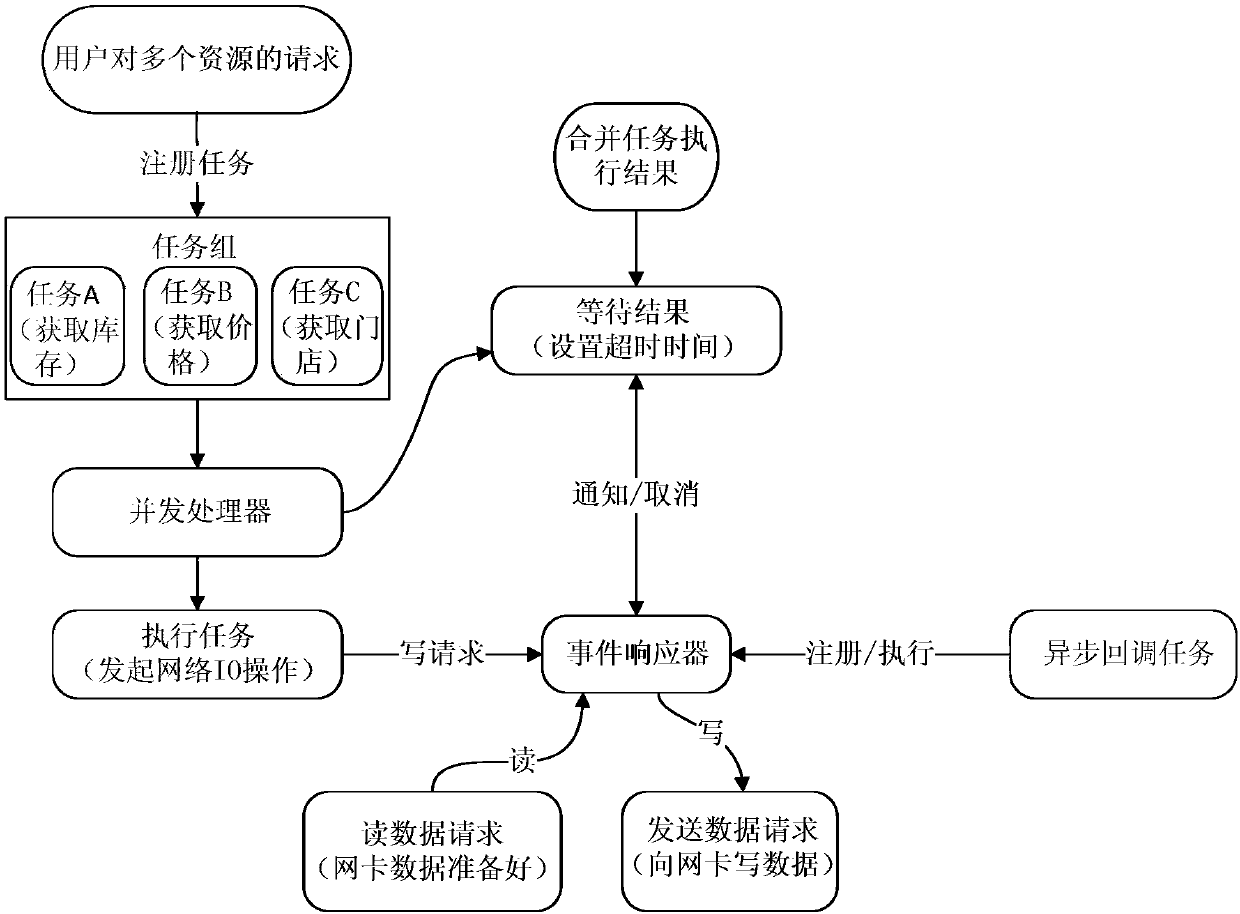
The invention discloses a method and device for concurrently obtaining resources, and relates to the technical field of computers. In one embodiment, the method comprises the steps that multiple resource obtaining tasks of a user are received, wherein each resource obtaining task is used for obtaining one resource on a corresponding remote server; the resource obtaining tasks are sent to the corresponding remote servers through network IO channels built by the resource obtaining tasks and the corresponding remote servers, so that the resource obtaining tasks are executed; whether or not a taskexecution result is sent back to the corresponding network IO channel by one remote server is monitored, and if yes, the task execution result is read from the corresponding network IO channel to obtain the corresponding resource. By means of the embodiment, the method and device do not need to rely on a thread pool, and concurrent treatment of all the business resources can be conducted simultaneously, so that the business requirements are well met, the transverse extensibility is high, the resources are recycled, the resource cost is reduced, and the development efficiency is improved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Improved data transmission method
ActiveCN106487487AImprove robustnessAdapt to business needsError prevention/detection by using return channelPilot signal allocationCommunications systemSignal on
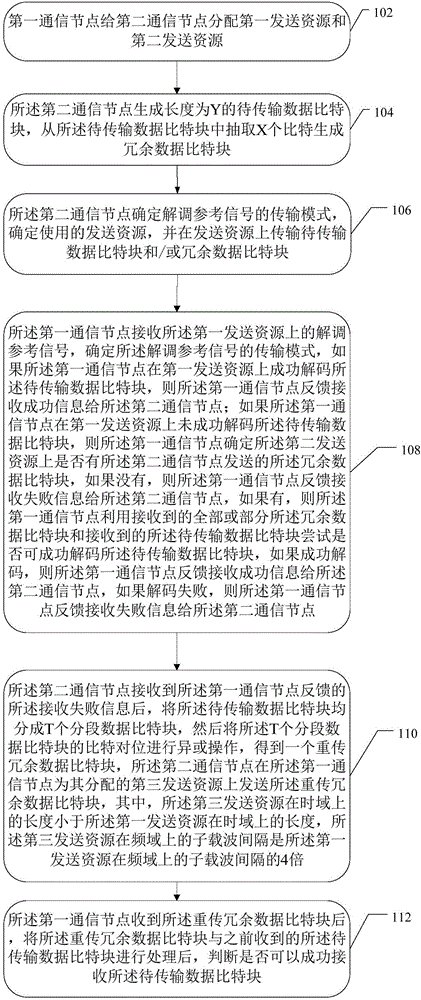
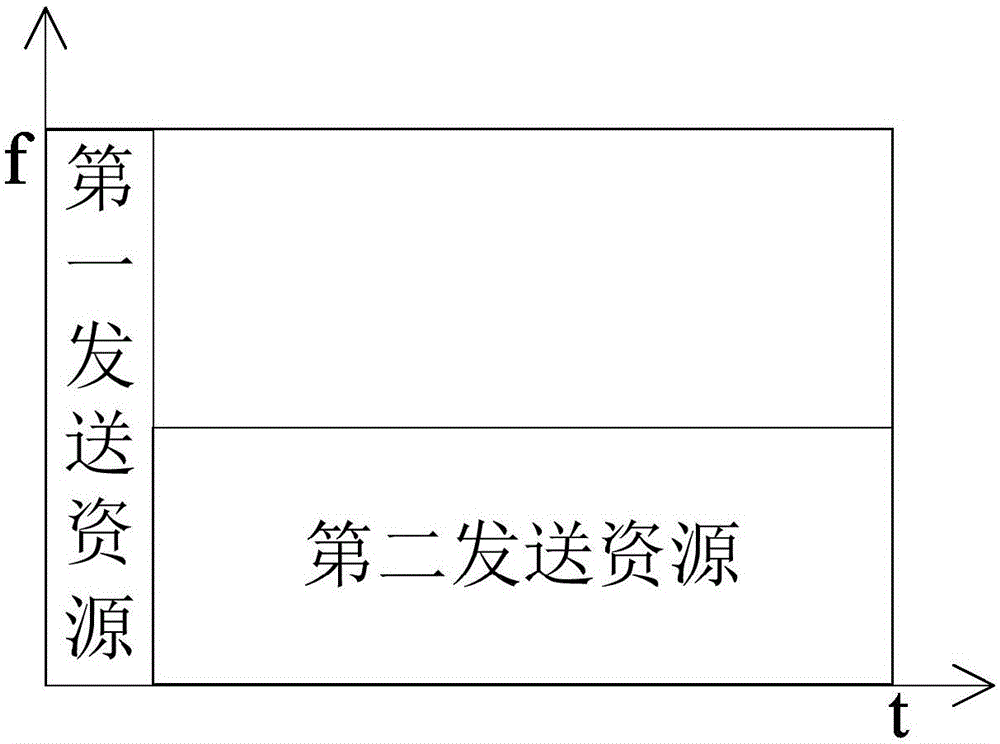
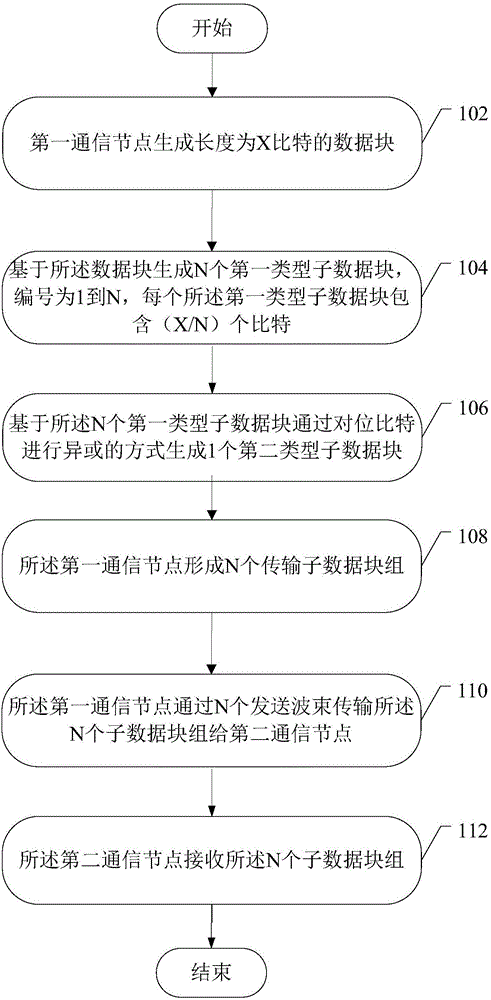
The invention provides an improved data transmission method comprising the following steps: a first communication node allocates a first sending resource and a second sending resource for a second communication node; the second communication node generates a to-be-transmitted data bit block which contains cyclic redundancy check information and of which the length is Y; the second communication node has three candidate demodulation reference signal transmission modes; the first communication node receives a demodulation reference signal on the first sending resource, determines the transmission mode of the demodulation reference signal, and feeds a message about reception success or failure back to the second communication node; after receiving reception failure information fed back by the first communication node, the second communication node generates a retransmitted redundant data bit block, and sends the retransmitted redundant data bit block on a third sending source allocated by the first communication node for the second communication node; and the first communication node processes the received retransmitted redundant data bit block and the previously-received to-be-transmitted data bit block. By using the method, the robustness of data transmission can be increased effectively to adapt to the service need of the fifth-generation wireless communication system.
Owner:SHENZHEN POLYTECHNIC
Data first transmission and retransmission method
ActiveCN106656435AImprove robustnessAdapt to business needsError prevention/detection by using return channelWireless communicationData transmissionSignal-to-noise ratio (imaging)
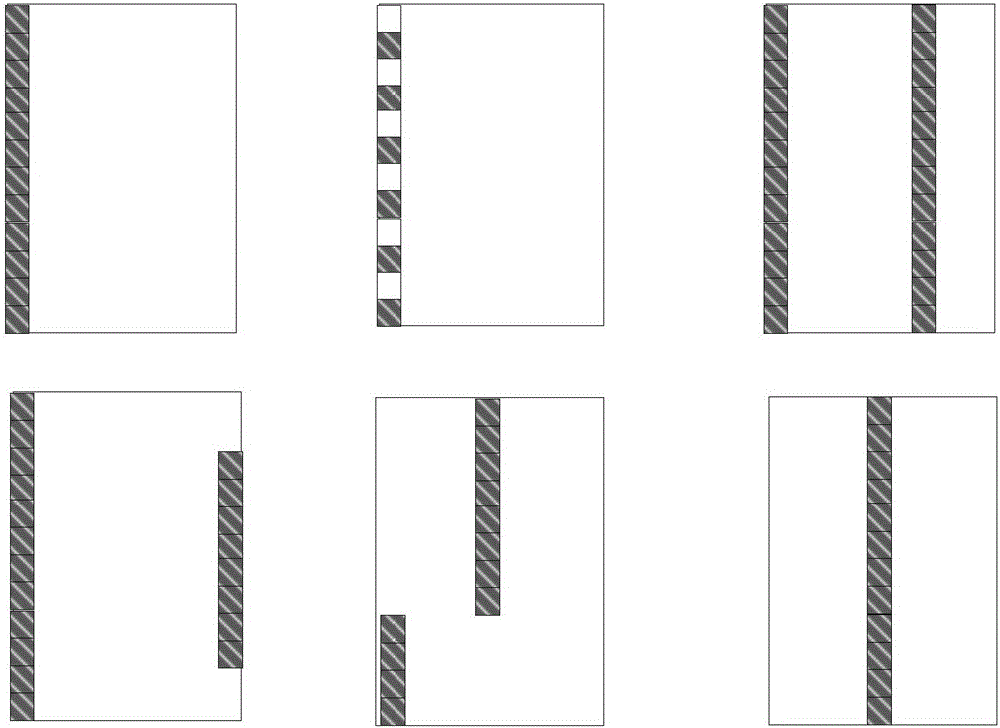
The invention provides a data first transmission and retransmission method, comprising: generating from an x-bit data block N first type sub-data blocks containing X / N bit; then, based on the N first type sub-data blocks, generating a second type sub-data block including X / N bit through the exclusive OR mode to the bit; based on the second type sub-data block, obtaining N third type sub-data blocks containing X / N2 bit; then, forming the N first type sub-data blocks and the N third type sub-data blocks as N transmission sub-data modules for transmission on N sending wave beams; utilizing the received third type sub-data blocks at a receiving terminal for an attempt to recover the first type sub-data blocks with errors; if the recovery is yet to be successful, then, replacing the third type sub-data blocks in the Y sub-data modules whose receiving signal-to-noise ratios are the poorest with the second type sub-data block for retransmission. The method of the invention can effectively increase the robustness for data transmission so as to adapt for the business requirement of a 5G communication system.
Owner:SHENZHEN POLYTECHNIC
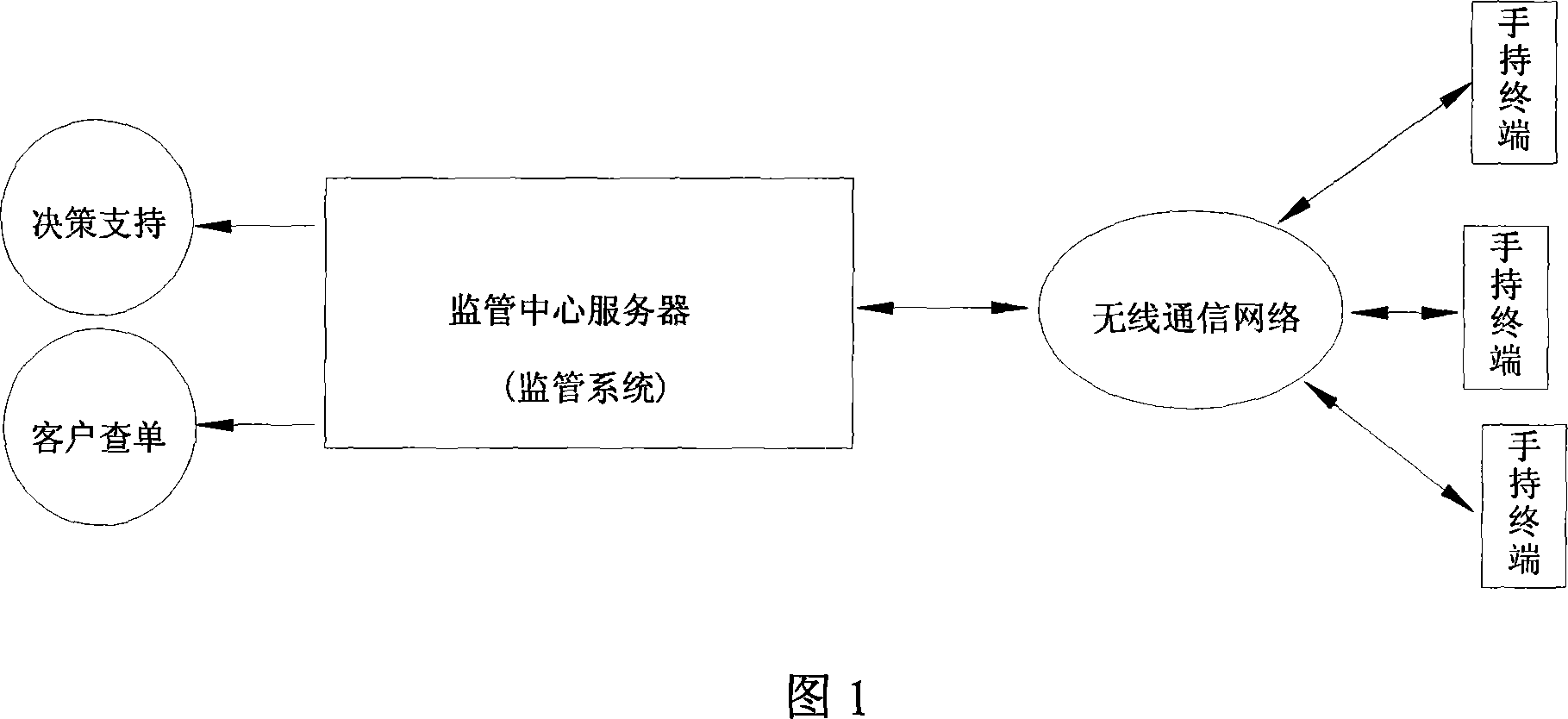
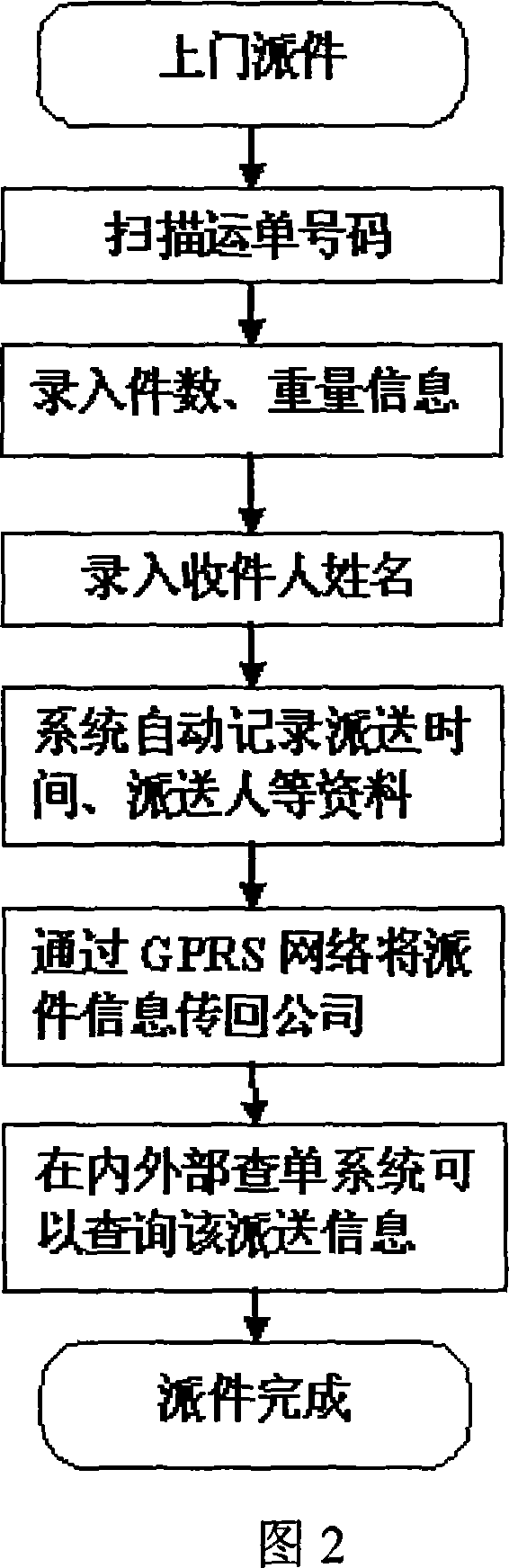
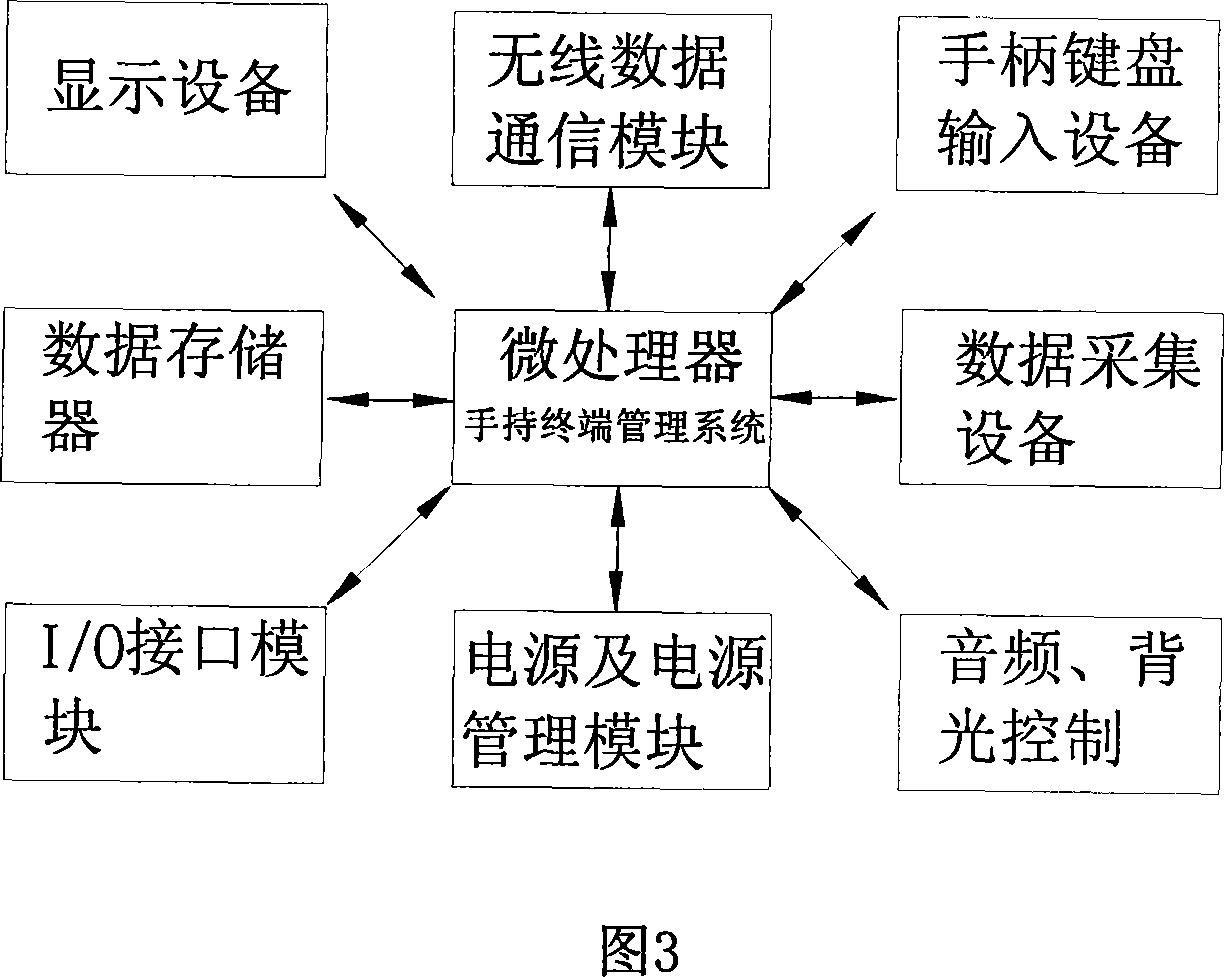
Logistic service tracking system and logistic service tracking method
InactiveCN101035311AHigh intelligenceFlexible collection and transmission of logistics informationTelephonic communicationBeacon systemsProcess stateFile transfer
This invention discloses a business logistics tracking system and logistics business tracking method, the system include: Set-defined operating procedures, data acquisition, storage, processing, display, manual and wireless communications, cell phone text messages, calls, and other functions in a handheld terminal; Set custom handheld terminals operating procedures, monitoring, tracking and logistics process state information with a handheld wireless communication terminals in a monitoring center server; to achieve handheld terminal server with the regulatory centers of communication between the wireless communications network. The methods include: handheld terminal on the above-defined procedures, file transfer, since the definition of that scene, such as acquisition process. This invention logistics business operations and logistics tracking system tracing method is the definition of application system, a high degree of intelligence, and logistics operations tightly integrated, flexible transmission of information acquisition, real-time, highly efficient, without secondary development, system implementation and low cost advantages.
