Human face identification method and system
A face recognition and identification code technology, applied in the field of recognition, can solve the problems of low security of human biometric identification systems, and achieve the effect of avoiding system application defects and improving safety and effectiveness.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
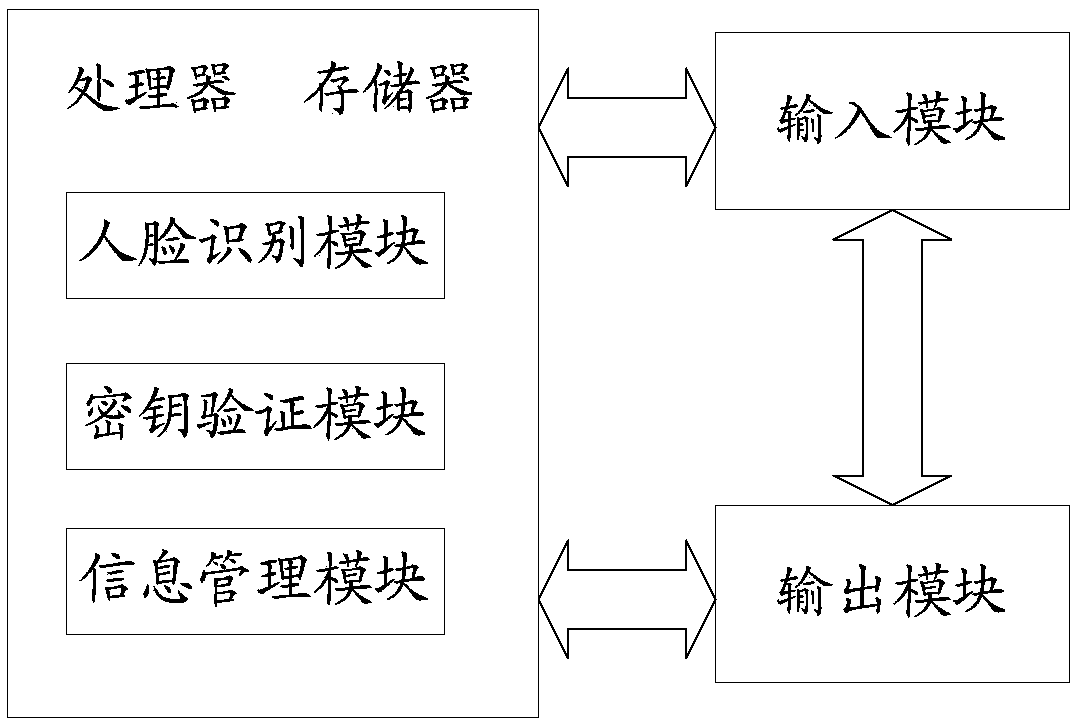
[0034] Embodiment 2: as image 3 The shown face recognition system includes: an input, an output module, a processor and a memory, and further includes: a face recognition module, a key verification module, and an information management module. The difference from Example 1 is that:
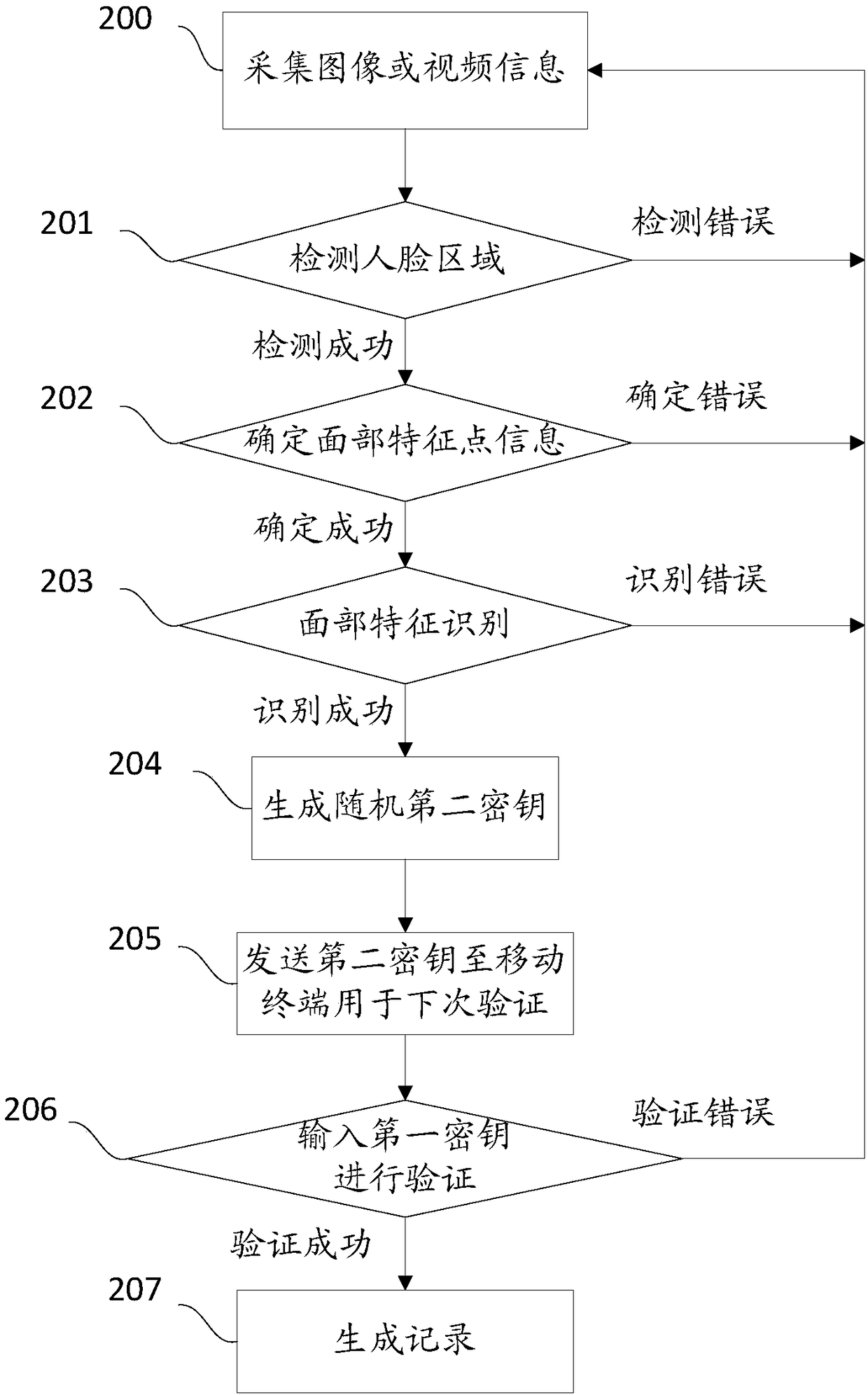
[0035] First of all, the information database in the information management module pre-stores a piece of face and facial feature information, and at the same time pre-stores a first key corresponding to the identification code and the facial feature information;
[0036] Secondly, the key verification module is used to randomly generate a new second key after receiving the face recognition success information, all keys are different; when the system is pre-stored, the first key in the information base is sent to the person The facial feature information corresponds to the mobile terminal bound by the user; the newly generated second key is simultaneously sent to the mobile terminal and the syste...
