Method and apparatus for preventing access to pseudo base station
A pseudo base station, base station technology, applied in the field of communication technology security, can solve the problems of misjudgment, large parameter range, inability to accurately match parameters, etc., to avoid harm, improve accuracy, and improve the effect of preventive measures.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
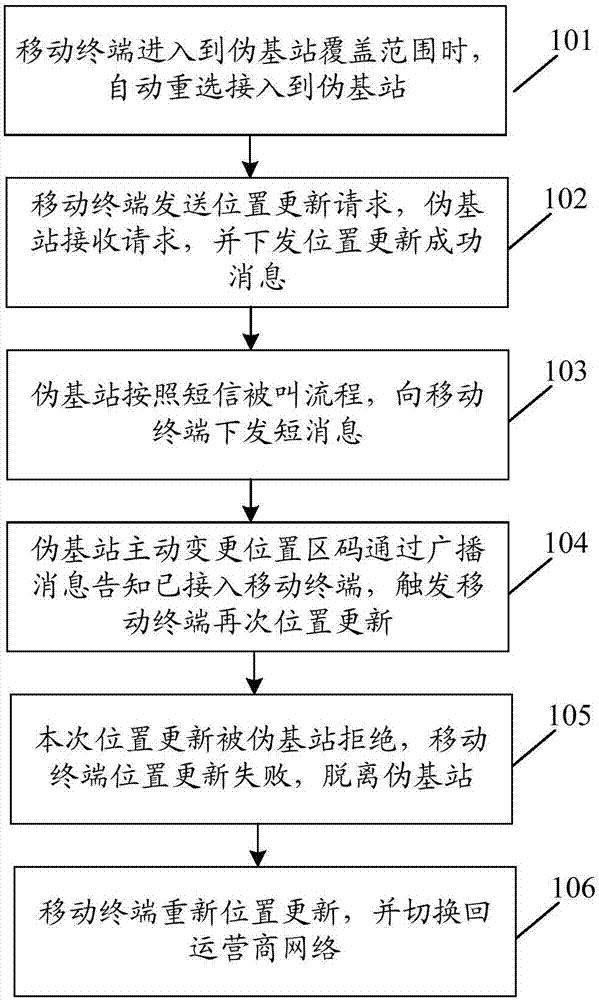
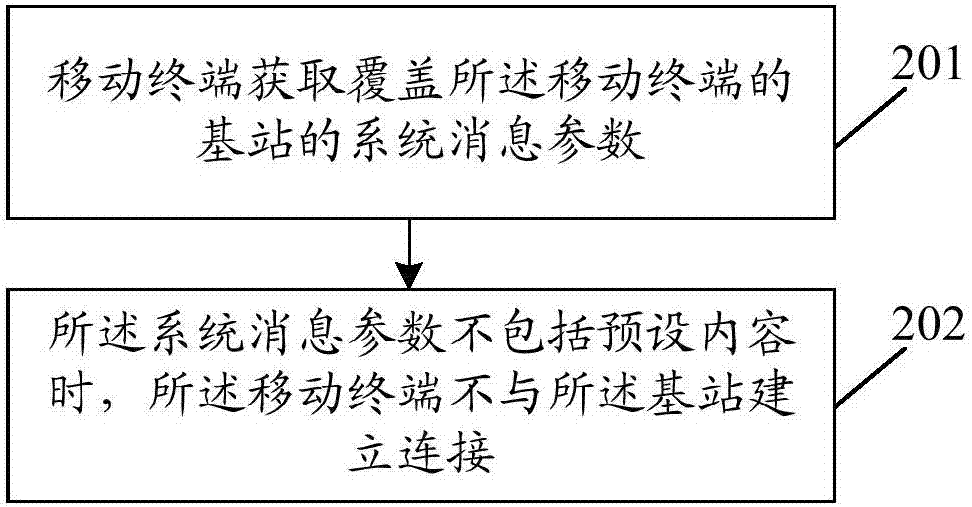
[0049] In this embodiment, the implementation process of the method for preventing access to pseudo base stations is as follows figure 2 shown, including the following steps:
[0050] Step 201, the mobile terminal acquires system message parameters of base stations covering the mobile terminal;
[0051] Usually, the air interface of the GSM network is used to realize the intercommunication between the mobile terminal and the fixed part of the GSM network, and the information on the air interface of the network is carried by various wireless logical channels. GSM logical channels are divided into two categories: traffic channel (TCH, TrafficChannel) and control channel (CCH, Control Channel). Among them, TCH mainly transmits services between the network and mobile terminals, such as voice and data; CCH is used to transmit The channel for signaling information and short packet data, the broadcast channel (BCH, Broadcast Channel) in the CCH is used to transmit information by br...