Owner:深圳市比特威软件科技有限公司
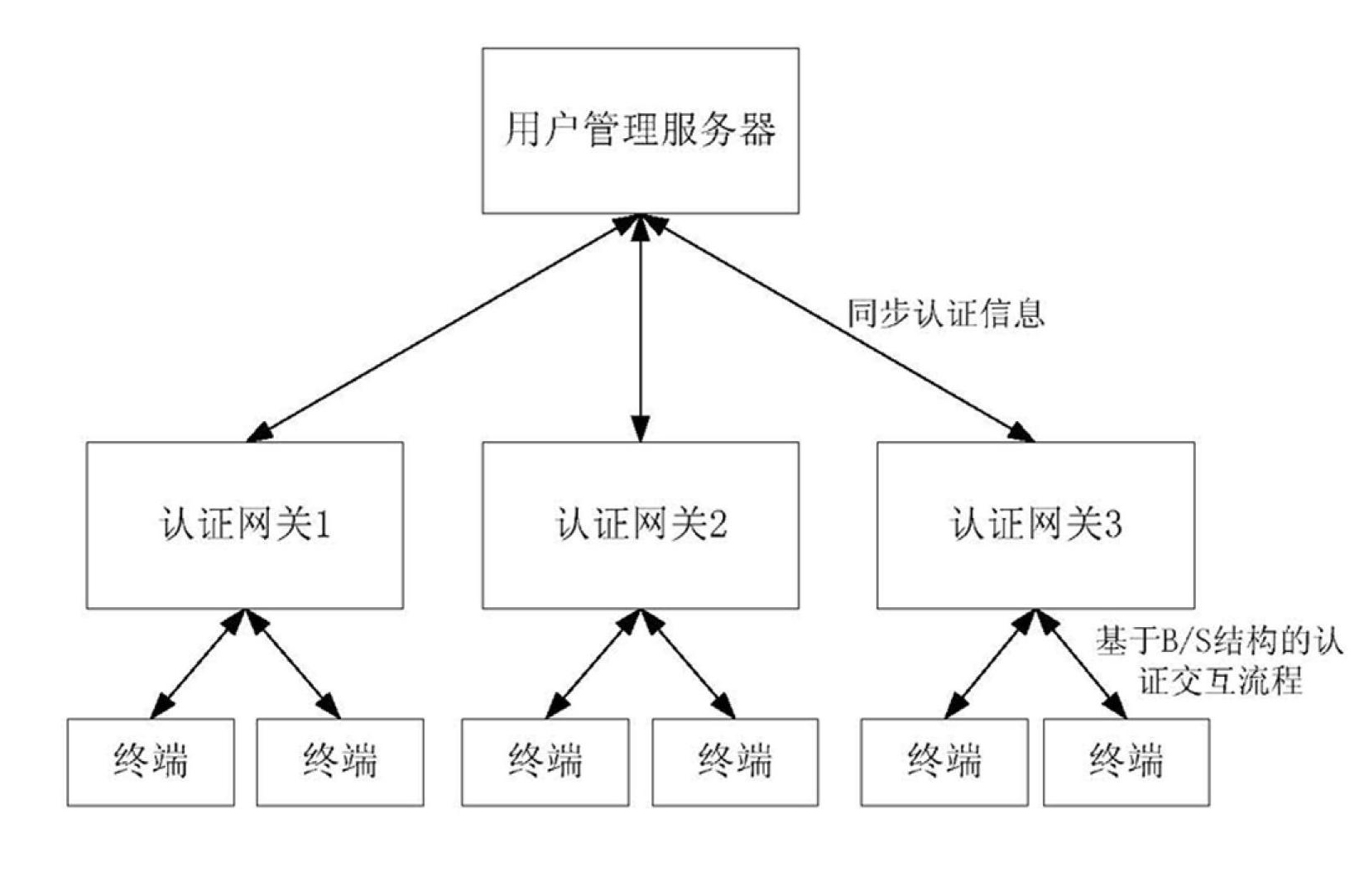
User authentication method for extensible and distributed wireless local area network (WLAN)
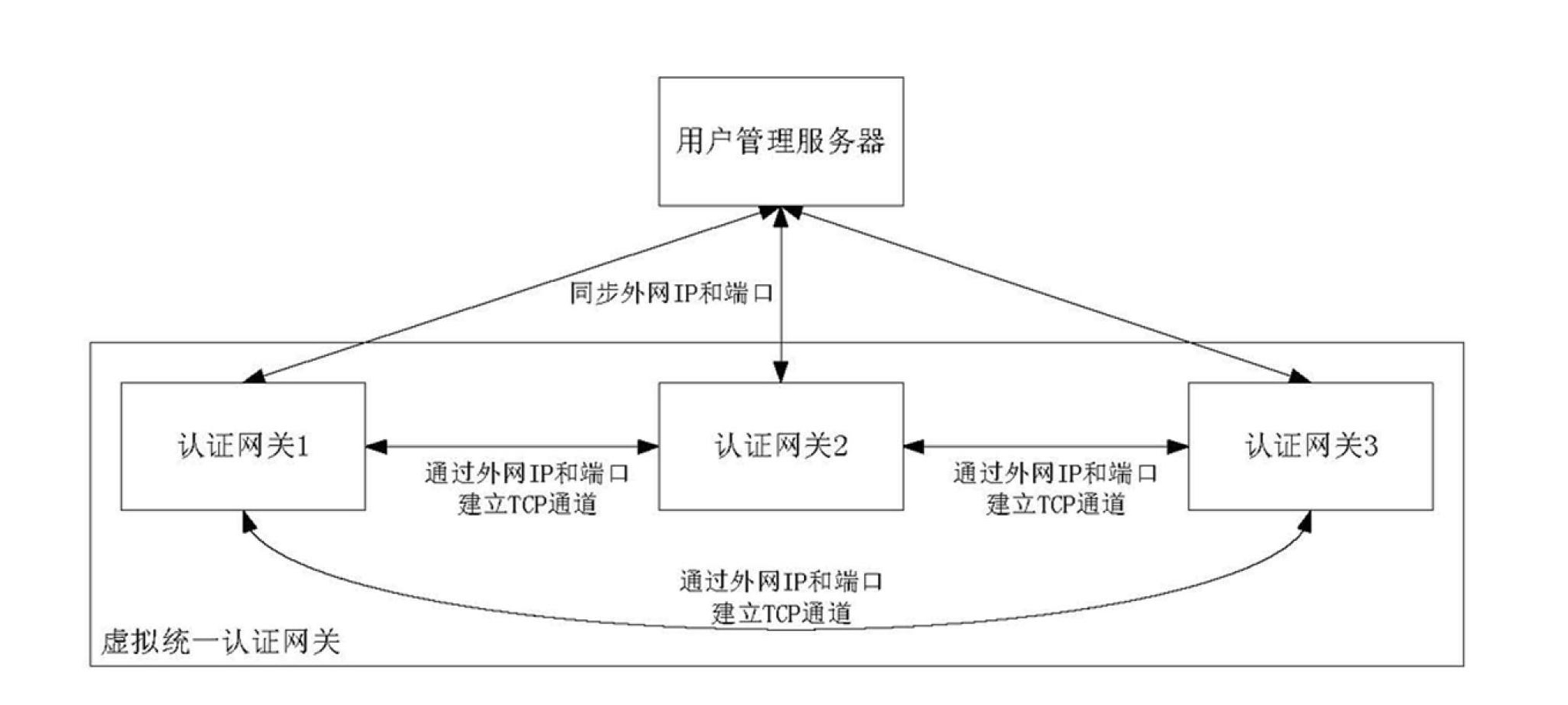
InactiveCN102665216AFunction increaseAdapt to business needsSecurity arrangementUser authenticationLocal area network
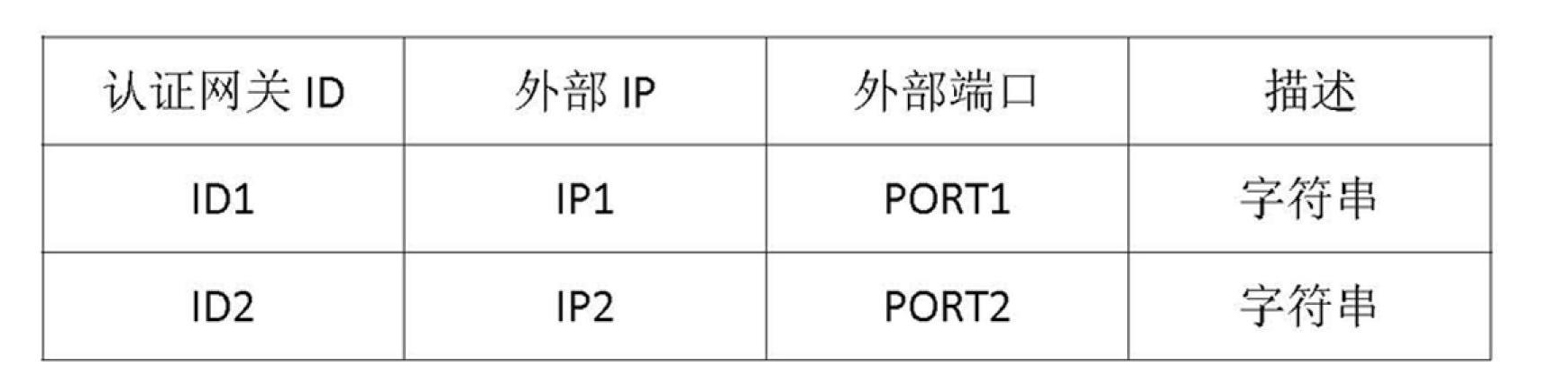
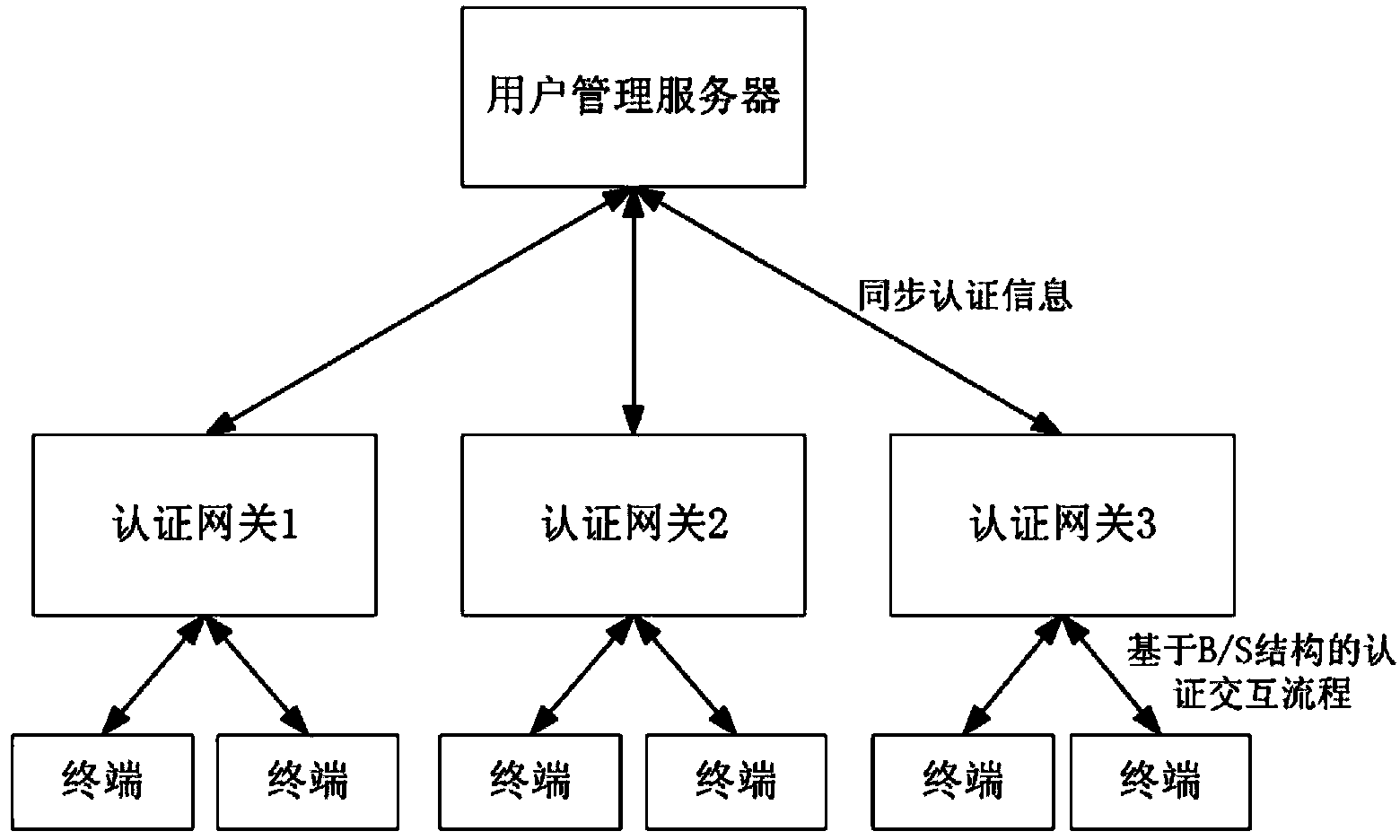
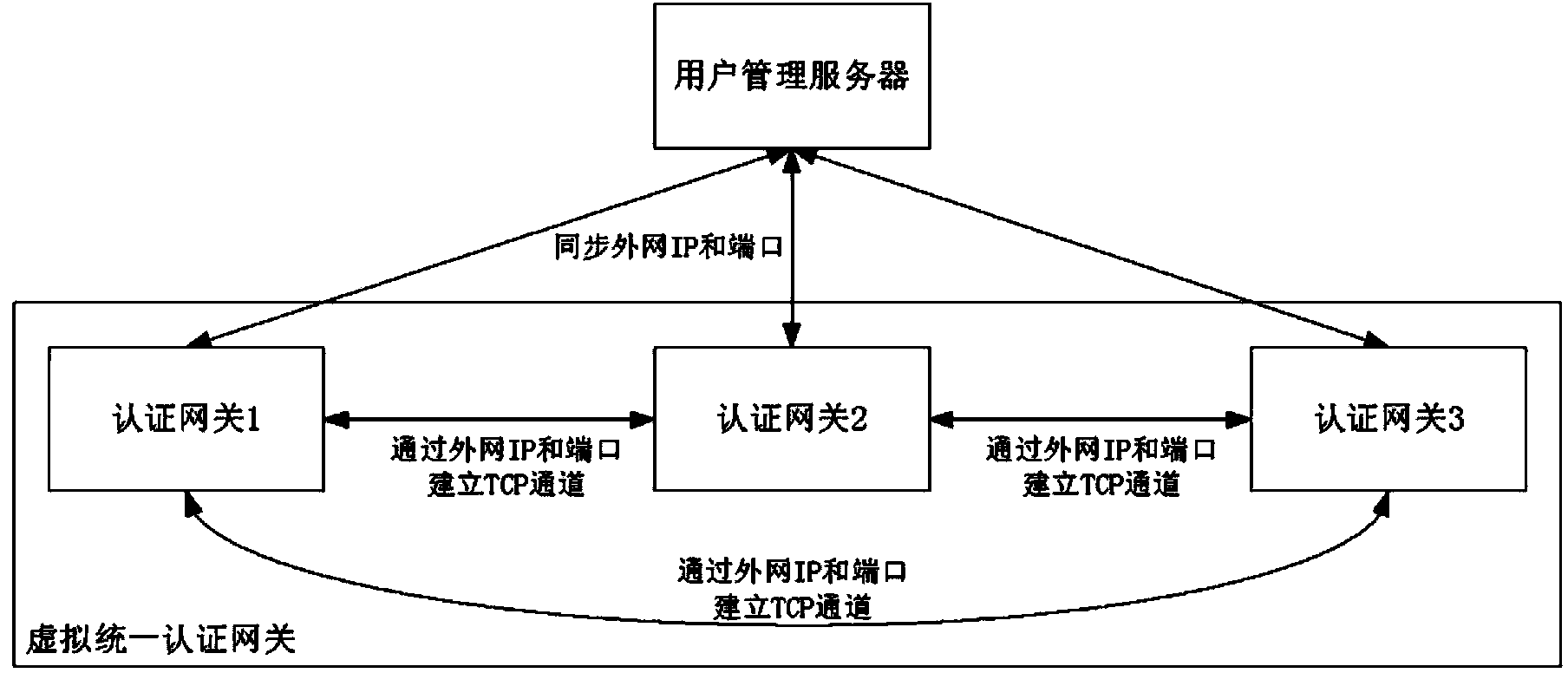
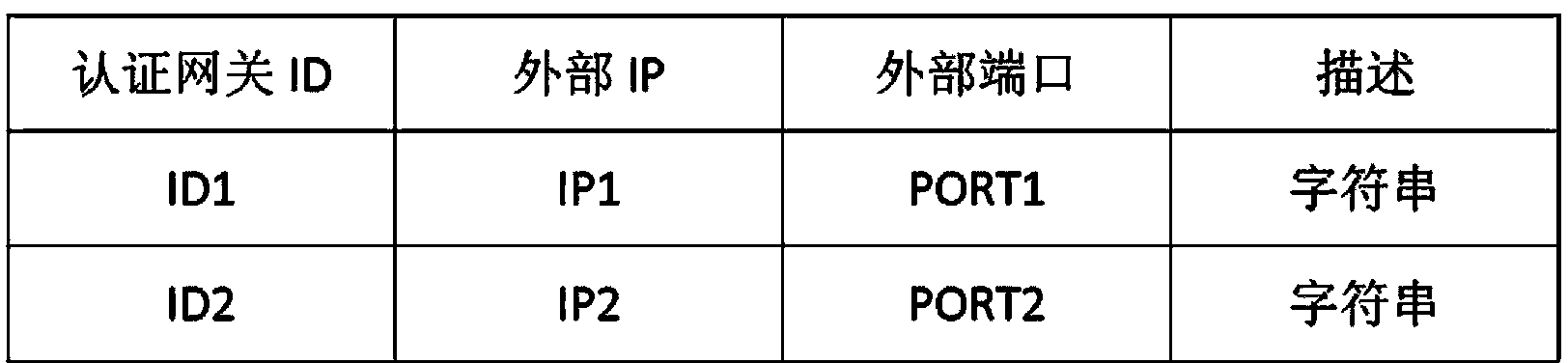
The invention relates to a user authentication method for an extensible and distributed wireless local area network (WLAN). The method has the characteristics that investment is small, and a user conveniently uses the network. The technical scheme is that the user authentication method for the extensible and distributed WLAN sequentially comprises the following steps that: 1) an extensible network user authentication system is established in the following way: a plurality of authentication gateways are directly connected with a user management server which stores all user information through an external network, and a wireless user terminal is subjected to the authentication process in one of the authentication gateways through a wireless access point (AP); and 2) the user management server generates a peer-to-peer (P2P) network through an external network Internet protocol (IP) and a port mapping table organization authentication gateway, and the authentication gateways are in transmission control protocol (TCP) long connection to form a virtual unified authentication gateway.
