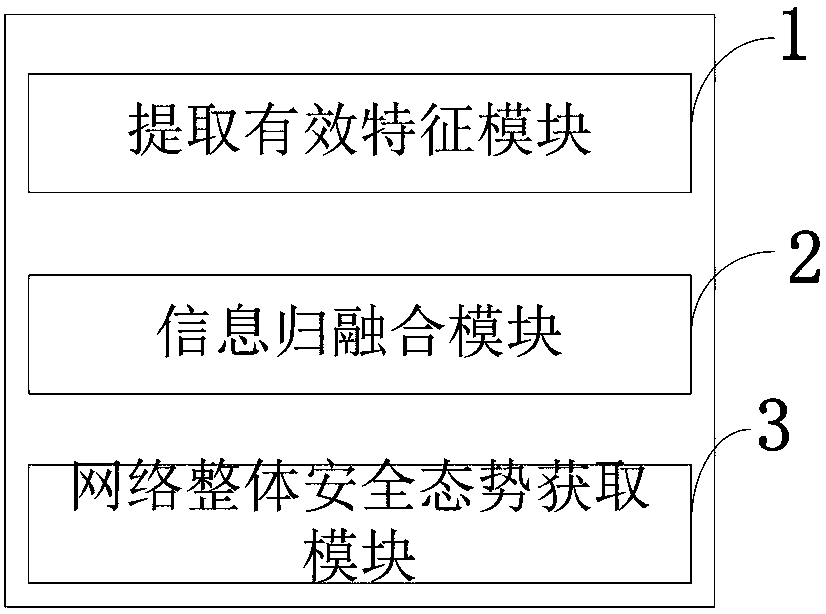
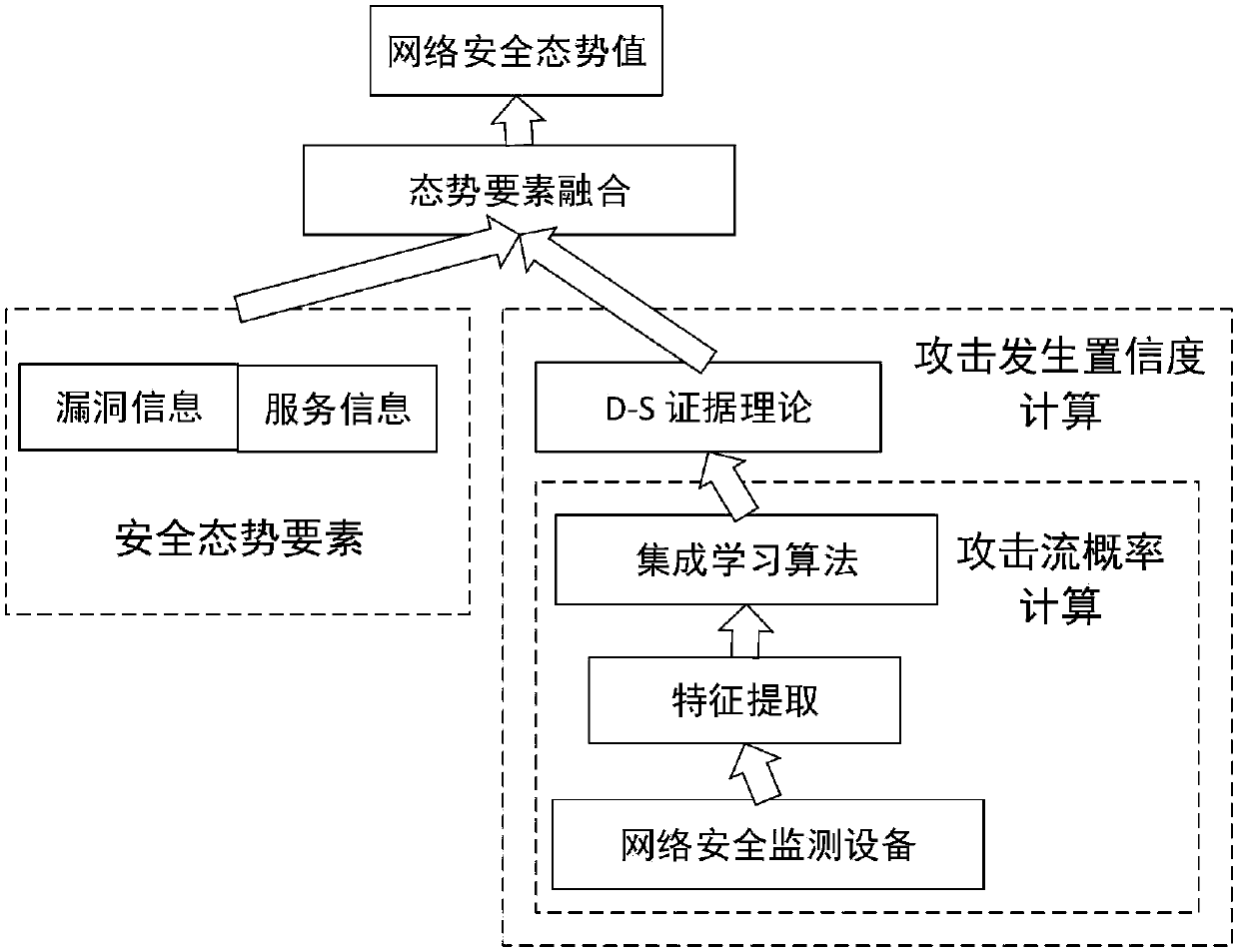
Attack occurrence confidence-based network security situation assessment method and system
A situation assessment and network security technology, applied in the transmission system, digital transmission system, data exchange network, etc., can solve the problems of increasing research difficulty in the network environment, affecting the accuracy of the quantitative evaluation system, and unreliable data sources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0110] Use the present invention to detect the DARPA 99 evaluation data set provided by MIT Lincoln Laboratory. DARPA’s evaluation data in 1999 included 58 typical attack methods in 4 categories including Probe (surveillance and probing), Dos (denial of service), U2R (user to root), R2L (remote to local) / Data, etc. A widely used benchmark dataset.
[0111] Feature extraction takes network connection or host session as the statistical unit, including four categories: basic characteristics of TCP connection, statistical characteristics of network traffic based on time, statistical characteristics of network traffic based on host, and content characteristics of TCP connection.
[0112] Data sampling is then performed. The categories of the training set are unbalanced, and directly using the original training set to train the classifier will seriously affect the accuracy. The method of undersampling is used to divide the sampling of the training set into multiple parts for use b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com