Embodiment 3
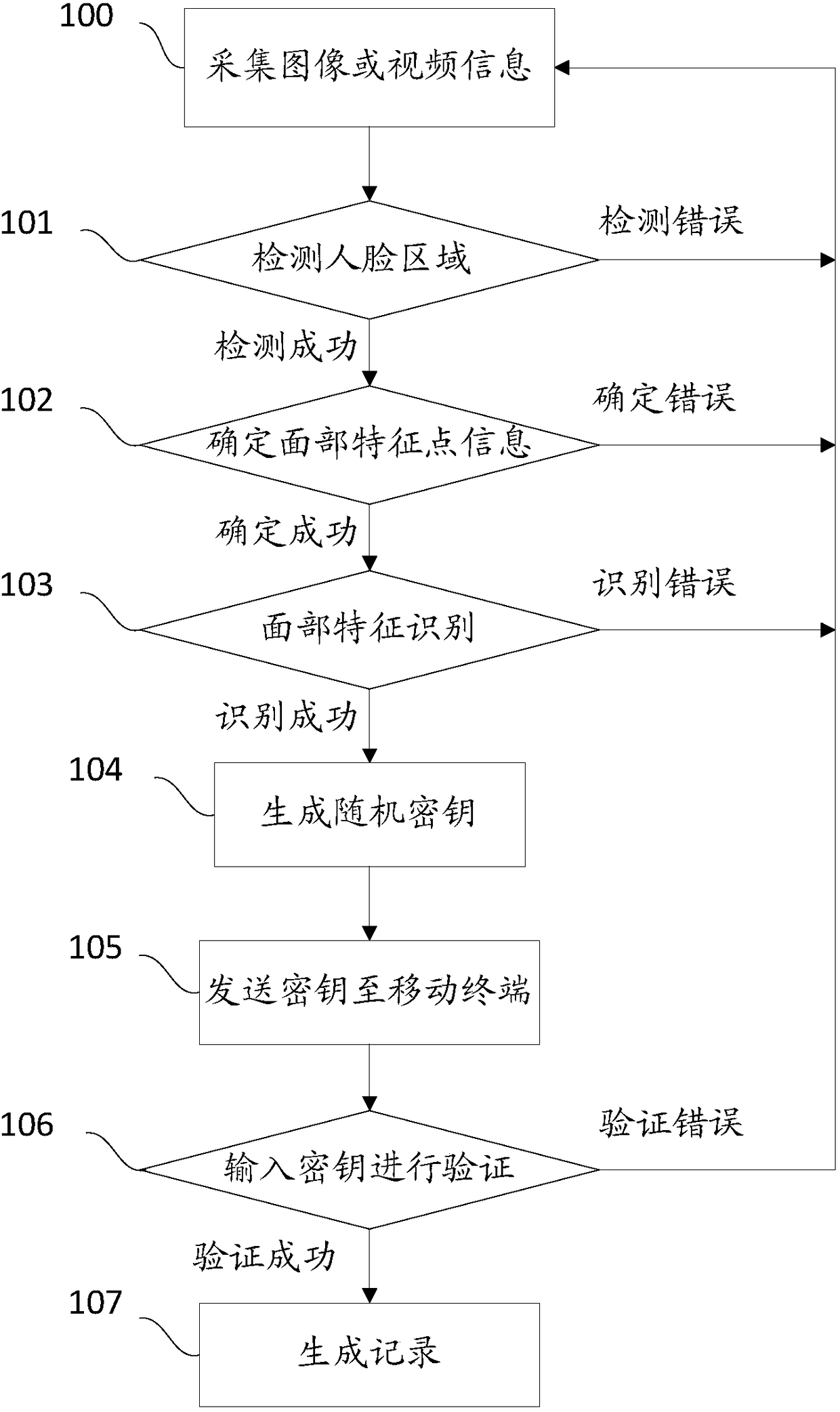
[0048] Embodiment 3: The face recognition method of this embodiment further includes: the face recognition process supports the collection of images or videos of one or more users at a time, and uses the Harr classifier to detect one or more face regions respectively, which are used for the ASM algorithm. Identify the facial feature information in turn, and perform one-to-one matching. Each time the match is consistent, a face recognition success message is sent, corresponding to the subsequent password verification process, otherwise a face recognition error message is returned.
[0049] The above-mentioned Haar classifier and ASM algorithm for face region detection and facial feature determination are all existing technologies, and this embodiment is only an example, and is not limited to the above-mentioned technologies.
[0050] The embodiment of the present invention can solve the main defect that the existing face recognition method is easy to crack by applying the method...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com