Owner:赵霏
Blind test method and device, uplink access method and device, receiver, transmitter and base station
ActiveCN107332796AImprove reliabilityAdapt to business needsError preventionTransmitter/receiver shaping networksAccess methodComputer science
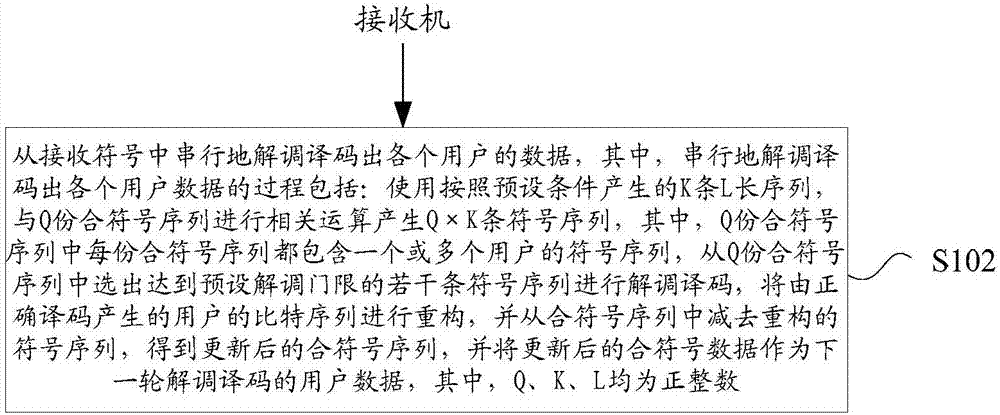
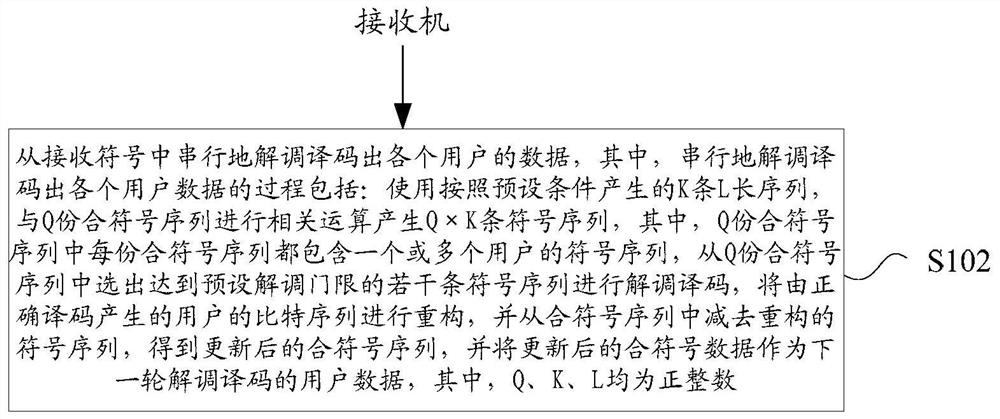
Embodiments of the invention provide a blind test method and device, an uplink access method and device, a receiver, a transmitter and a base station. The blind test method comprises a step of serially demodulating and decoding data of each user from a receiving symbol, wherein a process of serially demodulating and decoding the data of each user comprises the following steps of utilizing K L-length sequences generated according to a preset condition and Q compound symbol sequences to carry out correlation operation in order to generate Q*K symbol sequences, wherein each of the Q compound symbol sequences includes a symbol sequence of one or more users; selecting a plurality of symbol sequences which reach a preset demodulation threshold from the Q compound symbol sequences to demodulate and decode; reconstructing a bit sequence of the user, which is generated by correct decoding, and subtracting the reconstructed symbol sequence from the compound symbol sequences to obtain the updated compound symbol sequences; and taking the updated compound symbol data as user data of the next round of demodulation and decoding, wherein Q, K and L are all positive integers.
Owner:ZTE CORP
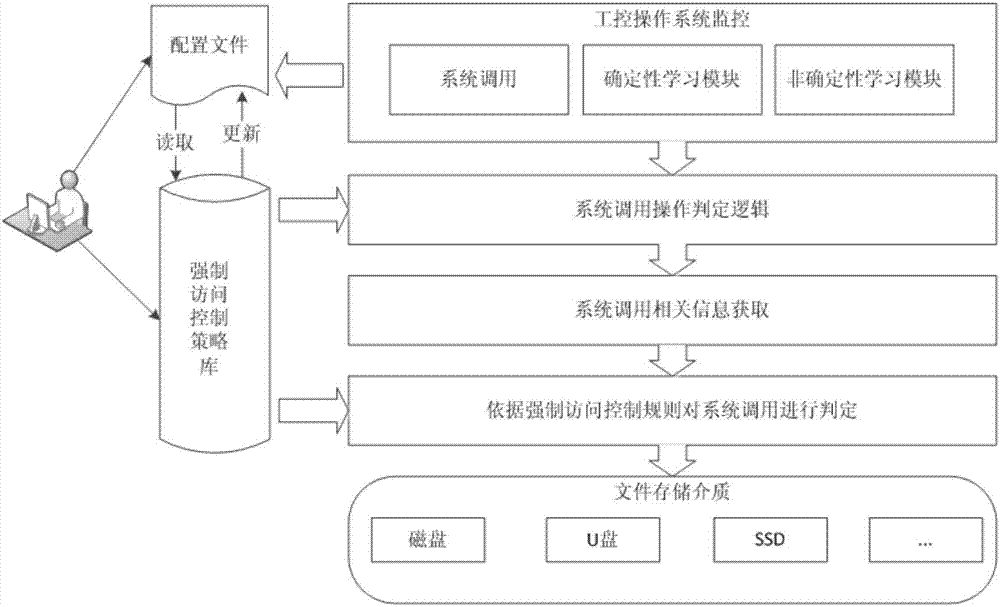
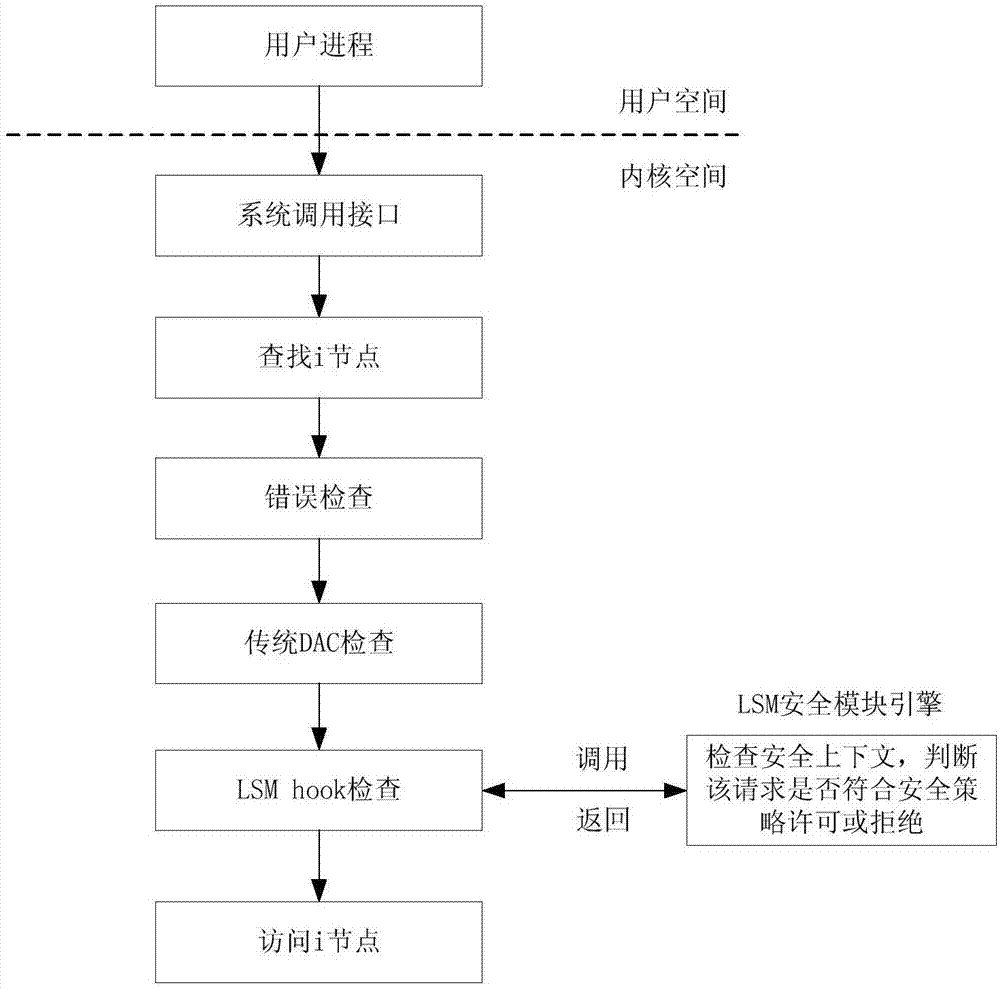
Industrial control operation system active defense method with self-learning characteristic
InactiveCN107491693AImprove general performanceIncrease flexibilityPlatform integrity maintainanceOperational systemLinux kernel
The invention discloses an industrial control operation system active defense method with a self-learning characteristic. The method comprises the following steps of: 1, judging whether a program is executable or not according to a credible strategy, and if the program is executable, monitoring a business behavior and accessing an operation according to a detected subject and a detected object; 2, monitoring a log generated via business call according to the step 1 so as to realize uncertain security policy learning; 3, monitoring a behavior of system call in a Linux kernel layer, collecting corresponding system call information, and judging whether the system call is allowed or rejected according to security policies generated in the steps 1 and 2; and 4, constructing an industrial control operation system active defense system by taking self-learning system forced access control as basis and utilizing application credibility measurement according to the steps 1 and 2. The method is still immune to attacks under the condition that loopholes exist, and has the characteristics of being automatic in learning, simple to apply and low in business influence.
Owner:NANJING NARI GROUP CORP +2
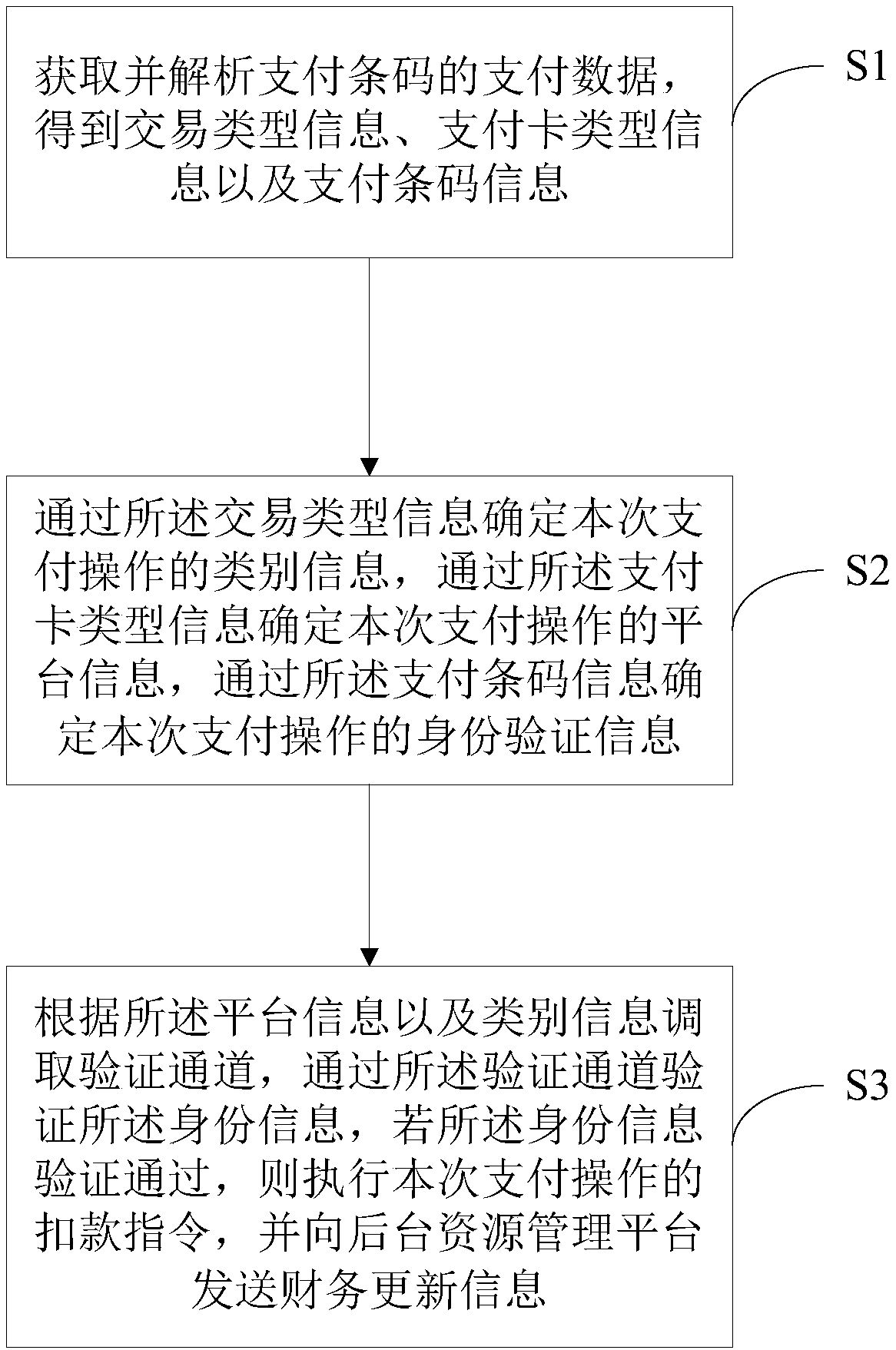
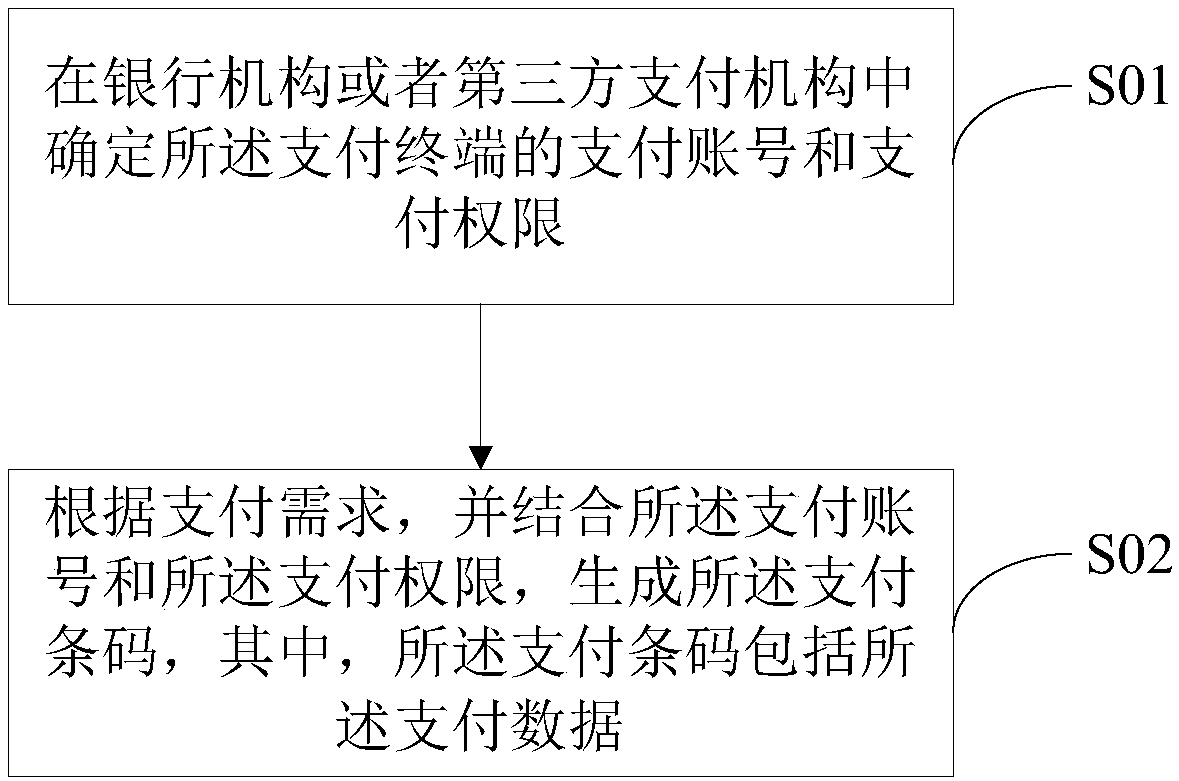
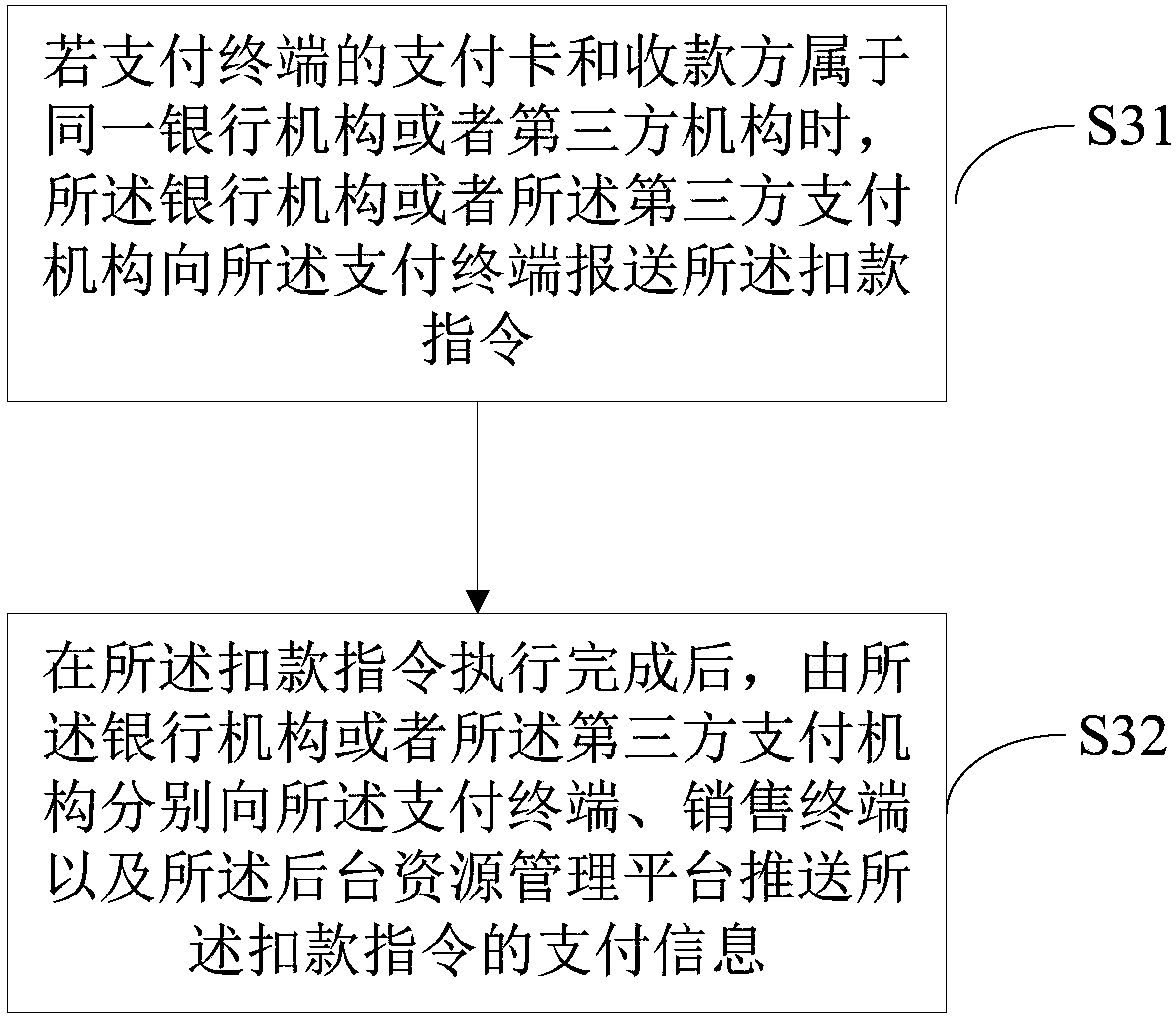
Payment method and equipment and computer readable storage medium
InactiveCN107808285AImprove payment experienceEnhance payment management capabilitiesProtocol authorisationBarcodeResource management
The invention discloses a payment method and equipment and a computer readable storage medium. The method comprises the following steps of: obtaining and analyzing payment data of a payment barcode soas to obtain transaction type information, payment card type information and payment barcode information; determining category information of the payment operation through the transaction type information, determining platform information of the payment operation through the payment card type information and determining identity verification information of the payment operation through the payment barcode information; and finally, verifying identify information, executing a money deduction instruction of the payment operation and sending finance updating information to a background resource management platform. According to the payment method and equipment and the computer readable storage medium, an efficient mobile payment scheme which is suitable for general commercial requirements isrealized, and the mobile payment process is enriched and completed at the same time; and a comprehensive and systematic marketing payment management system among consumers, sellers and merchants is established, so that the payment experience of user sides is improved and the payment management ability of marketing sides is strengthened.
