Key storage method
A key storage and key technology, applied in the field of information security, can solve the problems of increasing the probability of reading data errors and the time of reading data, hidden dangers of key data security, and the inability to change the encryption factor at any time, so as to increase the strength. , the effect of key storage security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] In order to facilitate the understanding of the embodiments of the present invention, several specific embodiments will be taken as examples for further explanation below in conjunction with the accompanying drawings, and each embodiment does not constitute a limitation to the embodiments of the present invention.
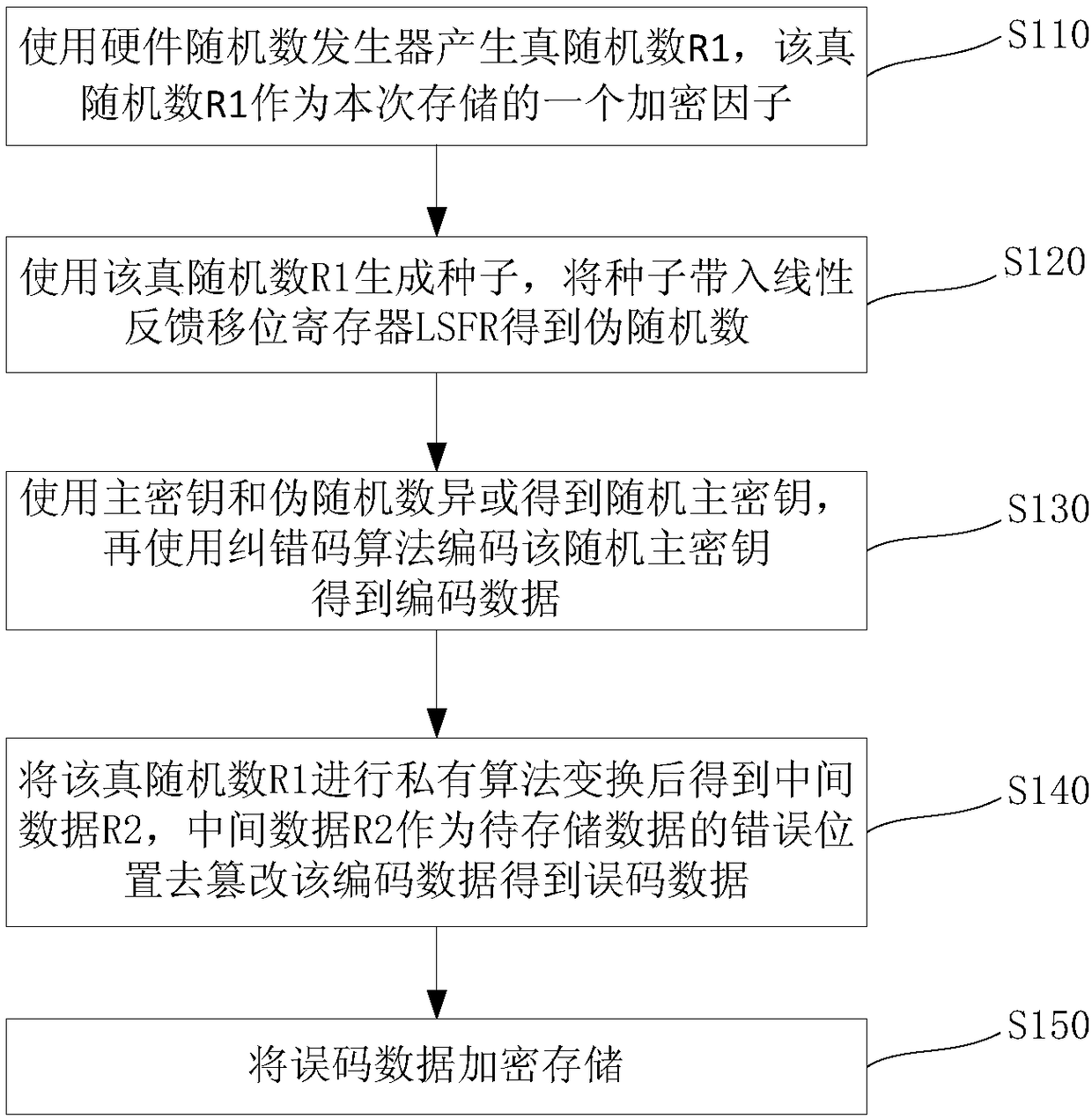
[0041] Such as figure 1 As shown, a key storage method, the method includes:
[0042] Step S110, using a hardware random number generator to generate a true random number R1, which is used as an encryption factor for this storage. This encryption factor needs to be replaced every time it is stored. The true random number R1 is only valid in one storage as an encryption factor. For example, a true random number R1′ needs to be regenerated when the master key is stored next time.
