A low-cost digital signature sopc design method based on rsa and sha-512
A SHA-512, digital signature technology, applied in digital transmission systems, public keys for secure communications, encryption devices with shift registers/memory, etc. Product versatility and other issues, to achieve the effect of improving computing speed, resisting side-channel attacks, and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The implementation of the present invention will be further described below in conjunction with the embodiments and accompanying drawings, but the implementation and protection of the present invention are not limited thereto. Those skilled in the art can realize and understand with reference to the prior art.
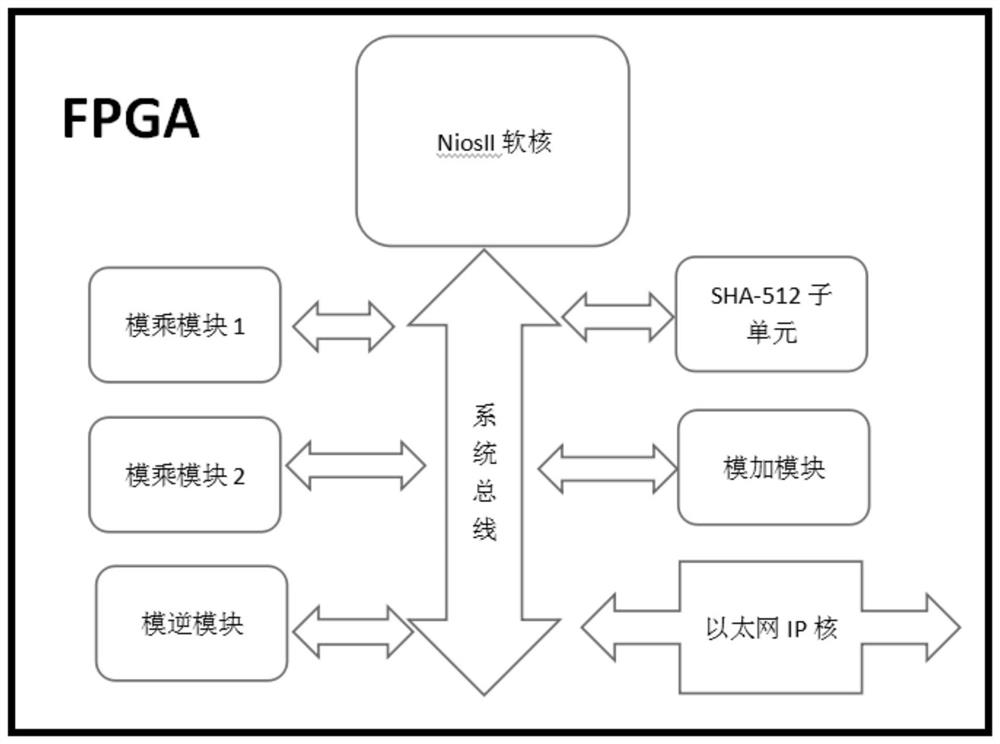