Owner:深圳市生银万国网络科技有限公司
Product control method based on soft component
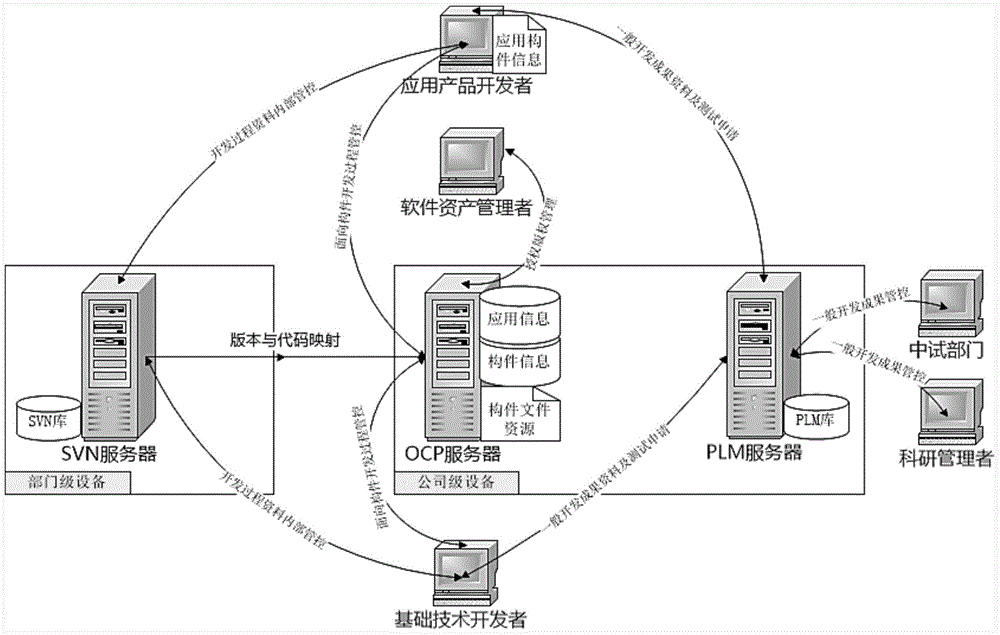
InactiveCN104102947ARealize plug and playAdapt to business needsSensing by electromagnetic radiationApplication lifecycle managementProduction line
The invention relates to a product control method based on a soft component. The product control method comprises the following steps: firstly, an operating system is is preinstalled in each of three server target machines; a SVN (subversion) software server side needs to be installed in a SVN server; a component management tool needs to be installed in an OPC(open component platform) server to be in charge of managing the component; and PLM (product lifecycle management) software needs to be installed in a PLM server to be in charge of managing the product. The reusability of the component can be improved, two development lines of platform and application are accelerated to be tightly combined, the management strictness of a product line is improved, the development and test period of the product is greatly improved, and the product quality is guaranteed to be reliable.
Owner:XJ ELECTRIC +1
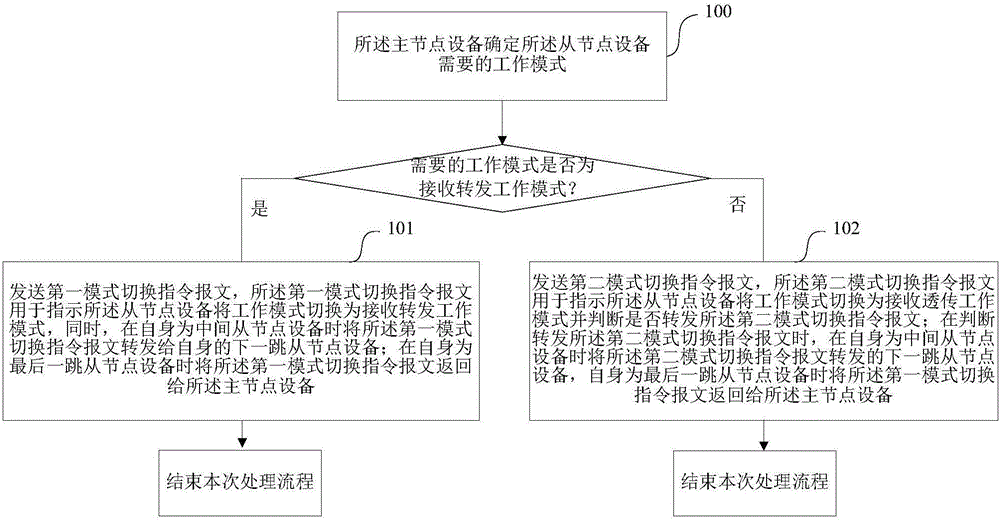
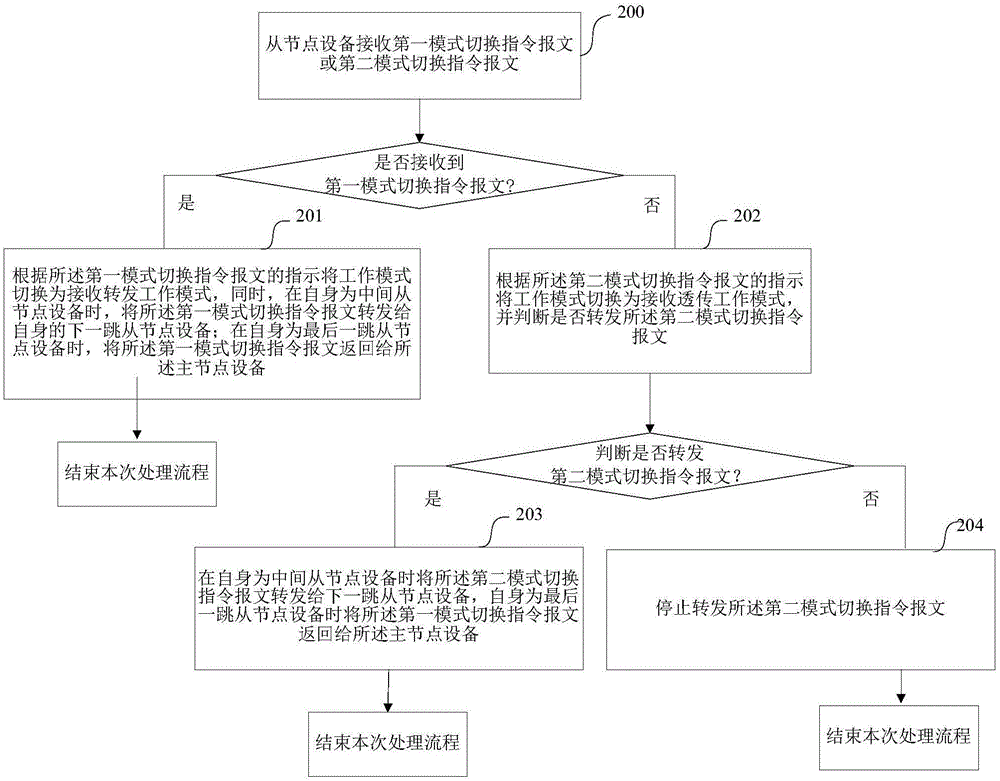
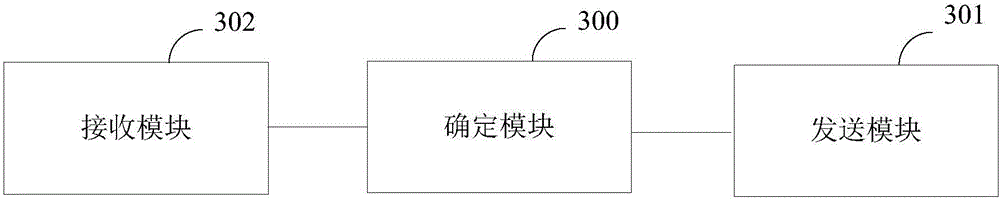
Mode switching control method, device and system for unidirectional serial bus network
InactiveCN106059876AAdapt to business needsData switching detailsBus networksTelecommunicationsBus network
The invention provides a mode switching control method, a mode switching method, a device and a system for a unidirectional serial bus network. Master node equipment determines a working mode required by slave node equipment, and instructs the slave node equipment by virtue of a first mode switching instruction message or a second mode switching instruction message to switch into the required working mode; the slave node equipment is configured with two types of working modes: a receiving and forwarding working mode and a receiving and transparent transferring working mode; when the working mode is the receiving and forwarding working mode, received service messages are processed, and whether to send the processed service messages or not is judged; and when the working mode is the receiving and transparent transferring working mode, the received service messages are processed, and the service messages are sent at the same time. Thus, in the embodiments of the invention, the slave node equipment can perform switching of the working mode according to instructions from the master node equipment so as to adapt to different types of service requirements.
Owner:CENTURY OPTICOMM CO LTD
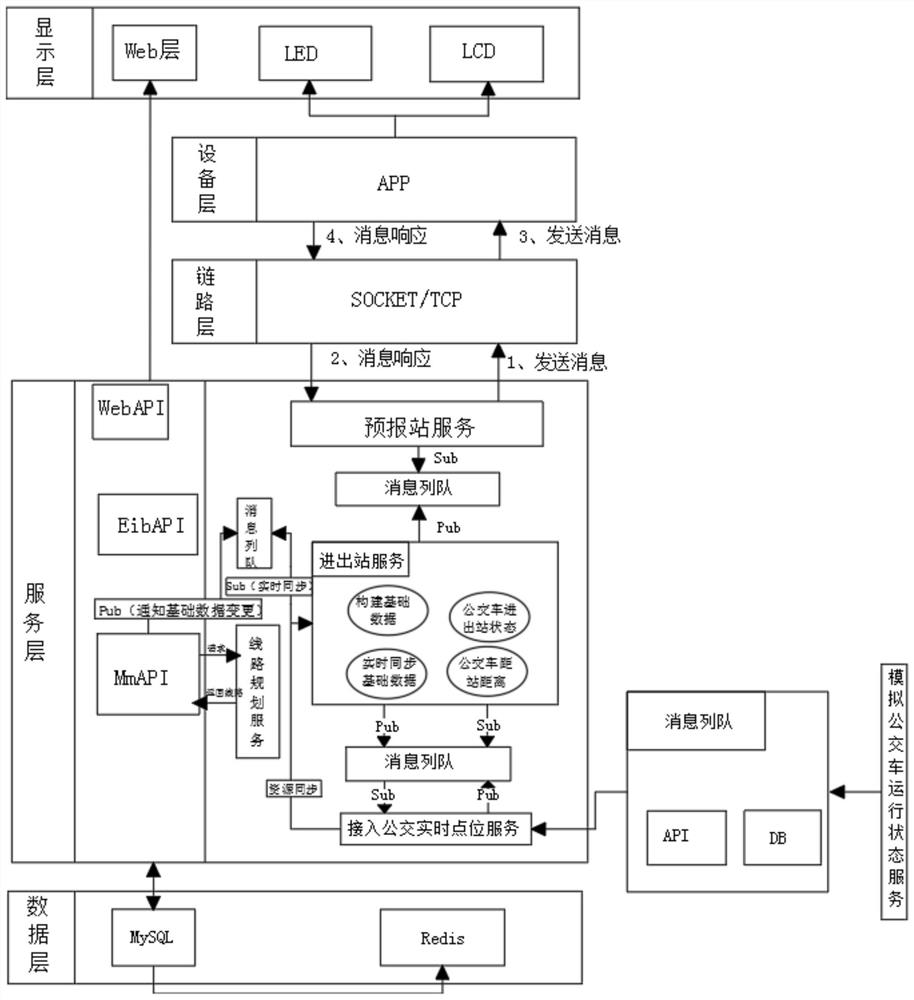
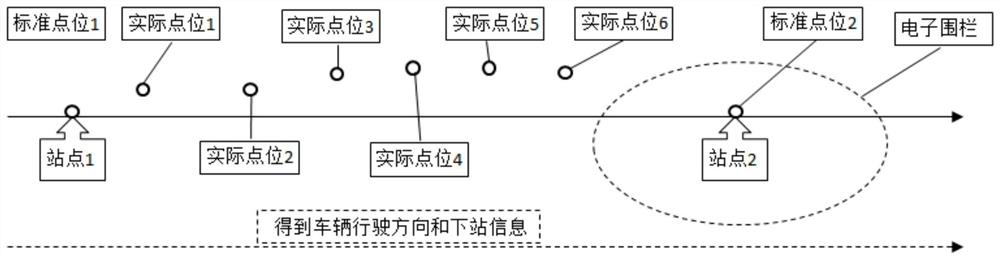
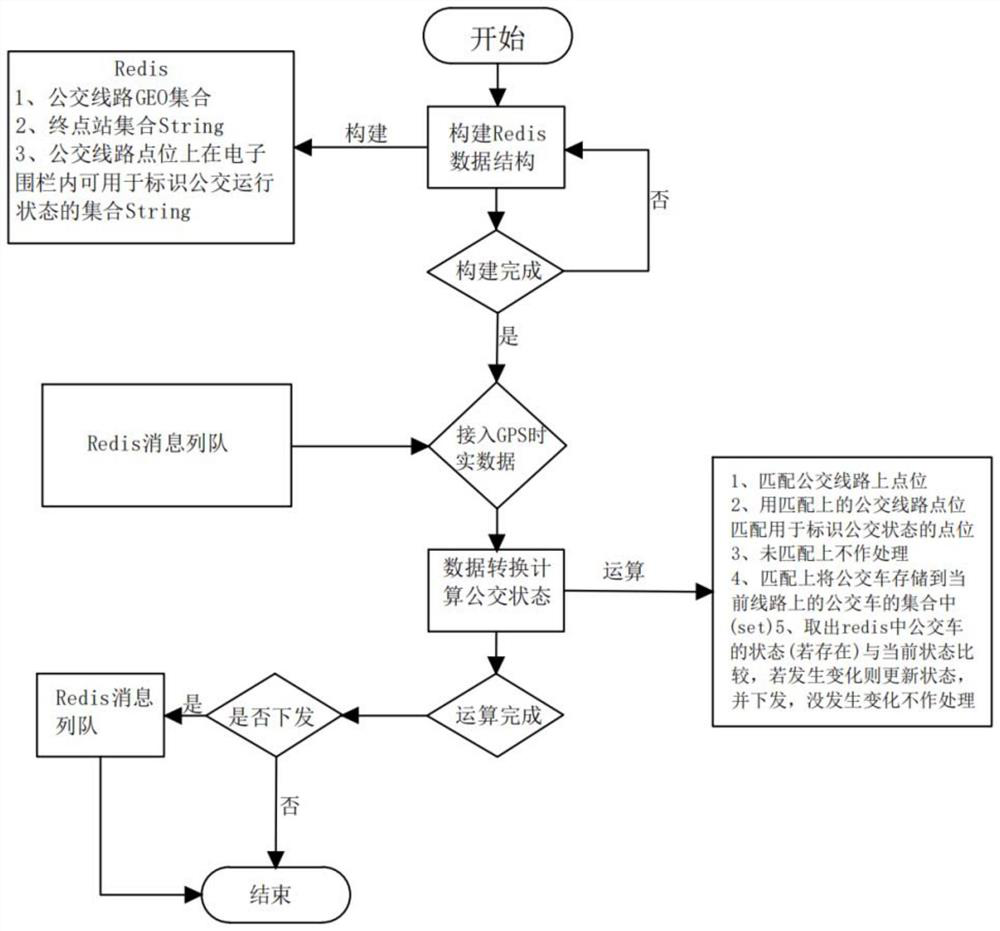
Electronic stop board forecasting system and method
InactiveCN112185152AEfficient electronic station sign forecast station functionEnsure timeliness and accuracyRoad vehicles traffic controlForecastingService layerExternal data
The invention discloses an electronic stop board station forecasting system and method. The system comprises an external data layer, a local data layer, a service layer, a link layer, an equipment layer and a display layer, can build the connection with a vehicle in real time, obtains the positioning data of the vehicle in real time, through a distributed high-efficiency calculation engine, calculates a result in a second-level and reports the result to an electronic stop board. Therefore, a full-automatic and efficient electronic station board station forecasting function is realized, the real-time performance and accuracy of station reporting information can be guaranteed, and station reporting information lag and errors are avoided. In order to meet different access numbers of differentclient devices, the system can realize elastic expansion and automatic expansion and contraction, a Redis sentry mode cluster adopted on the real-time calculation engine also supports an automatic expansion function, so that the product can meet the service requirements of various large, medium and small customers, and has relatively strong practicability and relatively good application prospect.
Owner:江苏亚楠电子科技有限公司
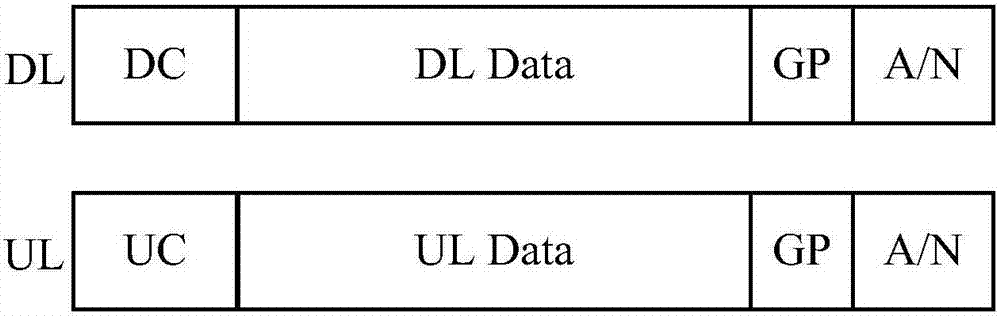
Data transmission method and device
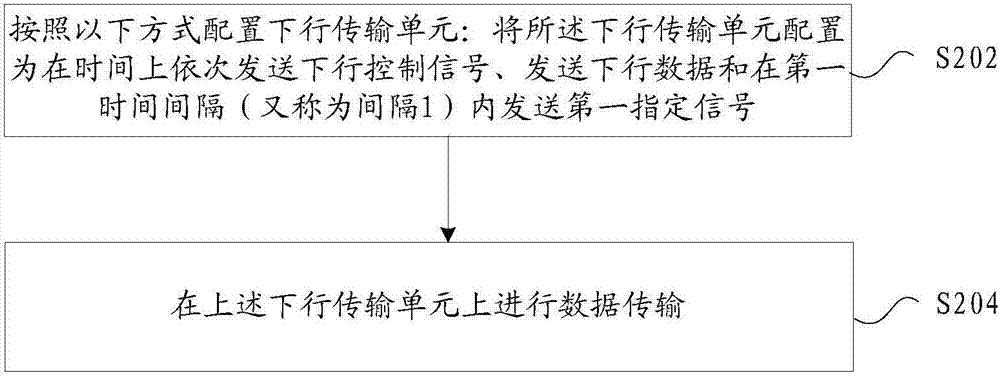
InactiveCN107370581AAdapt to business needsImprove efficiencyError prevention/detection by using return channelTransmission path divisionTime domainControl signal
The present invention provides a data transmission method and device. The method comprises: performing data transmission on a down transmission unit configured according a following mode: the down transmission unit is configured to send down control signals and down data in time domain and send first assigned signals at first time intervals. According to the technical scheme, the problem is solved of resource efficiency and high delay demand in a 5G FDD system.