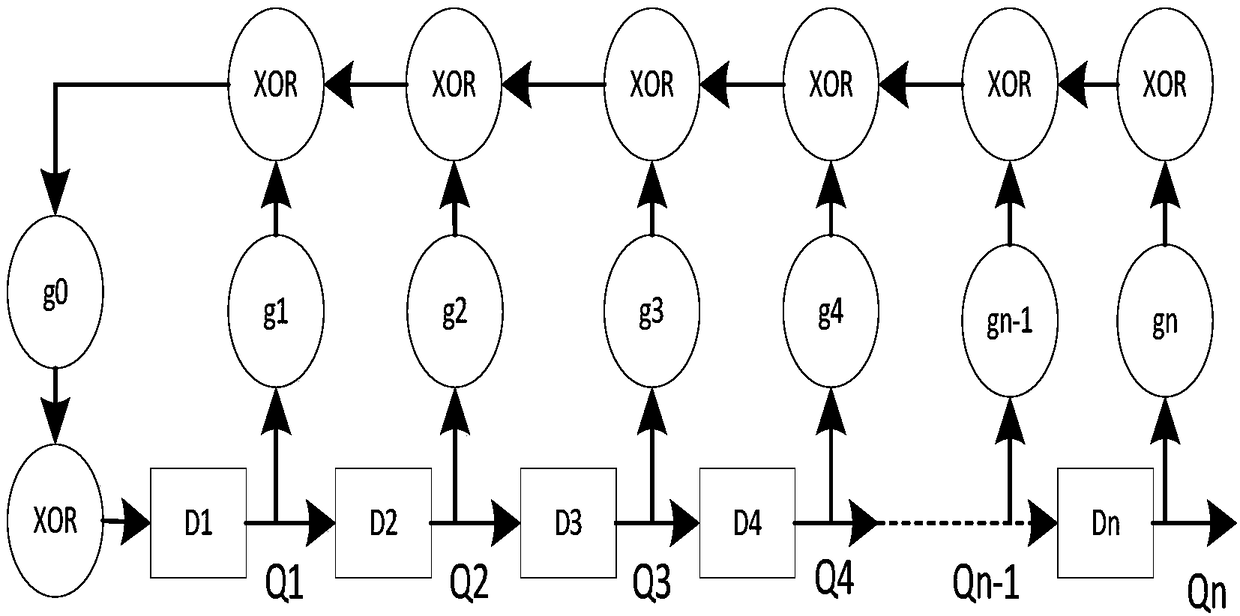
[0043] Step S120, use the true random number R1 to generate a seed, and put the seed into the linear feedback shift register LSFR to obtain a pseudo-random number.
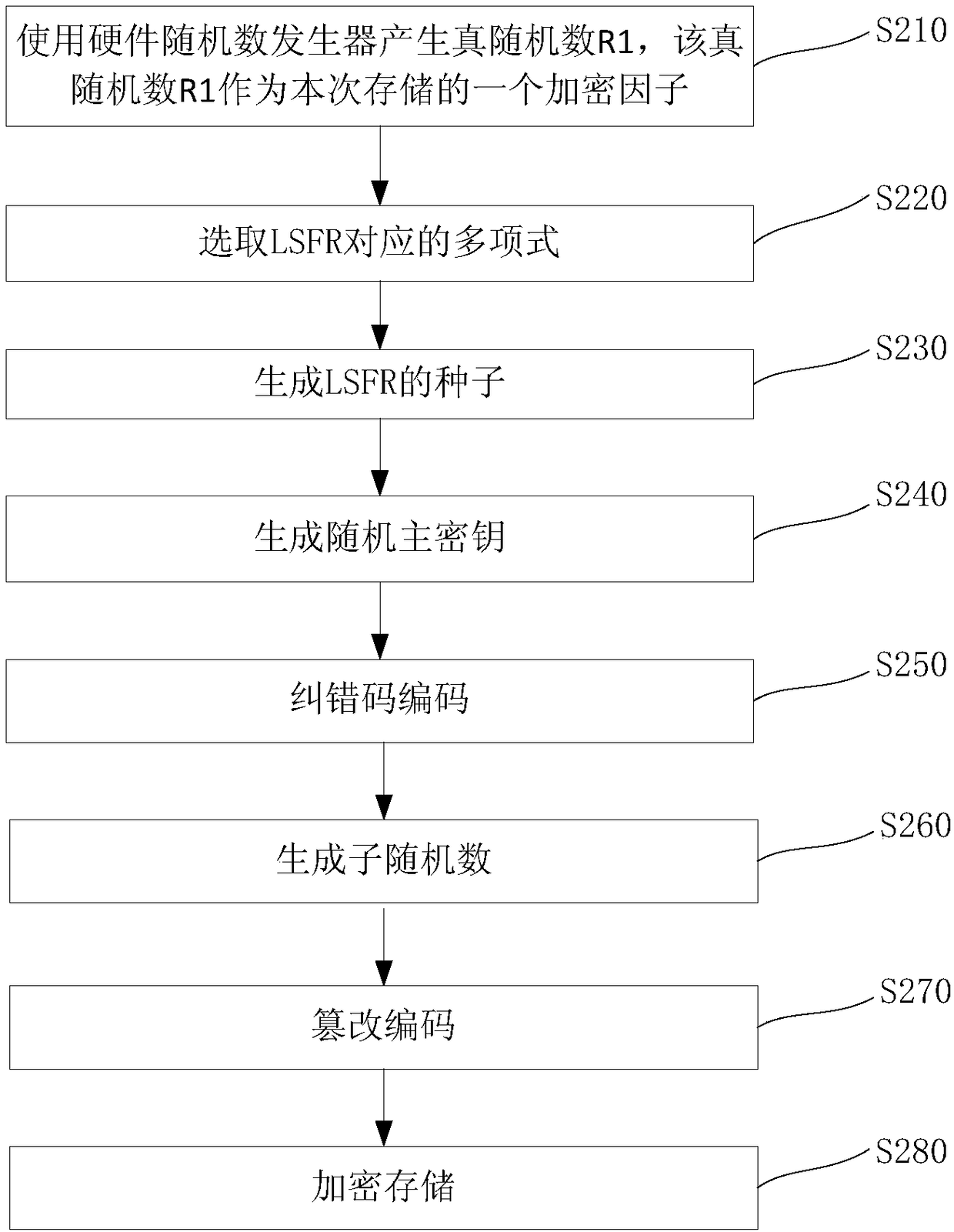
[0044] Step S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com