Network security service method oriented to health cloud
A technology of network security and service method, which is applied in the field of network security services for health cloud, can solve the problems of inability to prevent virtual machine network attacks, performance bottlenecks, high costs, etc., and achieve reduced maintenance and management complexity and good scalability and robustness, cost reduction effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The preferred implementation of the health cloud-oriented network security service method of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0029] Figure 1 to Figure 4 Provide the specific implementation method of this health cloud-oriented network security service method:
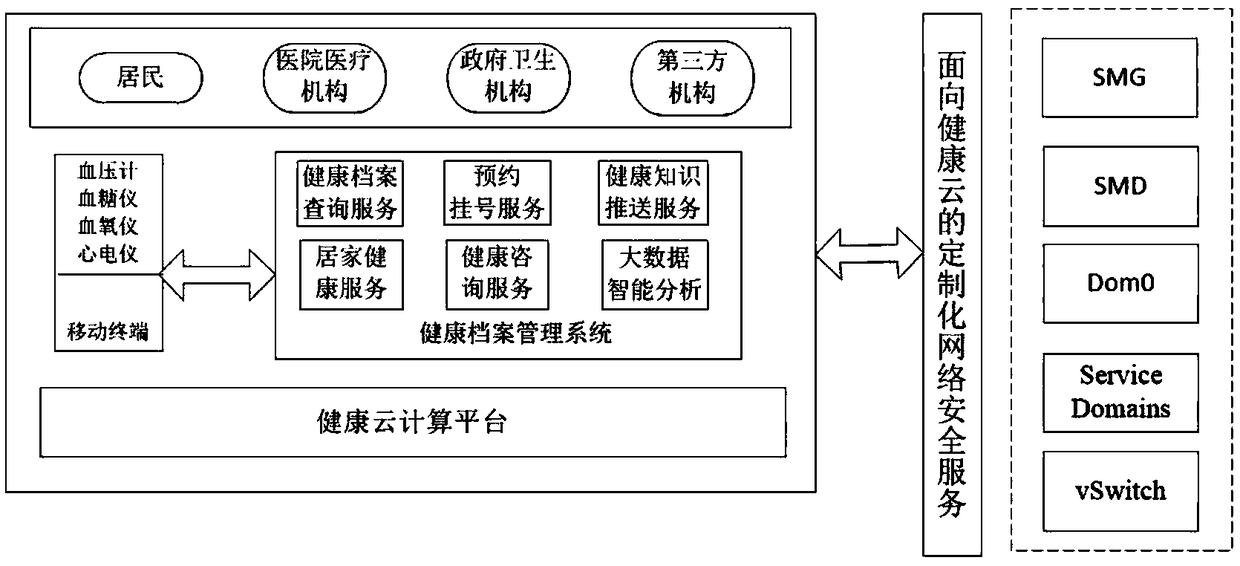