Owner:ZTE CORP
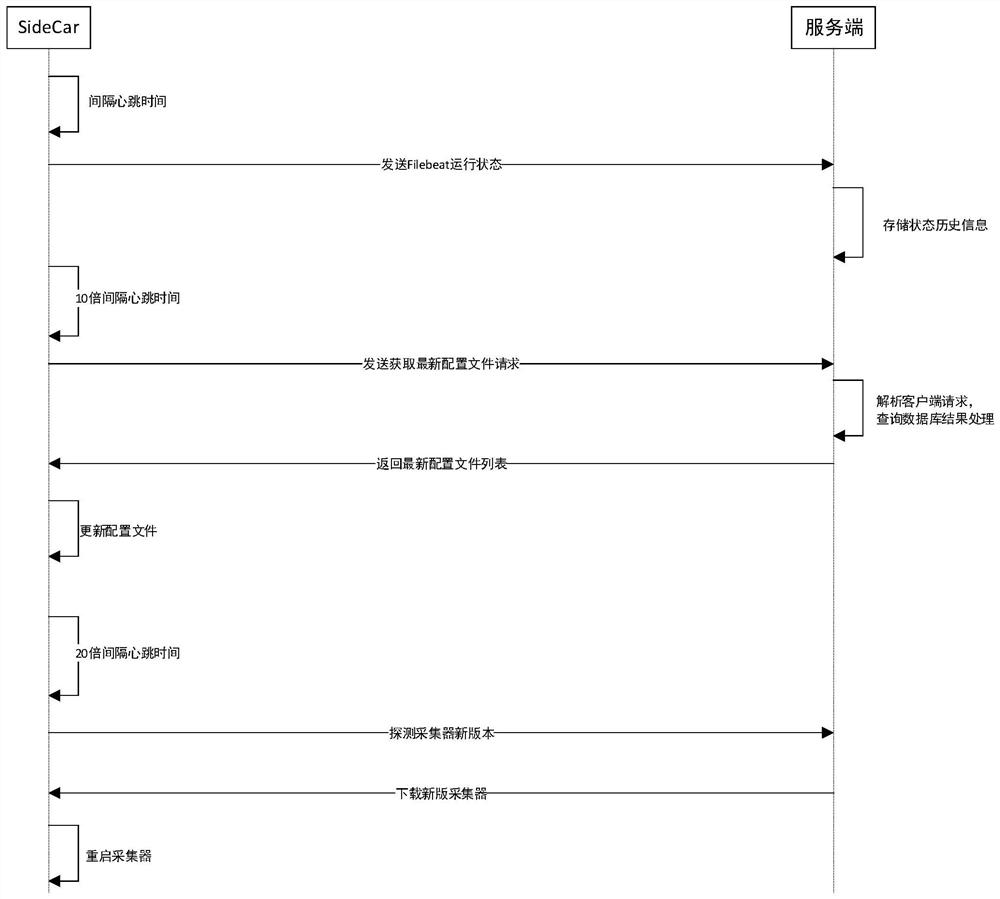
Cloud platform full-automatic management log collection method and terminal
The invention provides a full-automatic management log collection method for a cloud platform. The method comprises the following steps of judging whether Filebeat is started or not, reading a SideCar configuration file, updating log collection configuration according to heartbeat interval time during operation, adding a configuration file to be newly added to a file beat configuration file directory, and closing a module. According to the cloud platform full-automatic management log collection method and the terminal, the collection configuration is automatically pulled from the server side, the latest configuration file is dynamically loaded, and restarting is not needed in the period. Meanwhile, the log collection terminal sends the operation state to the server side, and whether the log collection terminal operates normally or not can be found in a state monitoring mode. The new version of the terminal is automatically detected and collected, and is automatically downloaded, updated and restarted, and the process does not need manual intervention of a user.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
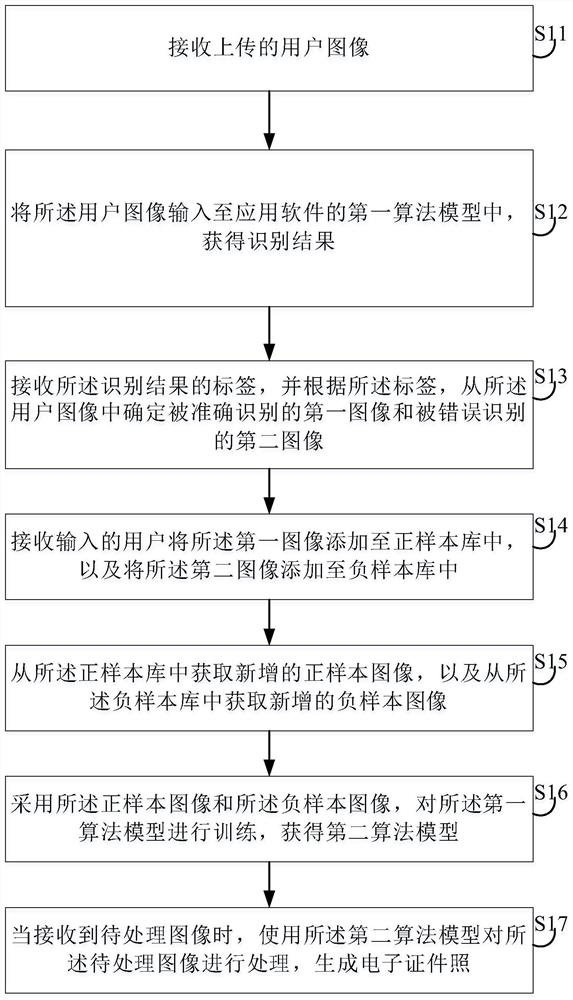
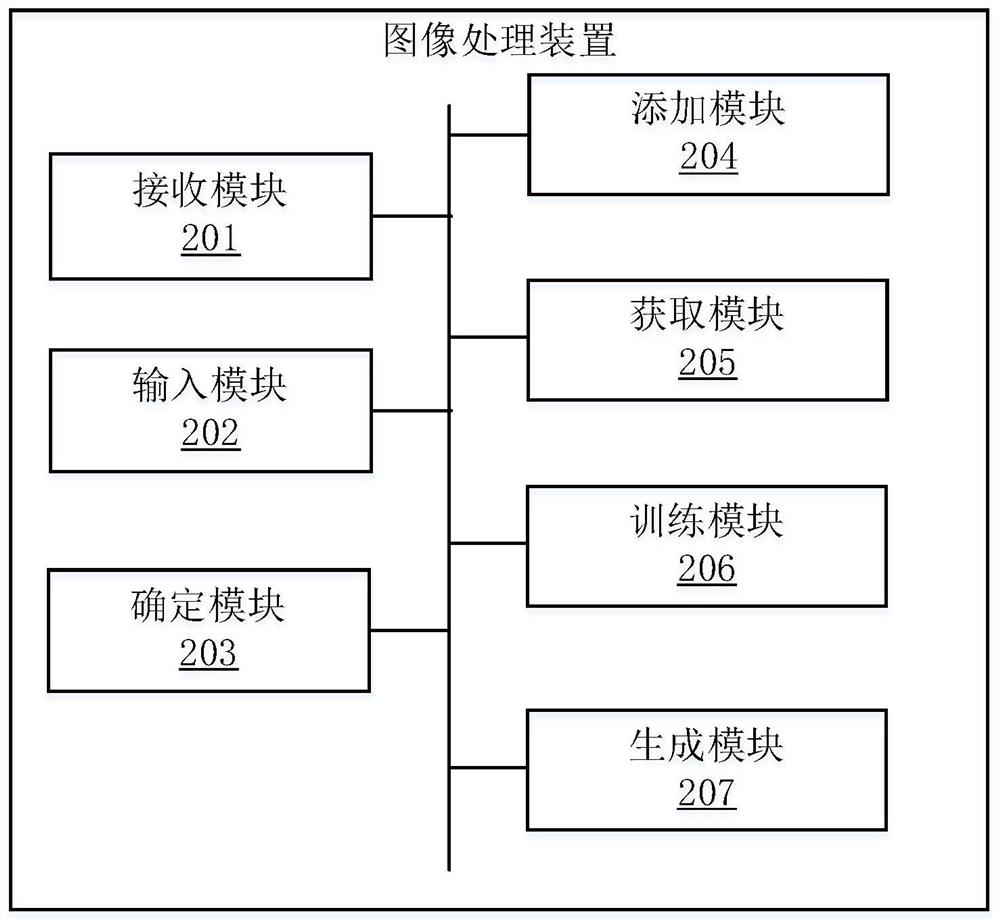
Image processing method and device, electronic equipment and storage medium
PendingCN112132218AImprove generation effectAdapt to business needsCharacter and pattern recognitionSample graphImaging processing
The invention relates to the technical field of artificial intelligence, and provides an image processing method and device, electronic equipment and a storage medium. The method includes receiving auser image; inputting the user image into a first algorithm model to obtain an identification result; receiving a label of the identification result, and determining a first image and a second image from the user images; adding the first image to a positive sample library, and adding the second image to a negative sample library; obtaining a positive sample image from a positive sample library, and obtaining a negative sample image from a negative sample library; training the first algorithm model by adopting the positive sample image and the negative sample image to obtain a second algorithmmodel; and when the to-be-processed image is received, processing the to-be-processed image by using the second algorithm model to generate an electronic identification photo. The invention can be applied to the fields of smart government affairs, smart medical treatment, smart transportation and the like needing certificate photo image processing, so that the development of smart cities is promoted.
Owner:PINGAN INT SMART CITY TECH CO LTD
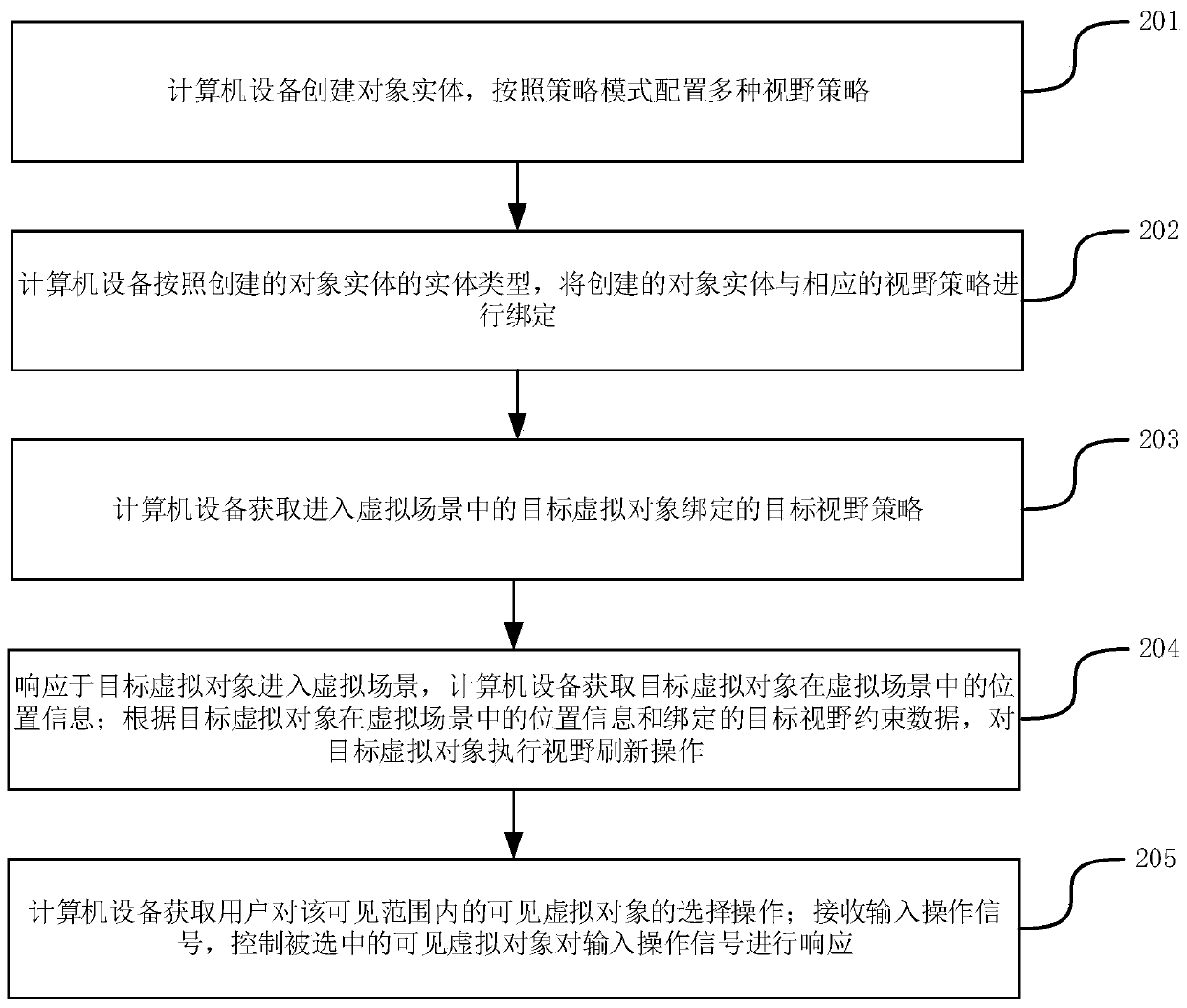
Visual field control method and device for virtual objects, storage medium and computer equipment
ActiveCN111589115AImprove refresh efficiencyReduce complexityDiscounts/incentivesVideo gamesComputer graphics (images)Software design
The invention discloses a visual field control method and device for virtual objects, a storage medium and computer equipment, and belongs to the field of virtual worlds. The method comprises the steps: configuring N visual field constraint data according to a strategy mode, wherein the strategy mode is a software design mode, the N visual field constraint data are independently packaged through different classes, and the visual field constraint data are used for indicating a visible relationship between the virtual objects and other virtual objects in a virtual scene; establishing a binding relationship between various types of virtual objects and corresponding visual field constraint data; in response to the fact that a target virtual object enters the virtual scene, obtaining target visual field constraint data bound with the target virtual object, and obtaining position information of the target virtual object in the virtual scene; and executing a visual field refreshing operationon the target virtual object according to the position information and the target visual field constraint data. The method and the device not only can well adapt to constantly increasing business requirements, but also improve the visual field refreshing efficiency.
Owner:TENCENT TECH (SHENZHEN) CO LTD
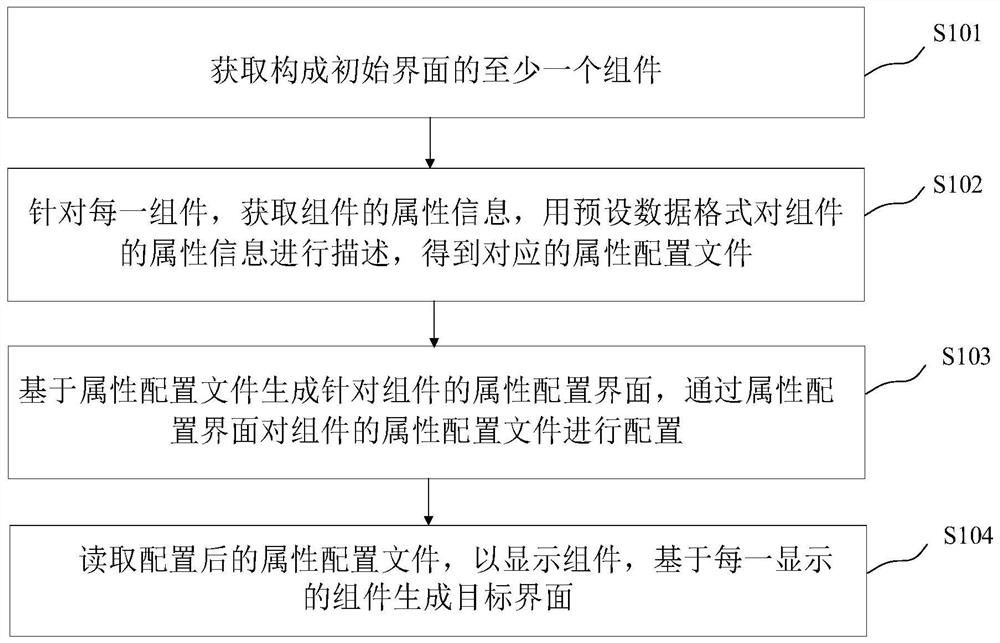
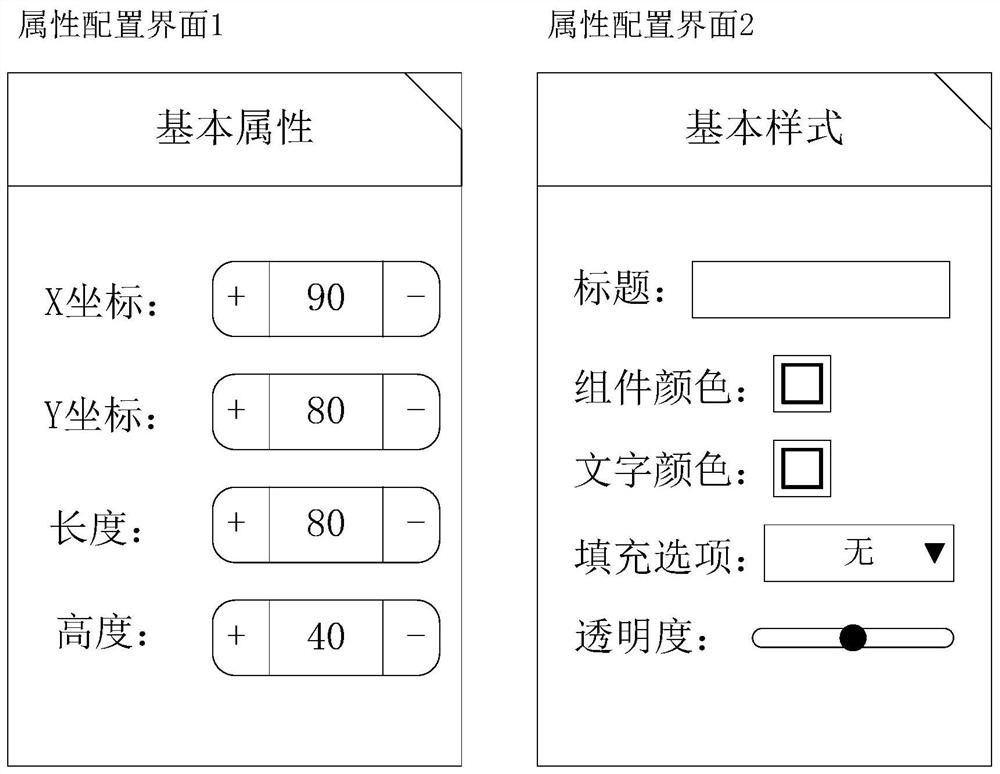
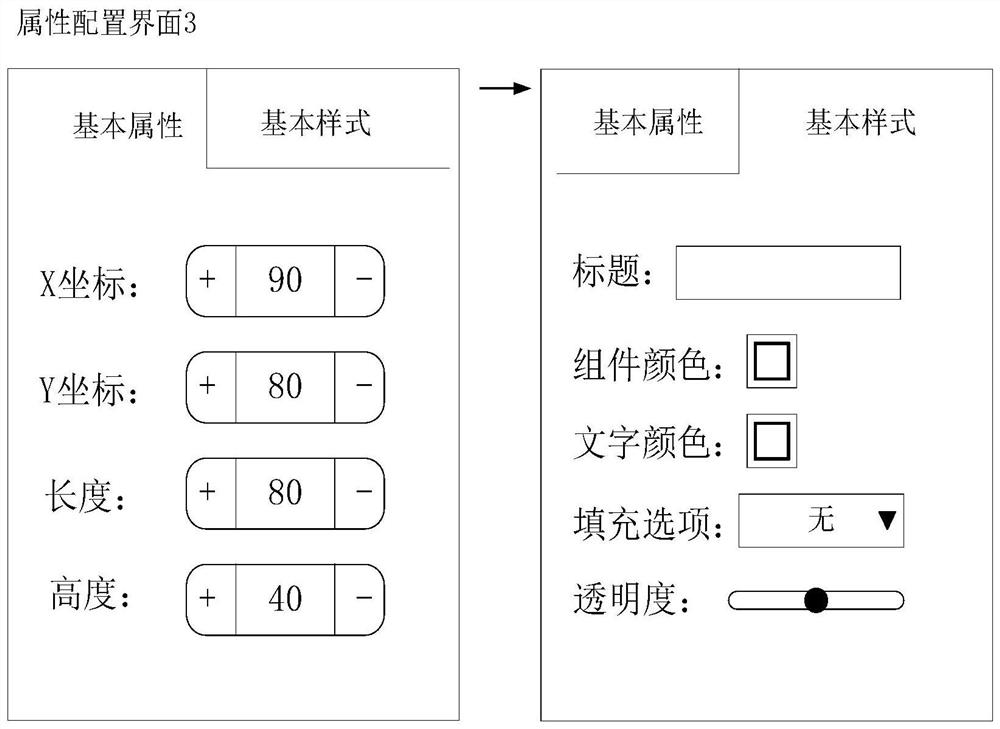
Interface generation method and device, electronic equipment and computer readable storage medium
PendingCN113535165ASolve problems that are difficult to make flexible changesAdapt to business needsSoftware engineeringProgram loading/initiatingData formatBusiness requirements
The embodiment of the invention provides an interface generation method and device, electronic equipment and a computer readable storage medium, and relates to the technical field of computers. The method comprises the following steps: for each component, describing attribute information of the component in a preset data format to obtain an attribute configuration file corresponding to the component; then generating an attribute configuration interface corresponding to the component based on the attribute configuration file, and visually configuring the attribute configuration file of the component through the attribute configuration interface; and reading the configured attribute configuration file, displaying the component, sequentially traversing and reading the attribute configuration file of each component, and finally, displaying a target interface formed by at least one component. According to the embodiment of the invention, the attribute configuration file is configured visually through the attribute configuration interface, and the component is modified based on the configured attribute configuration file, so that the problem that the component is difficult to change flexibly is solved, and more diversified business requirements can be met.
Owner:中电金信软件有限公司
Blind detection, uplink access method and device, receiver, transmitter, base station
ActiveCN107332796BImprove reliabilityAdapt to business needsError preventionTransmitter/receiver shaping networksAccess methodAlgorithm
Embodiments of the present invention provide a method and device for blind detection and uplink access, a receiver, a transmitter, and a base station, wherein the blind detection method includes: demodulating and decoding data of each user serially from received symbols , wherein the process of serially demodulating and decoding each user data includes: using K L-long sequences generated according to preset conditions, and performing correlation operations with Q combined symbol sequences to generate Q×K symbol sequences, wherein, Each combined symbol sequence in the Q combined symbol sequence contains one or more user symbol sequences, and several symbol sequences that reach the preset demodulation threshold are selected from the Q combined symbol sequence for demodulation and decoding. The user's bit sequence generated by decoding is reconstructed, and the reconstructed symbol sequence is subtracted from the combined symbol sequence to obtain the updated combined symbol sequence, and the updated combined symbol data is used as the next round of demodulation and decoding User data of , where Q, K, and L are all positive integers.
