Edge network security access defense system and method thereof
An edge network and defense system technology, applied in the field of network security, can solve the problems of inability to cope with data services, high energy consumption of equipment, increased delay, etc., to avoid non-uniqueness, improve simulation difficulty, and avoid information leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
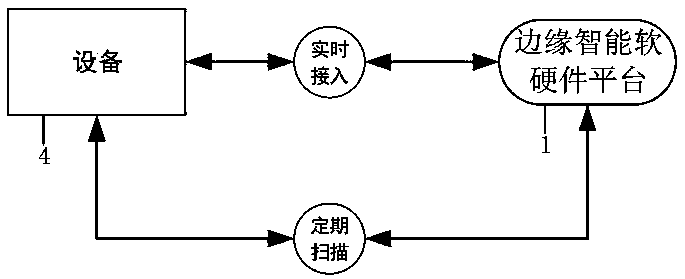
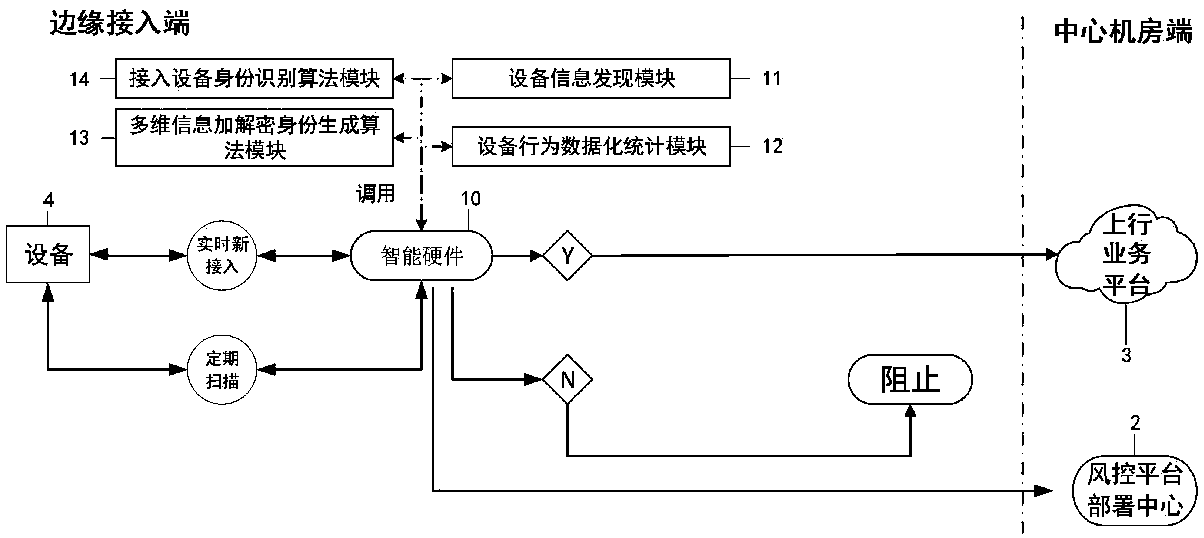
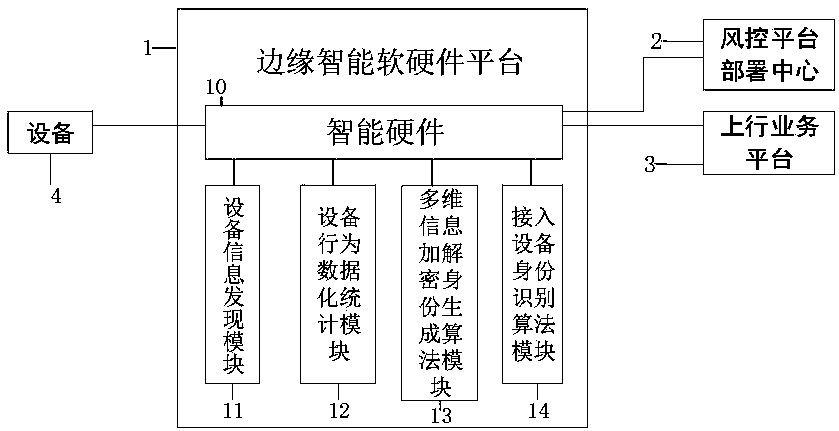
[0063] Embodiment 1, the edge network security access defense system of the present invention (hereinafter referred to as the system for short), such as Figure 1-3 As shown, it includes device 4 and edge intelligent software and hardware platform 1 located at the edge access end, and uplink service platform 3 and risk control platform deployment center 2 located in the central computer room, where device 4 and uplink service platform 3 are existing devices, such as this In the embodiment, the device 4 includes a camera, DVR, NVR, DVS or NVS, etc., and the uplink service platform 3 is an existing integrated service platform. The device 4, the uplink service platform 3, and the deployment center 2 of the risk control platform are connected to the edge intelligent software and hardware platform 1 with signals.
[0064] The edge intelligent software and hardware platform 1 is used to obtain the characteristic value and behavior characteristic value of the connected device, and ge...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com