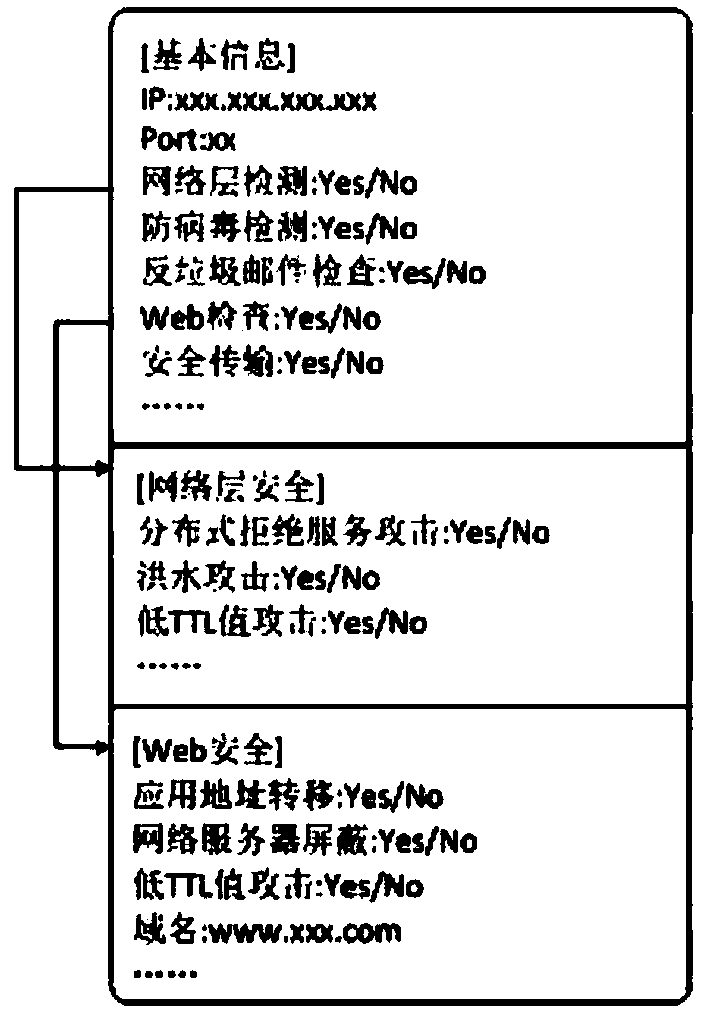
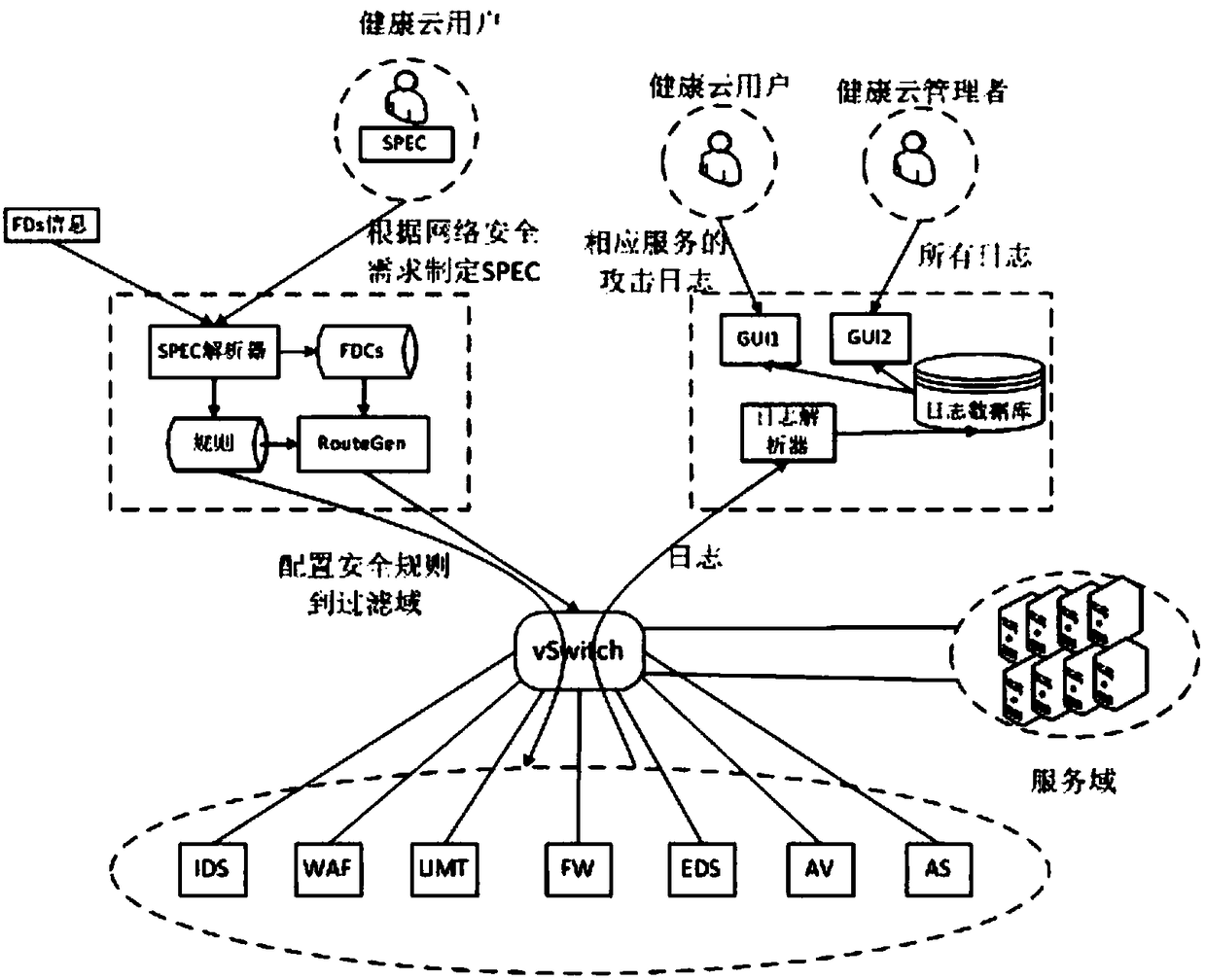
[0030] The user types of the health cloud are generally divided into residents, hospital medical institutions, government health institutions, and third-party institutions. Each type of user has a different role type. The health cloud platform obtains residents' health data from mobile terminals (such as blood pressure monitors, blood glucose meters, etc.) to establish a health file management system, and provides health file query services, appointment registration services, health knowledge push services, home health services, health consultation services, large-scale Intelligent data analysis, etc., such as figure 1 shown. Customized n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com