Security management system and method, equipment, storage medium, and information processing cloud platform
A security management and cloud platform technology, which is applied in transmission systems, data processing applications, general control systems, etc., can solve the problems of inability to achieve full coverage of automatic control, poor system connection and integration, and high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
[0167] Implementation Mode 1. Disaster Relief and Rescue
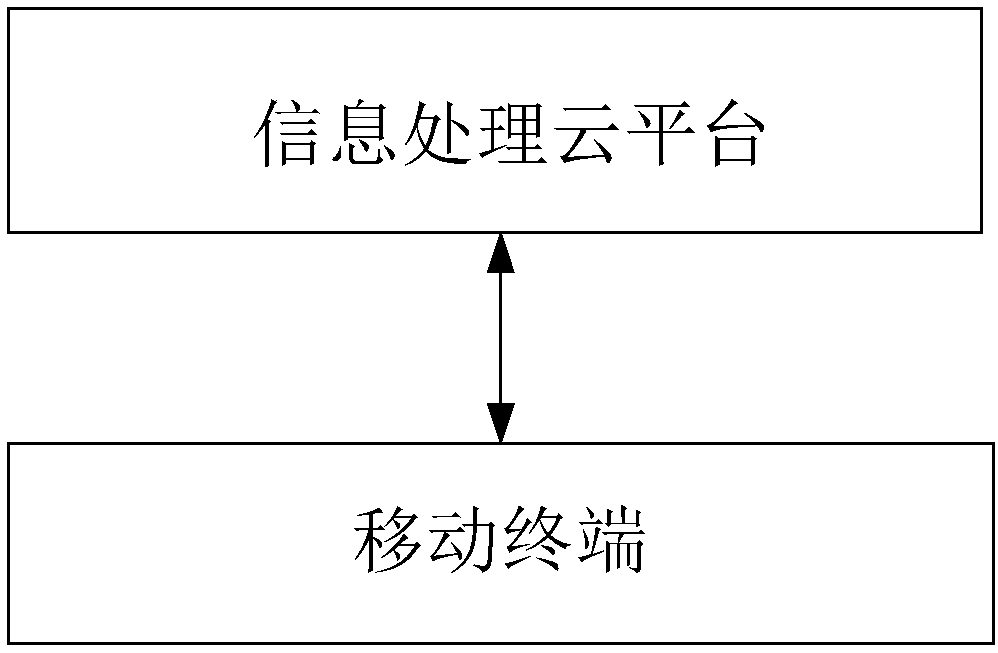
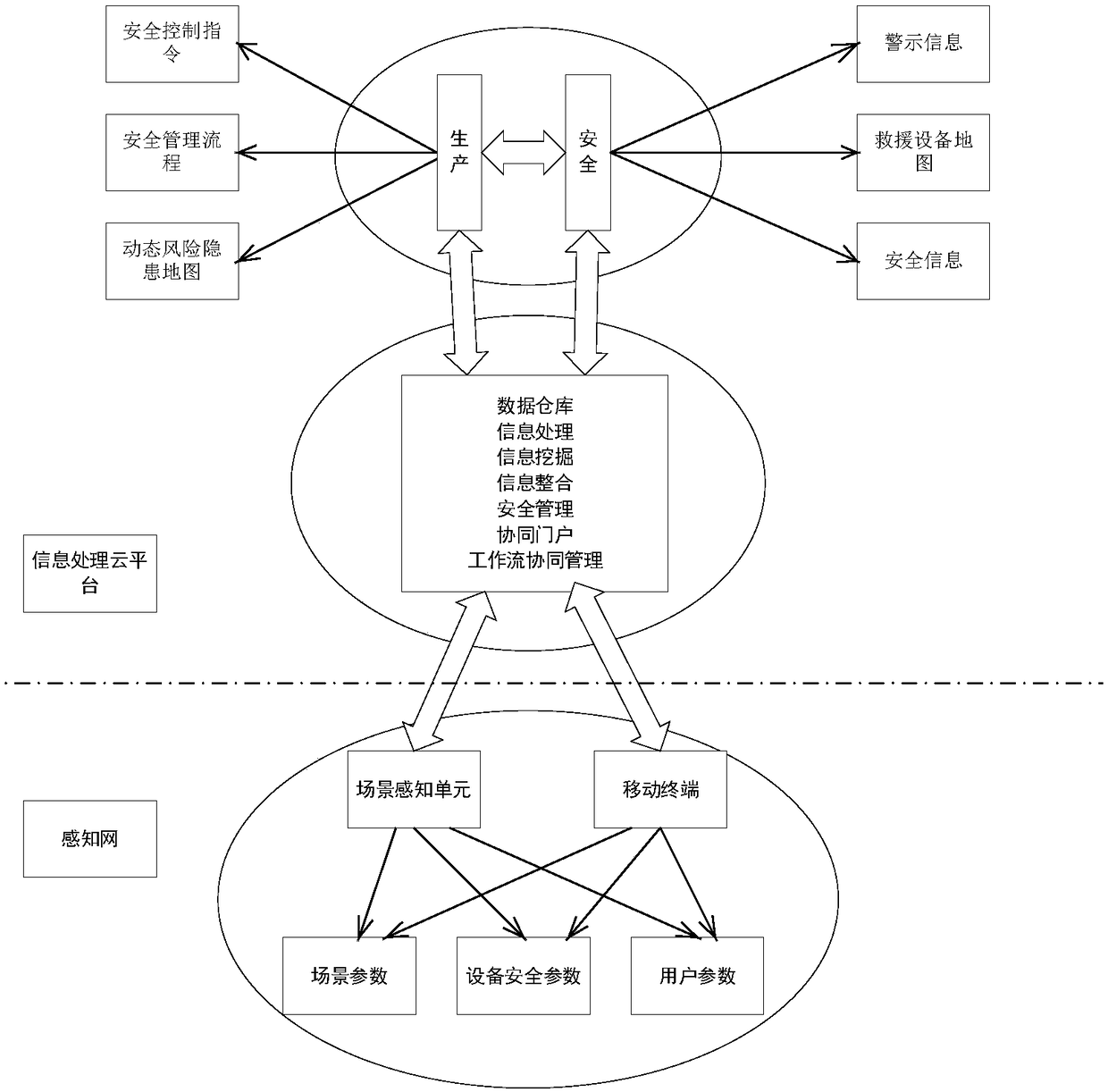
[0168] corresponds to figure 1 A safety management system, for example. When a fire breaks out in a certain building, the building and its surrounding area are used as the scene of the fire accident. There are firefighters, wounded, passers-by and other on-site personnel in this area. Computers and other mobile terminal personnel, through different trigger conditions, such as whether they are within the geographic range of fire disasters, whether they pay attention to and send fire information and their relevance, and whether they are valuable emergency rescue resources, experts, and technology within reach. Personnel and other conditions trigger scene modules and workgroup functions, and associate and group them with the fire scene. After association, disaster relief and work group management is carried out in the form of an emergency working group. These personnel share fire-related information in the working group...
Embodiment approach 2
[0169] Implementation Mode 2, Factory Security
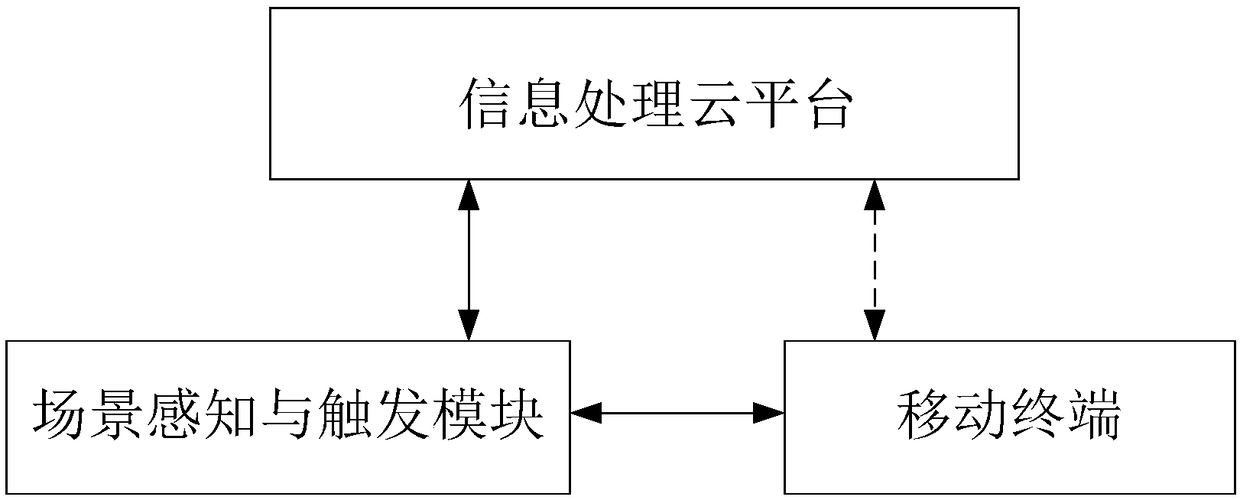
