A Computer Bios Design Method Based on Authentication and Credibility Metrics
A design method and reliability technology, applied in the direction of internal/peripheral computer component protection, digital data authentication, etc., can solve problems such as unsatisfactory security, loss, high requirements, etc., to ensure security, increase credibility, The effect of security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
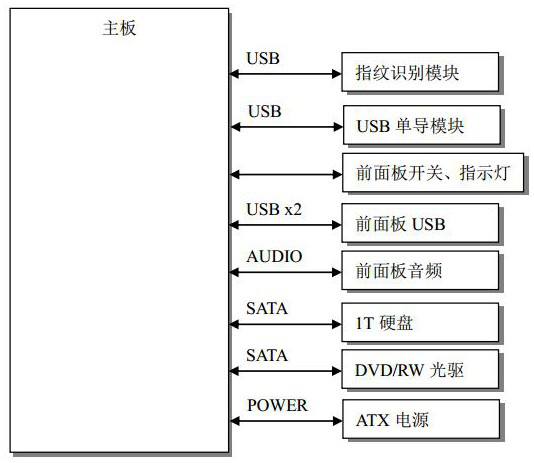
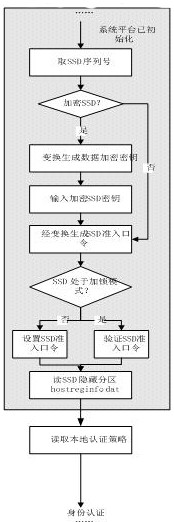
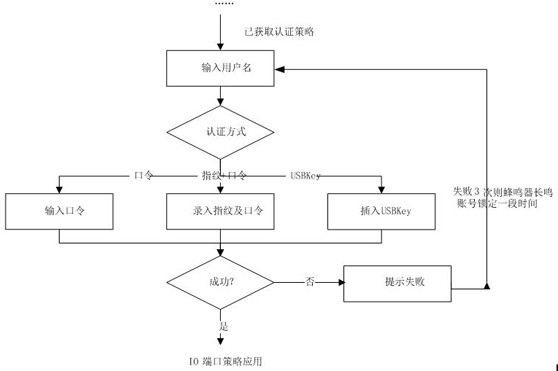
[0036] Such as Figure 1-4 as shown,
[0037] A computer BIOS design method based on authentication and trusted measurement, applied to computer security protection, comprising the following steps:
[0038] S01: After the BIOS is initialized, read the serial number of the SSD to determine whether it is an encrypted SSD; if it is an encrypted SSD, generate an encryption key for the encrypted SSD and execute the next step; if it is not an encrypted SSD, execute the next step;
[0039] S02: Generate a hard disk access password, select whether to insert the access password and verify the access password according to whether the hard disk is currently in a locked mode;
[0040] S03: Read the local authentication policy after passing the verifi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com