Owner:ZTE CORP
Manual call processing method and manual dispatching video call system
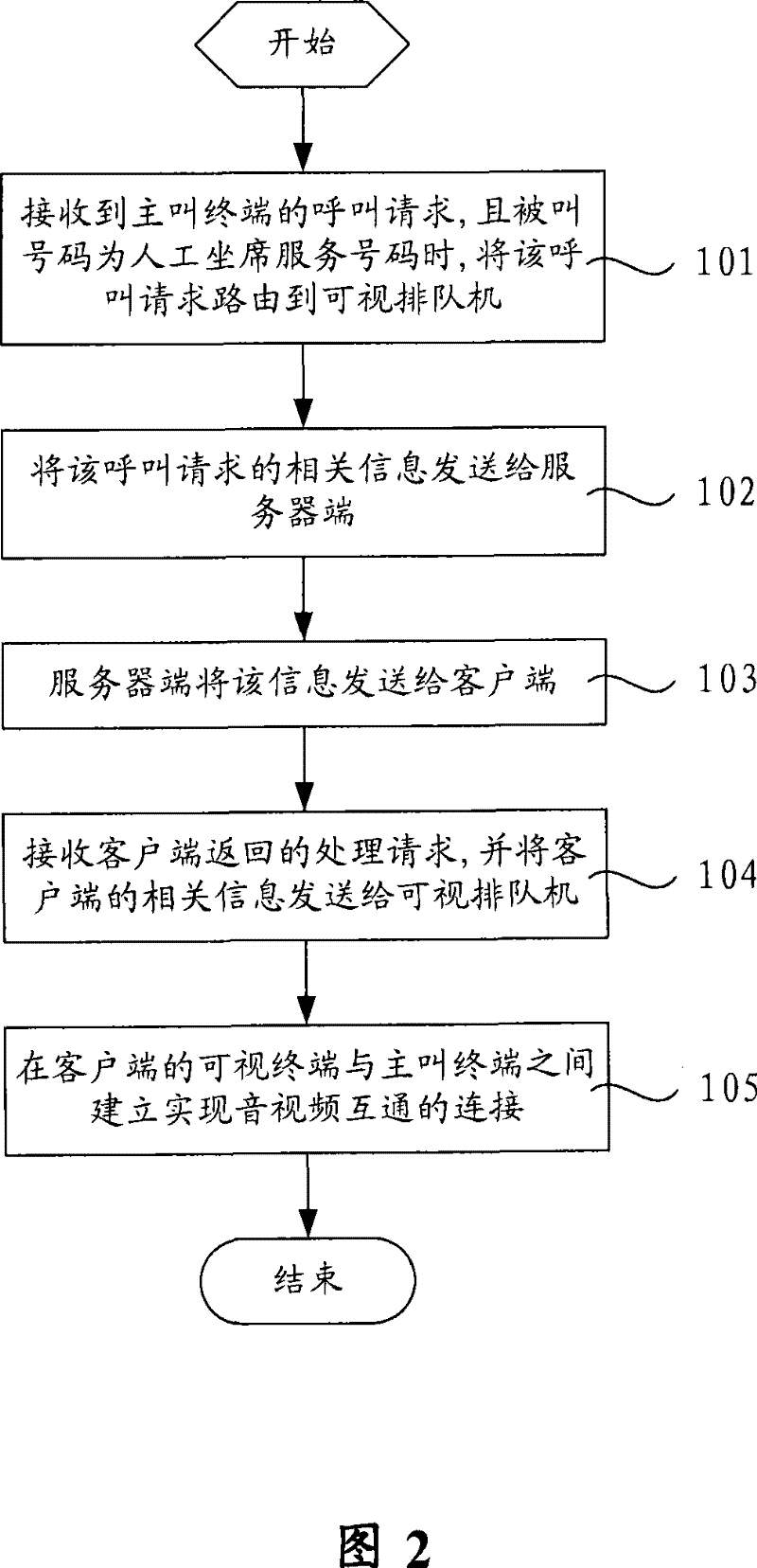
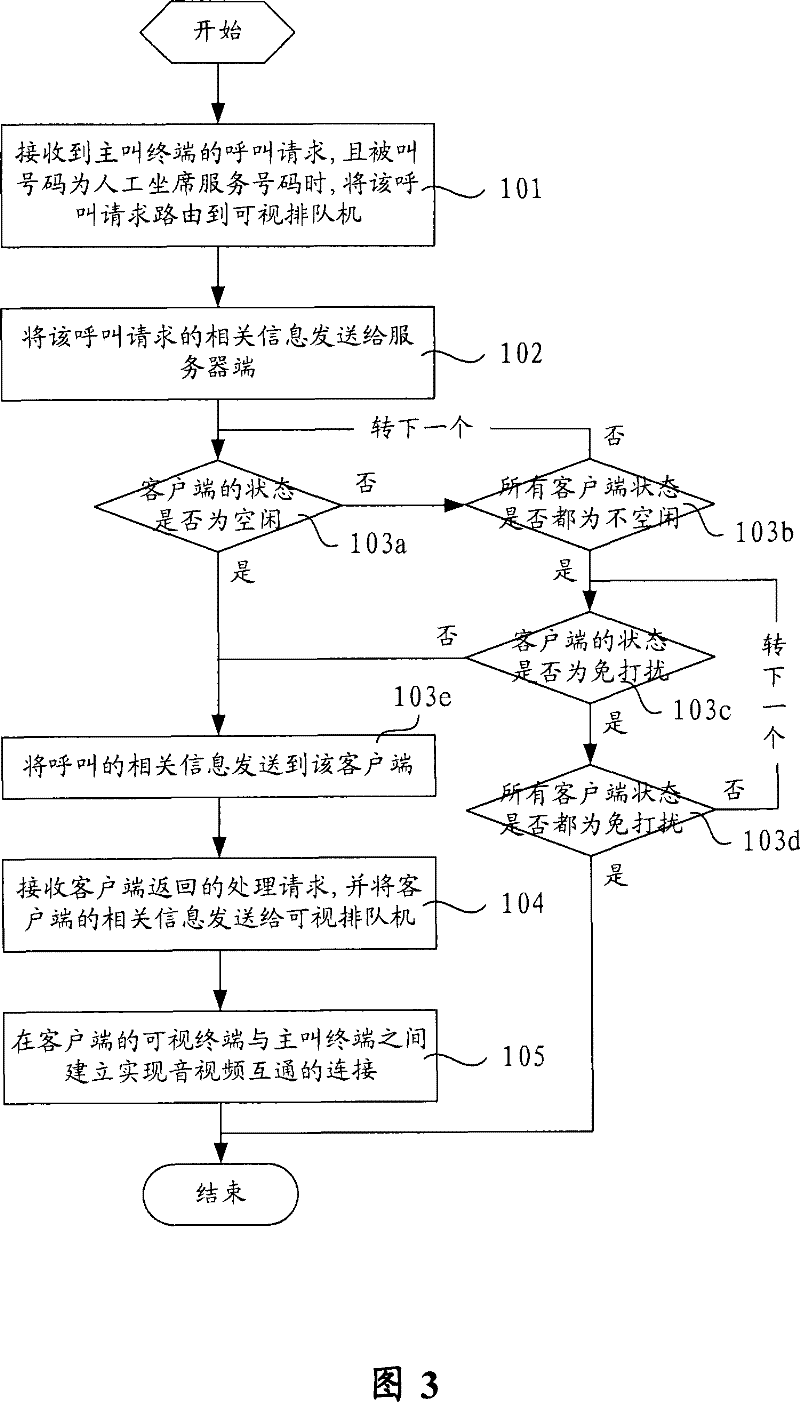
ActiveCN101237493BMeet the needs of artificial seatsMeet business needsSpecial service for subscribersManual exchangesRelevant informationCommunication link
The invention relates to an operator call handling method which comprises the following steps that: when a subsystem of a control center receives a call request from a calling terminal and a called number is an operator service number, the subsystem of the control center routes the call request to a visual queue machine; the subsystem of the control center transmits the related information of thecalling request to a server terminal of a visual traffic management subsystem, then the server transmits the information to a client terminal; the server receives the processing request returned fromthe client terminal, and transmits the related information of the client terminal to the visual queue machine; the visual queue machine establishes a communication link of audio-visual frequency between the visual terminal of the client terminal and the calling terminal. The invention also provides a visual call system of manual scheduling which comprises the subsystem of the control center, a visual call management subsystem and the visual queue machine. The invention carries out call queue management to calls accessing the system through the visual queue machine, and provides proper operator position services for the calls through the visual call management subsystem.
Owner:XINGTANG TELECOMM TECH CO LTD
User authentication method for extensible and distributed wireless local area network (WLAN)
InactiveCN102665216BFunction increaseAdapt to business needsSecurity arrangementEngineeringUser authentication
The invention relates to a user authentication method for an extensible and distributed wireless local area network (WLAN). The method has the characteristics that investment is small, and a user conveniently uses the network. The technical scheme is that the user authentication method for the extensible and distributed WLAN sequentially comprises the following steps that: 1) an extensible network user authentication system is established in the following way: a plurality of authentication gateways are directly connected with a user management server which stores all user information through an external network, and a wireless user terminal is subjected to the authentication process in one of the authentication gateways through a wireless access point (AP); and 2) the user management server generates a peer-to-peer (P2P) network through an external network Internet protocol (IP) and a port mapping table organization authentication gateway, and the authentication gateways are in transmission control protocol (TCP) long connection to form a virtual unified authentication gateway.
Owner:赵霏
A method and device for concurrently acquiring resources
ActiveCN107729139BReduce overheadSatisfy concurrent processingResource allocationComputers technologyThread pool
The invention discloses a method and a device for acquiring resources concurrently, and relates to the technical field of computers. A specific implementation of the method includes: receiving multiple resource acquisition tasks from a user, each resource acquisition task is used to acquire a resource on a corresponding remote server; The network IO channel established by the server is transmitted to the corresponding remote server to execute each resource acquisition task; monitor whether there is a remote server returning the task execution result to the corresponding network IO channel, and if so, from the corresponding network The IO channel reads the task execution result to obtain corresponding resources. This implementation mode does not rely on the thread pool, can satisfy the concurrent processing of various business resources at the same time, well adapts to business needs, has good horizontal scalability, can reuse resources, reduces resource overhead, and increases development efficiency.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
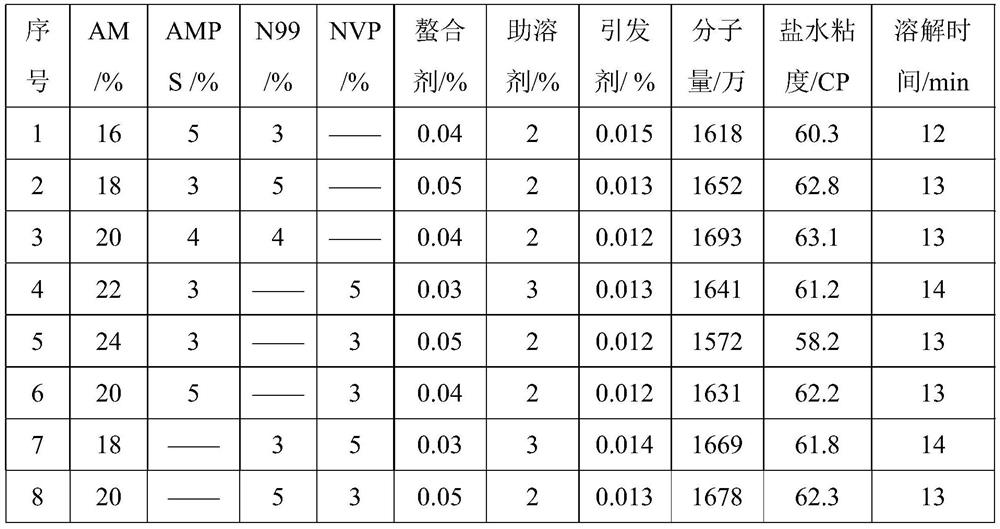
A salt-resistant fracturing fluid thickener and preparation method thereof
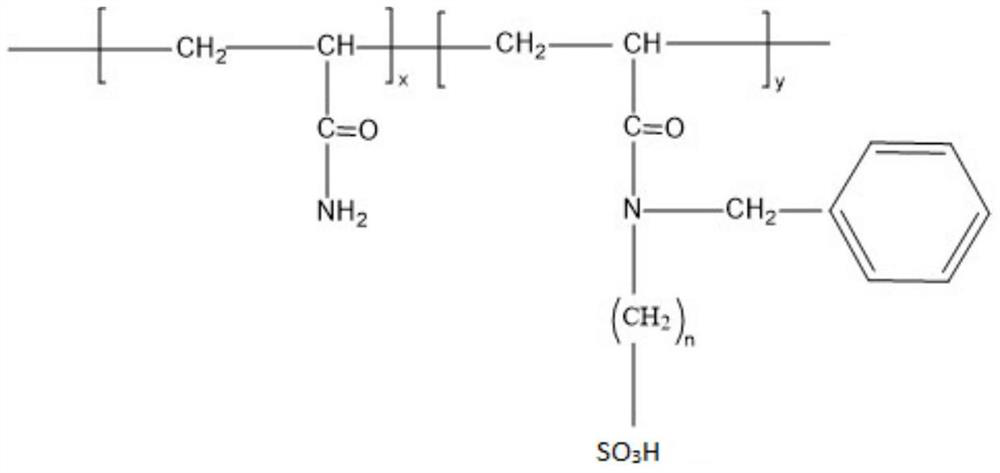
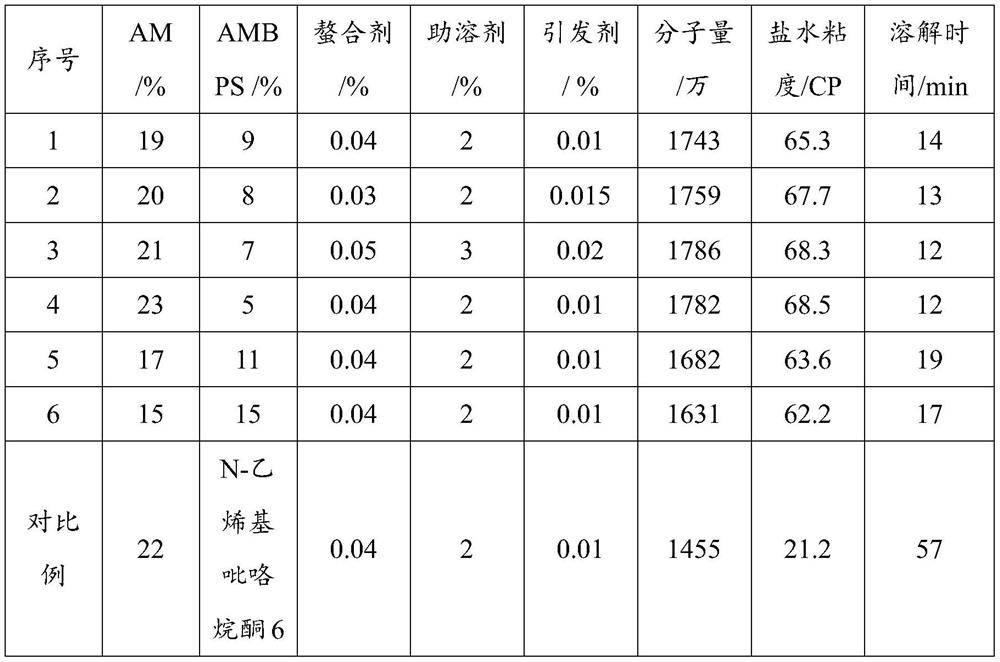
ActiveCN113024722BEnhanced steric hindranceGood temperature and salt resistanceDrilling compositionUltraviolet lightsOrganic polymer
The invention discloses a salt-resistant fracturing fluid thickener and a preparation method thereof, belonging to the field of organic polymer compound preparation. The method includes the following steps: adding salt-resistant monomer, acrylamide, chelating agent, cosolvent, initiator and deionized water into a container for mixing and dissolving, adjusting the pH of the solution to 6.5-7.5; purging nitrogen and deoxygenating for 20-30 minutes; placing the solution in Irradiate under ultraviolet light for 50-80 minutes; take out the rubber block, granulate, dry, crush, and sieve. The invention uses salt-tolerant monomers, polymer stabilizers and acrylamide to initiate polymerization under ultraviolet light, with simple process, rapid response and convenient adjustment. The obtained product has high molecular weight (≥15 million), fast dissolution speed and strong salt resistance (resistant to 50,000 salinity), and has a good application effect in the field of fracturing fluid thickening.
Owner:JIANGSU FEYMER TECH
Temperature-resistant and salt-resistant fracturing fluid thickening agent and preparation method thereof
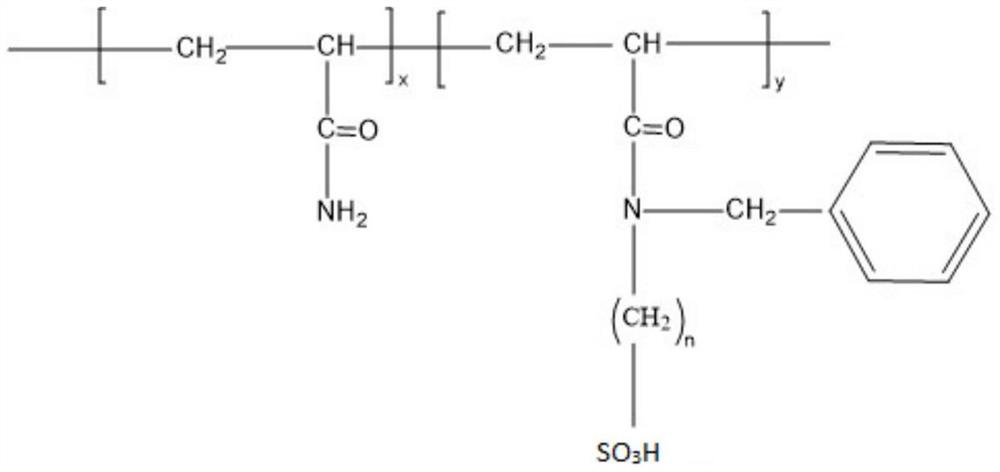
InactiveCN114106239AHigh activityGood temperature and salt resistanceDrilling compositionFunctional monomerBenzaldehyde
The invention discloses a temperature-resistant and salt-resistant fracturing fluid thickening agent and a preparation method thereof, and relates to a polymer thickening agent in the fracturing process in the field of exploration and development of oil and gas fields. The preparation method comprises the following steps: sulfonating alpha-olefin amine to obtain sulfonic acid alkylamine, reacting with benzaldehyde to obtain benzamide alkyl sulfonic acid, reacting with acryloyl chloride to obtain a temperature-resistant and salt-resistant functional monomer N-benzyl-N-acrylamido-alkyl sulfonic acid (AMBPS), and reacting with acrylamide to obtain the temperature-resistant and salt-resistant functional monomer AMBPS. Mixing and dissolving AMBPS, acrylamide, a chelating agent, a cosolvent, a polymer stabilizer, an initiator and the like, introducing nitrogen, and irradiating the solution under an ultraviolet lamp to prepare the temperature-resistant and salt-resistant fracturing fluid thickening agent. The prepared thickening agent is simple in process and rapid in reaction, and the obtained product is high in molecular weight, high in dissolving speed and high in temperature resistance and salt resistance and has a good application effect in the field of fracturing fluid thickening.
Owner:南通博亿化工有限公司
A method and system for intranet and extranet communication
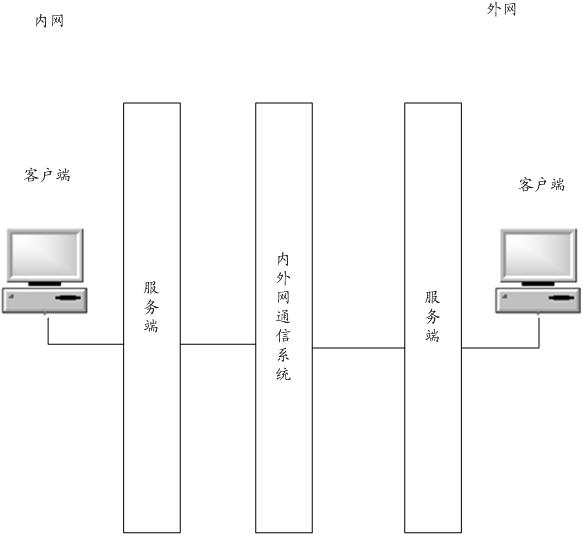
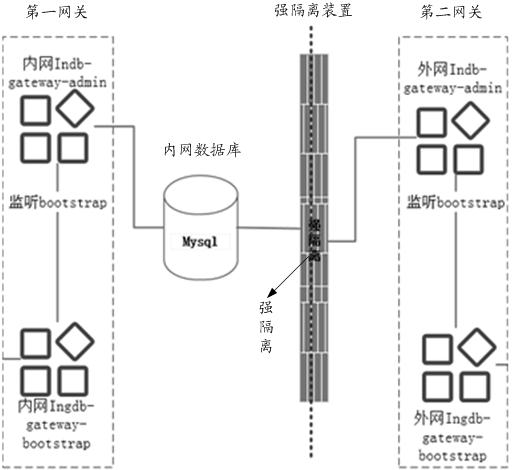
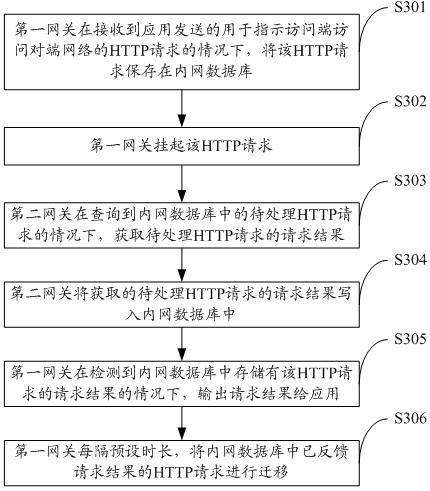
ActiveCN111818187BImprove communication efficiencyAdapt to business needsTransmissionCommunications systemNetwork communication
The invention provides an intranet and extranet communication method and system, and the method is applied to an intranet and extranet communication system. The intranet and extranet communication system comprises a first gateway, a second gateway, a strong isolation device and an intranet database, and the intranet gateway is connected with the first address of the intranet database; and the extranet gateway is connected with the second address of the intranet database. Under the condition that the first gateway receives an HTTP request which is sent by the application and is used for indicating the access end to access an opposite end network, the HTTP request is stored in the intranet database; the second gateway writes the obtained request result of a to-be-processed HTTP request intothe intranet database under the condition that the to-be-processed HTTP request in the intranet database is queried; and the first gateway outputs a request result to the application when detecting that the request result of the HTTP request is stored in the intranet database. In the application, both the intranet application and the extranet application have no direct relationship with the intranet database, so that the intranet application and the extranet application are not influenced by database change, and the communication efficiency of the intranet and the extranet can be improved.
