Embedded software credible property modeling and verification method
An embedded software and attribute modeling technology, which is applied in software testing/debugging, instrumentation, electrical digital data processing, etc., can solve the problems affecting the reliability and stability of the program system, compatibility, information interaction ability obstacles, and data verification process Lack of repair operations and other issues to achieve the effect of improving operating speed and data processing capabilities, improving system compatibility and scalability, and improving expansion capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
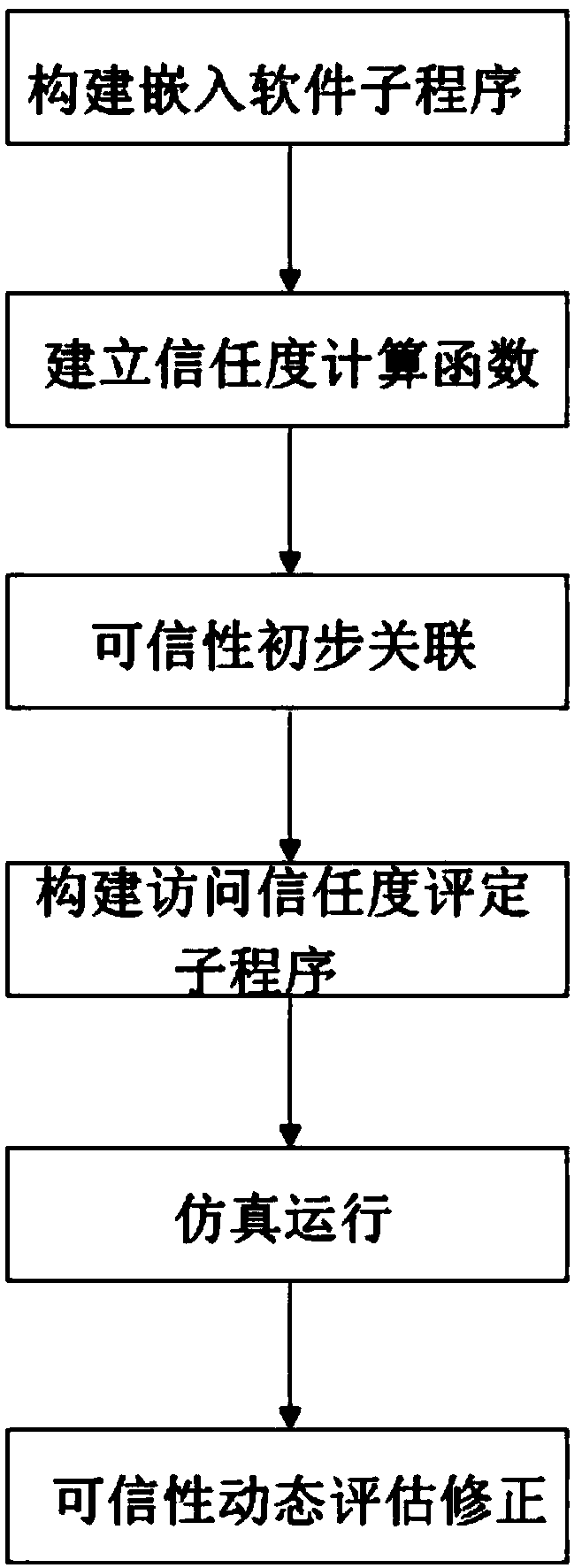
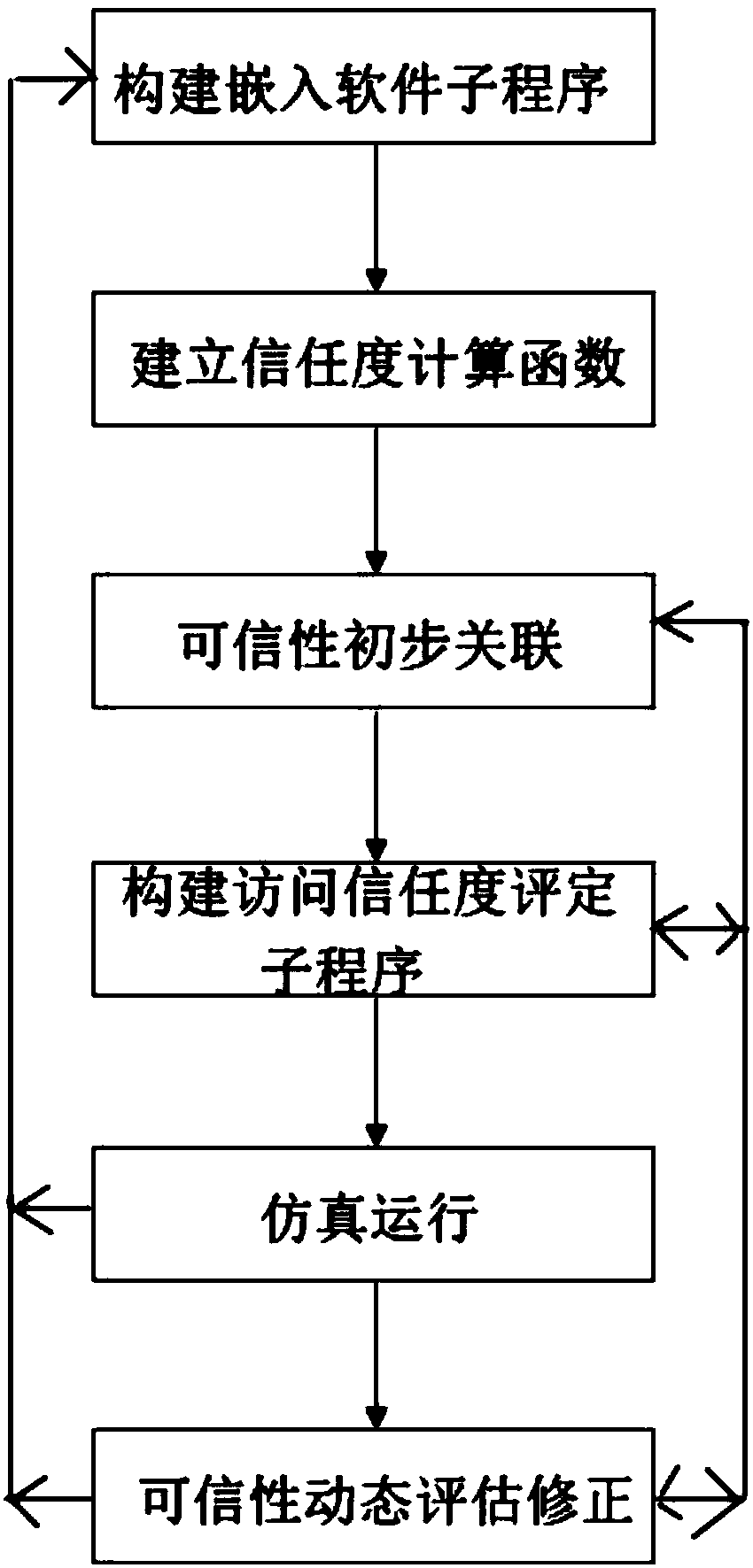
[0030] Such as figure 1 As shown in -4, a method for modeling and verifying trusted attributes of embedded software includes the following steps:
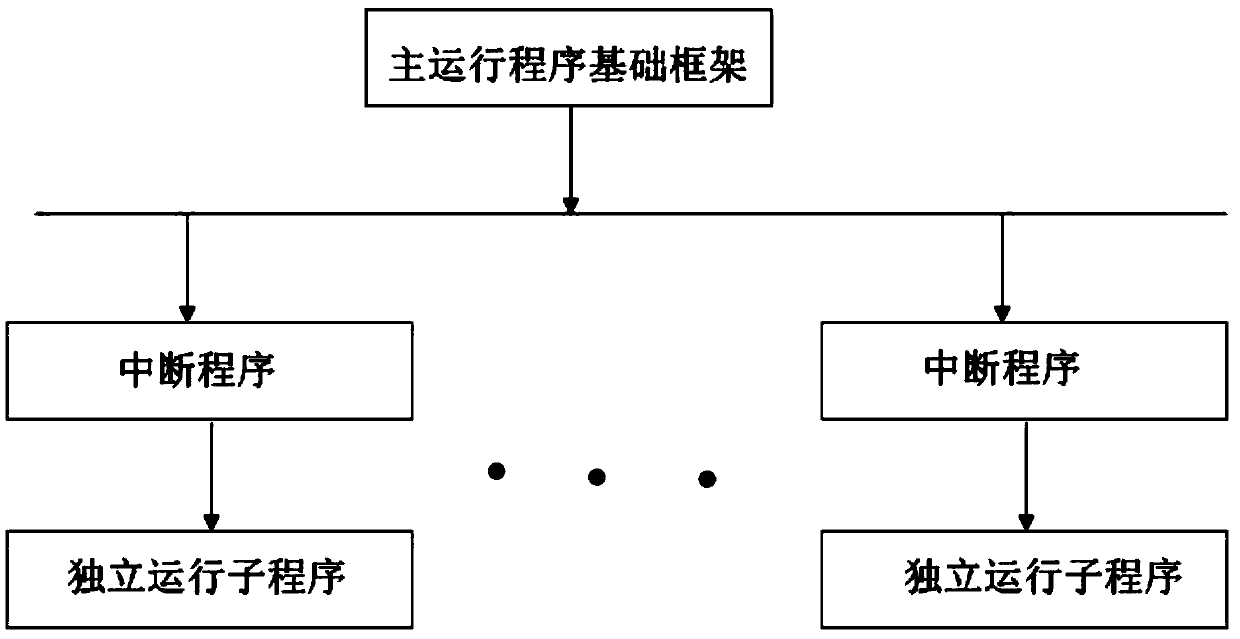
[0031] The first step is to build embedded software subroutines. According to the basic framework of the main operating program and according to the needs of use, compile at least one subroutine that meets the needs of each independent operation, and the independent operation subroutines are connected in parallel with each other. The corresponding interrupt programs are compiled for the operating conditions, and then the independent operating subroutines are embedded into the basic framework of the main operating program through the interrupt program;
[0032] The second step is to establish the trust degree calculation function. After the first step is completed, at least 3 groups of data groups that are directly related to the data in the basic framework of the main running program are selected from each independently running sub...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com