Embodiment 2
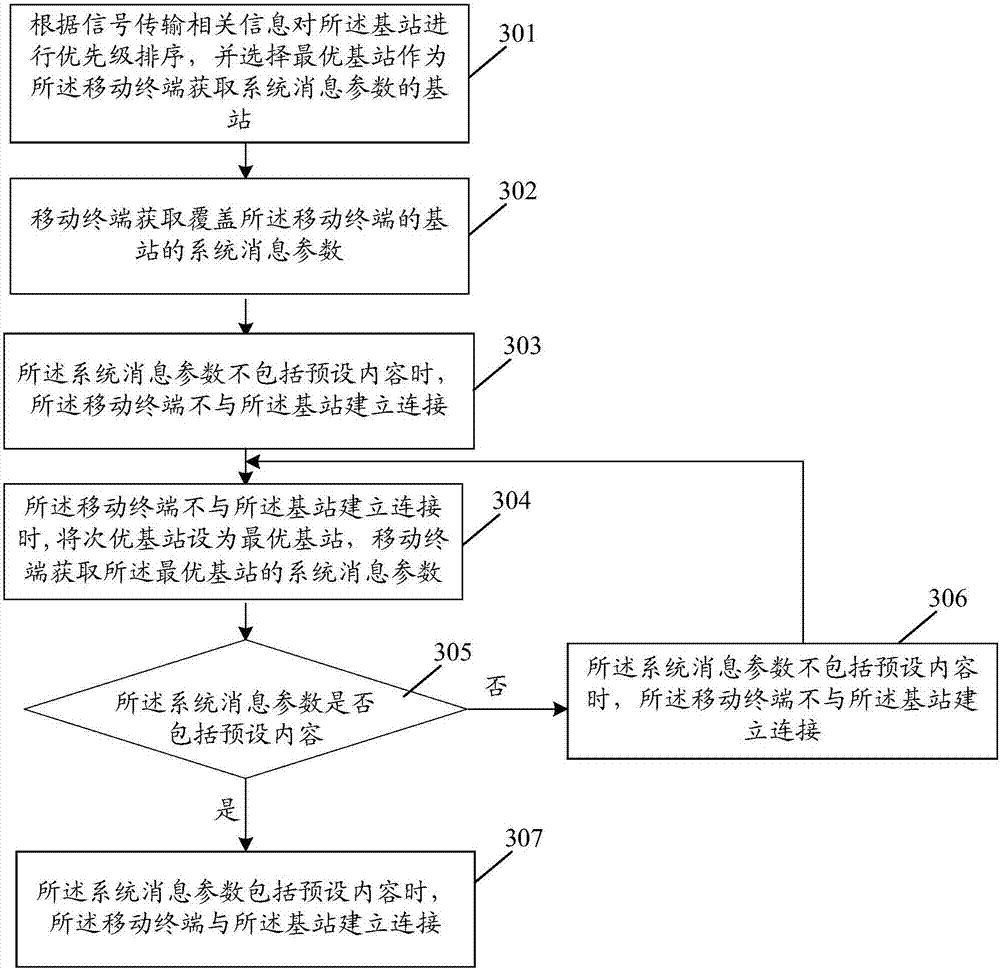
[0075] In this embodiment, considering that when the mobile terminal is within the coverage of multiple base stations, each base station can be judged one by one whether it belongs to a pseudo base station, then, for the convenience of judgment, each base station can be used for the base station according to the signal transmission related information. Priority sorting, sequentially judge whether each base station belongs to a pseudo base station and whether it can be accessed. The implementation process of the method for preventing access to pseudo base stations in this embodiment is as follows: image 3 shown, including the following steps:
[0076] Step 301: Prioritize the base stations according to signal transmission related information, and select the best base station as the base station for the mobile terminal to acquire system message parameters.
[0077] Here, the signal transmission-related information includes: signal strength, and / or the distance between the base...
Embodiment 3
[0110] This embodiment is a device using the method described in Embodiment 1. The composition and structure of the device for preventing access to pseudo base stations in this embodiment is as follows Figure 4 As shown, the device for preventing access to false base stations includes: an acquisition module 41 and a connection module 42; wherein,
[0111] The acquiring module 41 is configured to acquire system message parameters of base stations covering the mobile terminal;
[0112] Specifically, the information received by the acquisition module 41 includes system message types 1-4 and 7, 8 transmitted on the BCCH channel, and system messages 5 and 6 transmitted on the SACCH channel in the communication mode.
[0113] Before establishing a connection with a base station, the acquisition module 41 first acquires system information parameters of the base station, so as to detect whether the base station is a pseudo base station.
[0114] The connection module 42 is configure...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com