Owner:BEIJING HUITONG JINCAI INFORMATION TECH +3
Channel allocation method and central base station for security services in electric power wireless private network
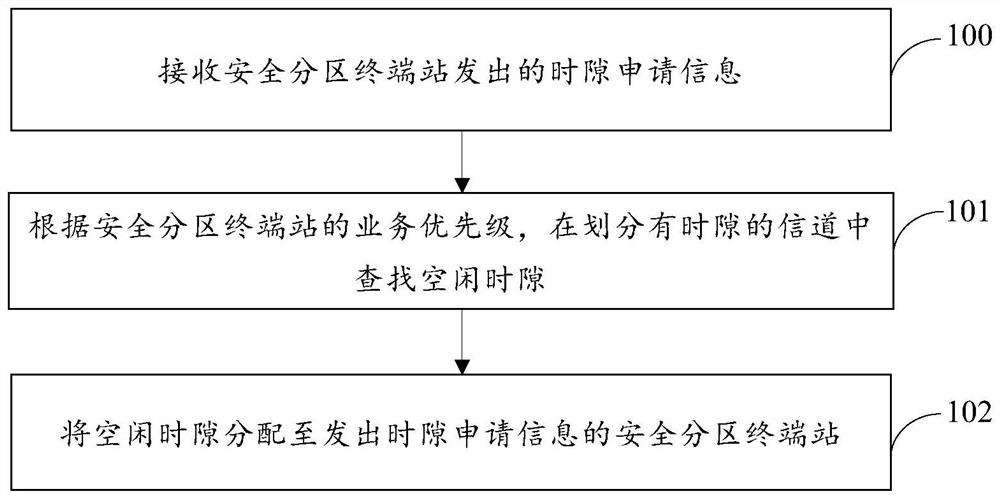
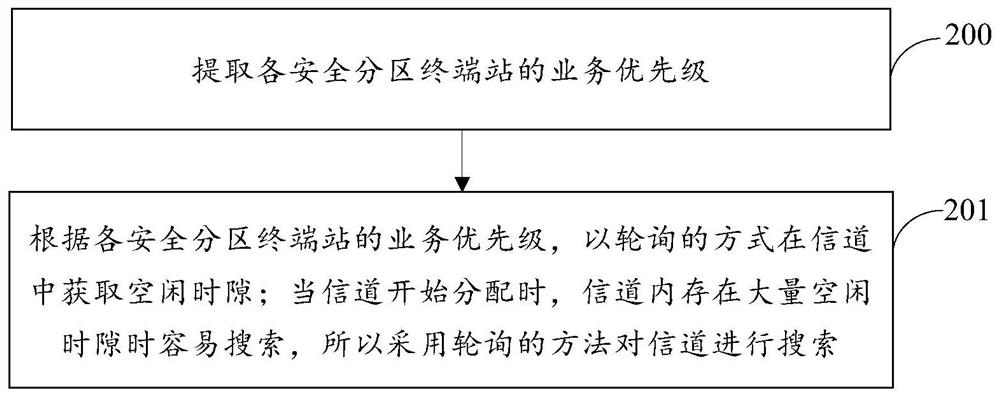
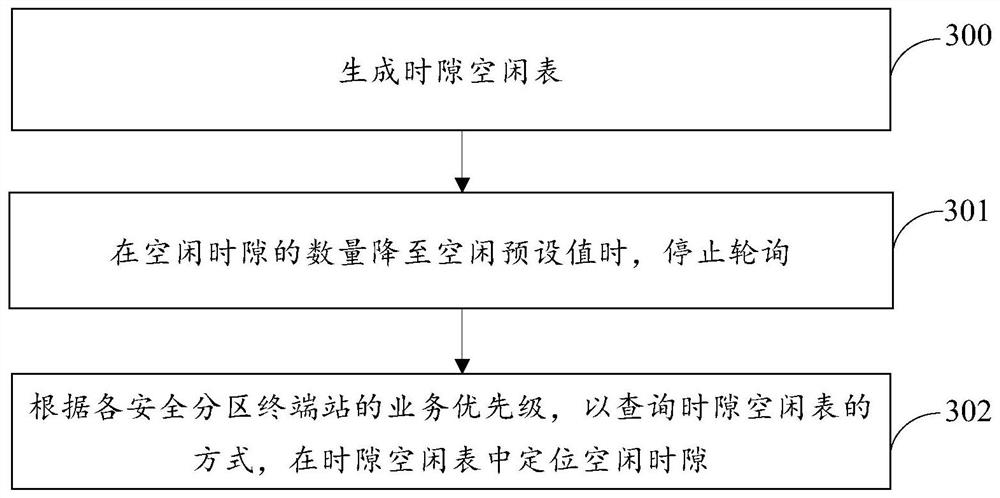
ActiveCN106455073BReduce occupancyImprove utilization efficiencyWireless communicationStationPrivate network
The present invention provides a channel allocation method and a central base station for security services in a power wireless private network. The method receives time slot application information sent by a terminal station in a security zone, and the time slot application information includes the services of the terminal station in the security zone. Priority; according to the service priority of the terminal station in the security zone, search for a free time slot in a channel divided into time slots; allocate the free time slot to the terminal station in the security zone that sends the application information for the time slot; The central base station is equipped with an application receiving module, a time slot query module and a time slot allocation information sending module. The present invention effectively reduces the occupation of channel capacity during service transmission, and improves the efficiency of wireless spectrum utilization. It has low cost, flexibility and strong scalability, and realizes independent and fast transmission of service data, thereby completing the transmission of different services. Air interface physical layer isolation improves the security and reliability of business data transmission.
Owner:STATE GRID JIBEI ELECTRIC POWER COMPANY +2
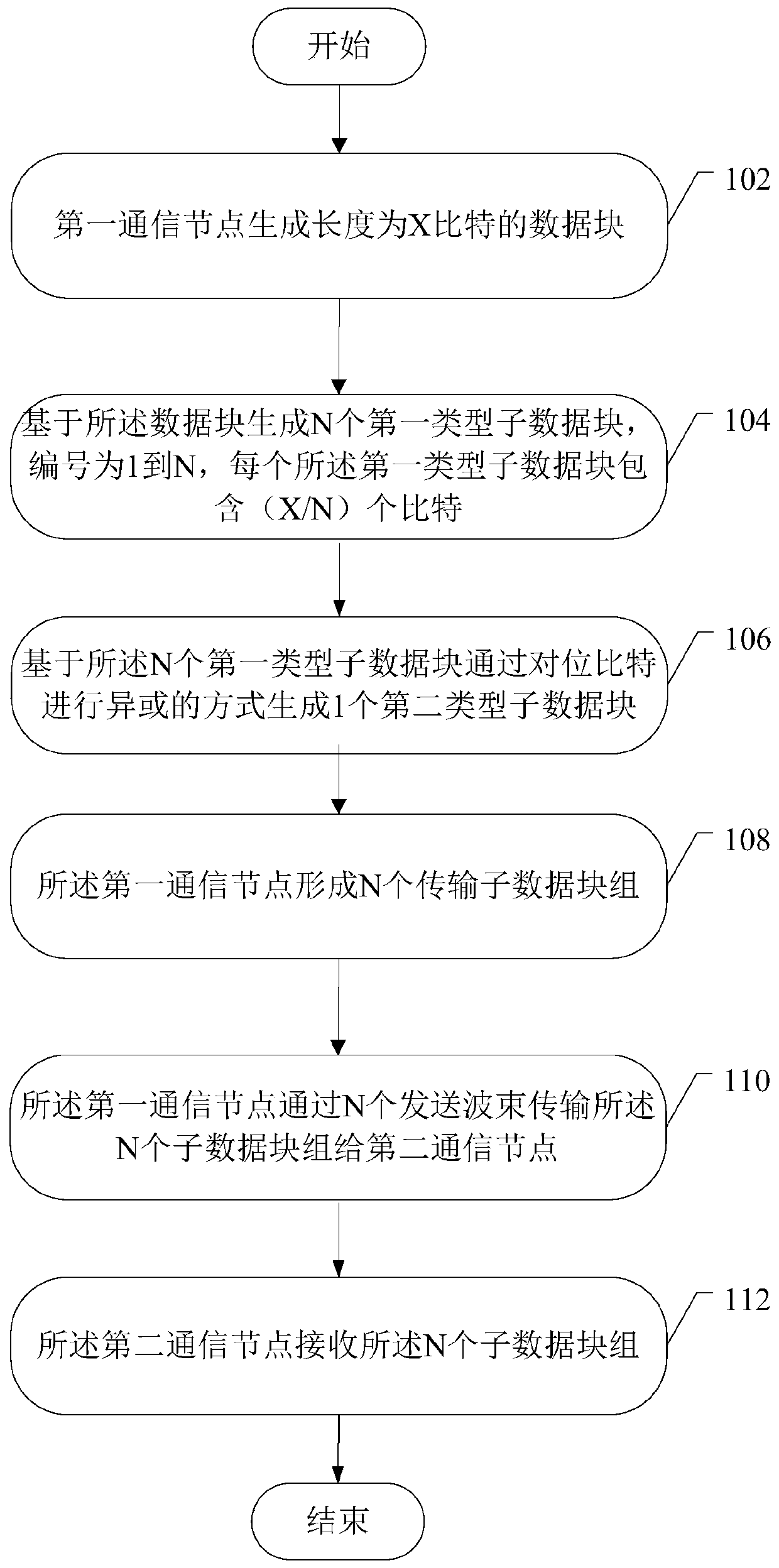
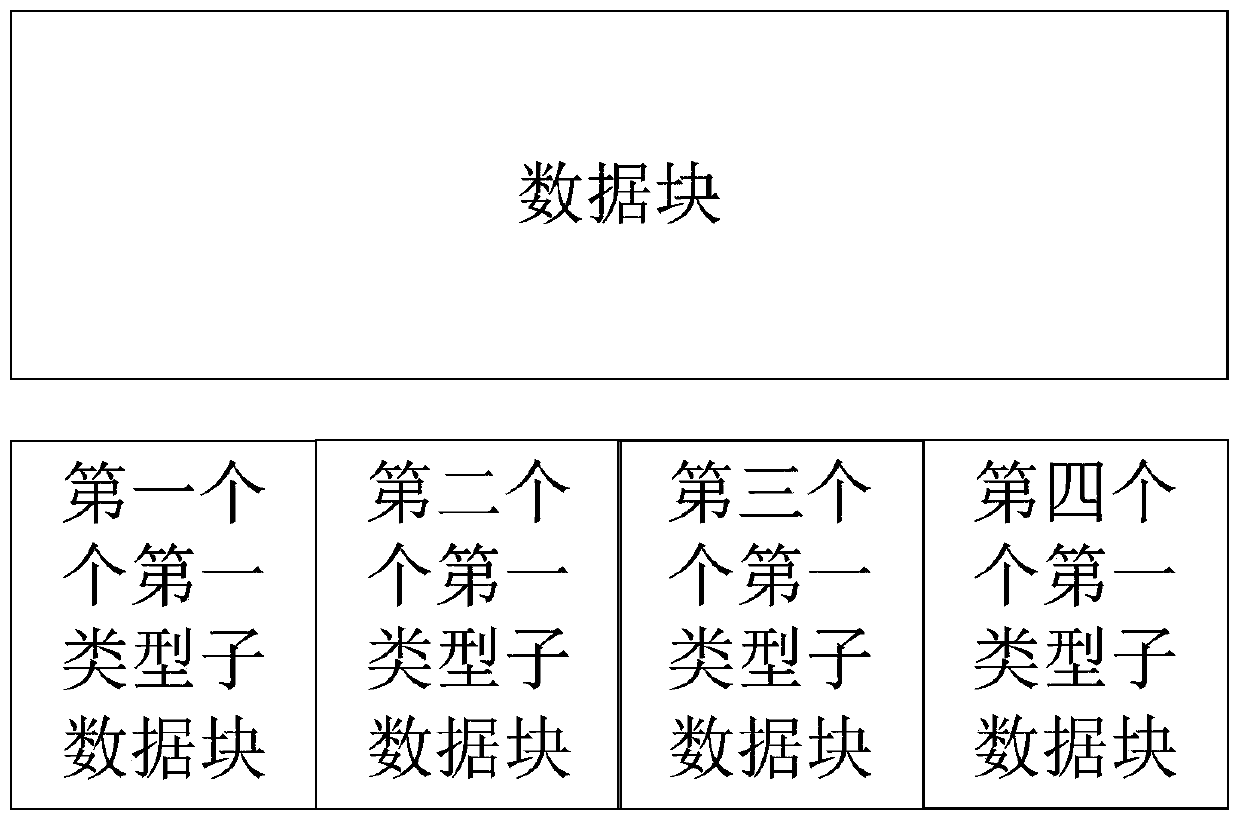
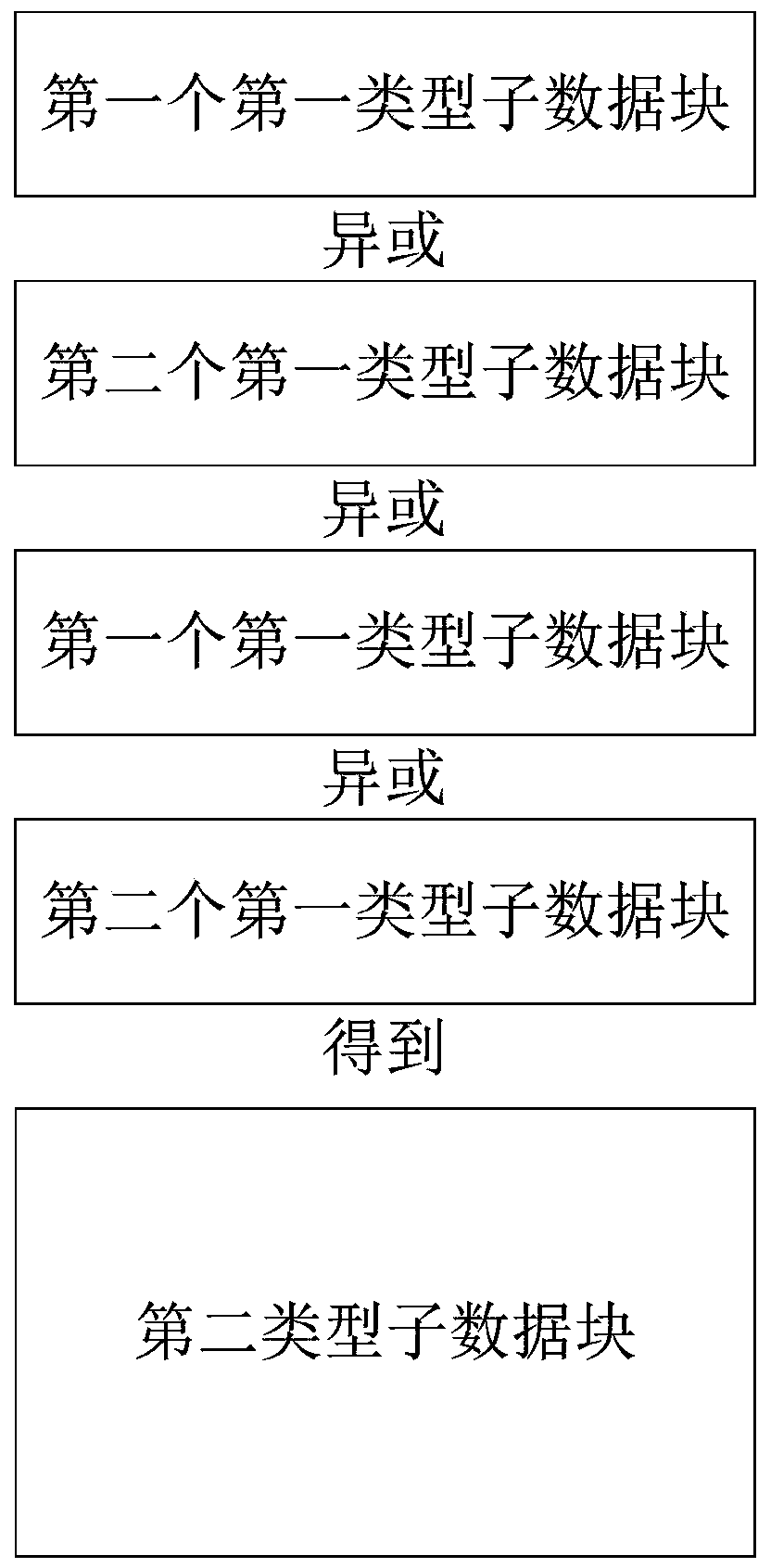
A Robust Data Transfer Method
ActiveCN106506117BImprove robustnessAdapt to business needsError preventionCommunications systemFifth generation
The invention provides a data transmission method of robustness. The method comprises the following steps: generating a data block with the length of X bit by a first communication node, wherein the data block comprises cyclic redundancy check information, and generating N first type sub-data blocks containing X / N bits through the data block, and then generating a second type sub-data block containing X / N bits through a counterpoint bit or XOR mode based on N first type sub-data blocks; respectively forming N transmission sub-data block groups through the N first type sub-data blocks and the second type sub-data block, and transmitting N sub-data block groups at N sending beams. The received second type sub-data block can be used for attempting to recovering the first type sub-data block in error. Through the adoption of the method, device and system provided by the invention, the robustness of the data transmission can be effectively increased to adapt to the service demand of the fifth generation wireless communication system in comparison with the prior art.
Owner:SHENZHEN POLYTECHNIC
Method and system for processing business work orders
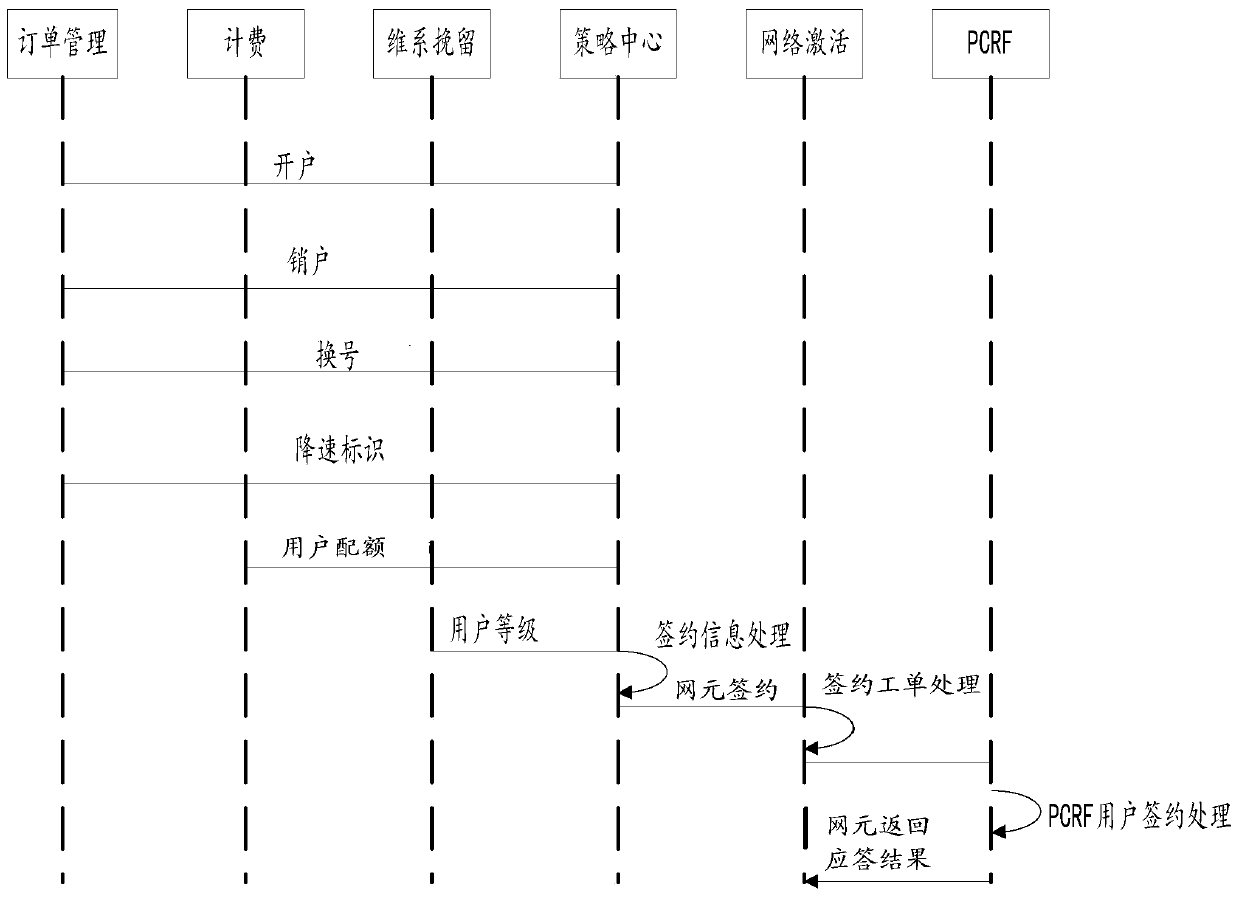
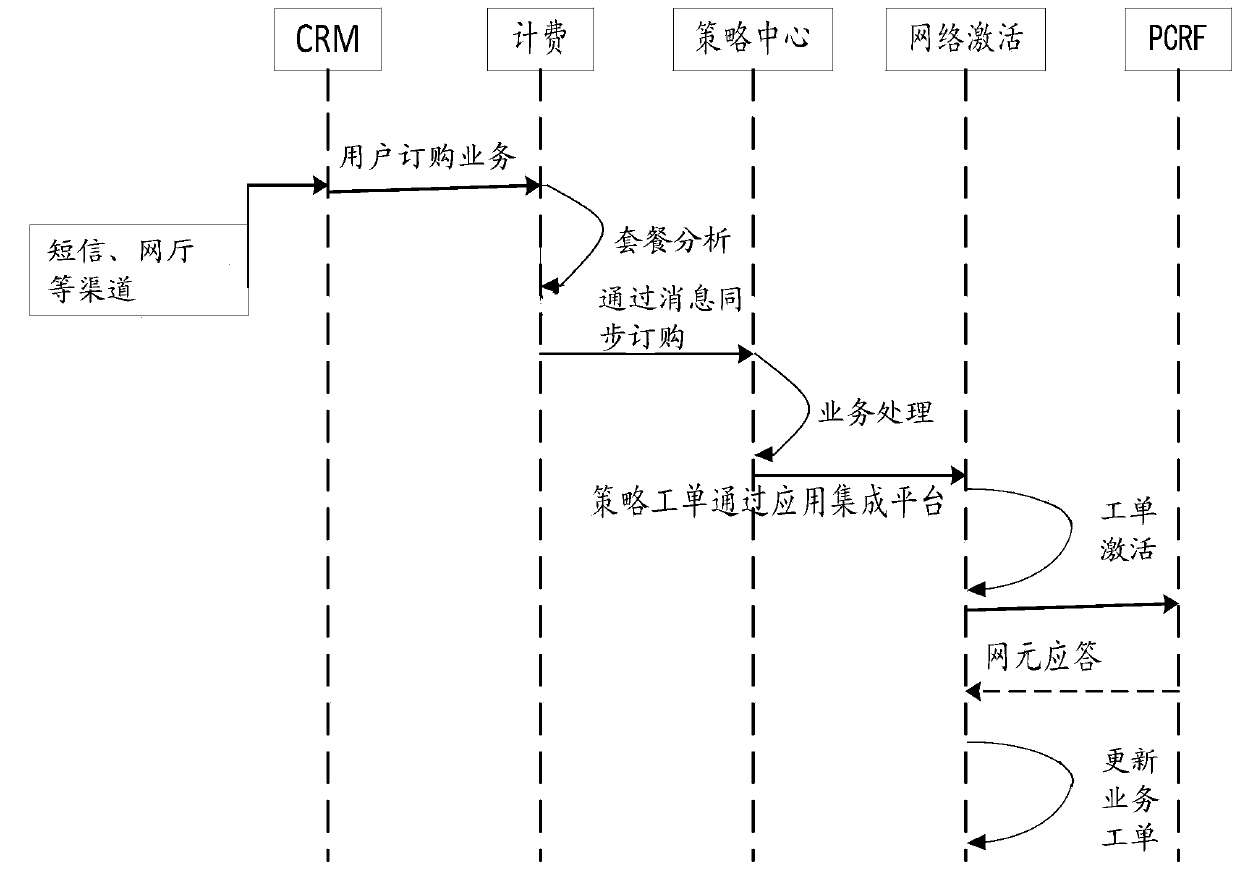
ActiveCN107276790BIncrease flexibilityImprove processing efficiencyData switching networksData synchronizationTerm memory
The invention relates to a processing method and system of a service work order. The processing method comprises the steps of S1, receiving a message, analyzing the message and putting the analyzed message into an interface table; S2, carrying out service logic processing for the data, and judging whether a strategy control instruction needs to be sent or not; S3, carrying out parameter supplementation and strategy decomposition; S4, sending the data to a network activation center synchronously, carrying out network element interaction with a strategy and charging rule function unit, and updating the service work order. The invention also relates to a system which comprises a message reception module, a strategy engine module, a strategy service supplementation and decomposition module, and a network activation module. Through the processing method and system of the service work order, configuration data are stored in a memory, the efficiency is improved, flexible configuration of the service work order is realized, and the processing method and system of the service work order can adapt to demands of all kinds of services in a better manner.
