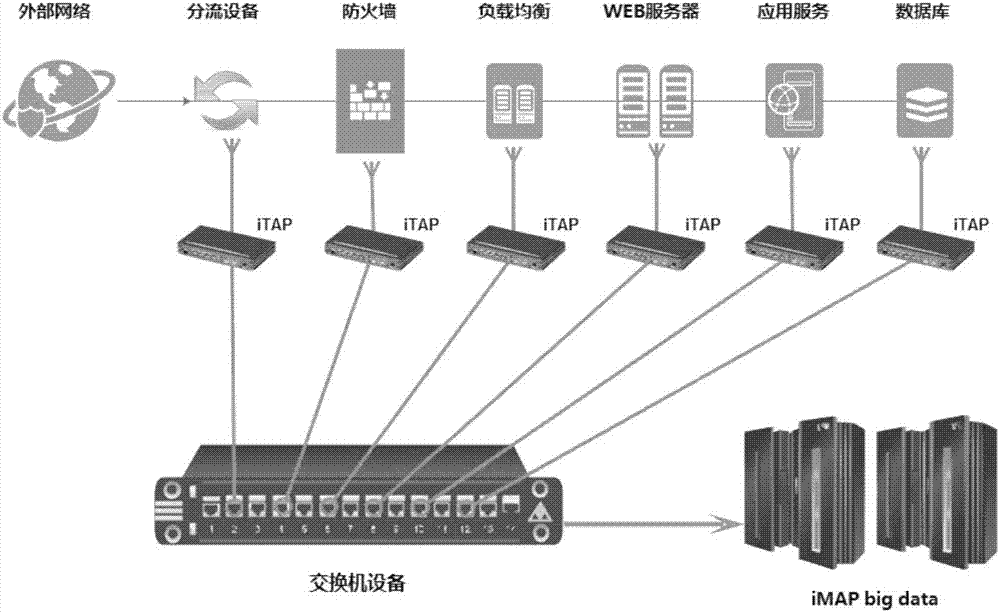
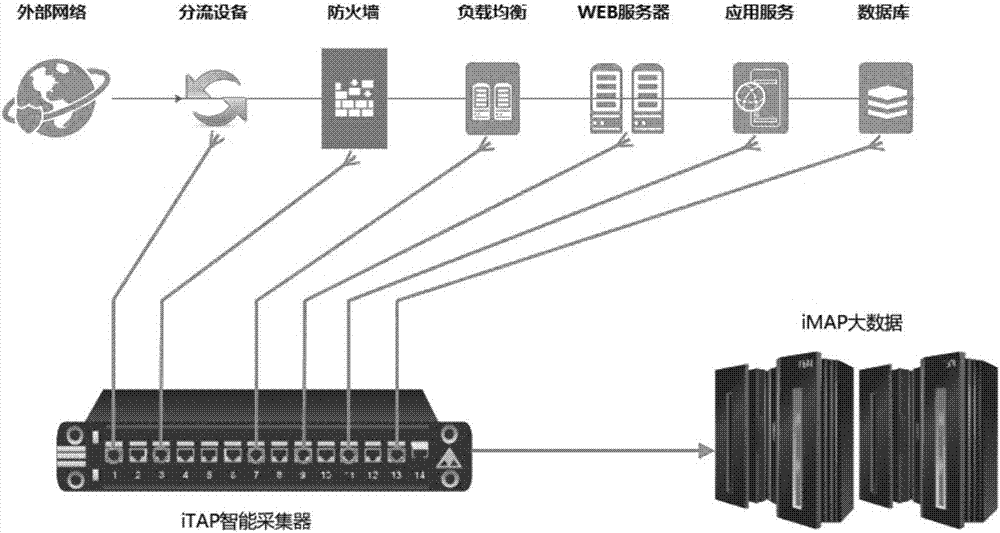
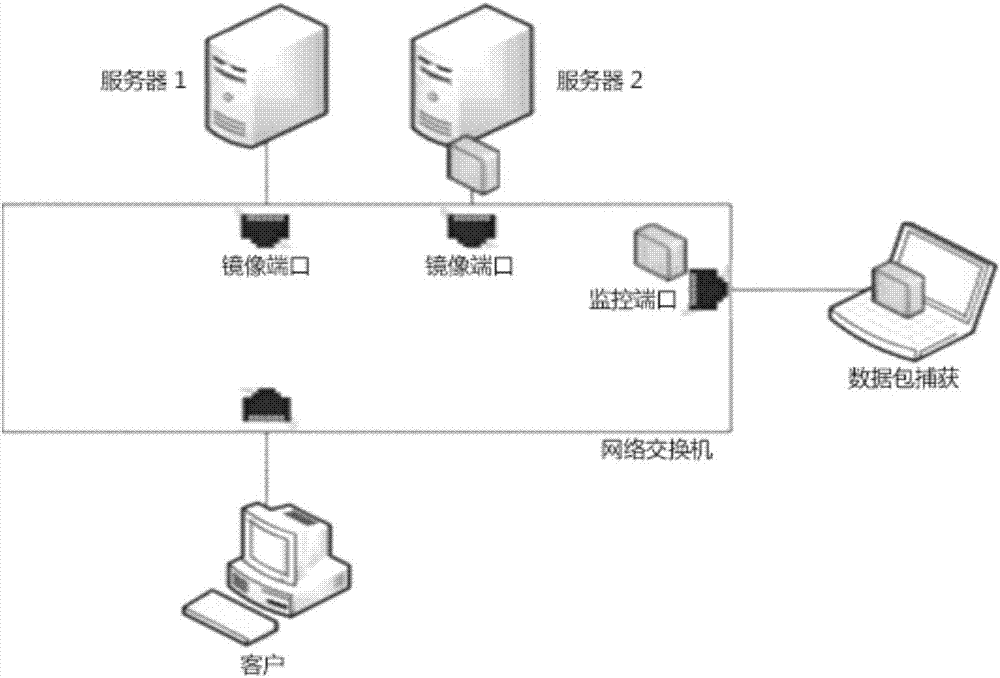
Data acquisition method based on metadata
A data collection and metadata technology applied in the information field to achieve the effect of saving deployment space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0044] 1.1 IEEE 802.1ad tag
[0045] IEEE 802.1ad and IEEE 802.1q are extensions of the network layer 2 protocol. The invention puts a second-layer label on the flow of different collection points to distinguish the flow of different ports. This action is done in the network card driver layer. For network cards that support IEEE802.1.ad, the required VLAN ID of IEEE 802.1ad is embedded in the Layer 2 protocol analysis, and the labeling algorithm is as follows:
[0046] 1) If the input is an Ethernet II message, add 802.1q TAG on the basis of the original message, TPID is: 0x8100, VID is the number of the physical port: starting from 2, 2, 3, 4 and so on.
[0047] 2) If it is an 802.1Q message, add the 802.1ad TAG on the basis of the original message, the TPID is: 0x88a8, and the VID is the number of the physical port: starting from 2.
[0048] 3) If the input is already an 802.1ad message, then it should
[0049] a. Configure the network card to accept such double-labeled ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com