[0170] corresponds to figure 2 A safety management system, for example. A security monitoring system (as a scene perception unit) is installed in a factory workshop, and a security management platform (as an information processing cloud platform) is installed in the central computer room. When the mobile terminal holder enters the site, the security monitoring system will confirm its identity and other information monitoring to determine which scenes are included in the workshop, and whether the mobile terminal holder meets the requirements for the degree of association with a certain scene in the workshop. If yes, send trigger information to the security management platform, group them as members of the scenario into the scenario working group, implement the operation of each functional module of the system and the operation of the security management workflow; if not, continue to monitor the behavior of the person and statu...
Embodiment approach 3
[0172] Implementation Mode 3. Safety of Tour Groups
[0173] Through the Internet of Things means such as WIFI and radio frequency identification RFID on the vehicle, the person holding the mobile terminal enters the vehicle, triggers and marshals the scene of the tour group on the vehicle, and becomes a member of the security working group of the tour group. In this working group, the group leader and the preset management module will implement the travel safety management in this transportation scenario, including the release of safety precautions, notifications, reminders and prompts, risk demonstrations and emergency demonstrations. At the same time, members can submit The management personnel of the means of transportation put forward opinions and suggestions, report and give feedback on the problems existing in the travel process (including safety issues and service issues) in the form of text, image, video, etc., and the management personnel issue work instructions to re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com