[0026] The system block diagram of this example is as follows figure 1 , the system is generated using ALTERA's tool Qsys, and the signature and verification process will be further detailed below.
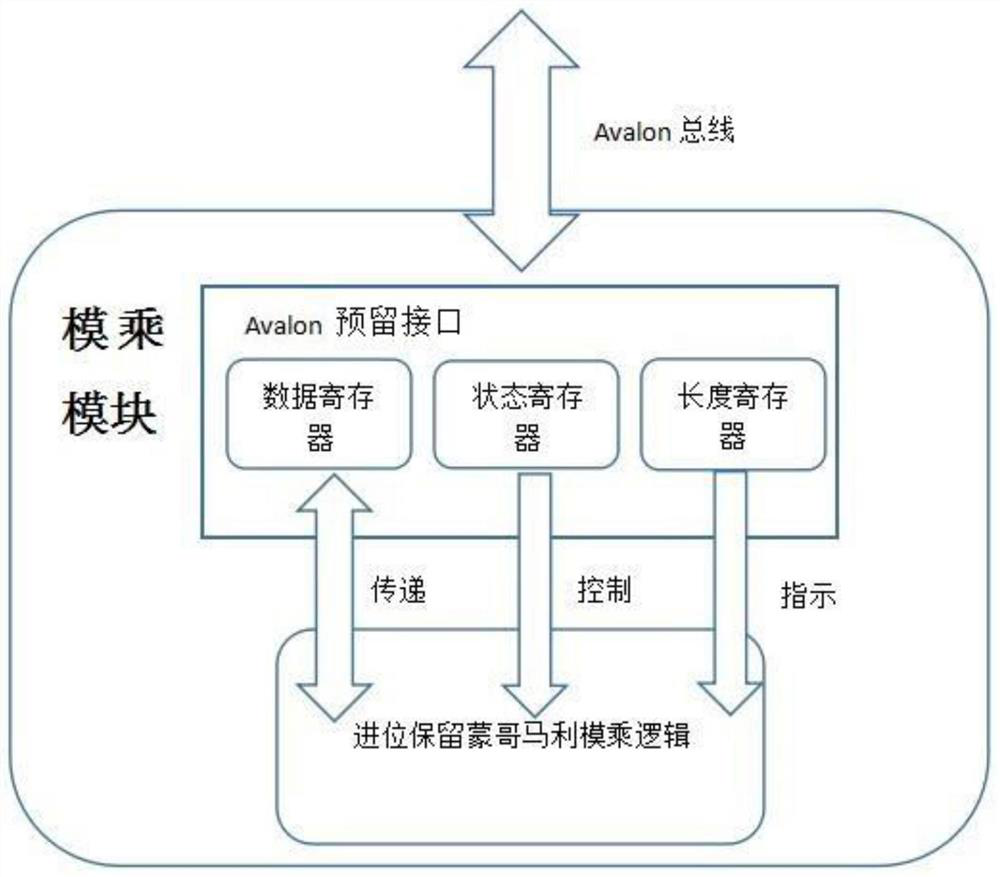
[0027] In the RSA private key and modulus on-chip ROM, NiosII reads the secret key and modulus through the avalon interface when the system is running, and the modulus is sent to the modulus module through the avalon interface after blinding N’=K*N. Among them, N is the correct modulus, K is a small random number, and N' is the result of blinding. The private key is stored in memory for later use.
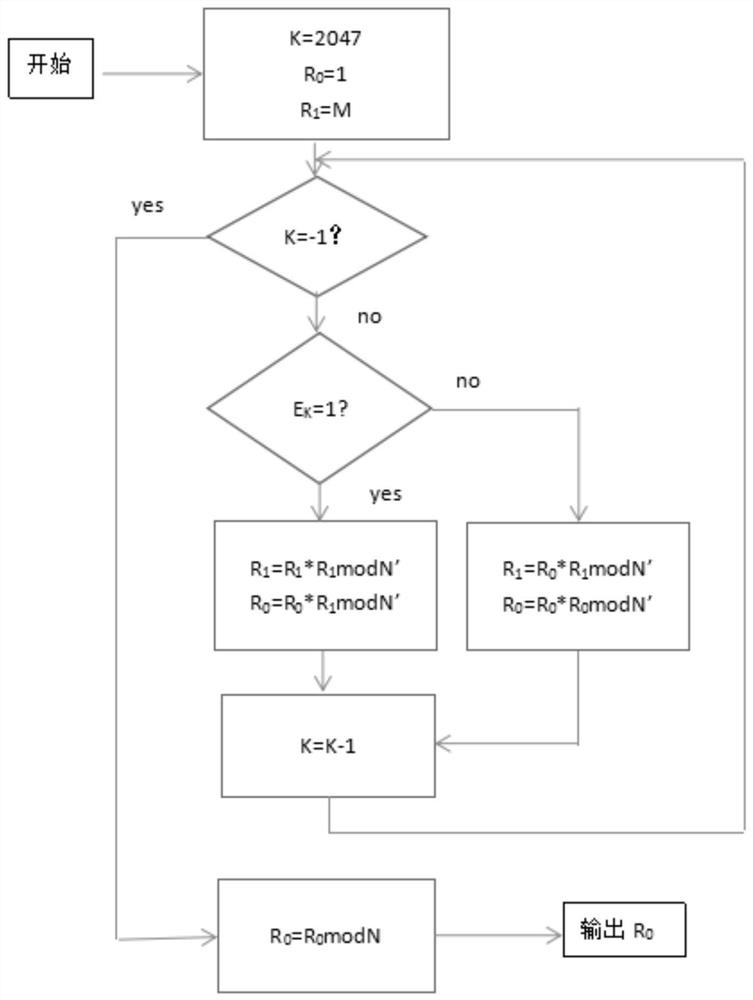
[0028] The signing process is as Figure 4 As shown, the system...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com