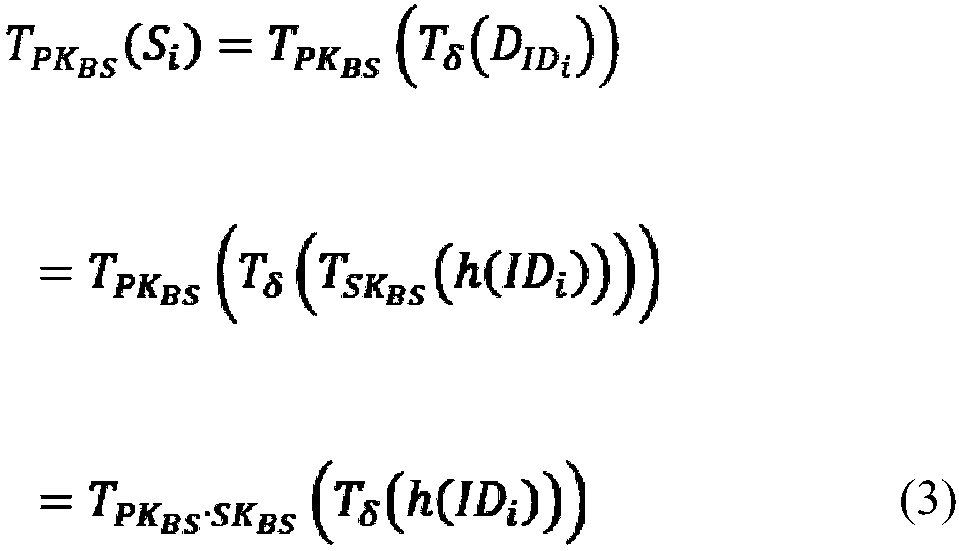Wireless sensor network broadcast identity authentication method based on chaos
A wireless sensor and identity authentication technology, applied in the field of wireless sensor network broadcast identity authentication based on chaos, can solve the problems of reducing wireless sensor network overhead, initial parameter overhead, limited wireless sensor network hardware resources, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
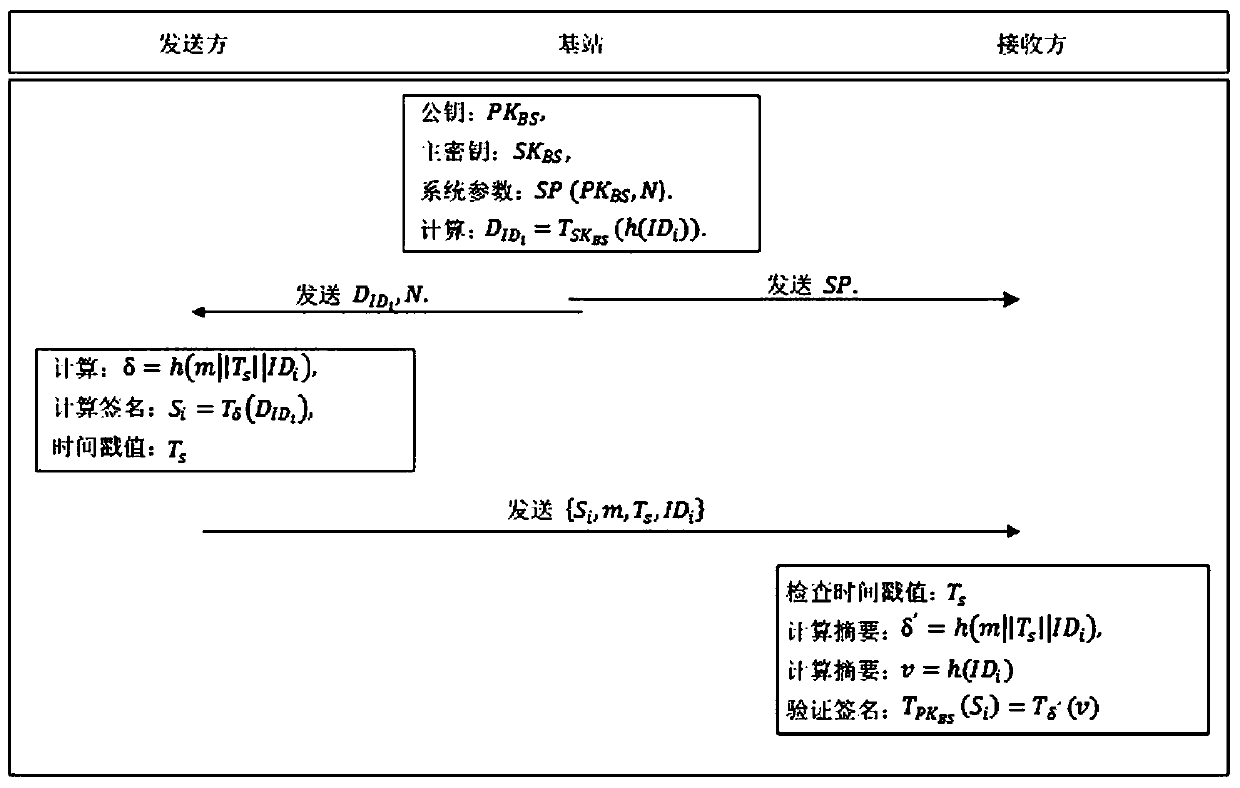
[0072] A chaos-based wireless sensor network broadcast identity authentication method, comprising the steps of:
[0073] 1) System initialization: In this example, the base station acts as a private key generation center and is a trustworthy entity. The system initialization phase