Owner:北京思特奇信息技术股份有限公司
Data query method and device based on integrated data
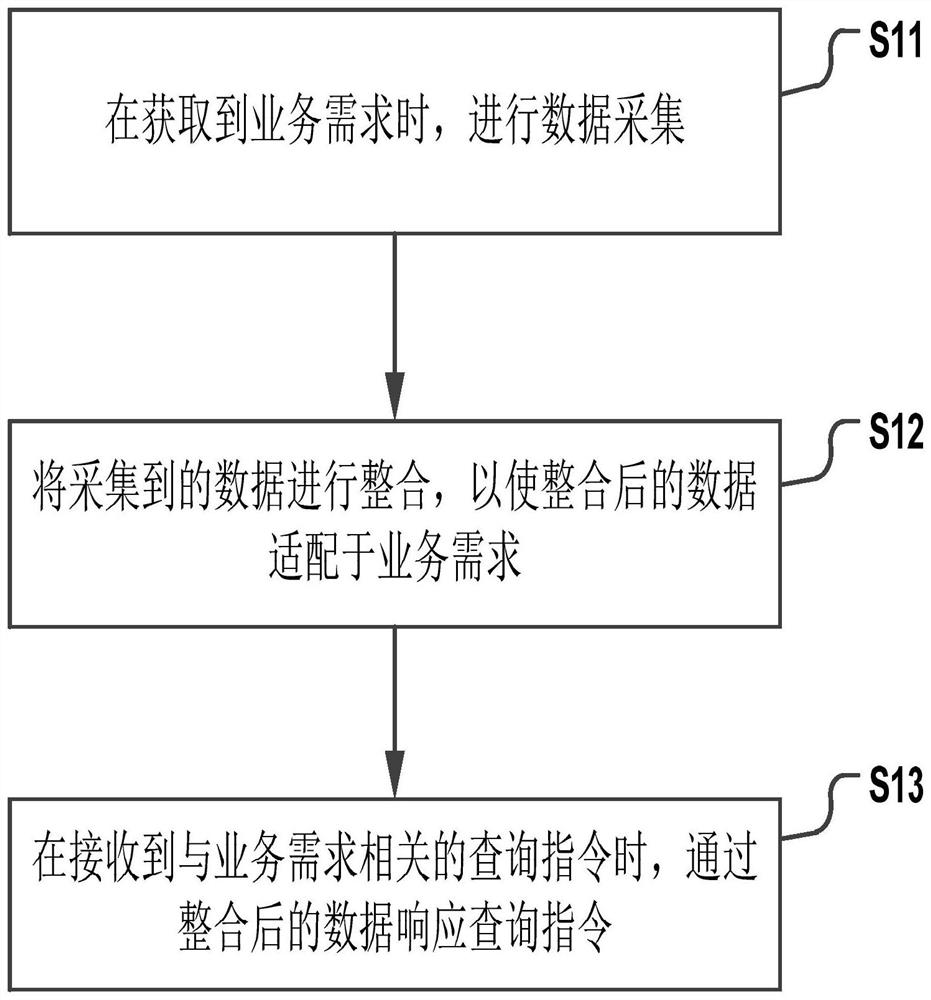
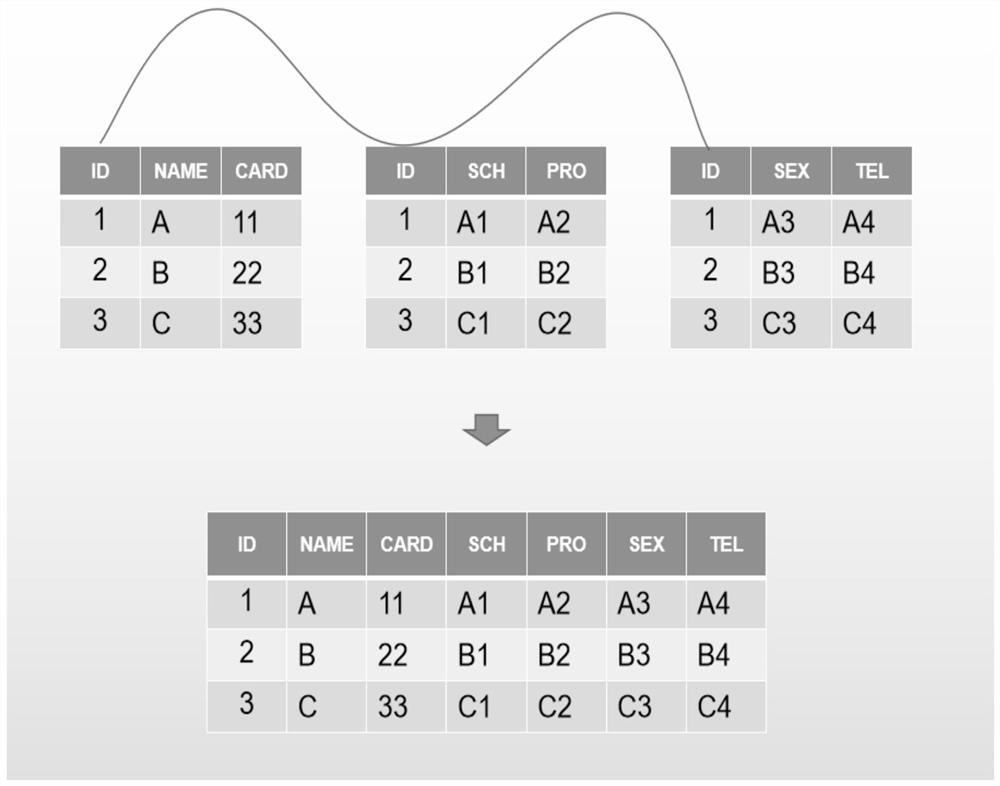
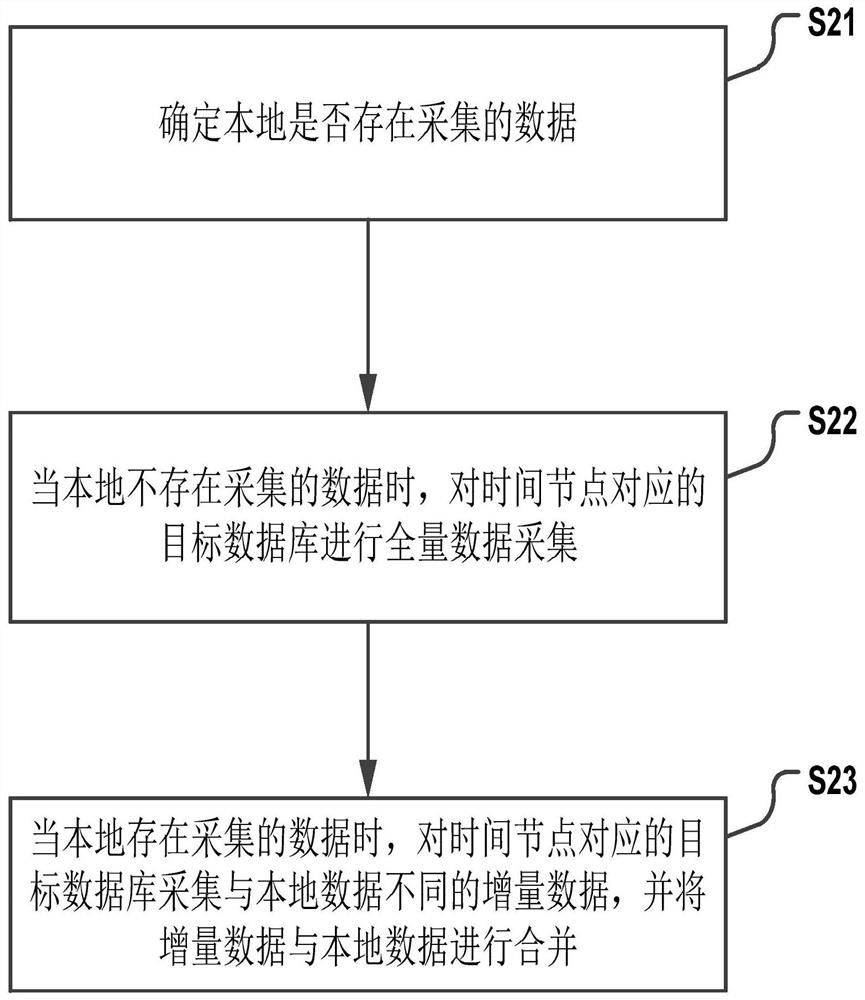
PendingCN112069215AImprove extraction efficiencyReduce the probability of extraction failureDigital data information retrievalSpecial data processing applicationsData ingestionData acquisition
The invention discloses a data query method and device based on integrated data. The method comprises the following steps: when a service demand is obtained, acquiring data; integrating the acquired data so as to enable integrated data to adapt to service requirements; and when a query instruction related to the service demand is received, responding to the query instruction through the integrateddata. By adoption of the scheme provided by the invention, the collected data can be integrated based on the service demand, so that the integrated data can adapt to the service demand, and after thequery instruction related to the service demand is received, the query instruction can be responded to based on the integrated data adapted to the service demand. Queried data can be adapted to the query instruction, so that the data extraction efficiency is improved, and the probability of data extraction failure is also reduced.
Owner:GUODIAN LONGYUAN ELECTRICAL
A demand-side resource control method and system
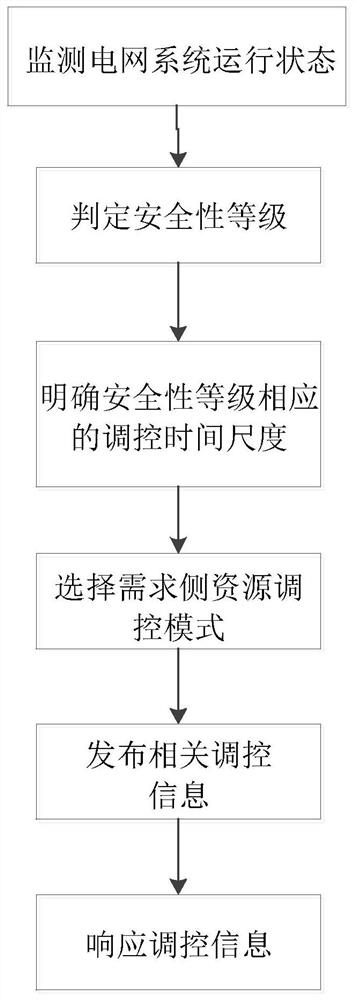
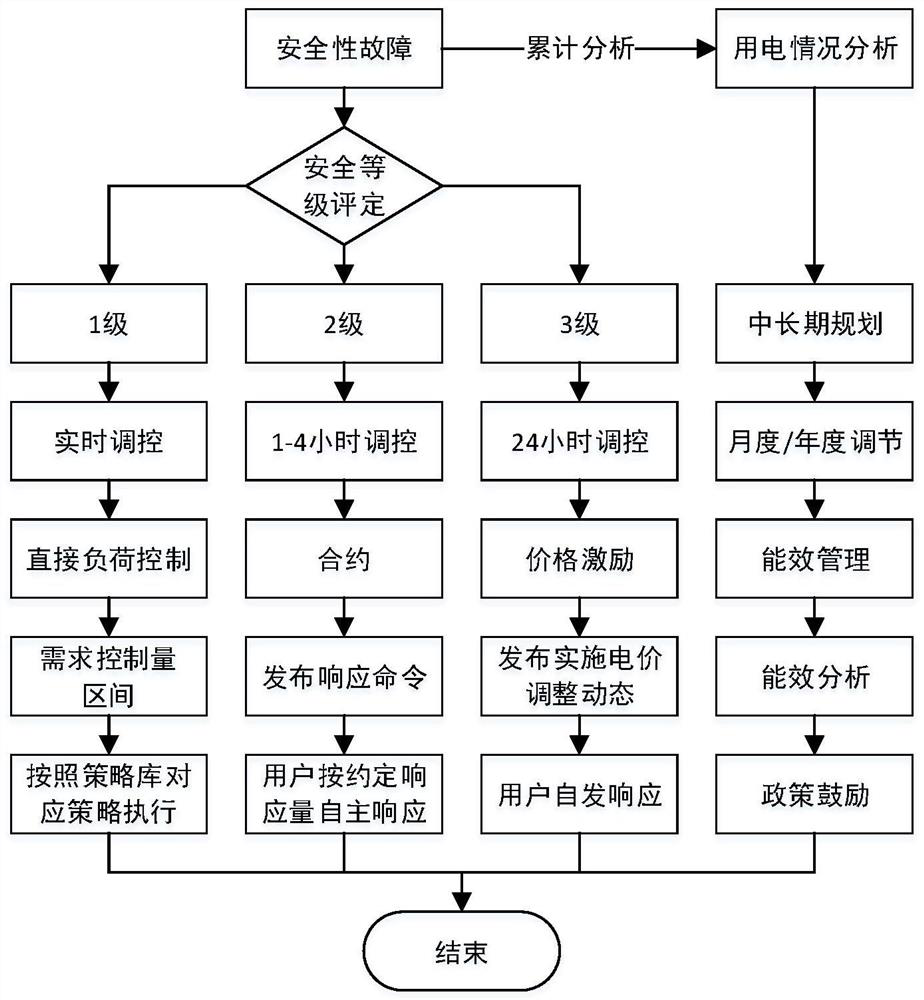
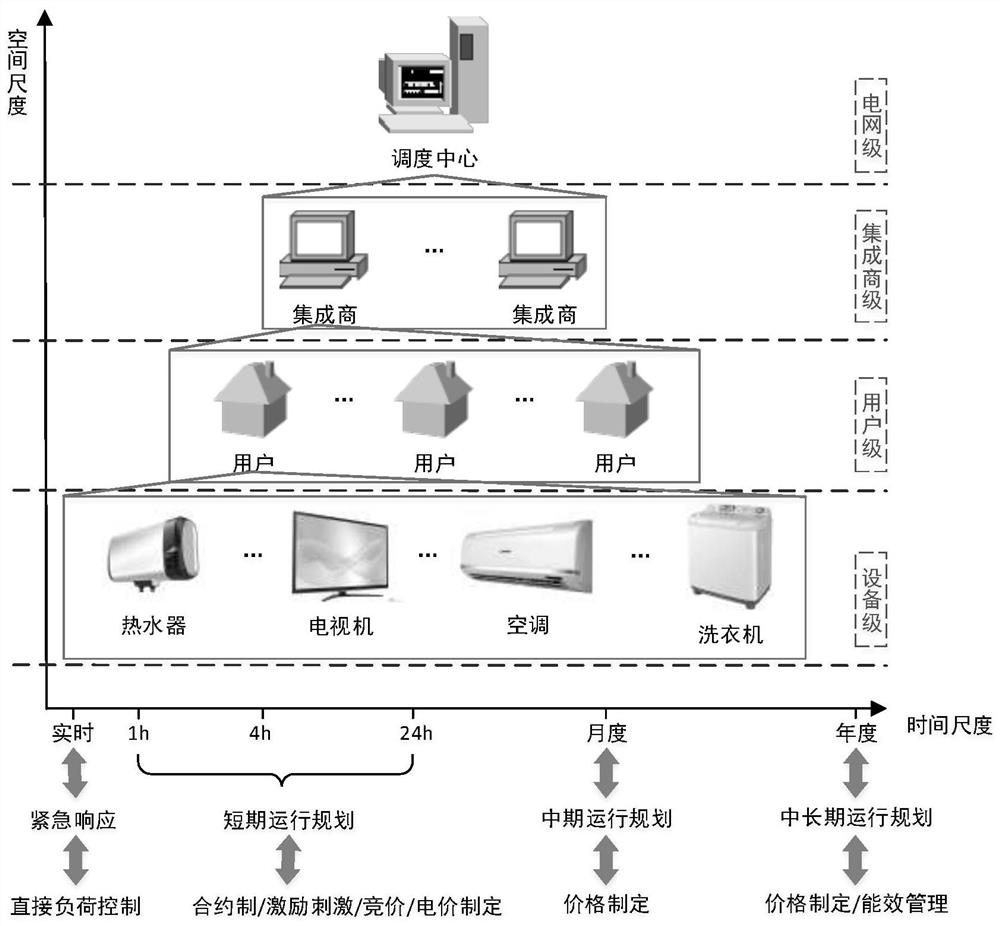
ActiveCN107887975BLarge participation spaceMeet regulatory needsCircuit arrangementsIntegratorPower grid
The present invention provides a resource regulation method on the demand side, including: monitoring the operation state of the power grid system, determining the security level, determining the regulation time scale corresponding to the security level, selecting the resource regulation mode on the demand side, and releasing relevant regulation information and a response to the control information; a demand-side resource control system, comprising: a communication module, a monitoring module, a data storage module and a processing module sequentially connected through a network cable. The invention can make the control requirements of the system more precise and match, realize more diversified choices under the condition of ensuring real-time business requirements in various scenarios, give users more room for participation, and adopt control corresponding to different time scales The mode selection strategy accurately locates the characteristics of each regulation mode, which is easier to meet the business needs of different time scales. At the same time, the multi-spatial scale regulation of load-user-integrator-grid can better adapt to the business under different granularity under the system need.
Owner:CHINA ELECTRIC POWER RES INST +2
Elderly long-term care demand evaluation input system and method
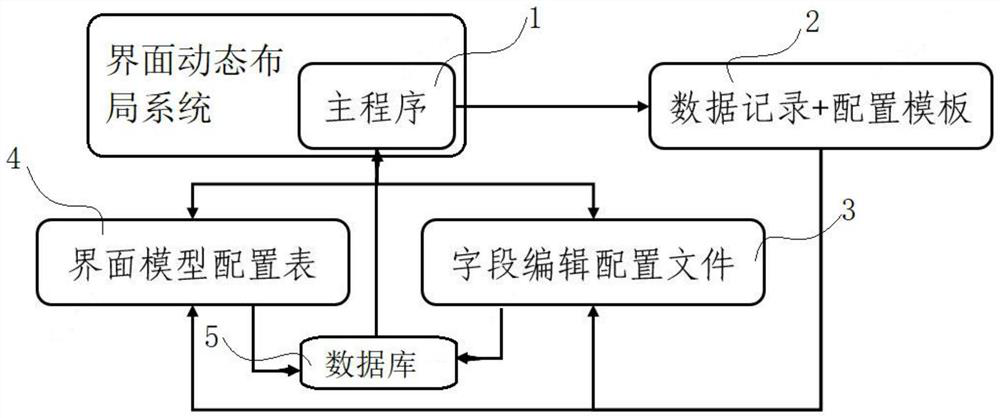
PendingCN113034327AClear structureClear thinkingNatural language data processingOffice automationSoftware engineeringData records
The invention relates to an elderly long-term care demand evaluation input system and method, and the invention comprises an interface dynamic layout system which is used for collecting information of a specified purpose; the invention further comprises a main program integrating an interface layout algorithm in the interface dynamic layout system, a data record, a configuration template, an input field editing configuration file, an interface model configuration table and a database of the interface model configuration table. The main program is a main program of an integrated interface layout algorithm developed on the basis of a C # language; and the invention has the advantages that dynamic layout of information collection and data input is realized by using a field editing configuration file and an interface model configuration table, so that service requirements can be more flexibly adapted, and the purposes of simplifying the process is achieved. The invention has the advantages that the efficiency is improved, errors are reduced, meanwhile, the nursing service demand condition of the old people is clearly reflected, the nursing efficiency is greatly improved, and the life quality of the old people is further improved.
Owner:丁汉升
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com