is completed in the base station. The base station randomly selects two different large prime numbers P and Q, which have The same number of digits, then calculate N=P·Q according to P and Q, and L=(P 2 -1)(Q 2 -1), select the private key SK of the base station BS , (0BS BS , the calculation result needs to satisfy the condition: SK BS ·PK BS ≡1(mod L), master key SK BS Only stored in the base station, the system parameters SP(PK BS , N) public;
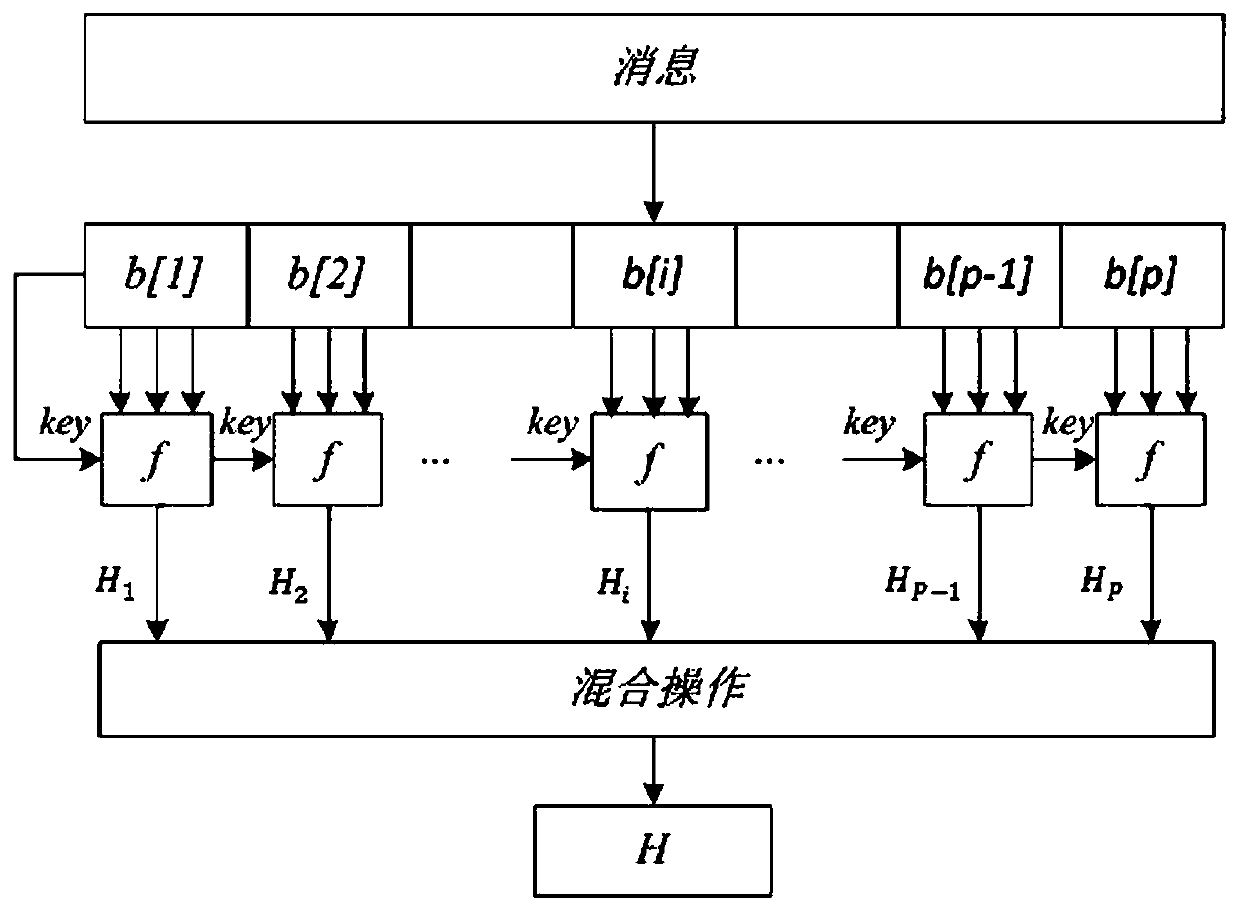
[0074] 2) Key generation: In this stage, a secure hash function h( ) is selected, and the base station uses the master key SK BS Through the identity information ID corresponding to the node S To calculate the respective private keys of all sensor n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com